Almost every Android device comes with a Google search bar embedded directly into its stock home screen app. But Google search is available in so many different places on Android that having this bar in your launcher is almost overkill. On top of that, Google recently changed the logo overlay to a more colorful one that may clash with your home screen theme, so there's plenty of reasons to dislike this feature.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

Not that long ago, Google introduced a beta program for their Google Search app on Android. Much like any beta program, testers will get access to new features before they officially debut, but you might have to put up with the occasional bug as new functionality is introduced. If you'd like to sign up, it's quite simple, but I'll go over the process in detail below.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

More than likely, the first thing you noticed after booting up Windows 10 initially was a handful of new items in the taskbar across the bottom of your screen. Windows 8 users were probably glad to see the Start menu button back from the dead, but just to the right of that Windows logo are a pair of brand new entries.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

App-locking apps have been around for a while, but none have had quite the panache of developer Fazil Kunhamed's latest offering, Oops! AppLock. While others use a PIN or password to restrict access to apps that are installed on Android, AppLock uses a stealthy volume button combo.

These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

This video will show you handy tips and tricks about Google search engine. These tips will help you to speed up your computing or browsing experience. This video contains tricks like Search by location, Filter image search, how to see sites that aren't online, movies running in a city theaters etc. This video is the 2nd part of the serial. You could also watch the part 1 here vimeo.com/104089915.

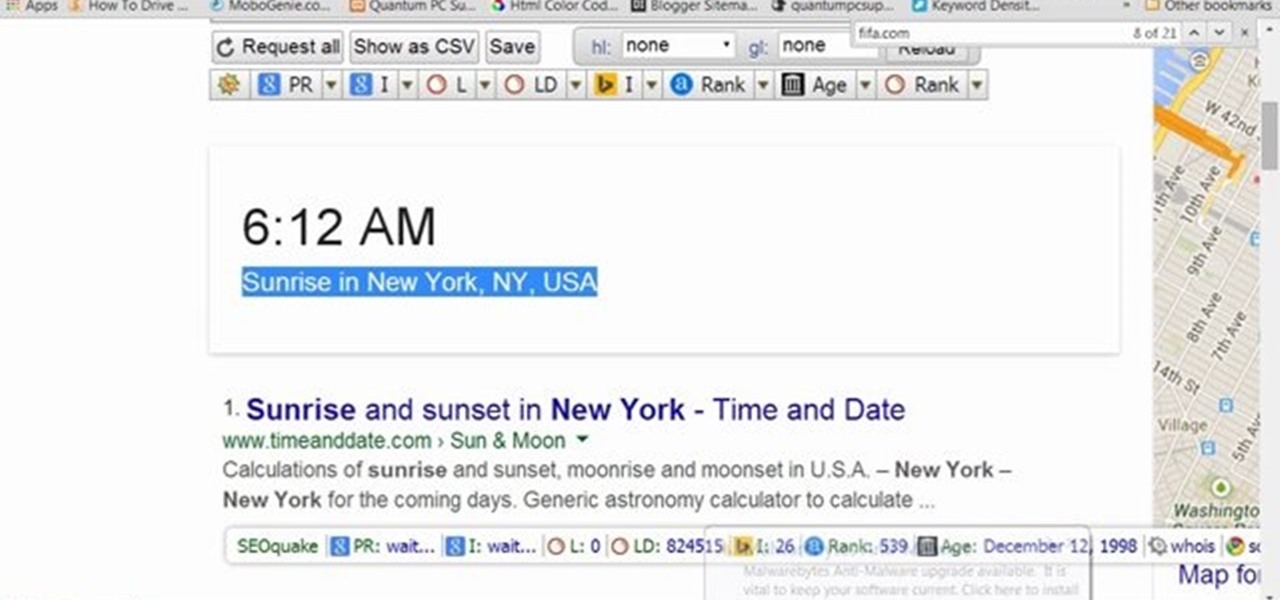
This video will guide you 5 useful tricks and tips for Google search engine. These tips include search operators, search in a single site, get definition, calculation and currency conversion, fast essential information etc. So please watch the video and follow all the steps to employ in your machine.

