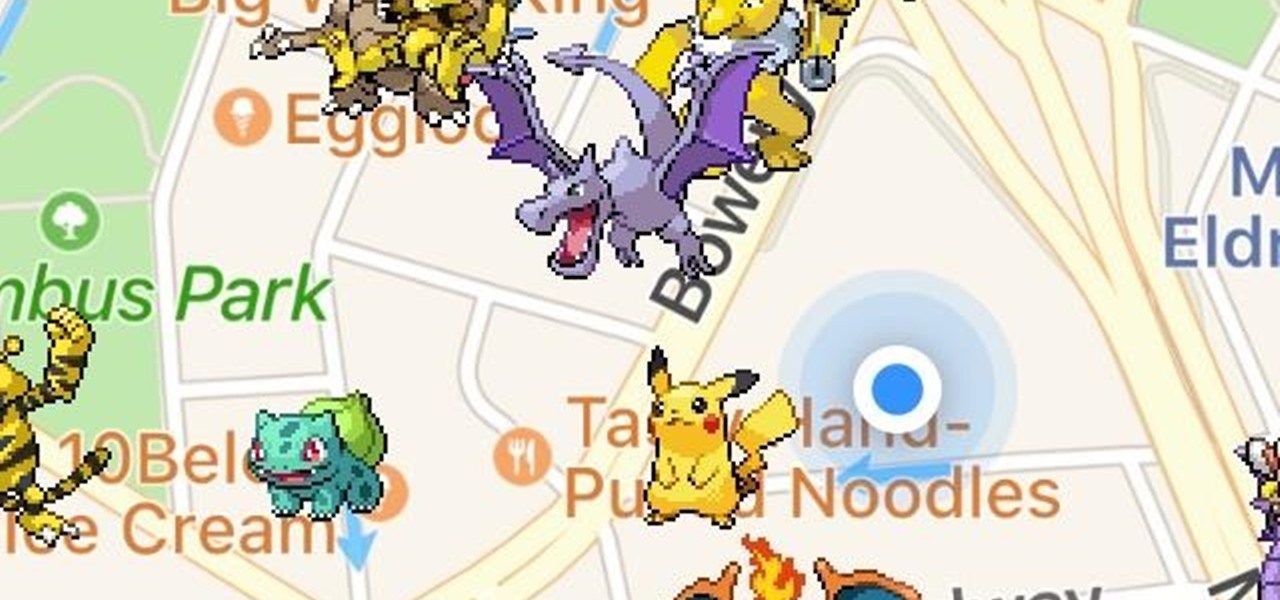
The only way to know which Pokémon are in your area in Pokémon GO is the cryptic "nearby" list, which sometimes doesn't work—and also doesn't tell you which direction to head off to hunt that Pokémon you're looking for.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

Google kicked off I/O 2016 by debuting Assistant, a next-level version of Google Now. While you could search the web by voice before, now you'll be able to have a conversational interaction with Google. In short, it's a smart chat bot.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.

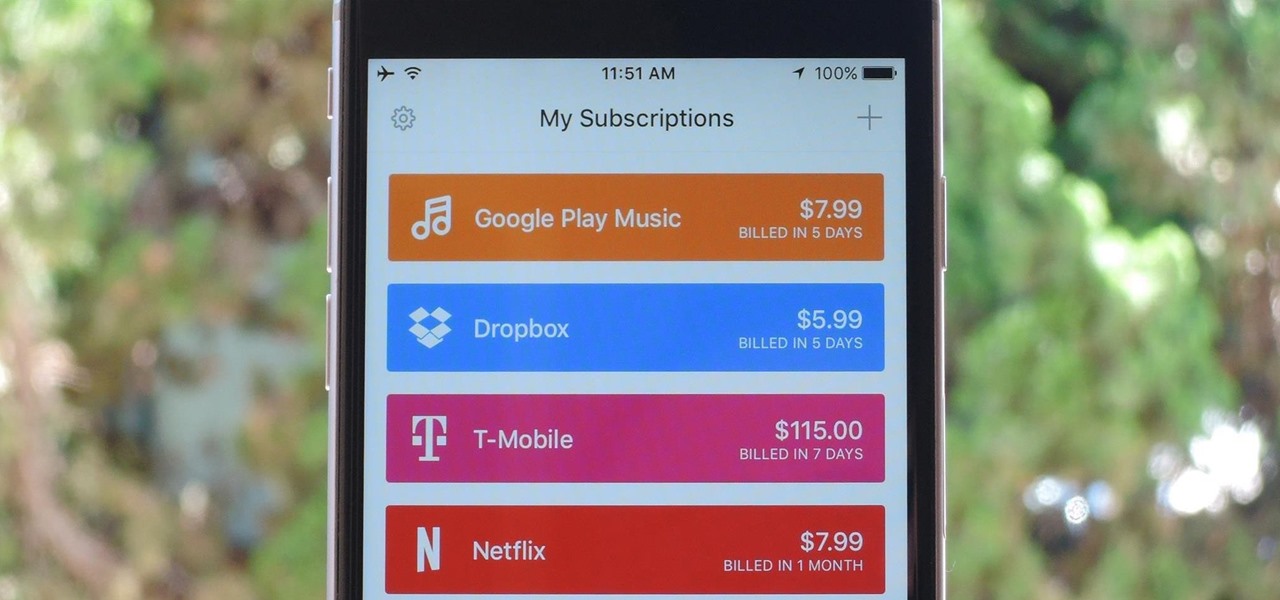
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

