If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.
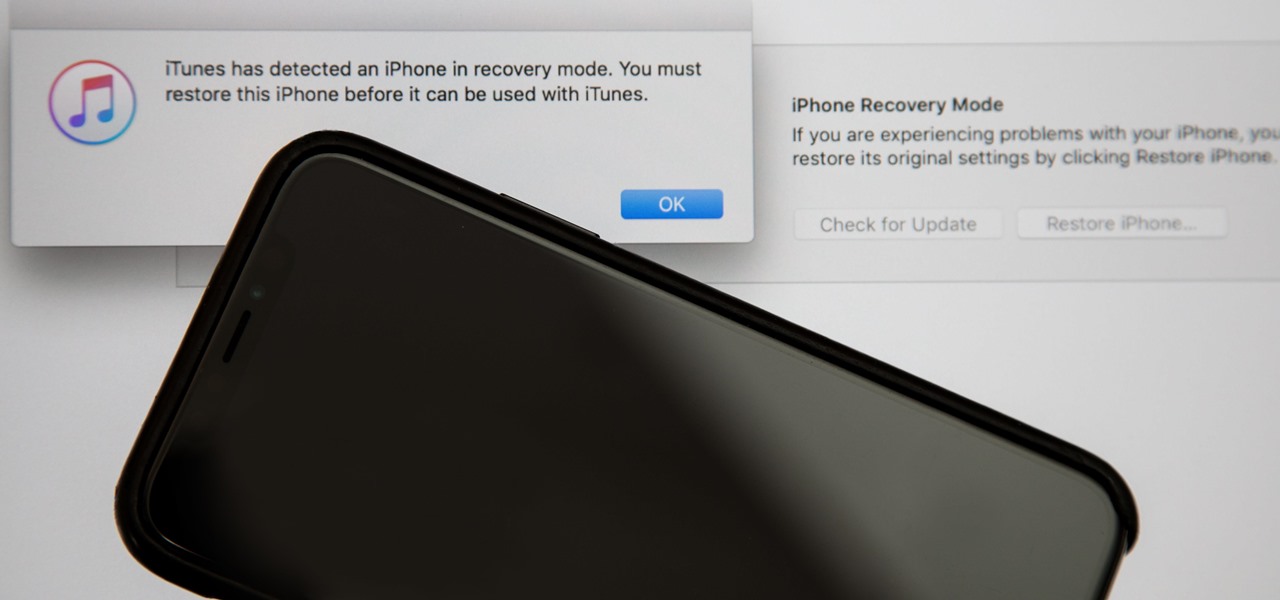
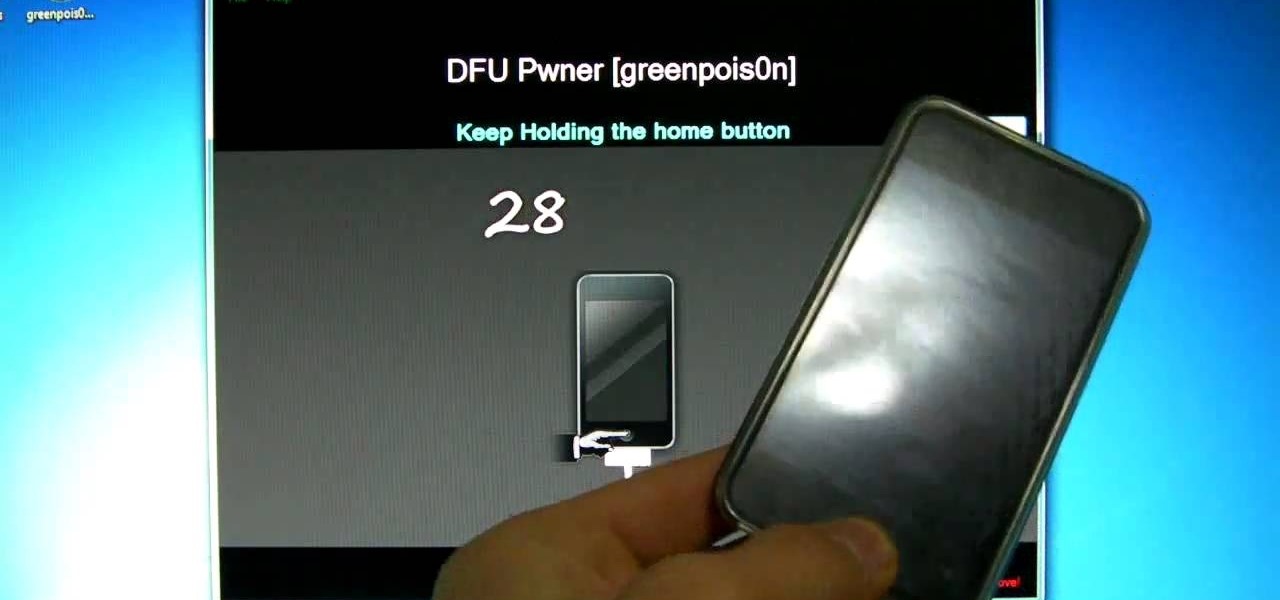
Following in the iPhone X's footsteps, the iPhone XS and XS Max, as well as the iPhone XR, have all ditched the iconic Home button last seen on the iPhone 8 and 8 Plus, which is one giant leap toward Jony Ive's ultimate vision of an iPhone that's a clean slab of glass. However, without the Home button, a lot of tasks have changed, most notably, entering and exiting DFU mode in iTunes.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