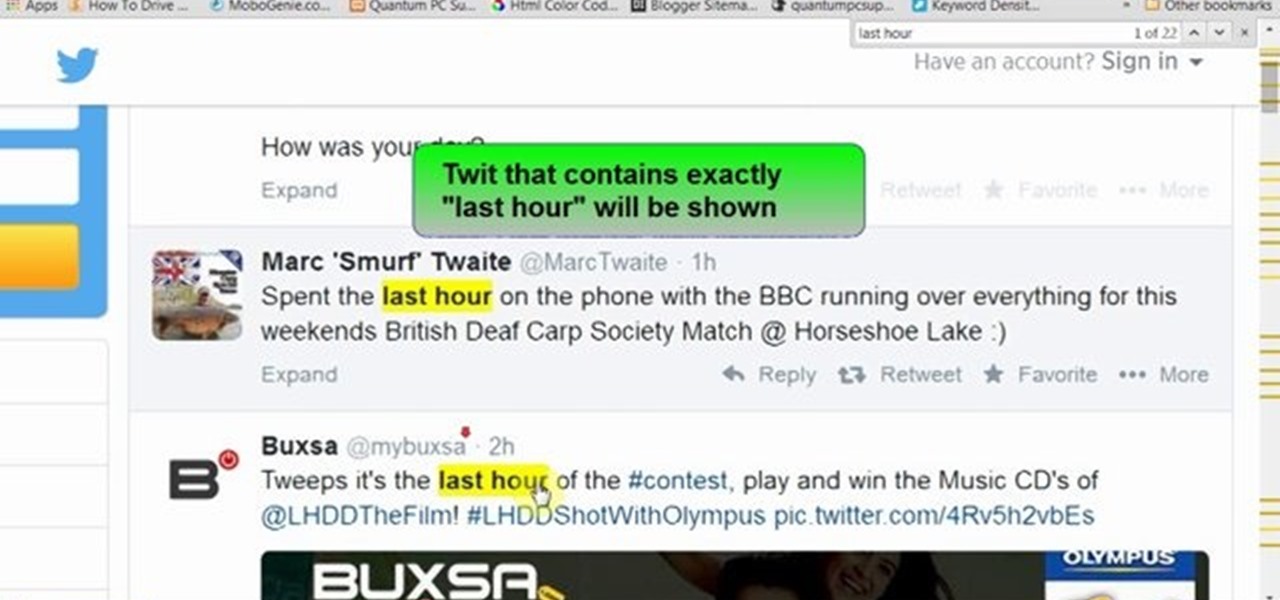
This video will show you how to search Twitter by parameters without sign up or log in. Here a person can use search parameters to find the desire twits. So there is no headache for signing up or logged in for searching. So please Watch the video and follow all the steps to do it yourself.

This video will show you how to search on twitter using parameters without Signup. You don't need to be sign up for twitter search. Anyone could use this twitter search feature and utilize parameter. Watch the video and follow all the steps carefully.

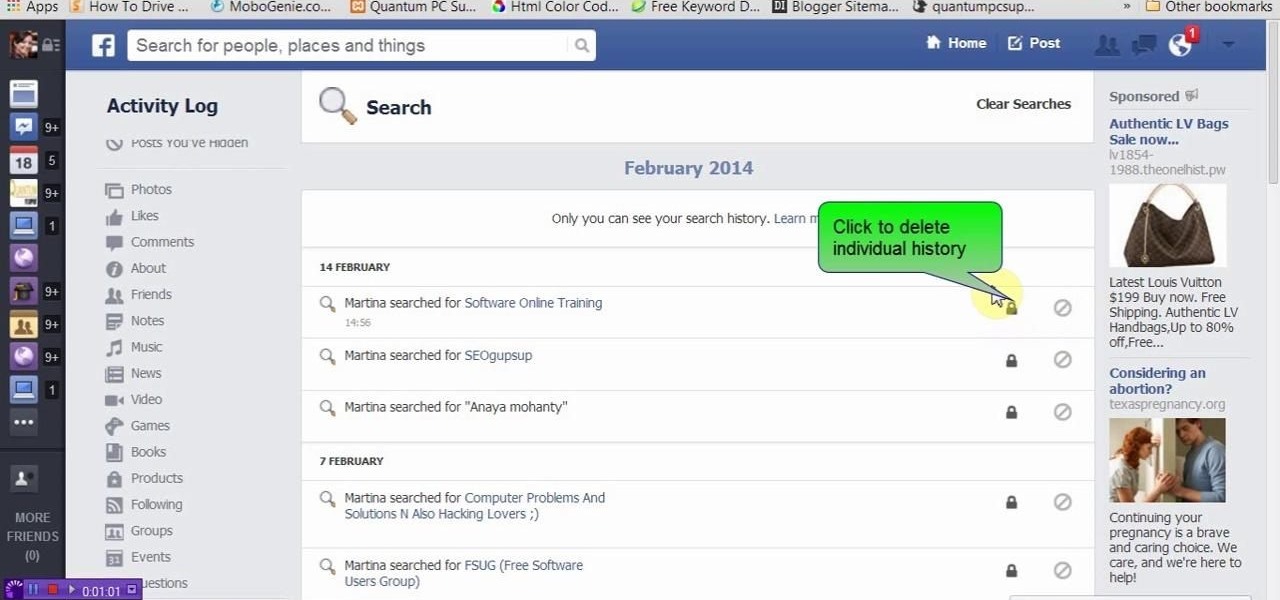
This video will show you how to delete or view Facebook search history. Facebook saves its user search history. User could view and delete this search history. Watch the video and follow all the steps to do it yourself.