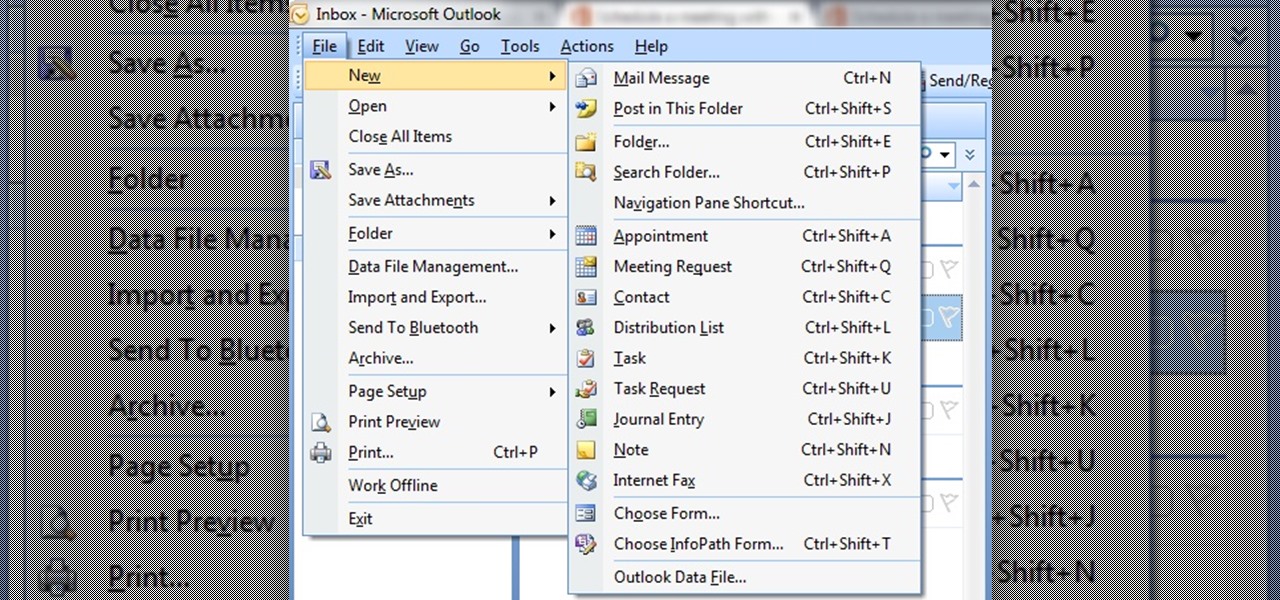
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