After you have registered to this site,sign in then to start missions. Basic Missions

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

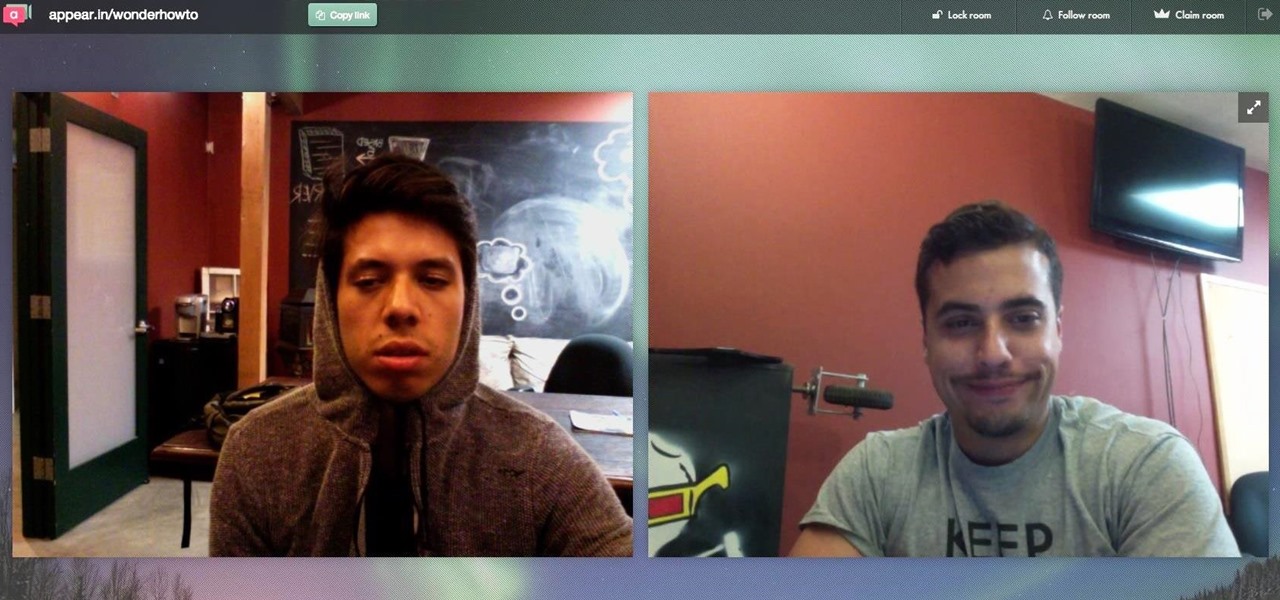
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

