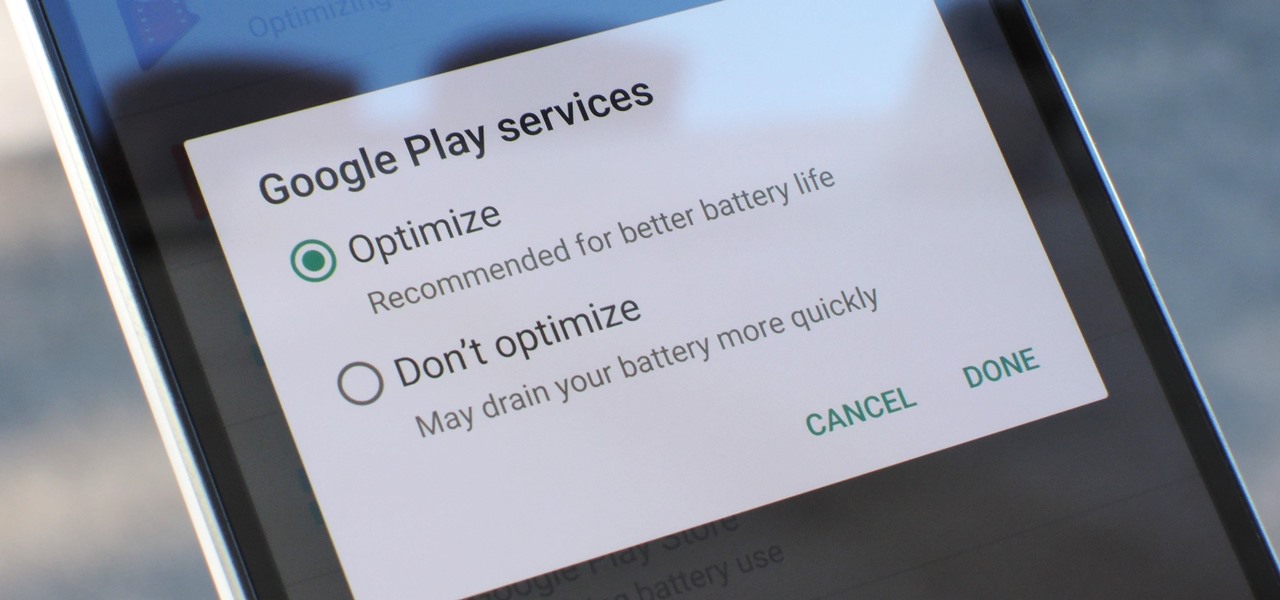
Google Play Services has been near the top of every Android user's list of battery-sucking apps for years now. It's a core system app, so you'd expect some battery drain, but for many folks, it runs rampant.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and '90s.
Google just made searching the web on your iPhone a whole lot easier with its new GBoard keyboard for iOS. It has a built-in Google icon so that you can search directly from whatever app you're in, making it a cinch to add images, GIFs, directions, videos, and more.

Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specific message.

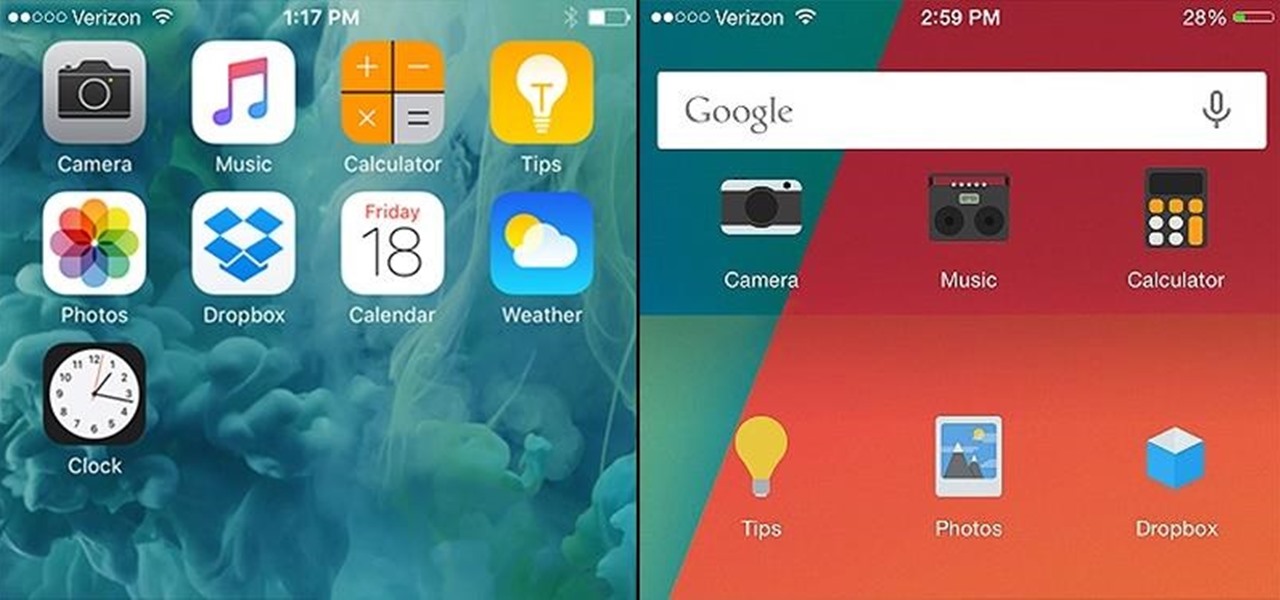
The competition between iOS and Android is fierce. Each operating system offers unique and powerful features, so it can be hard to choose which one you want. However, for iPhone users, a little tweaking and some themes can give your iPhone some of the key features and aesthetics of an Android.