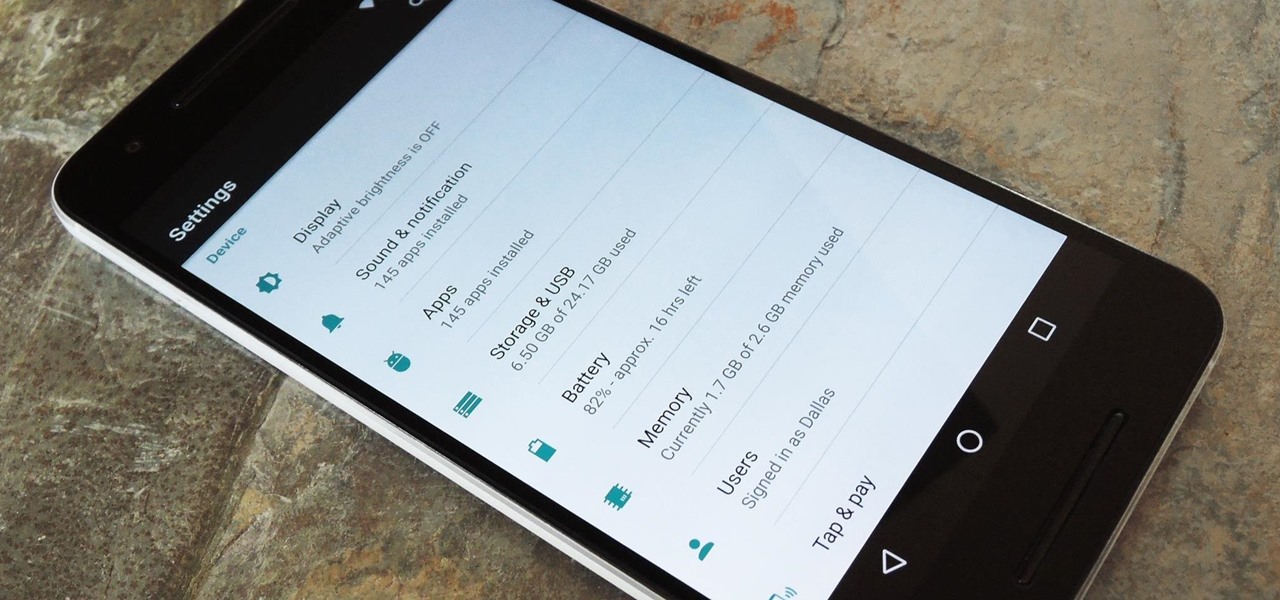
When Android N is officially released sometime later this year, it will bring a lot of cool new features along with it. We've already had the chance to play around with some of these, thanks to a preview build available to Android beta testers, and one change that we like in particular is a revamped Settings menu. Among other things, each settings entry now has subtext beneath it that shows relevant info at a glance.

How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that it's three or four times that amount.

The Google Play Store hosts the largest collection of mobile apps on the planet, and it's the default app store for almost all Android devices. Ironically, though, while Google made its name with a powerful search engine, it can sometimes be difficult to find what you're looking for on the Google Play Store.

Hello there Nullbyte users! This will be my first article here.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Because of Apple's iron grip over iOS, hiding stock applications is a topic we frequently like to cover. While not everyone may think that Apple's preinstalled iOS apps are bloatware, that's exactly what some of them are. For instance, the Apple Watch app; it's basically just an advertisement on your home screen unless you actually have an Apple Watch.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

Live Photos is an interesting new feature introduced by Apple on the iPhone 6S and 6S Plus models that captures the moments immediately before and after you snap a picture in the Camera app, resulting in a GIF-like animation.

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

One of the coolest features in modern smartphones is their Bluetooth connectivity. This is how two digital devices can communicate with one another—sending data like your phone call audio or your favorite song—all while using up minimal battery life.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

One of the highest rated posts on Spotify's own community forum is titled "Add support for Google Chromecast," a clear indicator of not only how much this feature is desired, but also of Spotify's lack of care for it. Remaining consistent with statements made in the past, Spotify is firm in their decision to not pursue Chromecast support at this time—or maybe ever—thanks to a deal with Sonos and Spotify Connect.