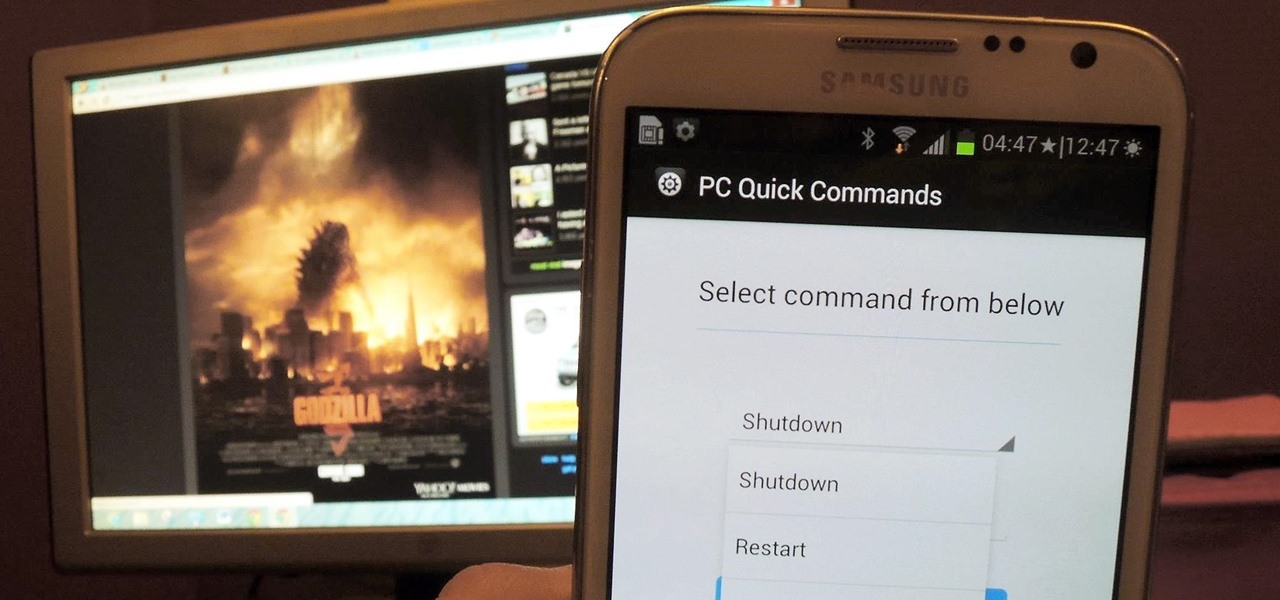
You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

If you've had the pleasure of owning both an iOS and Android device, you may have noticed one subtle difference on each one's PIN unlock screen. Android's lock screen requires you to press "OK" after entering the PIN, whereas iOS's simply unlocks the screen right after the last digit.

If you own an Apple iOS device (iPhone, iPod Touch, iPad) then you probably have the 4.3 firmware update by now. It's got some cool improvements, but as usual necessitates a new jailbreak. Enter Sn0wbreeze 2.3b1, the beta version of the jailbreak for the new iOS. It's in beta, so it's not perfectly stable, but this video will show you how to use it. You can see a written version of the guide and the necessary download links here.

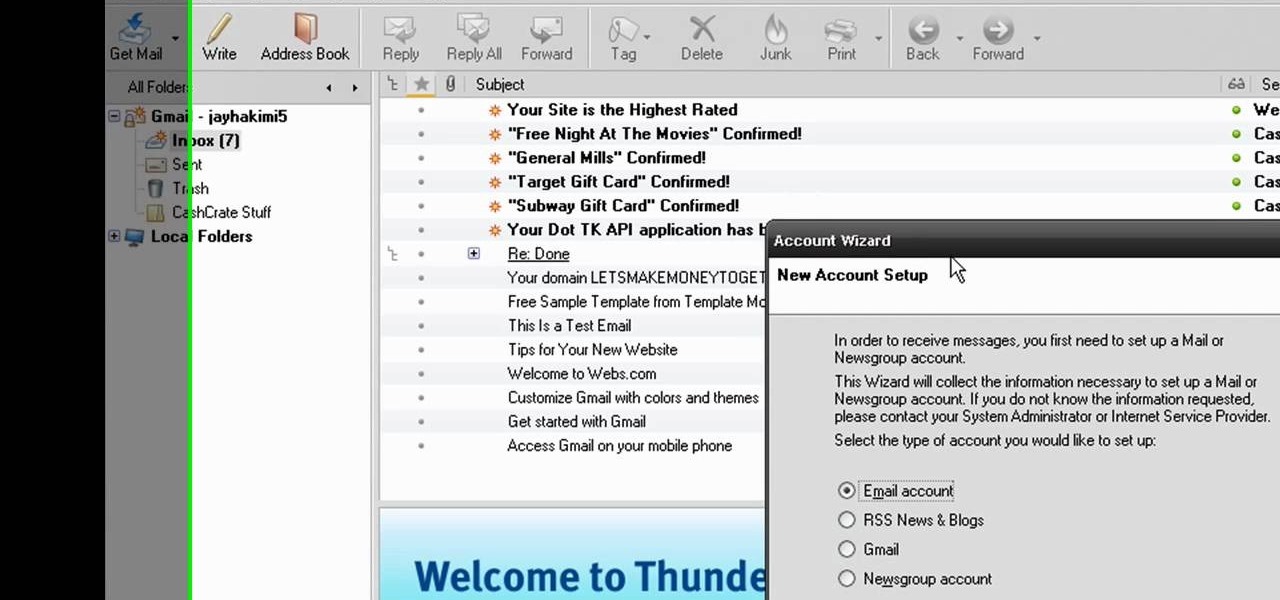
In this video from MegaByteTV we learn how to set up a Gmail account in Mozilla Thunderbird. First go to your browser and download Thunderbird from the Internet. Once downloaded, go to the Thunderbird application. Go to New and Account. Click on Gmail and enter your name and email address. Click Next and check off download messages now and click Finish. Your messages should now appear there. The first time you do this, all of your messages will look new but you can change that. If you'd like ...

