The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.
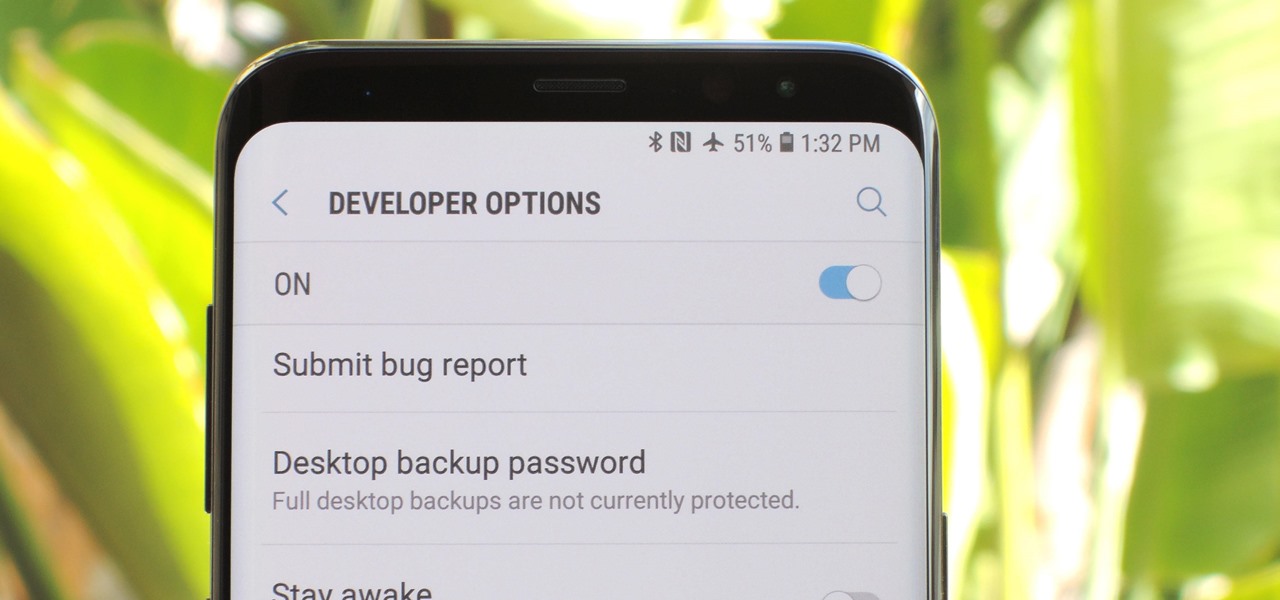
You don't need to have a fully modded and rooted Galaxy S9 to appreciate what developer options brings to the table. Besides the obvious USB debugging, which lets you use ADB, this hidden menu lets you tweak your phone's animations or change its DPI to better suit your needs — and that's just the tip of the iceberg.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone.

Apple likes to make their products simple. However, sometimes that simplicity leads to a confusing user-experience. Take the Apple TV, for example. How do you turn it off? Just press the power button, right? Sorry, there is no power button. Okay, so it's like an iPhone and has a nondescript button designated as a power button, right? Nope.

The Augmented World Expo or AWE — if you are a big fan of AR/MR technology, that is a very fitting acronym — is the world's largest conferences dedicated to all things augmented, mixed and virtual reality. AWE is in its 8th year, and with the massive growth we have seen in the space over the last year, promises to be its biggest year yet.