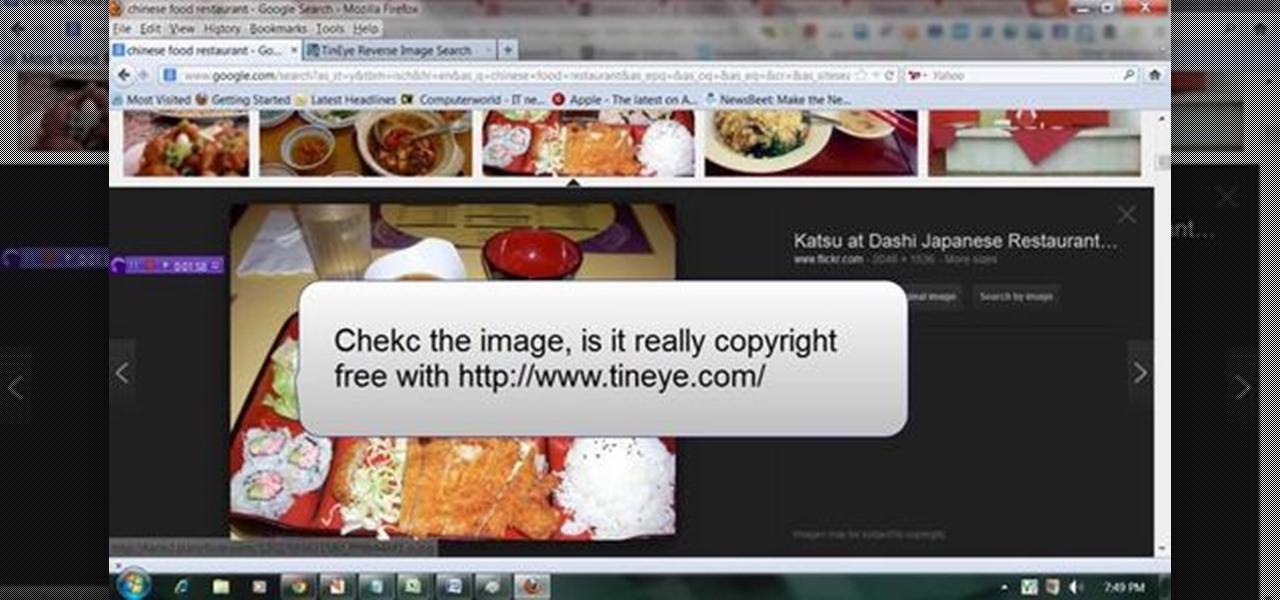
This video will describe you how to search for a Copyright free image. Google advanced image search gives you the opportunity to find free images from any category. Copyright free images are free to use in personal even as commercial purpose. Watch the video and follow the steps.

As I begin my move across the country, I find myself dodging all kinds of Craigslist scams, particularly in the apartments and housing classifieds. Fortunately, I've discovered a little trick that will tip me off to a scam before I lose $1,000 in a fake security deposit.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

As an avid reader, I come across a plethora of words I don't know, but my iPhone is always right there to help figure out their meanings.

