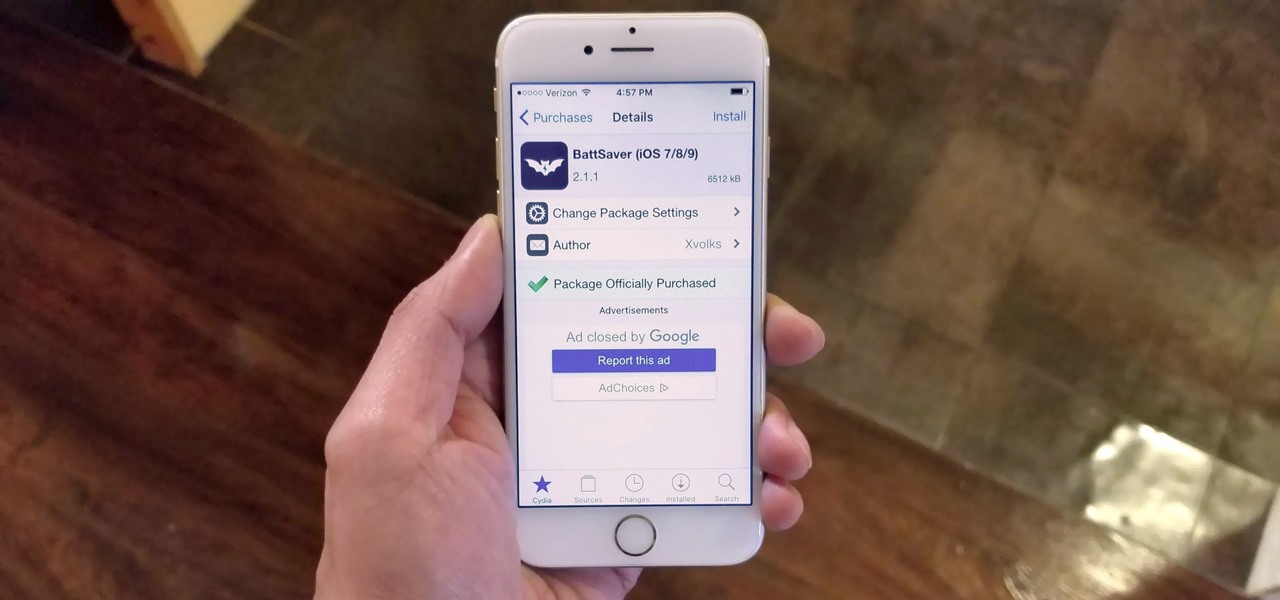
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.
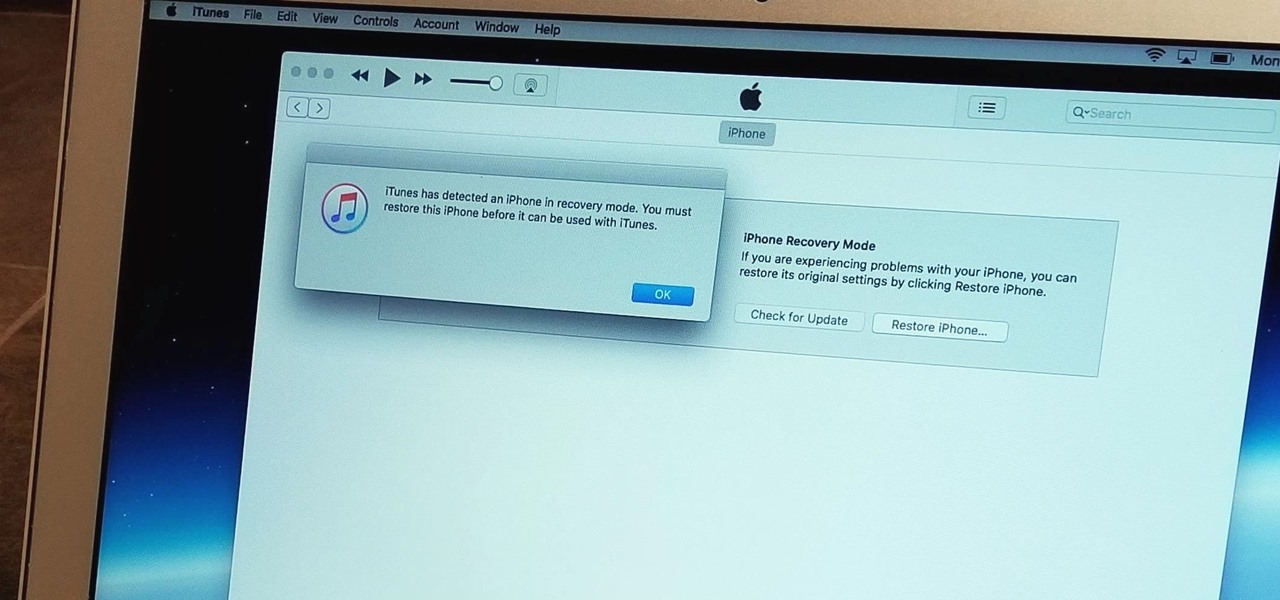
With the iPhone 8, 8 Plus, and the exclusive iPhone X, Apple has come full circle in transitioning its users away from the home button present since the first iPhone a decade ago. This gives us a window into Apple's design philosophy moving forward, but it also presents some new problems, especially when it comes to entering and exiting DFU mode in iTunes.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