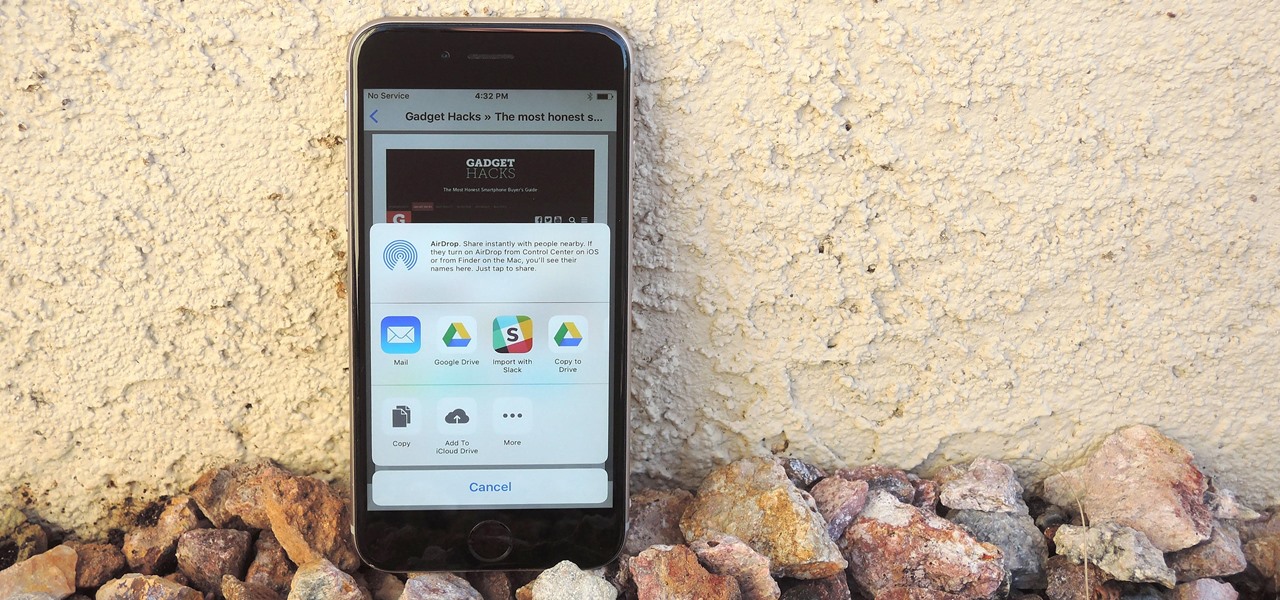
Apple lets you save webpages as PDF files in iOS 10, but the only obvious way to do this is by using iBooks. The thing is, most people would probably rather save their PDFs to a service like Google Drive or Dropbox to make sharing a bit easier. Plus, iBooks isn't officially available for Windows or Android, so there are some cross-platform problems there, too.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

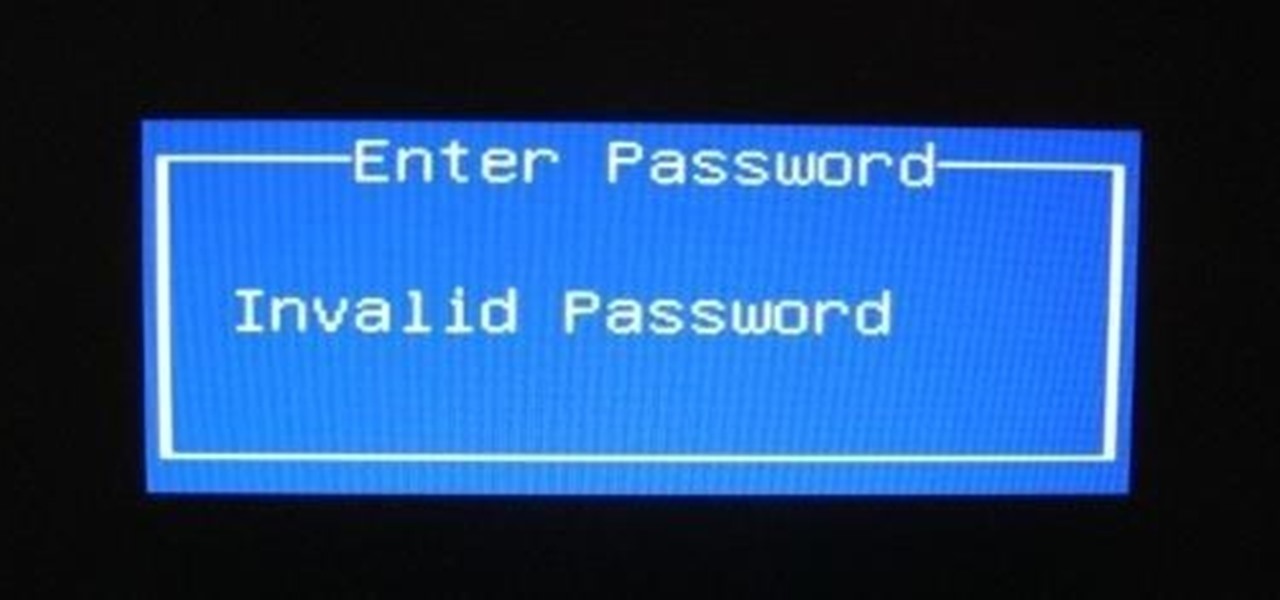
So i ran into a problem few days ago and it seemed to be very annoying one. I got hands on ASUS X55A with broken HDD. So i changed HDD and woo enter bios password. I hit enter and got into bios where uder security tab was shining ADMINISTRATOR PASSWORD INSTALLED. There was no user password but administrator password was set and it led to that i wasnt able to boot anything. At all.