Of all the new features in Android 6.0 Marshmallow, an automatic battery-saving function called "Doze" might just be the most interesting. What it all boils down to is that if you set your phone down on a flat surface, the device uses internal sensors to detect that it's motionless and not in use, then responds by drastically scaling back battery-sucking services until the next time you pick your phone up.

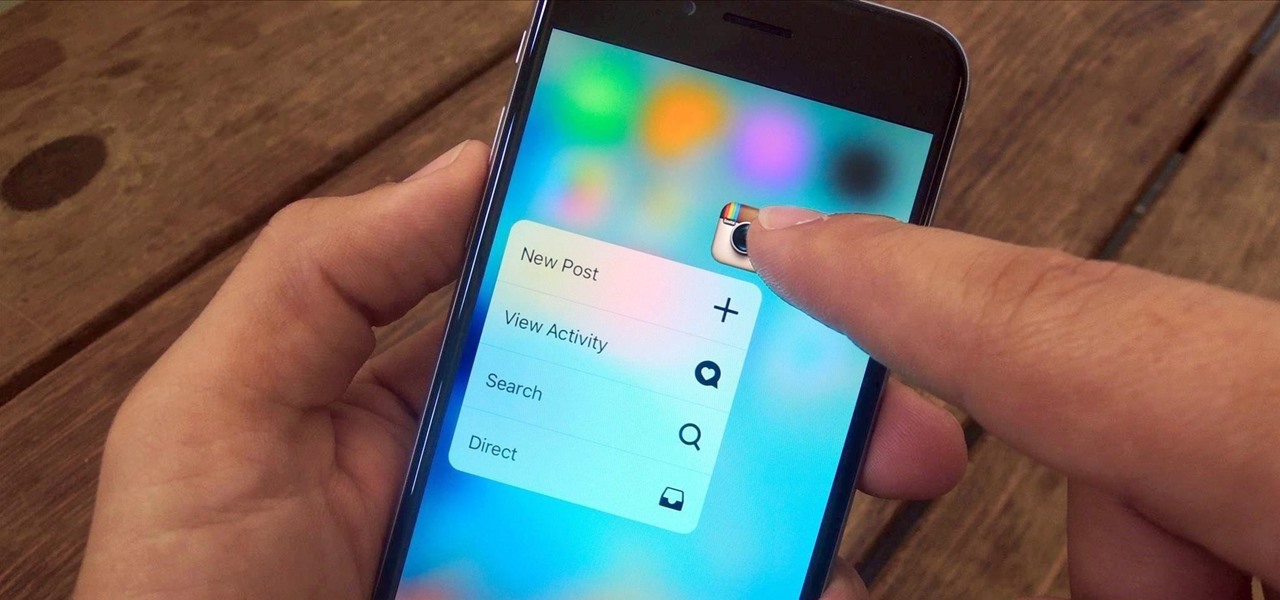
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

You'll have to forgive me if I sound a little overexcited about this, but in my opinion, Google's "Now on Tap" is one of the most innovative™ smartphone features that I've seen in years. Sure, Microsoft heard about the feature being in the works and rushed out a similar Android app so they could say they were first, but that solution pales in comparison to this one.