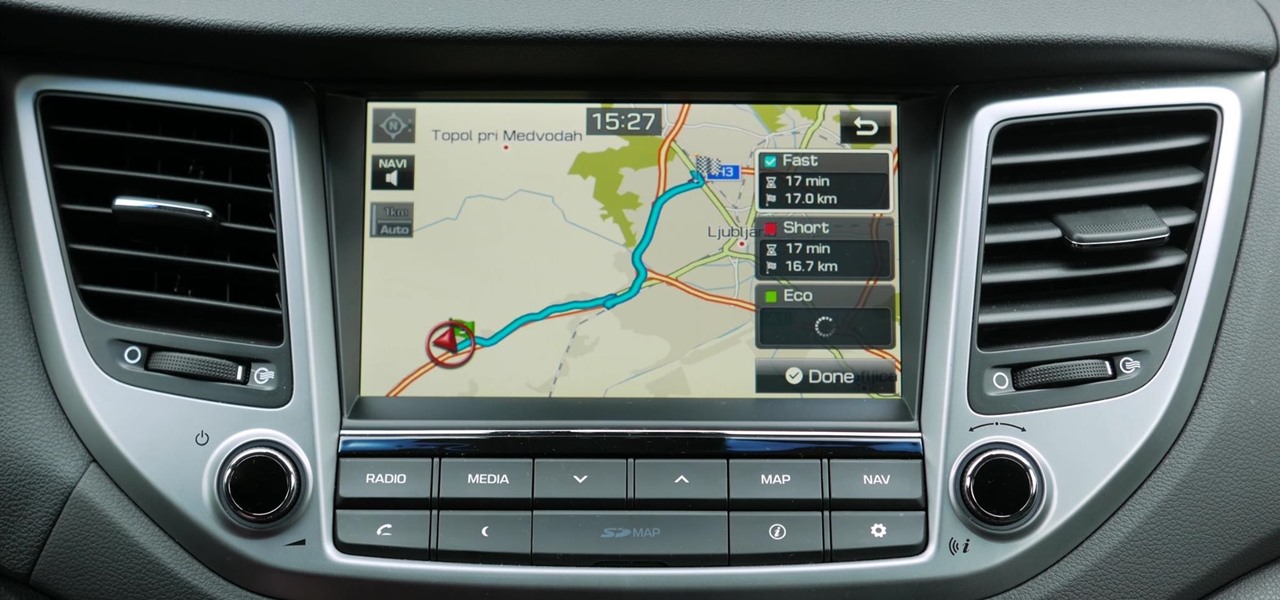
How to enter an address in the navigation (infotainment) system in a Hyundai Tucson (2015–2016 model, formerly known as ix35) as well as other Hyundai models with similar systems.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Catching up with Windows 8, Apple has finally included a way in Mac OS X to use two apps side by side in full screen view. In the 10.11 El Capitan update, it's called Split View, and it works fairly well for the most part. It's not quite as intuitive as it should be, but easy enough once you get the hang of it.

If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

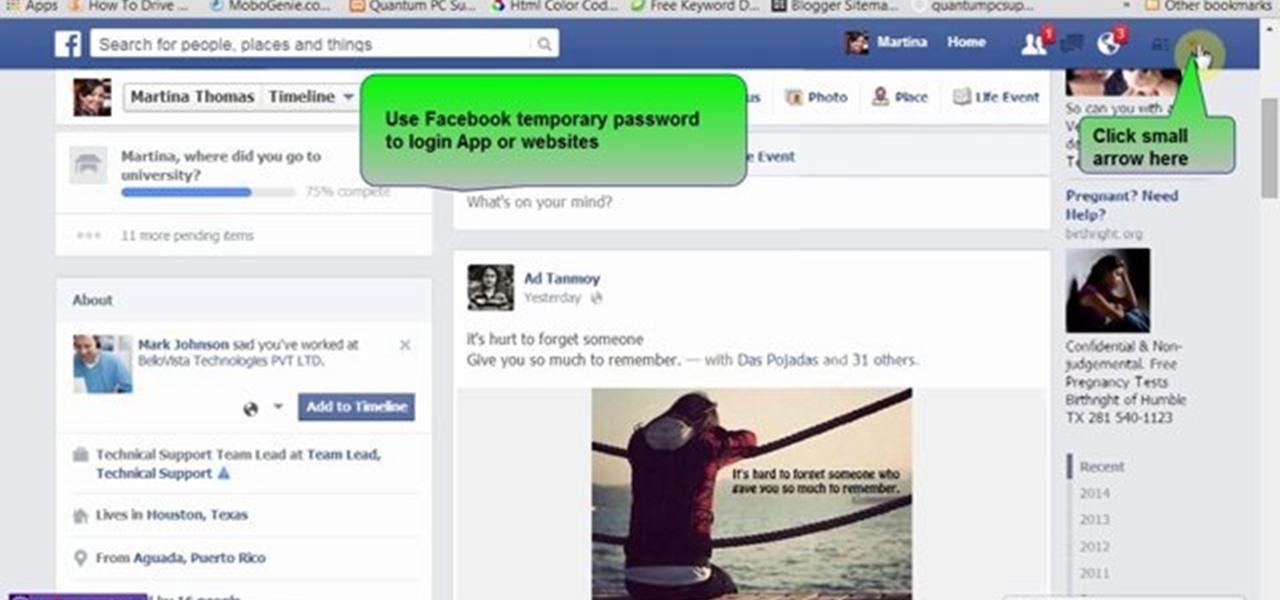
Many people use Facebook login detail to enter different apps or websites. This is somehow dangerous because unethical websites or apps may use your Facebook detail. So to avoid this warning Facebook is generating a temporary password for you. Now you could use this detail to login app or websites. You don't have to use your Facebook original login detail.