In an attempt to get more people to subscribe to Apple Music, the Music app was completely revamped in the iOS 8.4 update for iPad and iPhone to include new tabs for New, For You, and Connect.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

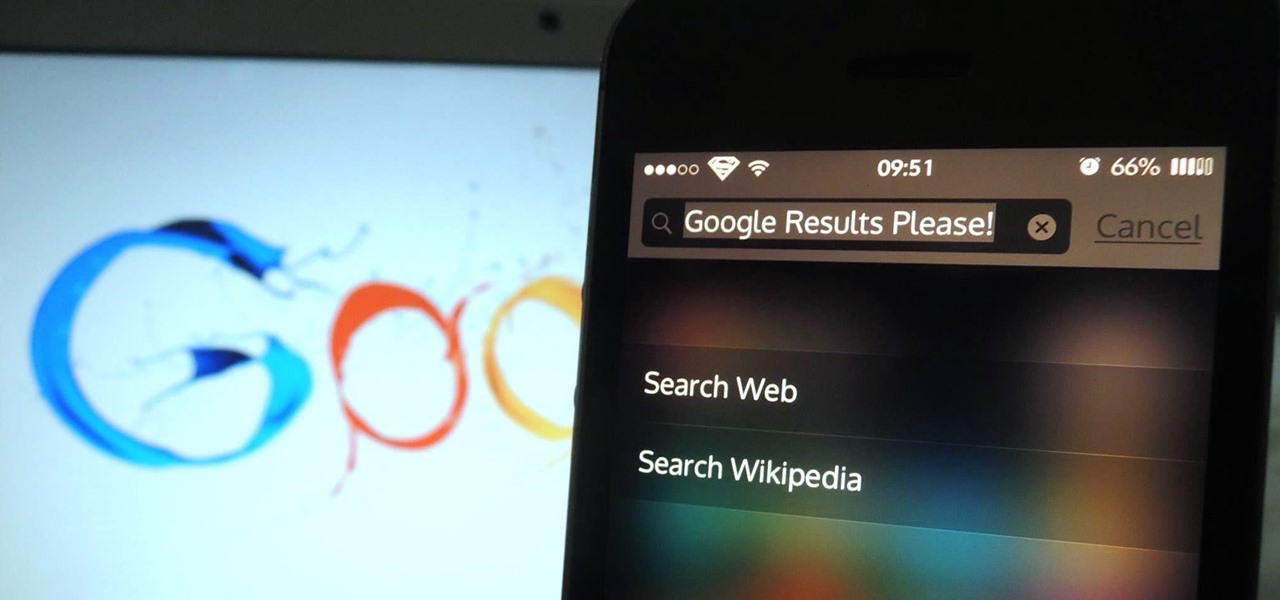
Spotlight makes finding apps, contacts, emails, songs, and old messages extremely easy on an iPad, iPhone, or iPod touch. You can even search for Wikipedia articles online, as well as perform general web searches.

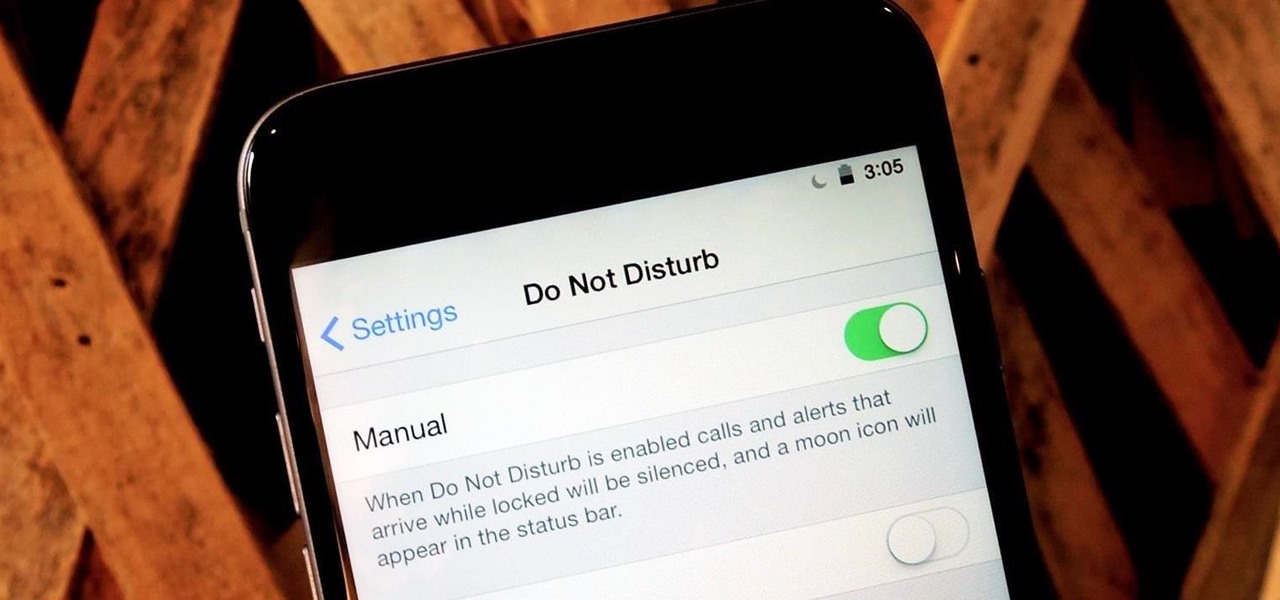
At certain times of the day, like when I finally get home after sitting through aggravating traffic, the last thing I need is the sound of my phone irritating me any further. So, I toggle on the "Do Not Disturb" feature (introduced in iOS 6) on my iPhone and get to enjoy a little peace of mind.