Initially reluctant to port Firefox over to iOS, Mozilla has finally released the first public preview of their famed web browser. While this is great news for all Firefox users, the bad news is that the browser is currently available for download only in New Zealand.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

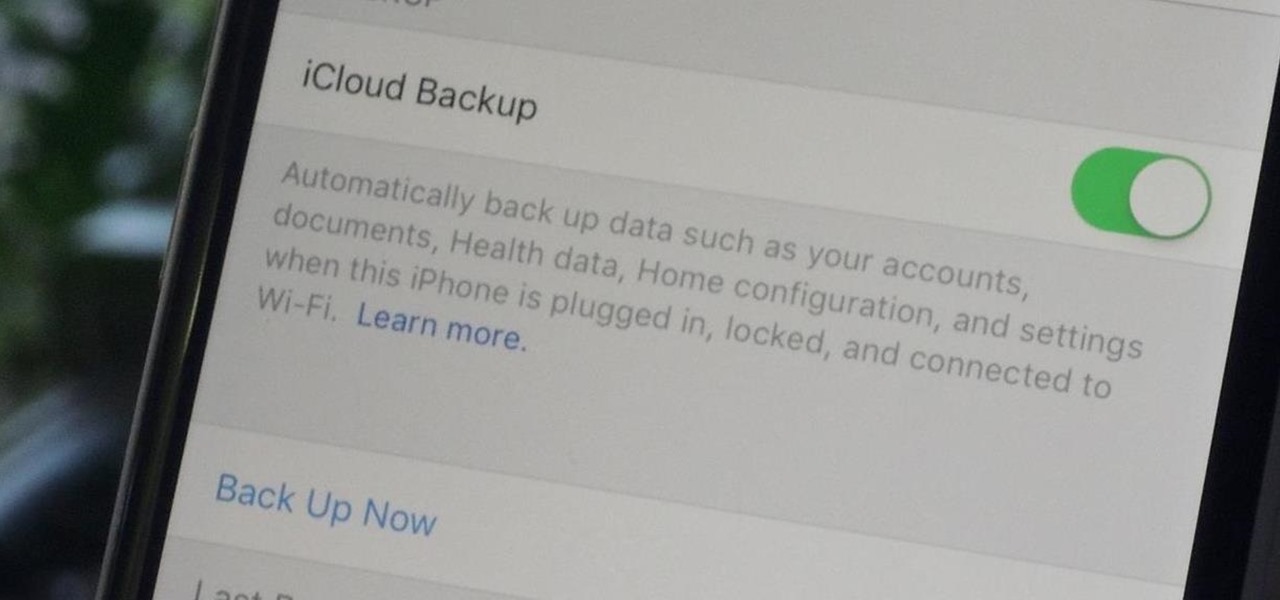
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

The horizontal dotted icon in your iPhone's status bar serves as an indicator of your device's network strength. And while it does help provide an approximation of how strong your signal is, swapping it out to display an actual numeric value is a lot more precise and can change up the look of your iPhone (or at least the status bar). The process is quick, painless, and you don't even need to jailbreak your phone.

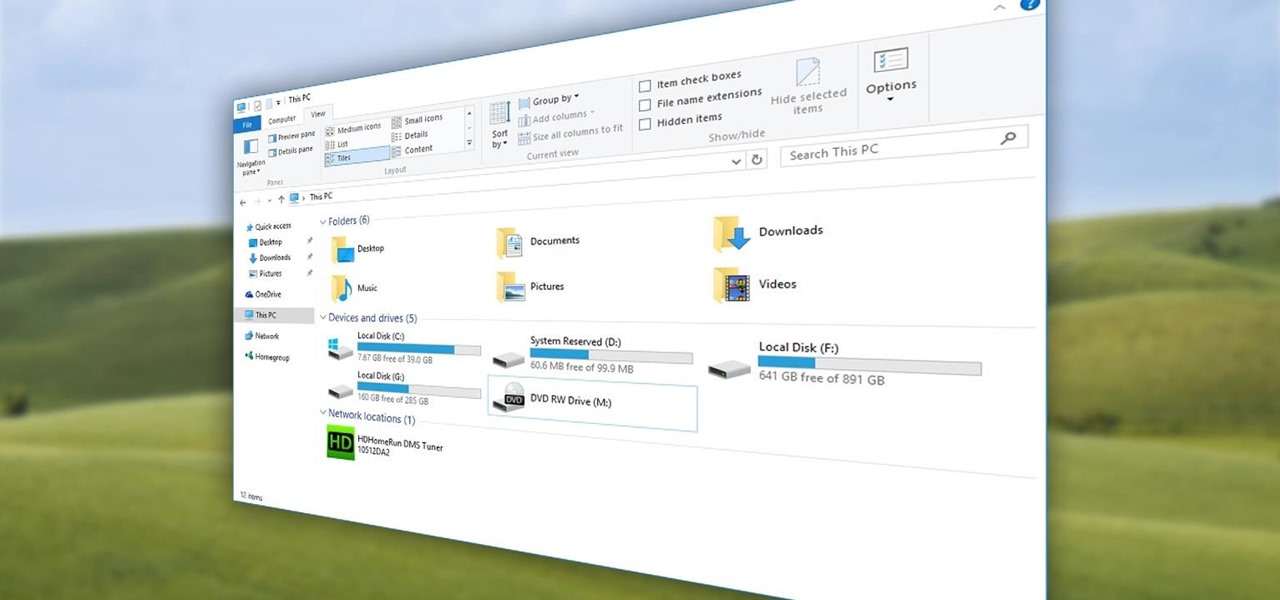
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