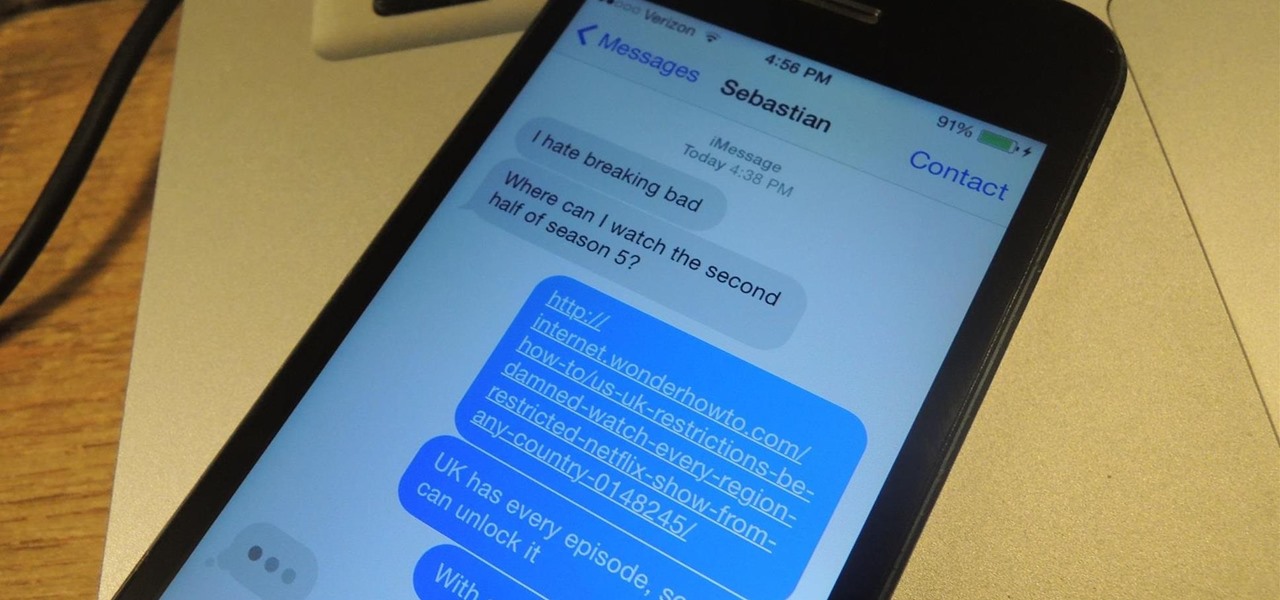
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

If you've had the pleasure of owning both an iOS and Android device, you may have noticed one subtle difference on each one's PIN unlock screen. Android's lock screen requires you to press "OK" after entering the PIN, whereas iOS's simply unlocks the screen right after the last digit.

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

If you have an iOS device, chances are you've spent a decent amount of time in the App Store—without at least a few apps, smartphones are pretty boring. There's an app to do just about anything you could ask for, but the problem is finding them. Searching the App Store sucks.

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

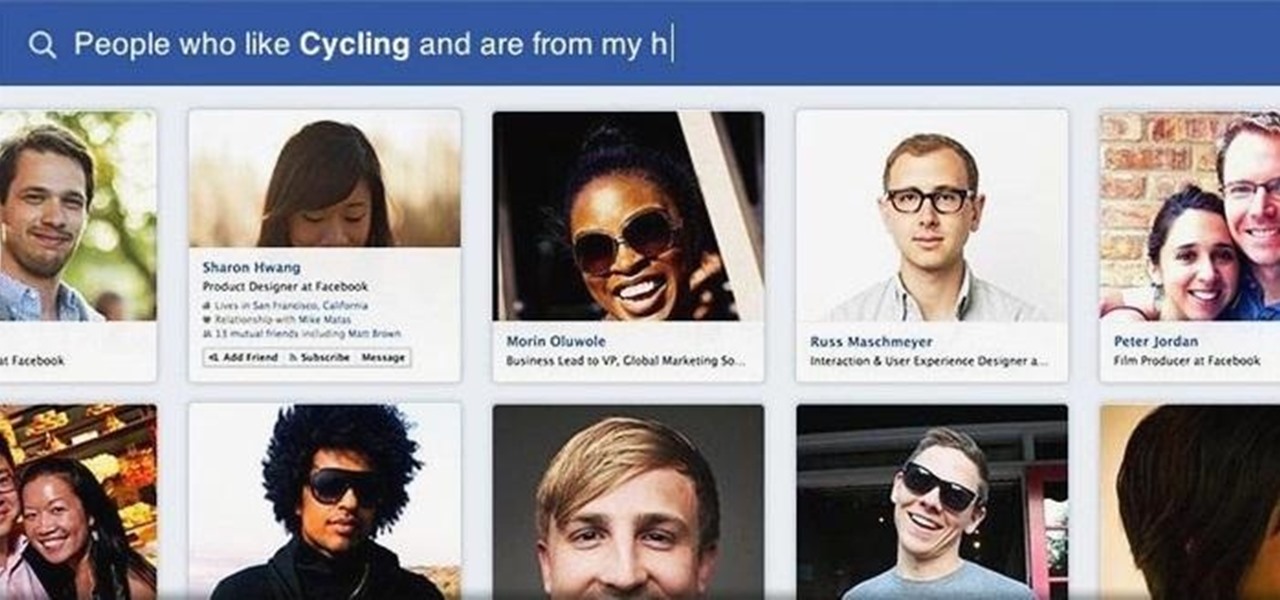
Facebook has been looking to launch a new product for a while now, and it seems they've finally realized what they're best at—being as creepy as possible. If you thought your boss checking out your girlfriend's beach photos was weird, Facebook's new Graph Search has only upped the ante. Now, I don't want to be an alarmist, because I'm sure there are a bunch of great things a Facebook search would find. If you're single, perhaps you could search "Girls that are single that like Goodfellas." Th...