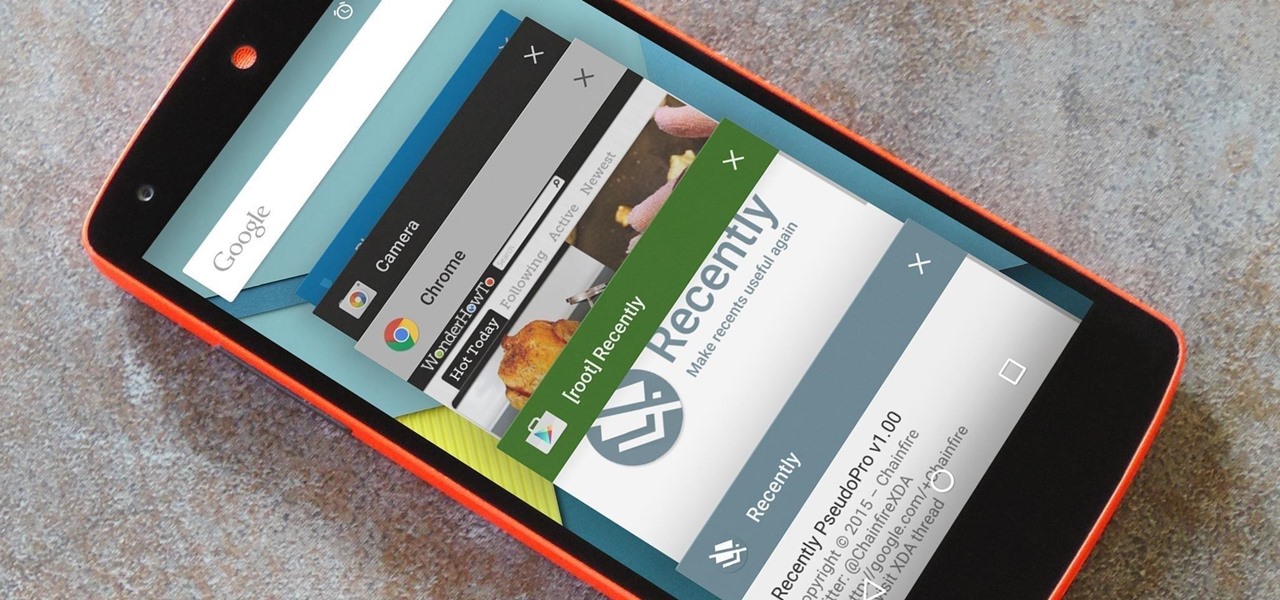
Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

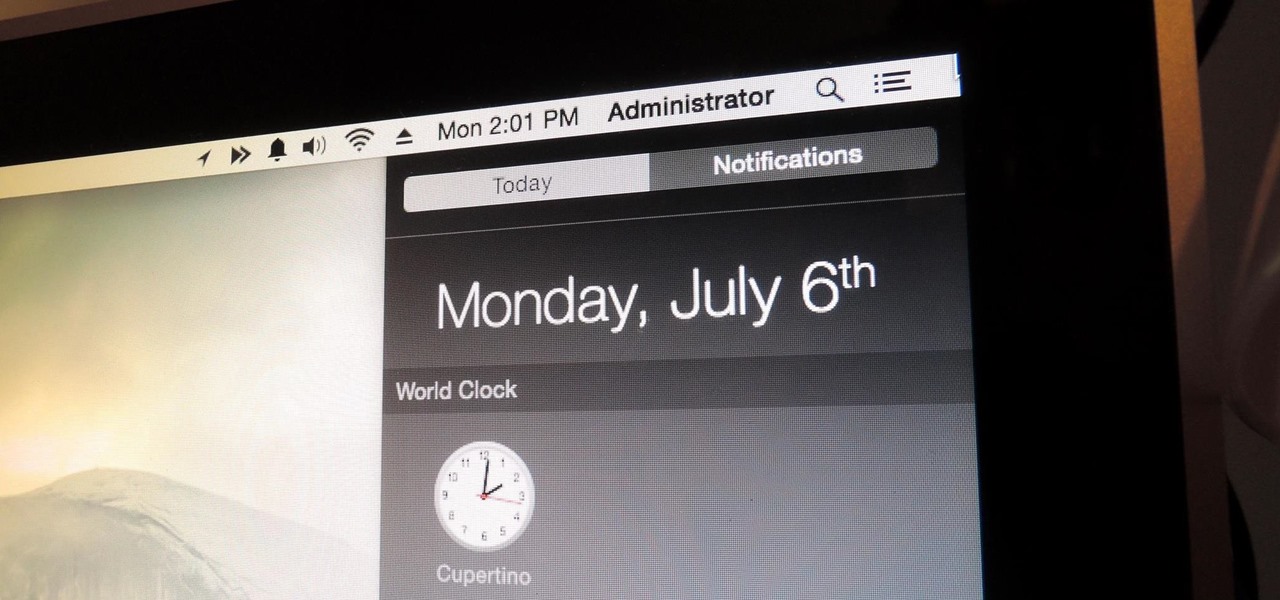
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

The Samsung Galaxy S6 includes a pretty nifty feature known as "Gesture wake up," which lets users wave their hand over their locked display to wake it, making those periodic notification checks from the lock screen a lot more simple than having to press the power or home key every time.