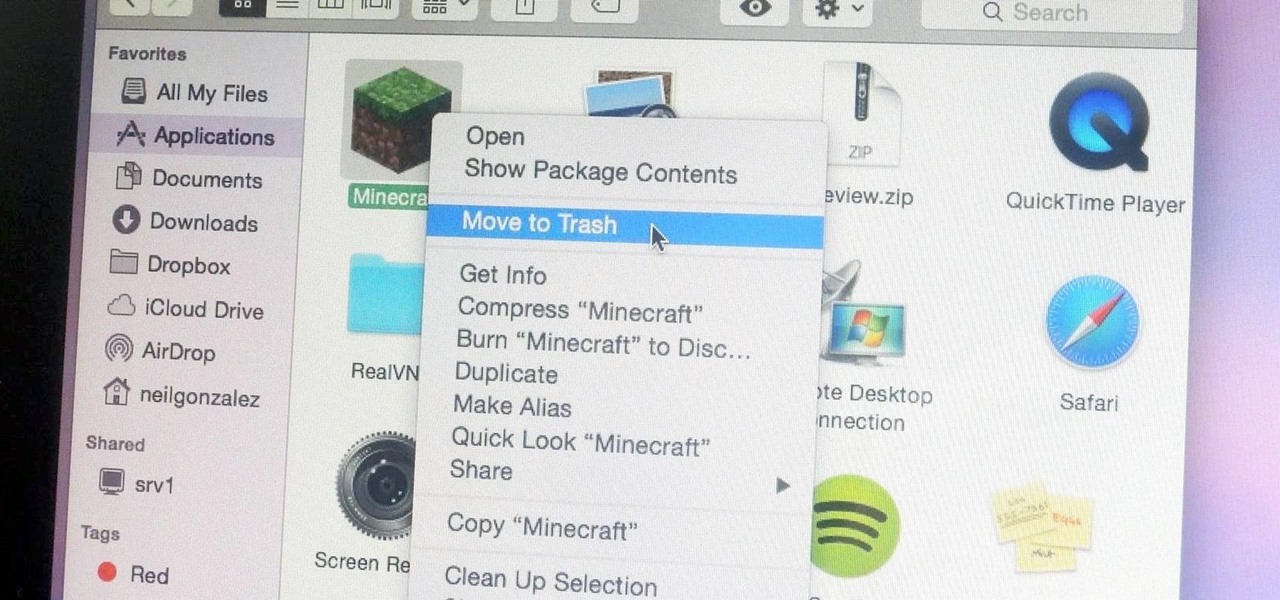
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