Before heading out on a hike, or any excursion for that matter, it would be wise to take a map with you just in case you get lost while on your quest.

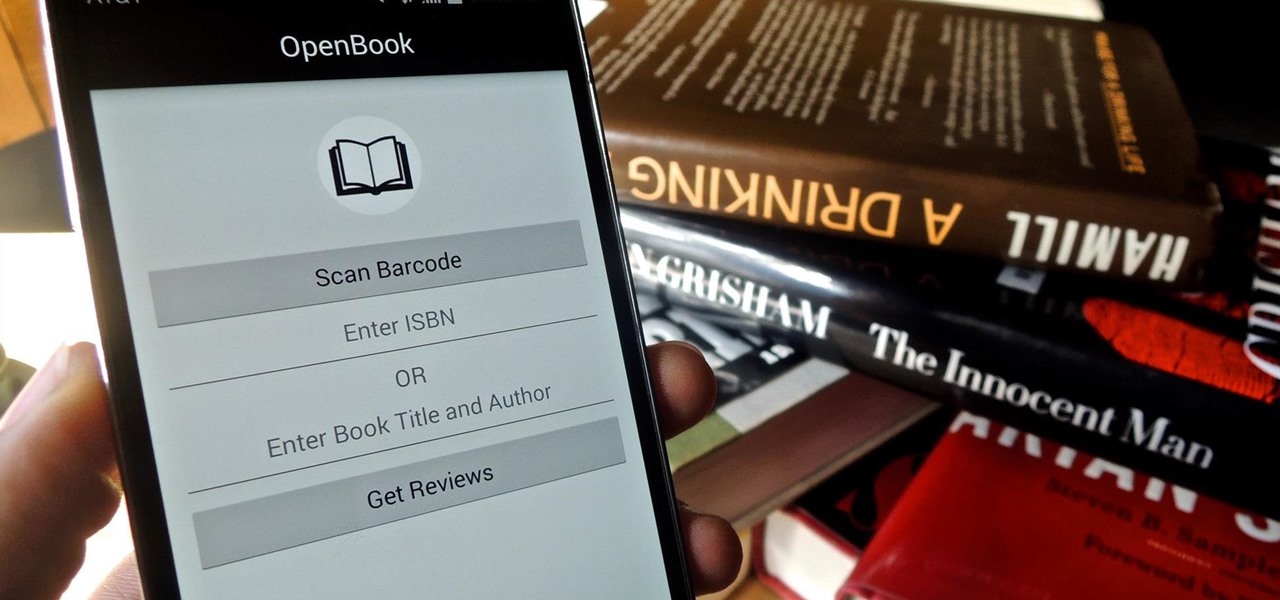
Purchasing an actual book from a brick-and-mortar store is becoming increasingly less common for people to do, but it hasn't completely gone out of style just yet. There's something about entering a bookstore and viewing all the potential great stories and epic tales just sitting on the shelves, waiting to be discovered.

Aside from identifying songs with Shazam and using the "Hey Siri" feature while driving, Apple's personal assistant isn't something I regularly use on my iPhone.

I may not be a well-traveled man, but one thing I've learned from my few excursions across the world is that currency exchange rates are a serious pain to keep up with. With global markets seemingly in a continuous flux, I started looking for anything to make staying on top of them easier, and thats when I found Price Helper.