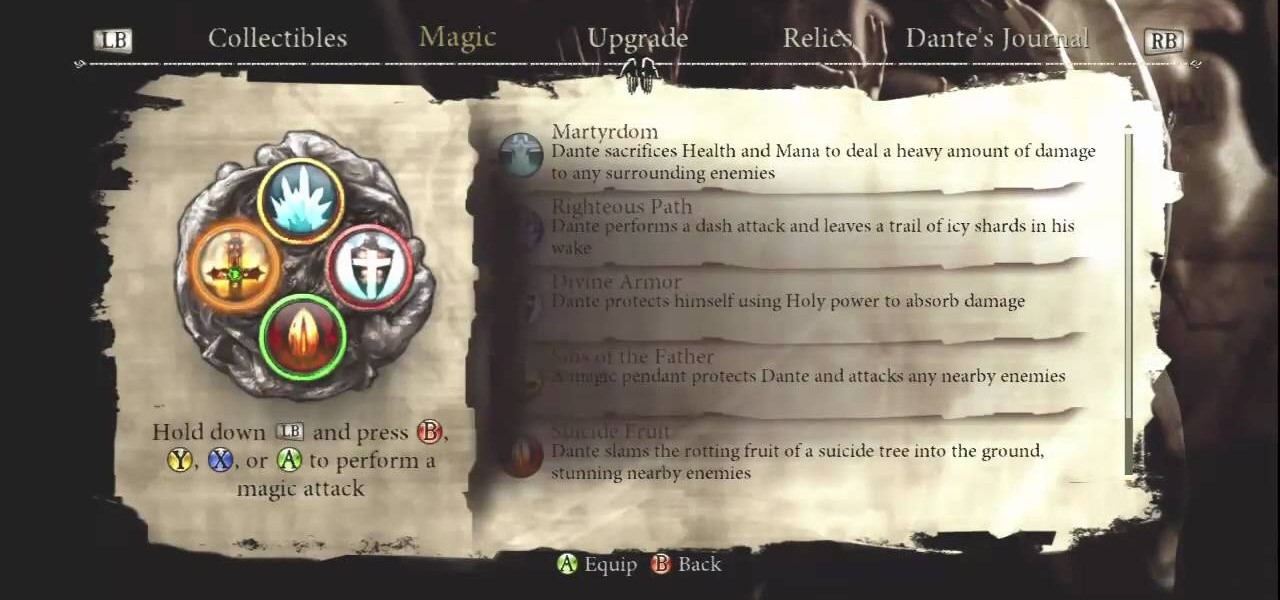
This video will show you how to get the "Poetry in motion" and "Masterpiece" achievements. When you enter the Fraud Circle towards the end of the game, you will be faced with ten challenges on ten levels. The fourth challenge (the save point is Malebolge 4) requires you to stay in the air for eight seconds. Instead of doing this, keep hitting the two demons until you get a 666 hit combo and the "Poetry in Motion" achievement. This can be done easier with the "Coin Of Plutus" and "Wings Of Fur...

Want to make a phone call on an iPhone 4 running Apple's iOS 4.1, but don't know its passcode? Not a problem. In this clip, we learn a simple trick that will allow you to bypass the lock screen entirely and permit you to view the phone's contact list and place phone calls to any number you like. This glitch has been fixed with iOS 4.2, so treasure this hack while it still lasts! This will let you unlock someones password on an ipod or iphone touch.