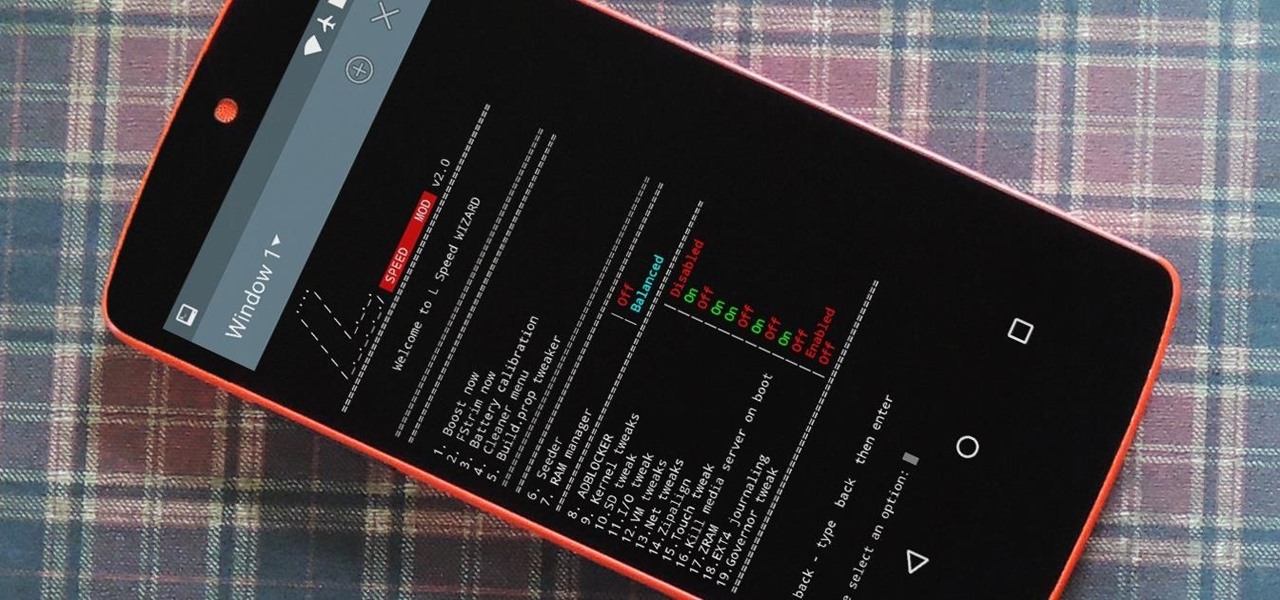
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management and other system-level functions, he created a flashable ZIP that will apply many fixes in one fell swoop.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

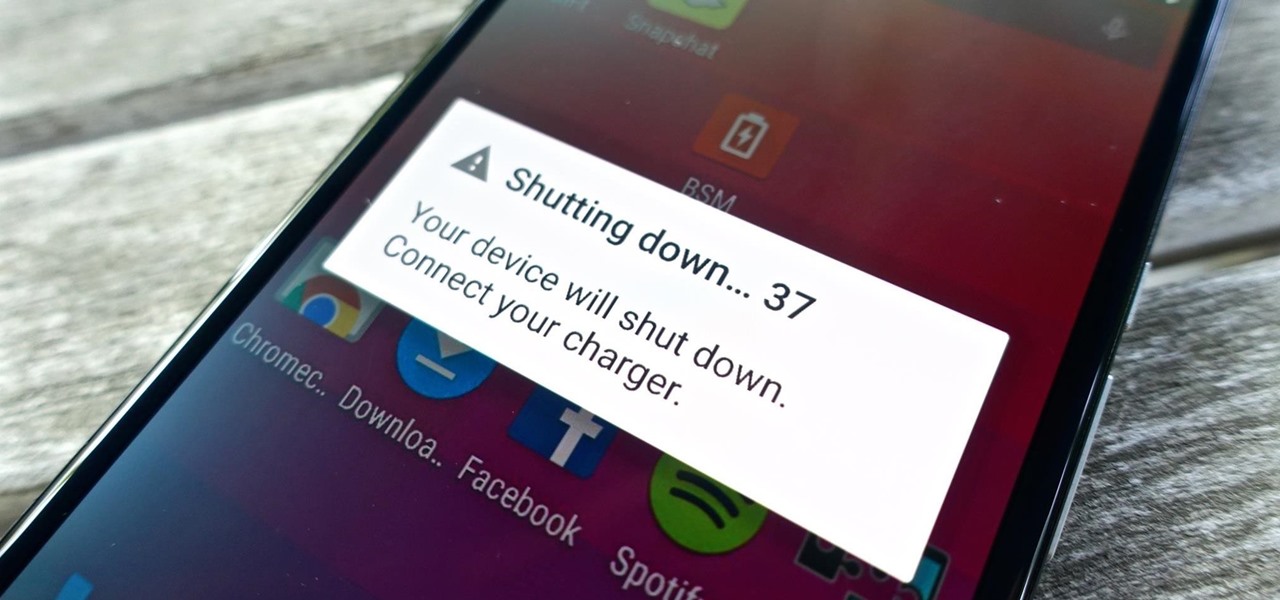
Even if my phone has only 1% of battery life left, I'll keep using it until I can get to a power source somewhere. Most times I never make it to a charger, and my device eventually powers down on its own.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