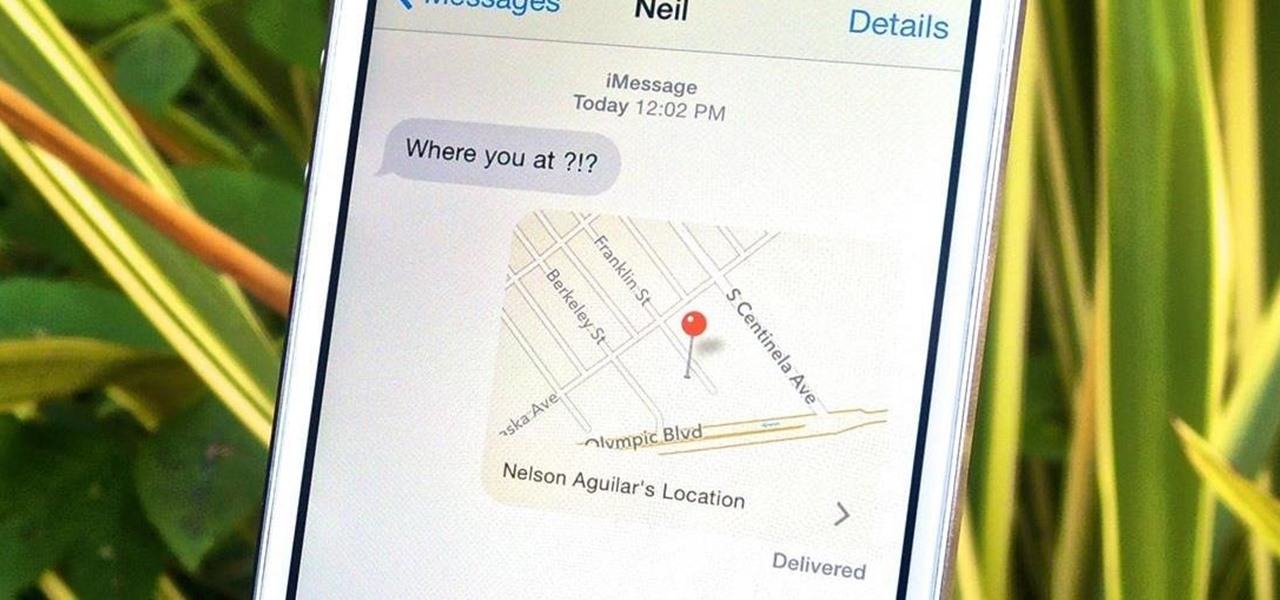
In certain situations, it can be a little difficult to get a handle on my exact location when others ask where I am or how to get to me. Now, thanks to one of the newly introduced features on iOS 8, I can easily share my exact location with friends, right from within the Messages app on my iPhone.

This past year, Facebook spent $19 billion purchasing the popular messaging app WhatsApp, and for good reason. Mark Zuckerberg isn't going to spend that type of money on just any application. WhatsApp is widely popular and frequently used by more than 500 million users worldwide, which is almost twenty percent of the Earth's population.

Trying to remember if it's "beer before liquor or liquor before beer" can be too much of a hassle, especially if you've already have had a few too many. While it would be great if one rhyme could determine the amount of pain you will feel the next morning, we must accept that we all react differently to alcohol and that's that.

This is an easy step by step tutorial how to lock your jewels in a hotel room or in a public safe. Be aware that in a public safe it is more secure to use the second method of locking by a magnetic card, not by a PIN code that can be easily seen by someone nearby.

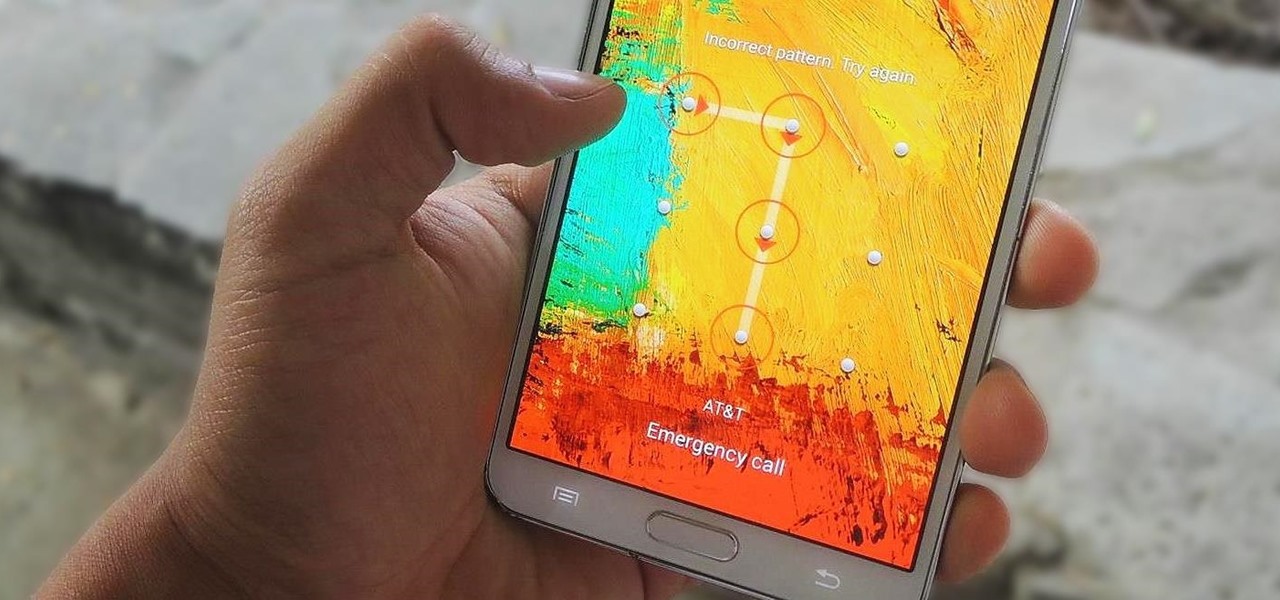
Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