It's a tired expression that men are dogs and women are cats, but there is definitely some truth to the saying. Women who are feline are a bit stealthy, sexy, and enter a room when THEY want to, not when you want them to. They're very independent and are in tune with their instincts.

Who is the hottest animated female character of all time? We're sure there are lots of differing opinions on that, but we think Jessica Rabbit must be at the top of the list of viable options. With curves so, well, curvy, that they enter the room before she does and eye-catching red hair, the seductress is one hot lady.

Need to protect a section of your overall flash content (say movie or slideshow) from unauthorized access, learn how to do so in this video.

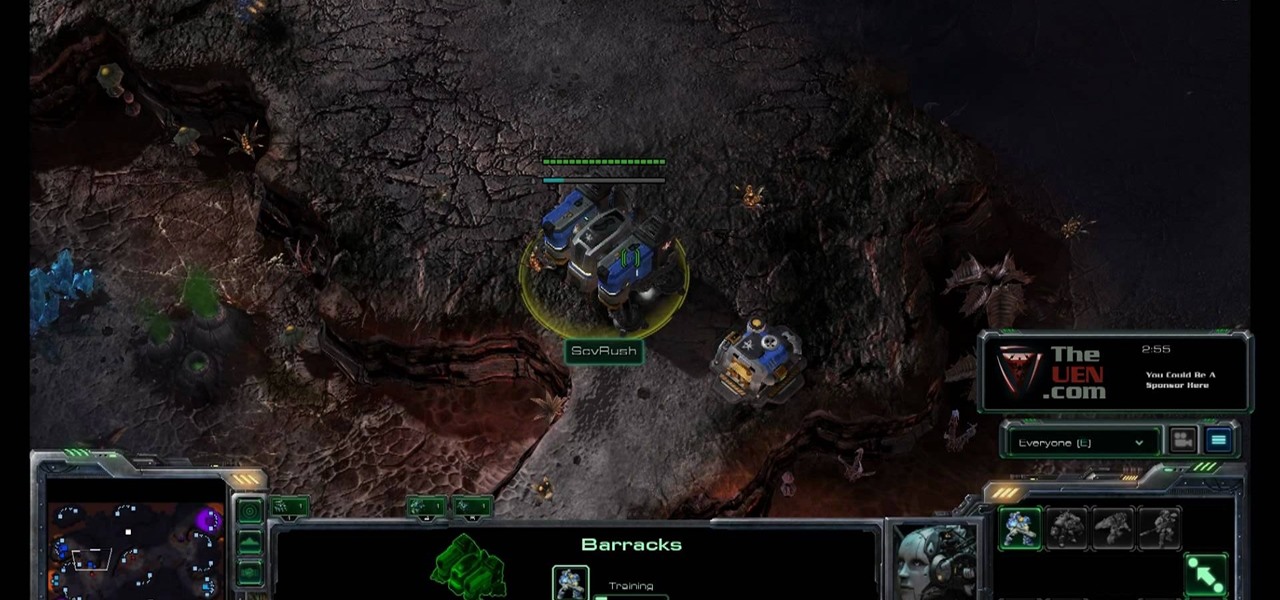
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to you can make a mobile wall of supply depots on your Terran base's...

In this video tutorial, viewers learn how to quickly troubleshoot memory problems in Windows. Begin by clicking on the Start menu. Type "mdsched" into the search bar and press Enter. The Windows Memory Diagnostic window will then appear. Click on "Restart now and check for problems". Your machine will then be rebooted and will run its memory diagnostics tool. It will look for any issues that may cause problems for your system. Advanced users can press F1 when it starts to specify certain opti...

If you just got a new Android mobile phone, then chances are, the first thing you're going to want to set up is your email account, so you have instant access to your emails all the time, everywhere and anywhere. Setting up your specific email account or accounts is actually not hard. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up an email account on an Android cell phone.

Are you in college? Too lazy to make a proper meal? Too cheap or poor to go out to dinner? But, still have that sophisticated pallet, this video will show you exactly how to eat like your in beautiful Mexico and make tasty fish tacos in the microwave, to enjoy any night of week. Don't be afraid to enter the kitchen, after watching this video you'll be eager to have dinner guest.