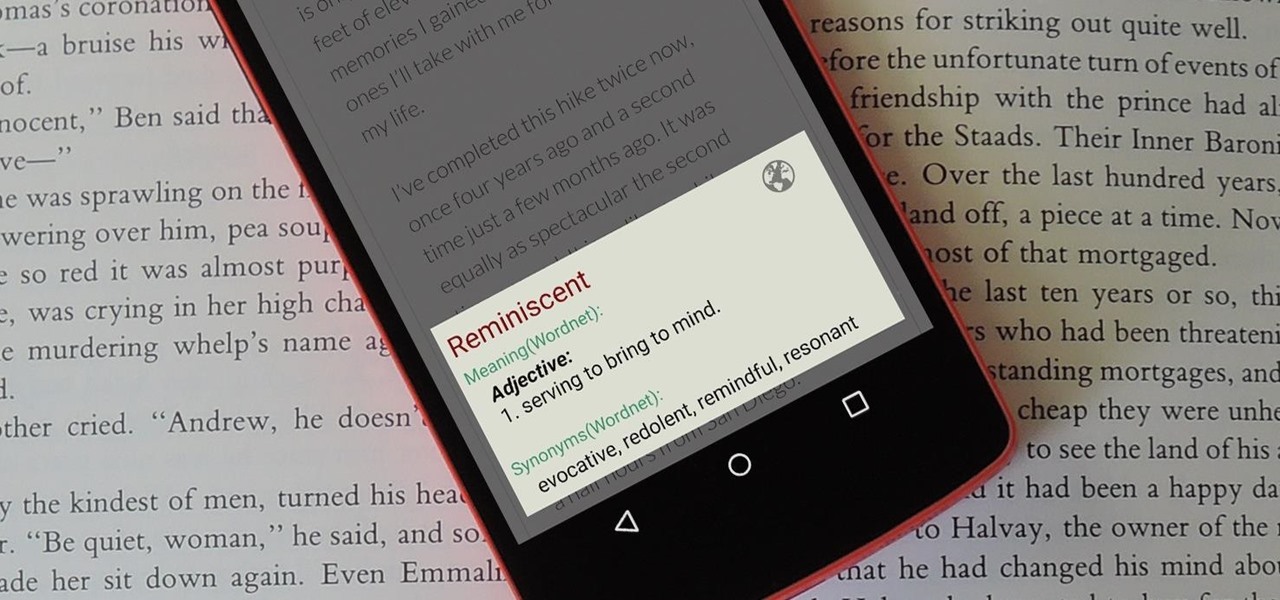
When you're browsing the web, going through emails, or reading a book or magazine, you'll occasionally come across a word or phrase that you haven't seen before. This would be a perfect time to have some sort of built-in dictionary lookup service, but most Android apps lack such a feature.

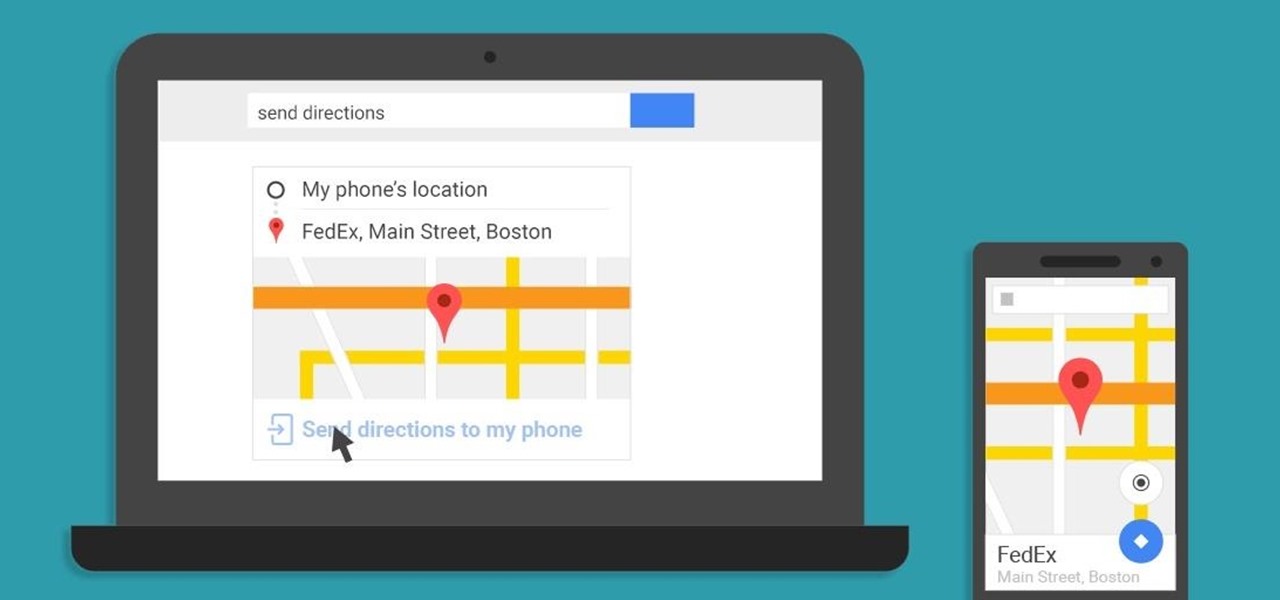
A set of cool new Android-related Google Search functions made their debut this week, which will allow you to locate your phone, send directions to your mobile device, set alarms and reminders, and send notes from any web browser.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