I'm a textaholic. One of the problems with being a textaholic is that your device just can't keep up with you.

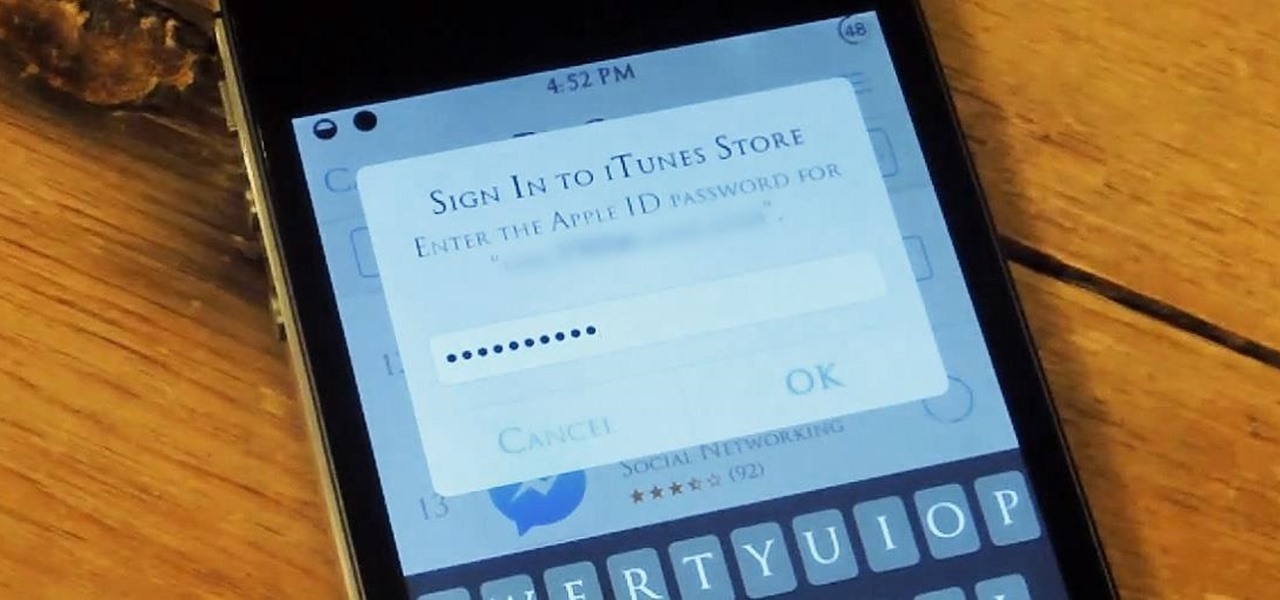
I hate typing in my password every time I want to install an application on my iPhone. My fat fingers make it so that I rarely get it correct the first time. If you're like my mom, you might not even remember it. Keyboard shortcuts are not a viable option either, since they are disabled for passwords.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Last week, Google updated the YouTube layout to be more in tune with other Google properties. One thing that's different is the new, more Google+ look of your YouTube homepage. Though some may like the change, some definitely do not. Also new is the "Guide" on the left side when you're watching a YouTube video. for you folks looking to get back to the normal YouTube layout, it's as easy as copying and pasting some code into your browser.