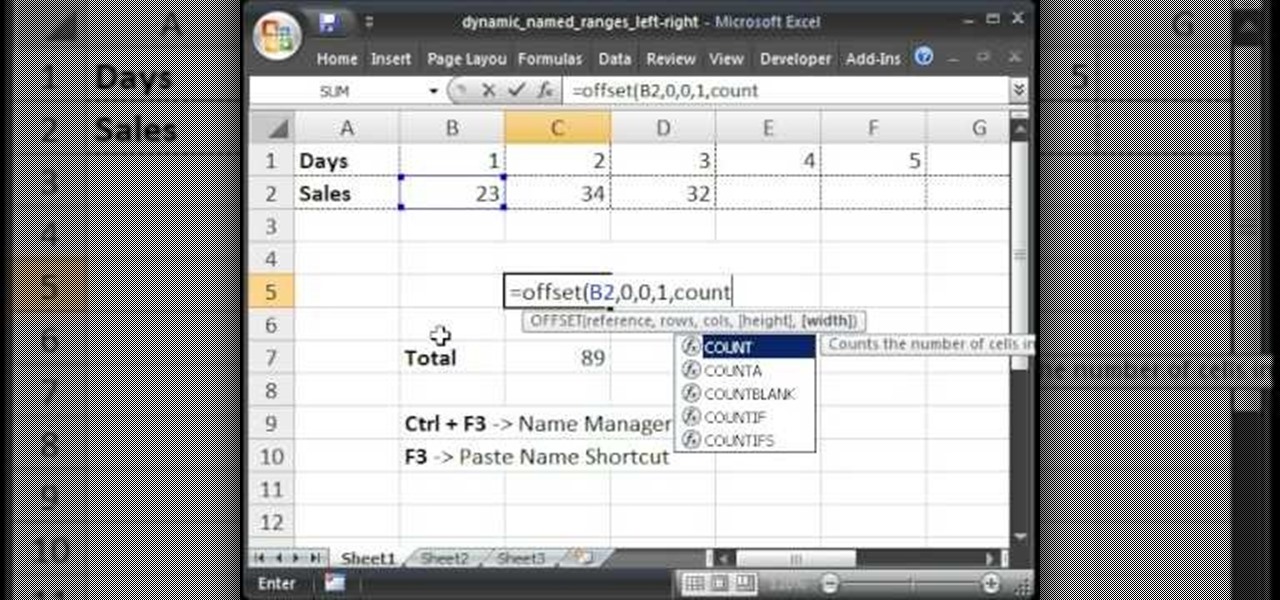
Teach Excel describes how to create a dynamically updating named range that goes from left to right using Excel. First, you define the named range by highlighting the cells containing numbers in a certain row. In the name box to the left of the formula bar, type the name of the data. In this example, the numbers correspond to sales, so type "sales." To check if the named range works, click on an empty cell and enter =sum(sales). That should return the sum of the highlighted cells. However, as...

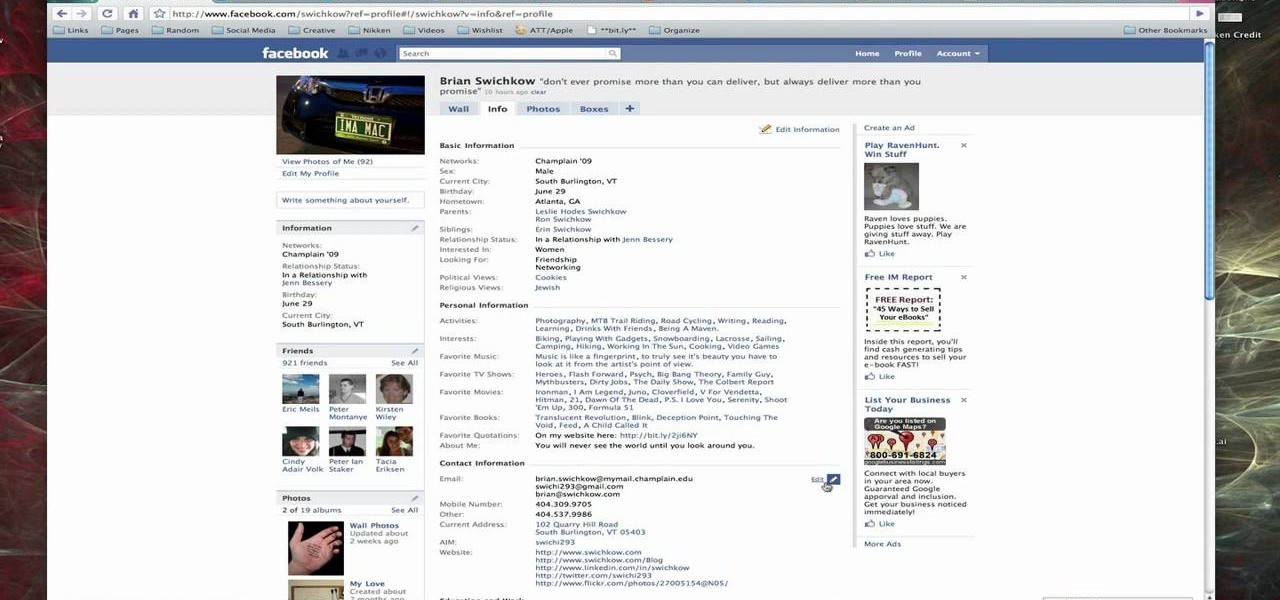
When you register for a new Facebook account you enter your profile details. How ever these profile details can later be changed by editing them. To do this go to your Facebook home page. Open the link that says view my profile which is located beside your picture. You can also click on your name or your picture. This takes up your profile page. At the top you can see boxes which are links to various pages like info, photos etc. Open the info box and there you can see your profile information...