The newest version of iOS 8 beta is now out. Almost three weeks ago, in the iOS 8 beta 2 release, we saw podcast integration, full-screen caller ID, new assistive touch toggles, and a "disable all" button for app notifications, among other things.

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

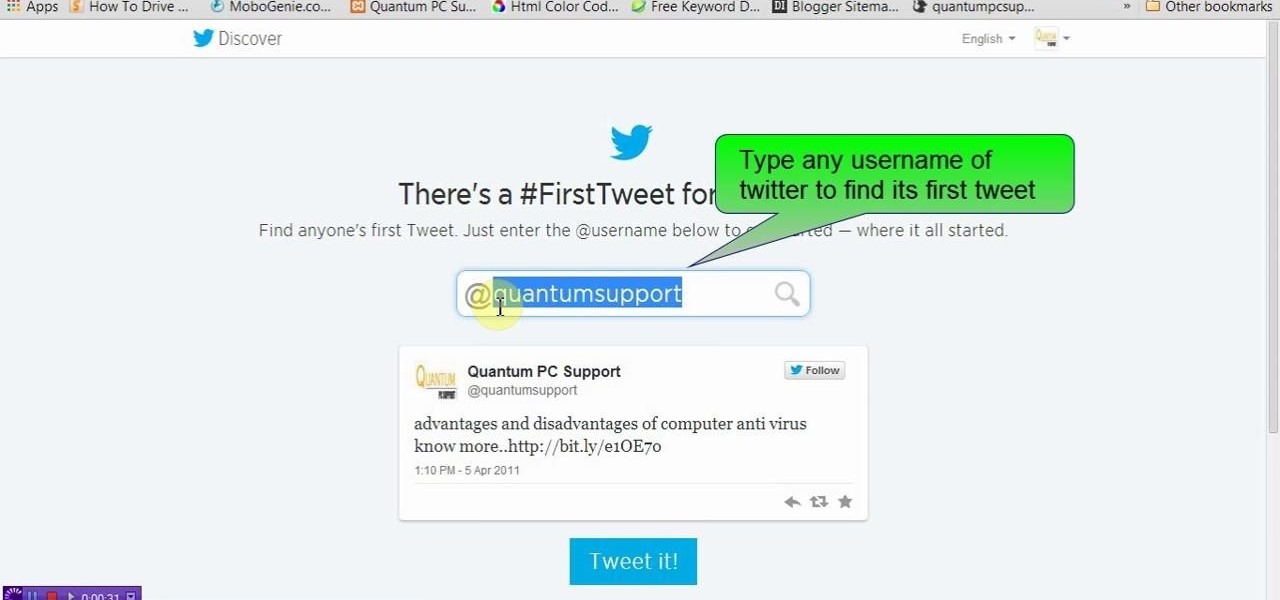
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

Autocorrect, a common feature available on most Android keyboards, helps fix fat-finger typos and even predicts the words you want to write. Without this feature, it'd take me about 5 minutes to write a sentence, and even then, it'd probably still be intelligible.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.

This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.