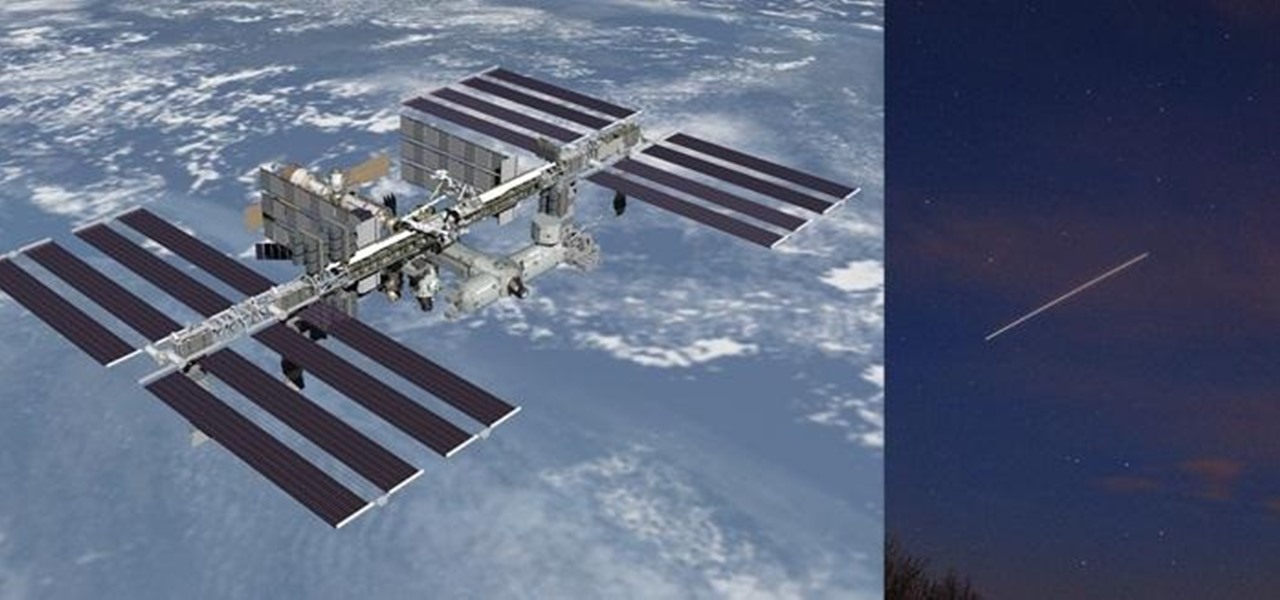
The International Space Station is one of the brightest objects in the night sky when it can be seen. If you know when and where to look, you can even see it from your house. It looks more or less like a really fast-moving plane—so fast, actually, that it's only visible from a specific place for a few minutes at a time. But now you don't have to do a ton of mathematical equations or rely solely on luck to spot the ISS at night. NASA just launched a program called Spot the Station that sends y...

Several people have been reporting Wi-Fi problems after updating to iOS 6 on both iPads and iPhones. The connection might work sometimes, but it usually cuts out or takes forever to connect to anything, only to time out shortly after.

The passcode, or the four-digit code you enter in order to access an iPhone or iPod touch, was created to ensure security and prevent hacking. But what if you haven't touched your iPhone in a month and you simply don't remember what your passcode is anymore?

Need to browse the web on your new Samsung Galaxy Tab? Well, first you're going to have to set up Wi-Fi on the Android device. This video shows you the complete steps to getting connected! Press MENU < SETTINGS < WIRELESS & NETWORKS < WI-FI SETTINGS and then select WI-FI to turn in on. Next, choose your network, enter the password and press CONNECT. It's that easy.

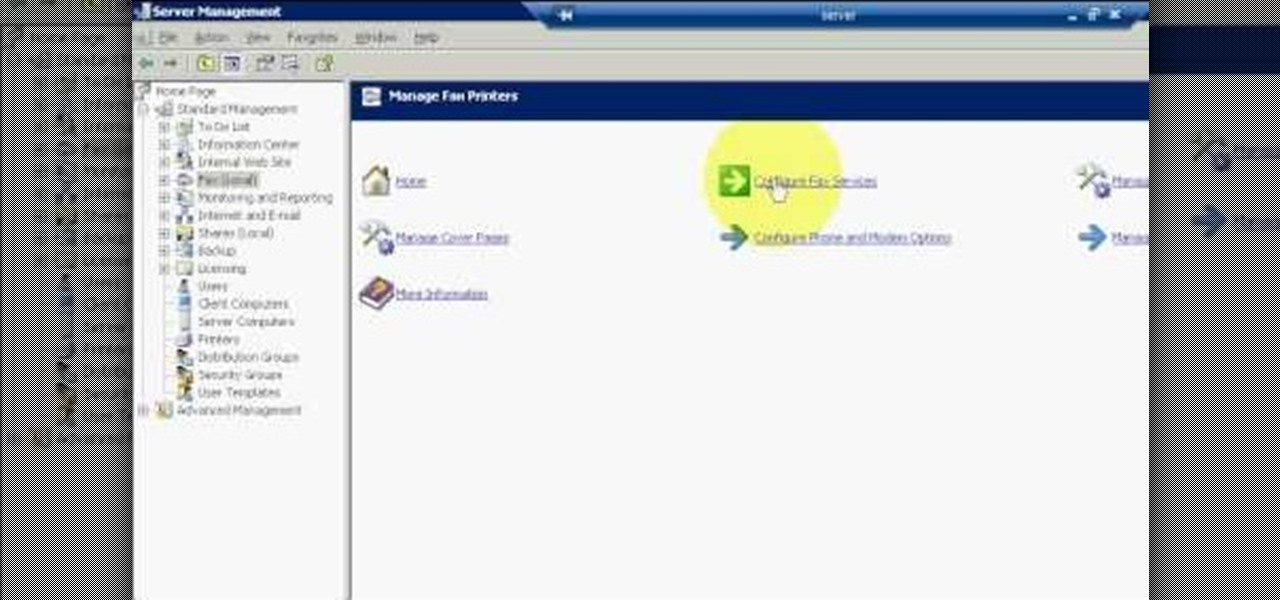
The first step to create a fax using Outlook 2003 and 2003 server. Using add/remove windows component make sure your fax equipment is properly installed. Under the start menu select the printers and fax option and select the share option. Then under administrator tools/users/new/users/fax to enter your password to turn our fax information transfer on. You must now select fax user and select advanced settings and double check to make sure the fax is able to see the object it needs to send the ...