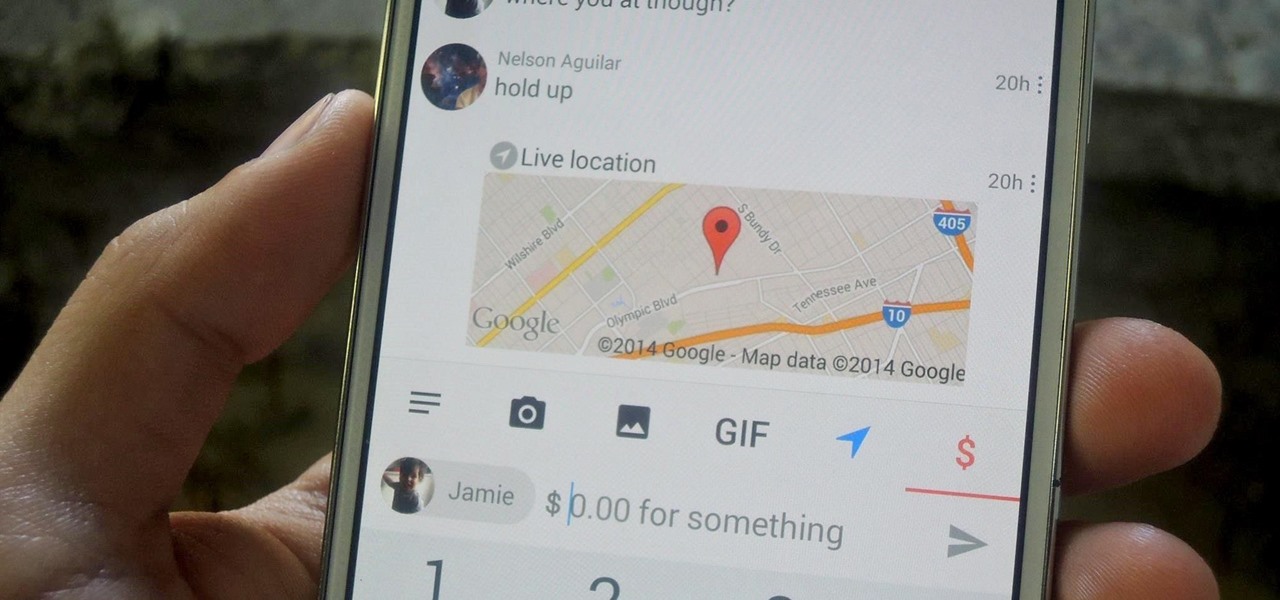
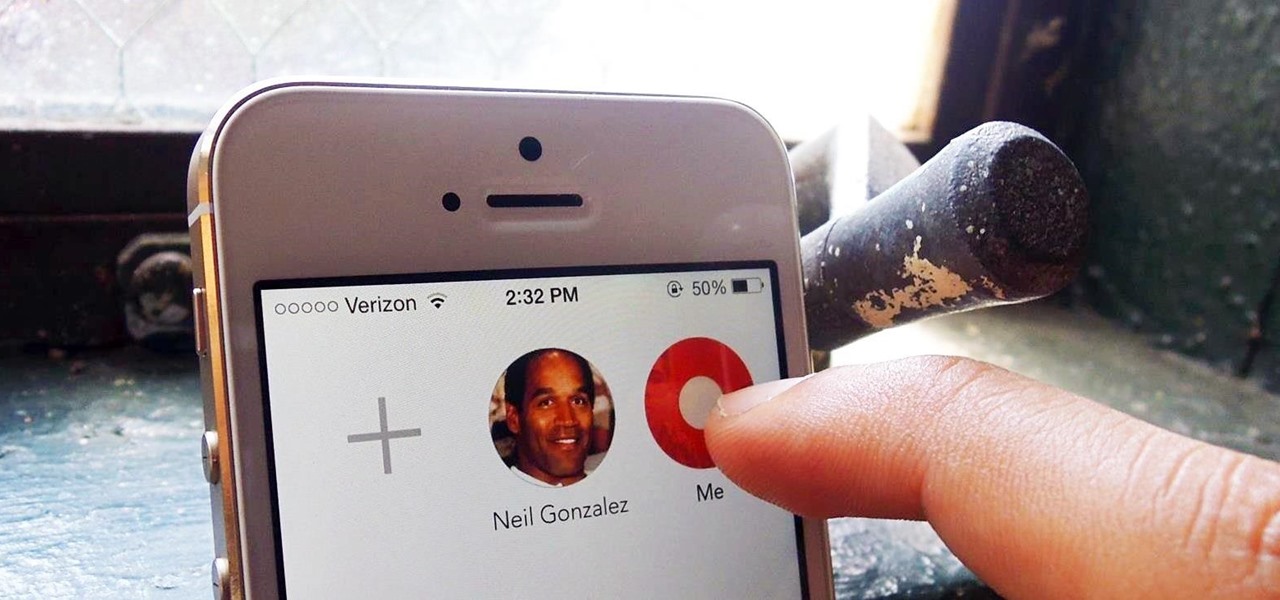
A messaging app that blows your mind doesn't come along very often. Yeah, there's WhatsApp and Facebook Messenger, which are both good for what they are (web-based messaging platforms), but when it comes to interesting or unique features, they're somewhat lacking.