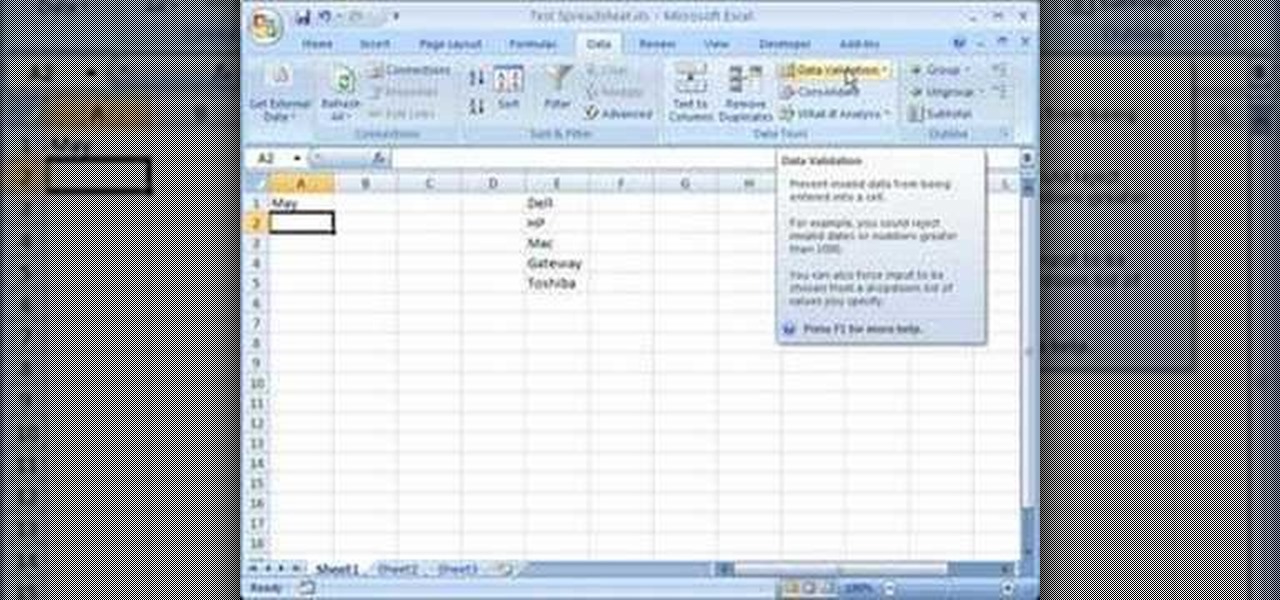
This video is a tutorial on how to create drop-down menus in Excel 2007. Select a cell on your spreadsheet and click on the “Data” tab. Go to the “Data Tools” section and select “Data Validation”. In the window that opens select "Allow" and choose "List". You will create a list of the values you want to allow. Type in the values, separated by commas, and click OK. Now you will see your selected cell has an icon to right that indicates there is a drop-down menu containing the value...

If you want to learn how to do the Water Polo Position Drills this is for you. The water polo swimming position is important because it allows you to quickly and easily change your support in the water with little head movement. When you are swimming make sure that you are high in the water. When swimming make sure that there is a 180 degree parallel cycling. When the entry hand is about to enter the water the exiting hand should be about to exit. When the entry hand enters the water the exit...

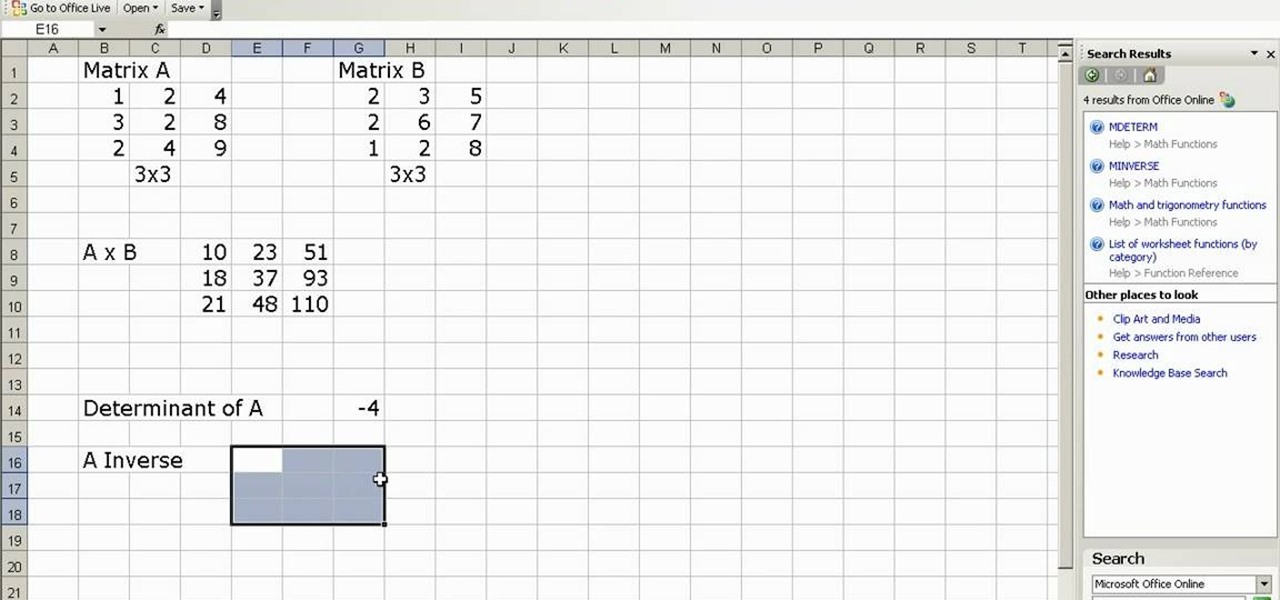
This is a video about the multiplication, determination, and inverse of matrix using excel. First we have to take two matrix in excel. If you take two 3x3 matrices and multiply it then you will get a 3x3 matrix as a result. First we have to select 3x3 cells in the excel and give then a formula of =mmult(and then select the first matrix it will automatically takes the row and cell numbers, next select the second matrix). Then it will give the answer. Next if you want to find the determinant of...