In this video from sjsharksiPodtouch we learn how to jailbreak your iPhone 3Gs with firmware 3.0 using a Windows machine. With your iPhone plugged it, download the PurpleRa1n file and click make it rain. Then your iPhone will enter into recovery mode. You'll see the PurpleRa1n logo on your iPhone and then it will reboot. Tap the Freeze app, and tap Install Cydia. Once finished, exit and then reboot your iPhone. Now Cydia is fully installed. You will get a message on your iPhone saying Reorgan...

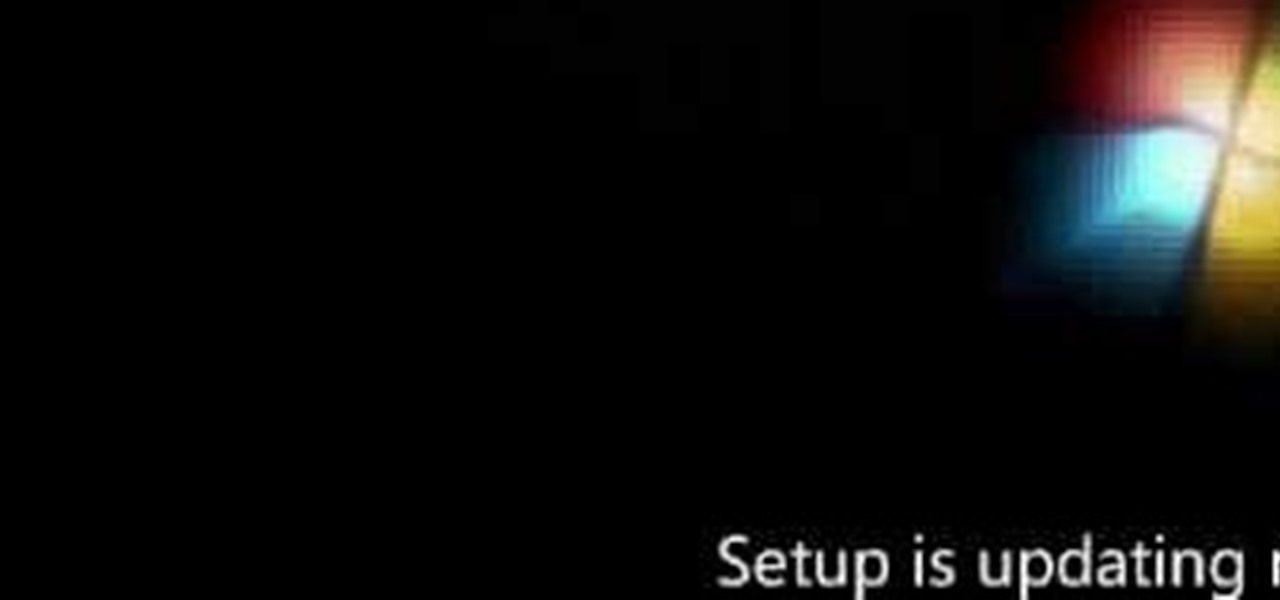
In this video, we learn how to install Windows 7 on your computer. First, place the disk inside your computer and start the installation process. Setup will start, then it will start to copy files, expand files, install features, install updates, and then complete. As it runs through each of these, it will show you a percentage of how far through the process it is. Once it has finished installing, you will be able to set up your user account. After this, you will need to enter in the product ...