In this how-to video, you will learn how to send an update to the fans on your Facebook fan page. First, go to your fan page. Go to the top and press edit page. Now, click send an update to fans. Now, click edit to change who will receive this update. This includes sending it according to gender or location. Enter the subject and message of the fan page. Click send to complete the process. This update will be shown in the sub category in the messages page called updates. Click it to read the ...

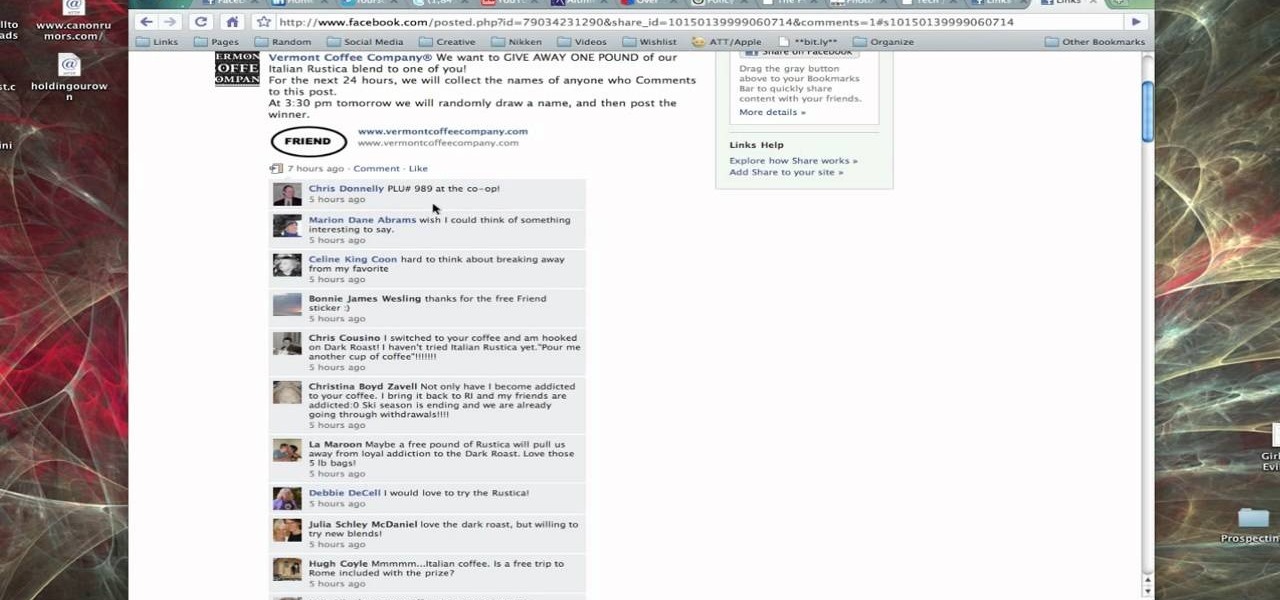
In this tutorial, Brian from TruTricks shows us an example of what Facebook can do to promote your business! One of the best ways to do this is to do micro giveaways on your Facebook. You don't have to give away something big, just something small that gives people incentive to post on your page and become a fan of your business! You will be able to see what people are posting on the page as well as everyone that is entered in your contest. This giveaway has given all the fans reason to parti...