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

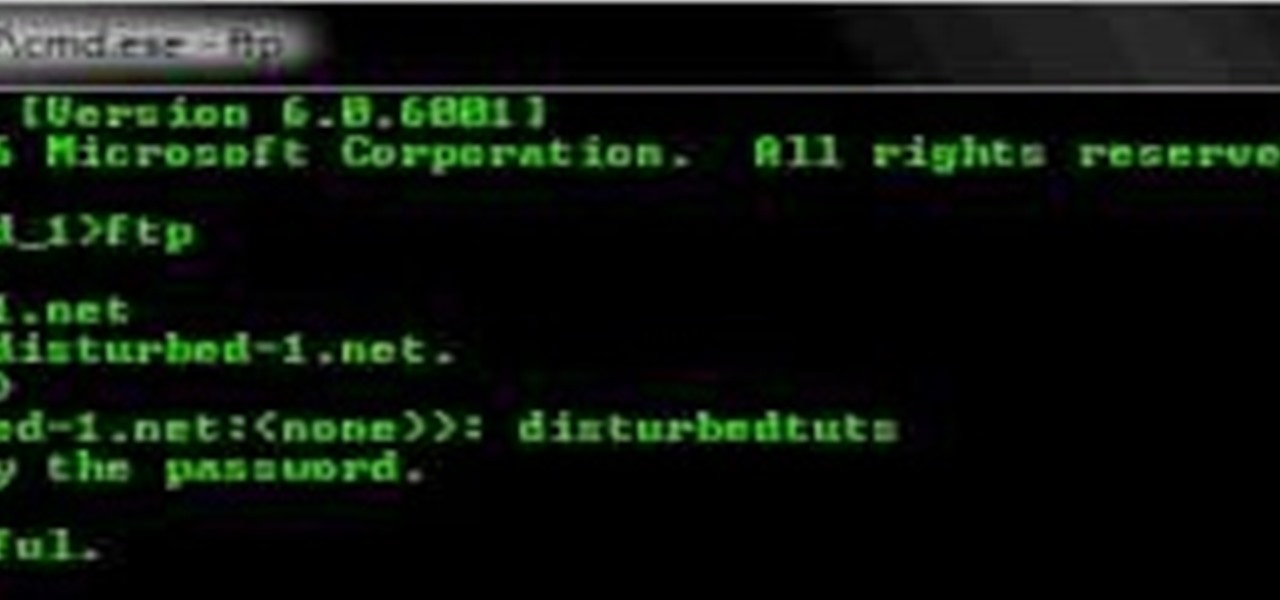
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server. Next type in the server name you want to connect to. Now you will need the authentication credentials to connect to the server. First enter the user name and then the password. Up on successful log in it shows the same...

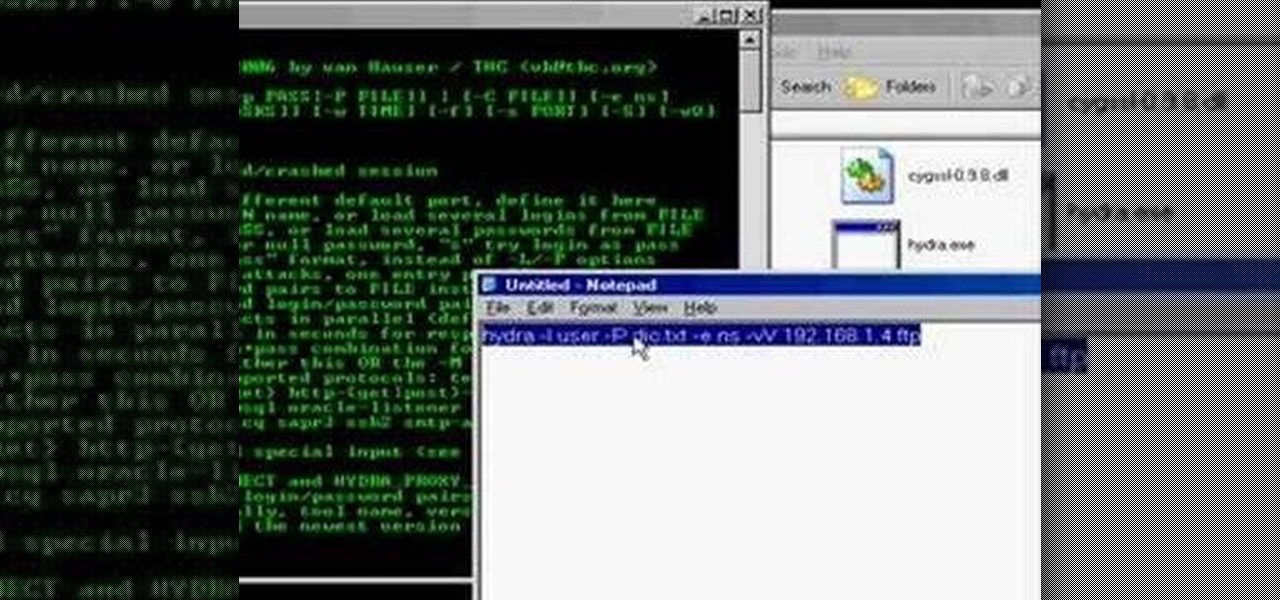
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