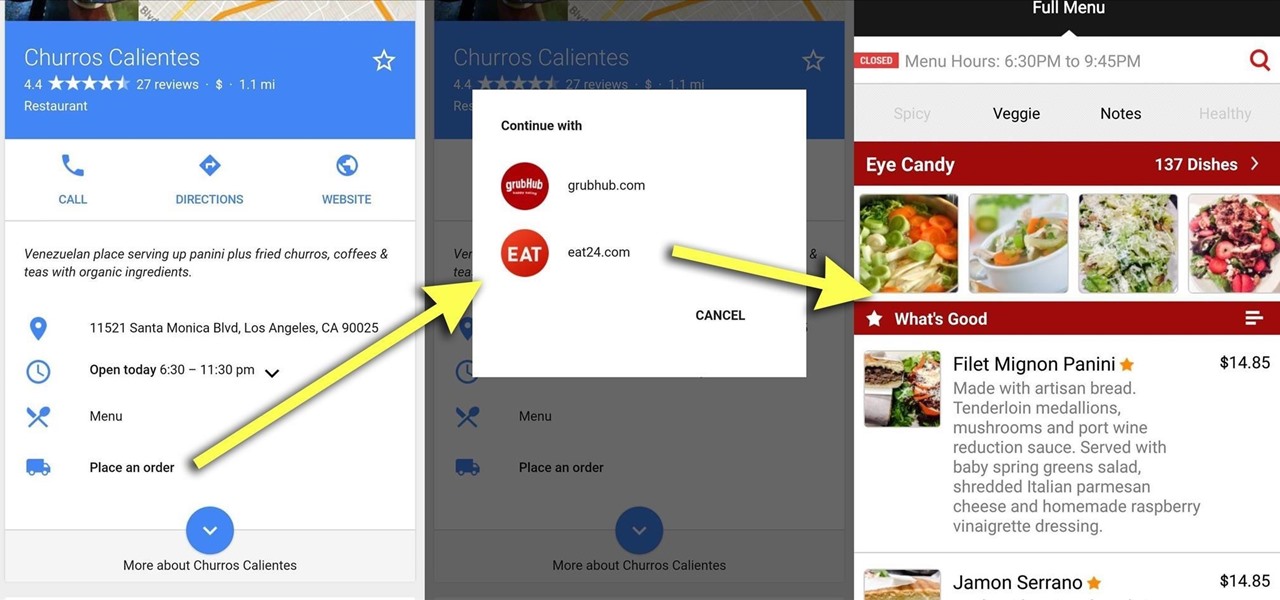
In addition to sharing emojis and GIFs, most of us also probably share various types of links through email or text, whether it be for a Google Maps location, a bar or restaurant on Yelp, or an awesome song on Spotify.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

Google constantly adds useful little features to stay on top of the search engine heap. Recently, we've seen them add "Find my phone" functionality, as well as the ability to set alarms and send directions to your Android phone or tablet.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

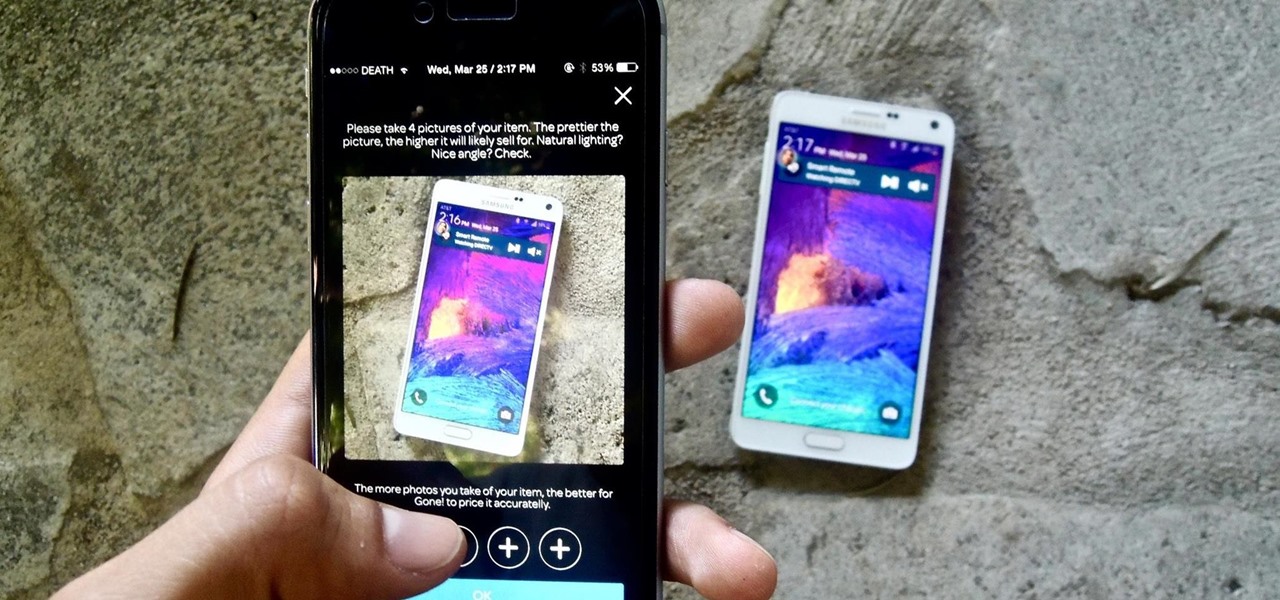
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