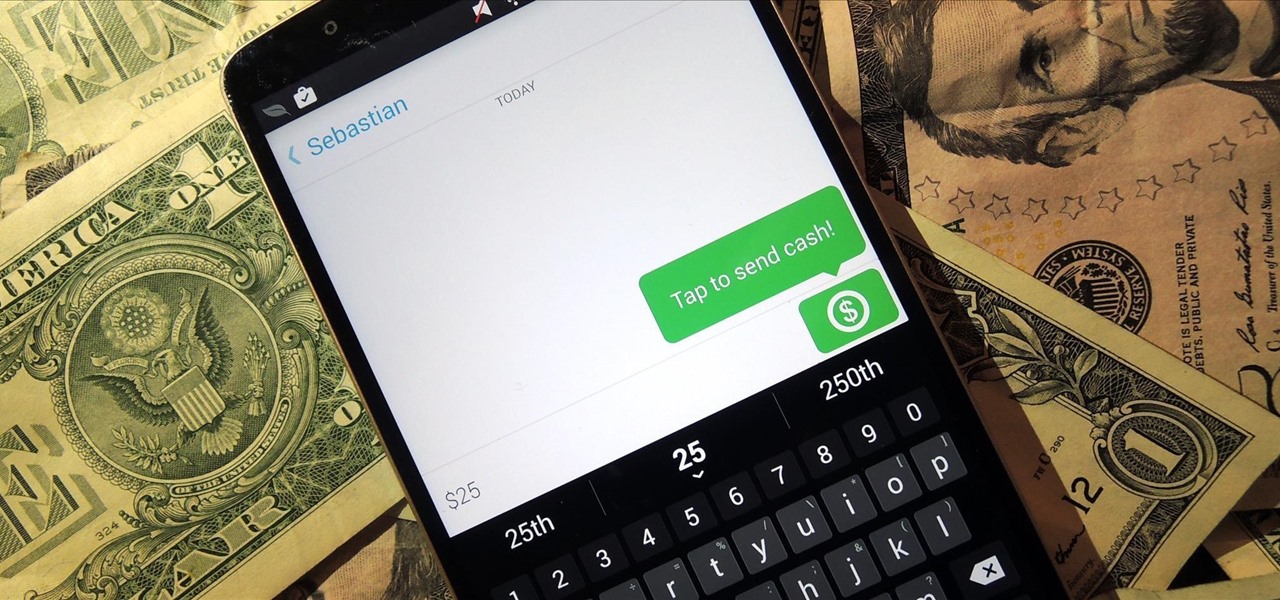
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Apple is bringing one of the biggest updates ever to its Messages app, including a feature that will allow users to send audio messages back and forth with the press of a button. Goodbye, voicemail.

Notice anything different about your Google searches lately? Your favorite businesses are becoming even more reachable online. Now, you can simply Google a business and click on its highlighted phone number to give them a call immediately from your computer.

Downgrading your iPhone from iOS 8 beta back to iOS 7.1.1 is a really simple process, and a very necessary one if you're experiencing frozen screens and apps that either unexpectedly quit or don't even work at all.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Numbers are everywhere in life, and some are better at doing the math than others. Unless you're Gert Mittring, it's safe to say you use the calculator app on your tablet just as much as I do, and it's often disrupting your other tasks.

It's time to trip out with your tablet. If you're not looking to drain that precious battery life with a fancy-looking live wallpaper, then apply an optical illusion that appears to be moving on your Nexus 7 (or any other Android device) instead.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.