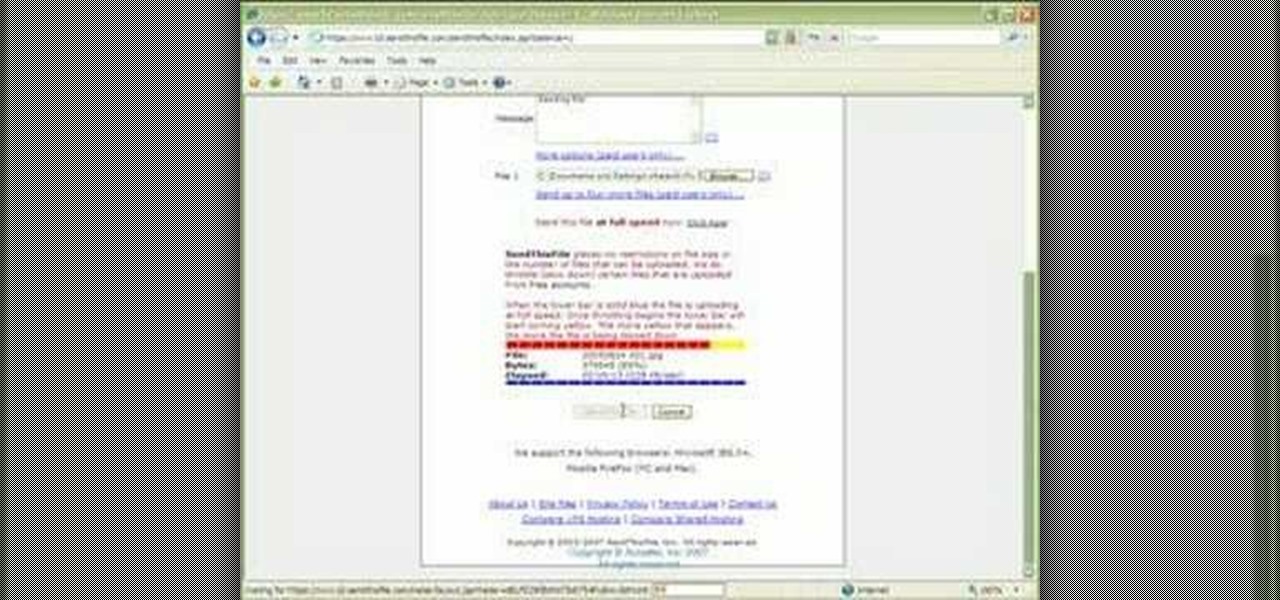
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...

First of all create a website. Go to 'file' and then click 'new'. Choose it as ‘general’ and then as 'empty'. Name this as 'practice site'. Click 'ok'. Now create your first webpage. Click on 'general', 'html' and then 'ok'. Now click on the 'file ' and then choose 'ccs' to create an external style website. This is basically a text file given a '.css' extension. Now click 'ok'. Now go back to your 'html' page and then 'save' it. Now you have to type in 'index' to replace 'default', and th...

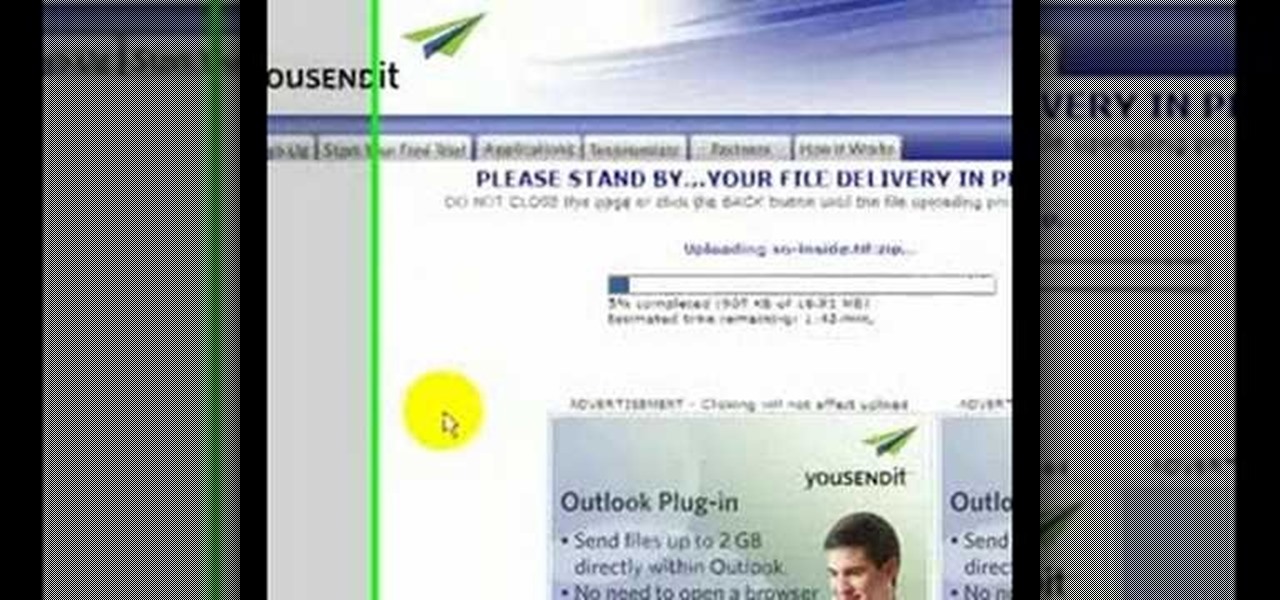
This video shows you how to use the online file delivery service YouSenditIt.com to send a file to someone. There are two ways to do this. One is to register for an account and send a file, and the other is to do it directly from the interface that you'll find on the website. You don't have to register, but generally if your file is going to be larger than 20 MB the person on the receiving end will need to register. But in this video we're shown how to send a file from the interface you're pr...