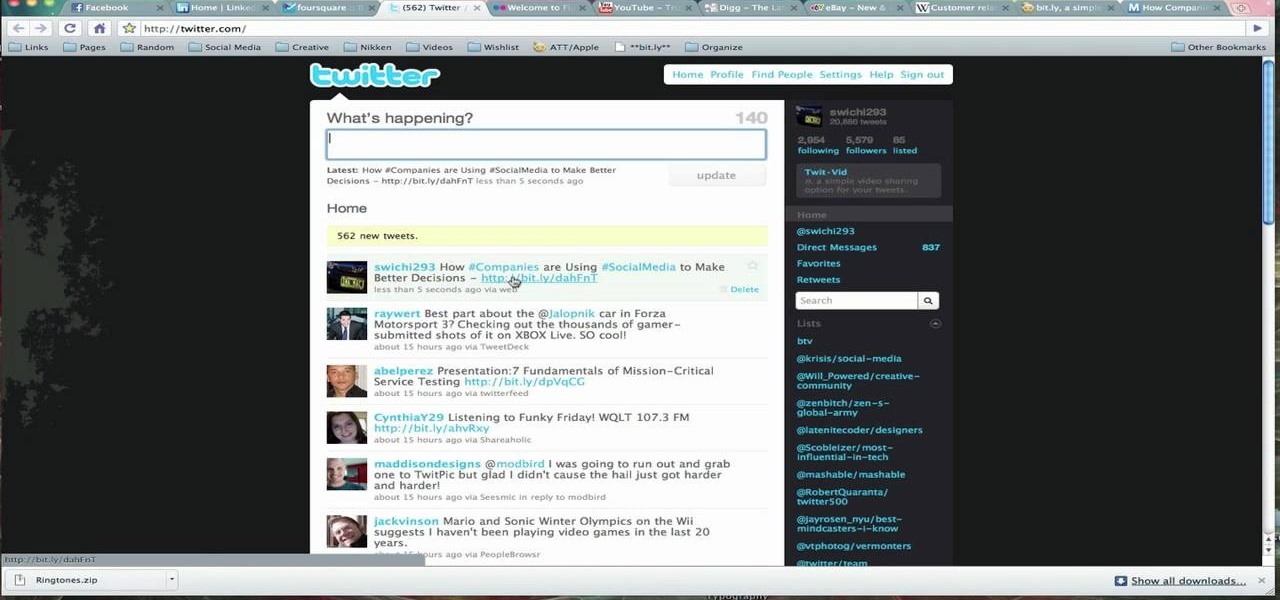
In this video, Brian from Trutricks shows us how to create a new Twitter account. First, go to Twitter and click on the "sign up now" button. You will now be brought to a new page where you can choose your user name and enter your email, password and full name into the information boxes. Once finished, click "create account". After this, you will be able to follow people you want as well as have other people follow you. Once you are ready to tweet you can type whatever is on your mind in 140 ...

Link shortening is the process of cleaning up the URL link which is long and converting it into a short URL. You can use bit.ly to do link shortening. Using bit.ly you can not only shorten the link but also track the users who are using those links. To use this service go to the http://www.bit.ly website. There in the home page you are provided with a text box. Enter your long link in the text box and submit it. Now the website converts the long URL and provides you with a short link which ca...

In this video, you'll see how and why wax can be a deadly. This is how it works,When the test tube is submerged in cold water, the glass forms tiny cracks. The Water enters gets into the tube and vaporizes causing a micro explosion. The hot wax is then ejected from the tube quickly as oxygen is displaced from the tube itself. Be careful, and make sure to be as safe as possible when trying this experiment at home.

This video shows you how to do a mathematical representation on computing the nCr function using a TI-89 calculator. You can write the nCr notation in different forms. It can be simplified from nCr to C(n,r). The symbol can either be read "n choose r" or "n taken r at a time" which are from it's probability applications. On the example to find "26 choose 17", go to the Home screen of the TI-89 calculator and then go 2nd 5 which is Math. Go choose probability and then to nCr to type in (26,17)...