Family Feud is one of the longest-running game shows in American TV history. Its viewer base spans generations, and this is mostly due to the fun nature of the show. Contestants have to guess the most popular answers to survey questions that were posed to 100 random strangers, and the responses often range from silly to downright funny.

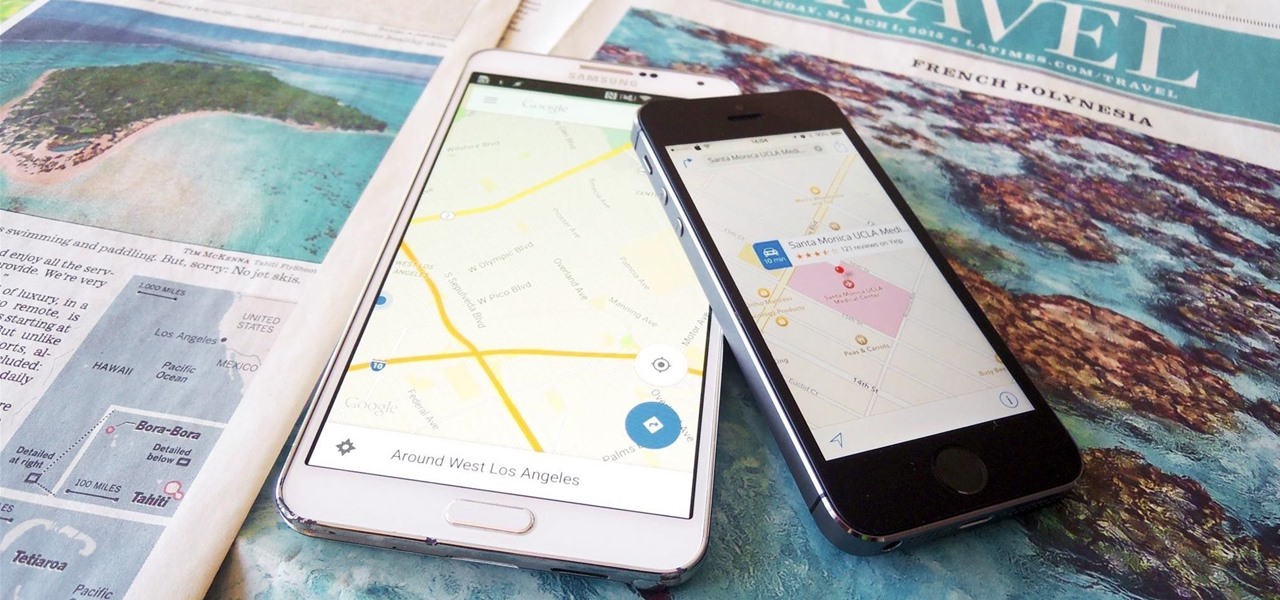
Applications like Apple Maps, Google Maps, and Waze save every location you visit or search for as a way to speed up future searches and to find commonly-frequented places. But what if you go somewhere unsavory and don't want anyone knowing?

As is the case with most software updates, Android 5.0 brought changes that were viewed by users as somewhat positive and somewhat negative. This generally happens because we're accustomed to the old way of doing things, and changes, no matter how useful, can slow us down.