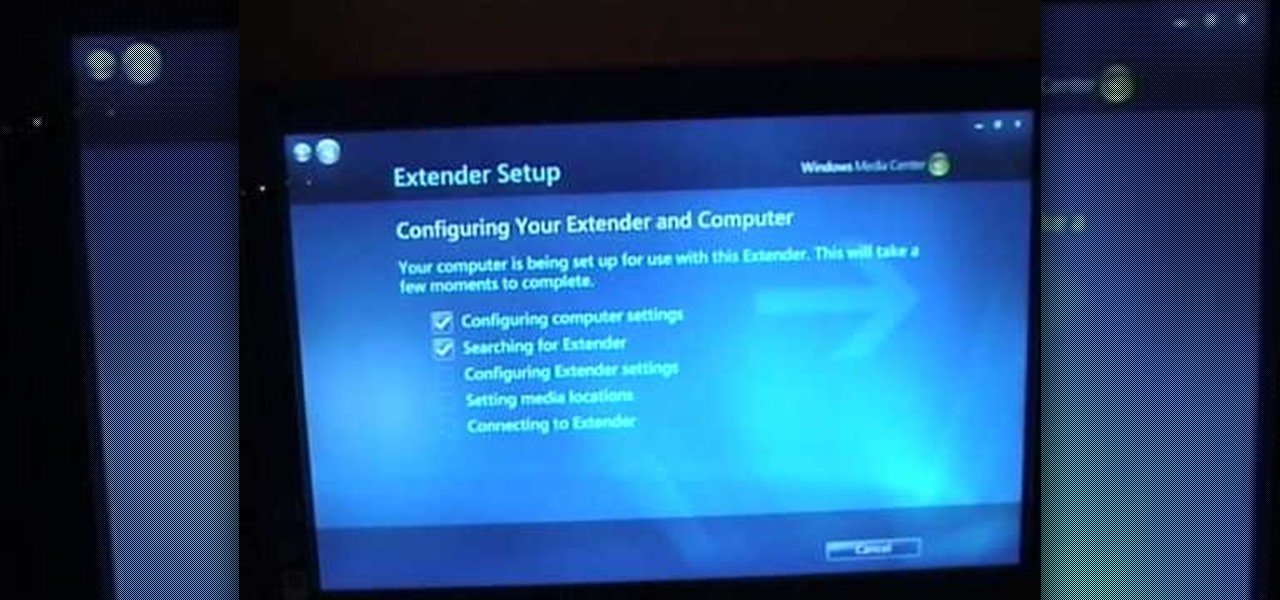
With Windows Media Center, you will have the ability to watch videos, live TV, and listen to music on the XBOX 360 without having to use your computer. You’ll need to have the following things: A PC equipped with Windows Media Center, your XBOX 360, and a fully functional high speed home network. On certain Windows 7 or Vista machines, Media Center is already included. (If not, it can be downloaded from Microsoft) A wired network is preferred for the best connection, although a wireless netwo...

Check out this awesome tip from CNET on getting FREE eBooks of the web and onto your Amazon Kindle for easy and cheap reading. They show you the exact process for getting free ebooks for your Kindle, so watch and learn. It's worth it!