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to cheat on facebook's Bejeweled Blitz (07/27/09).

Want to learn how to make your own comic book? This instructional video will teach you how to take your created character and their powers and enter them into a comic book world. The first step, is to decide whether your character will be acting as a hero or villain. Next, you must create the setting. This is followed by the conflict of the story. Finally, the resolution. The hero must defeat the villain and everything is back to normal. The video then takes you through a sample comic book an...

In this clip, you'll learn how to make use of the new Global Search app on the BlackBerry Torch 9800 smartphone. This clip will teach you everything you'll need to know. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this official video guide from the folks at Blackberry. For detailed information, including step-by-step instructions, take a look.

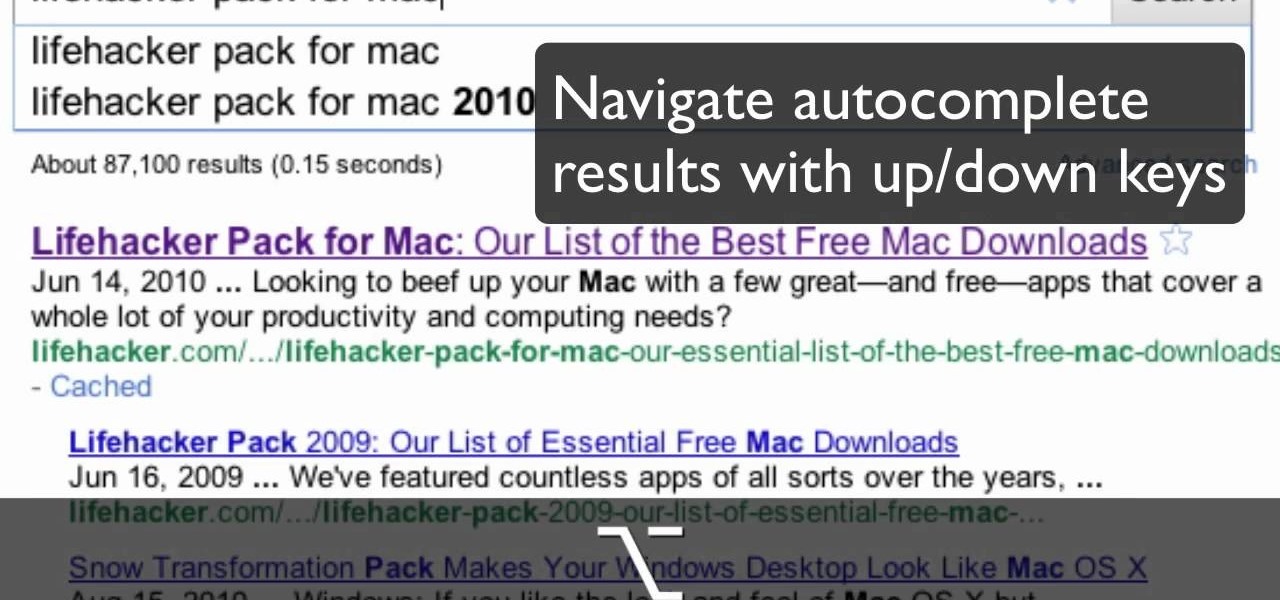
Google Instant has made searching on the main page of Google faster than ever before. Did you know that there are several keyboard shortcuts that you can use to make it work even faster? This video will show you how to use shortcuts to go to results more quickly and add more time to your day.