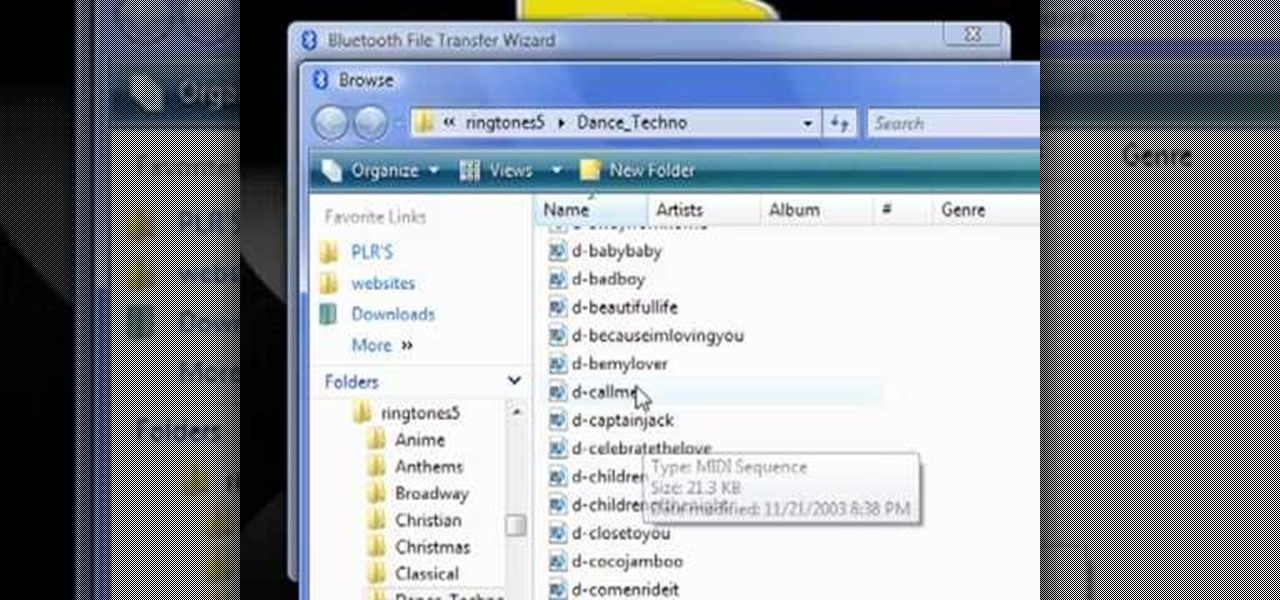
The video demonstrates how to connect your Bluetooth phone to your computer and send/receive files between them through Bluetooth. You need to first switch on Bluetooth in your phone and then click on the icon for Bluetooth connectivity in the computer. Then click on the option called 'Add a Bluetooth Device'. You can see a setup wizard pop up in your computer screen where you have click on the check box and then click on Next button. Once the phone is detected, select it and click on Next. T...

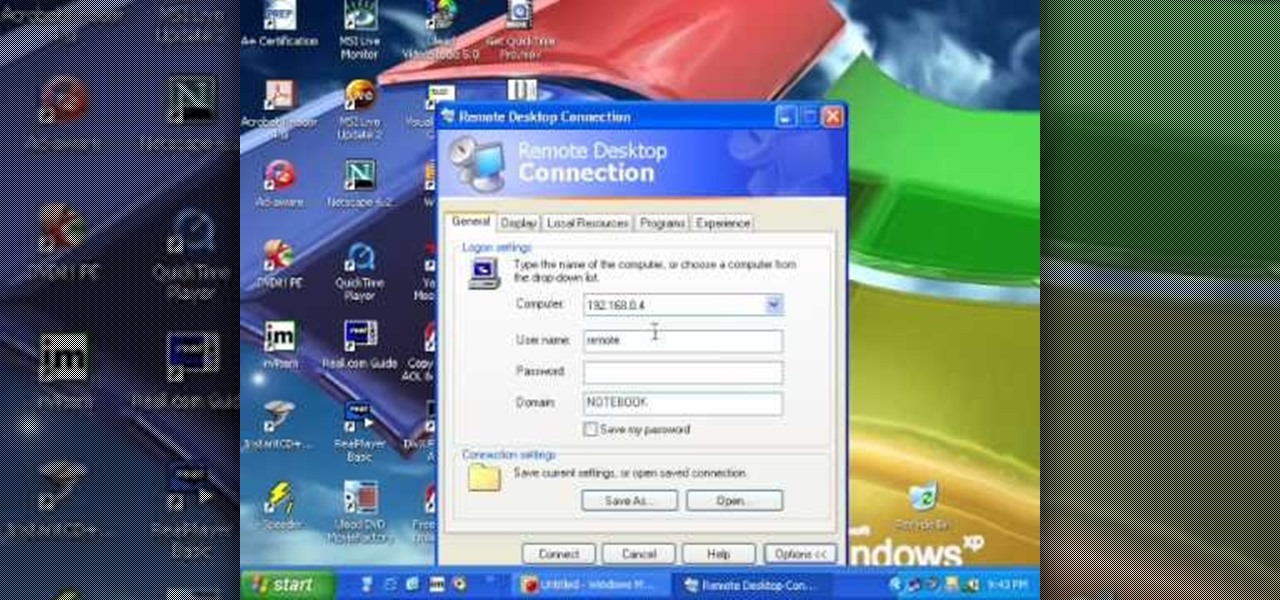
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

This video presents how to connect to your iPod Touch or iPhone using SSH (Secure Shell) without using Wi-Fi connection.

To start with you have to write the author's name, with the last name entered first followed by first name and then the period. Title of the article should be in quotation marks. Do not use italic format. Title of the actual journal must be written. After this there is a series of numbers the volume number, issue, year, pages number separated by a colon. Don’t write 'p' for pages as the number itself is a standard for it. Write the period and also the dates.