The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.
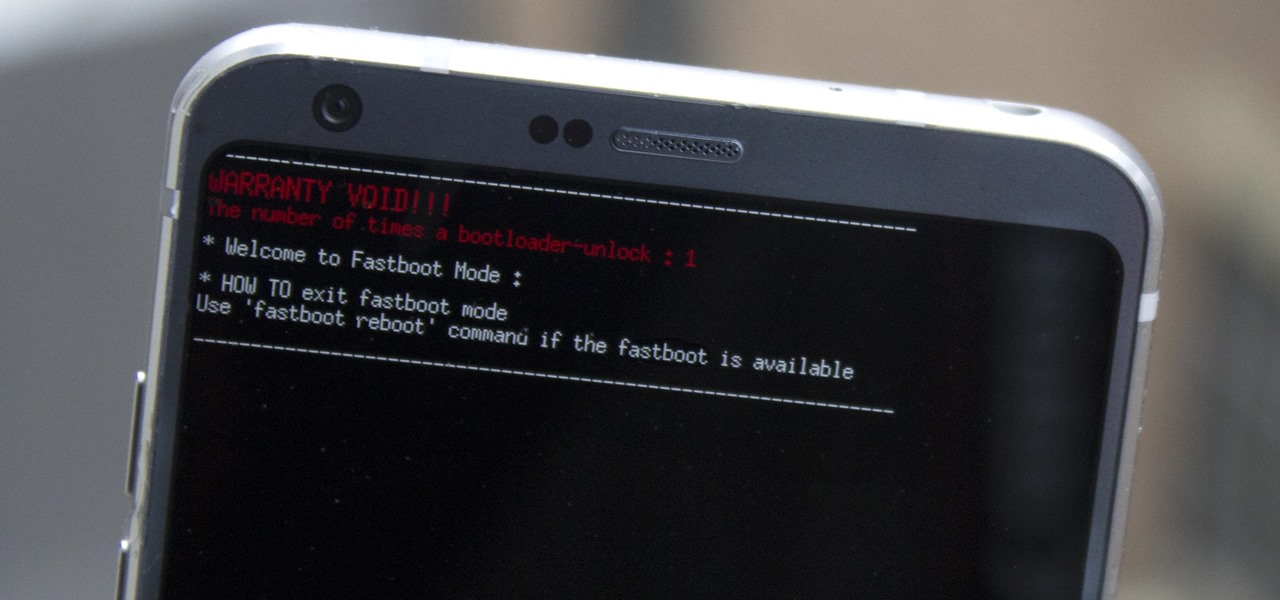
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that it's three or four times that amount.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

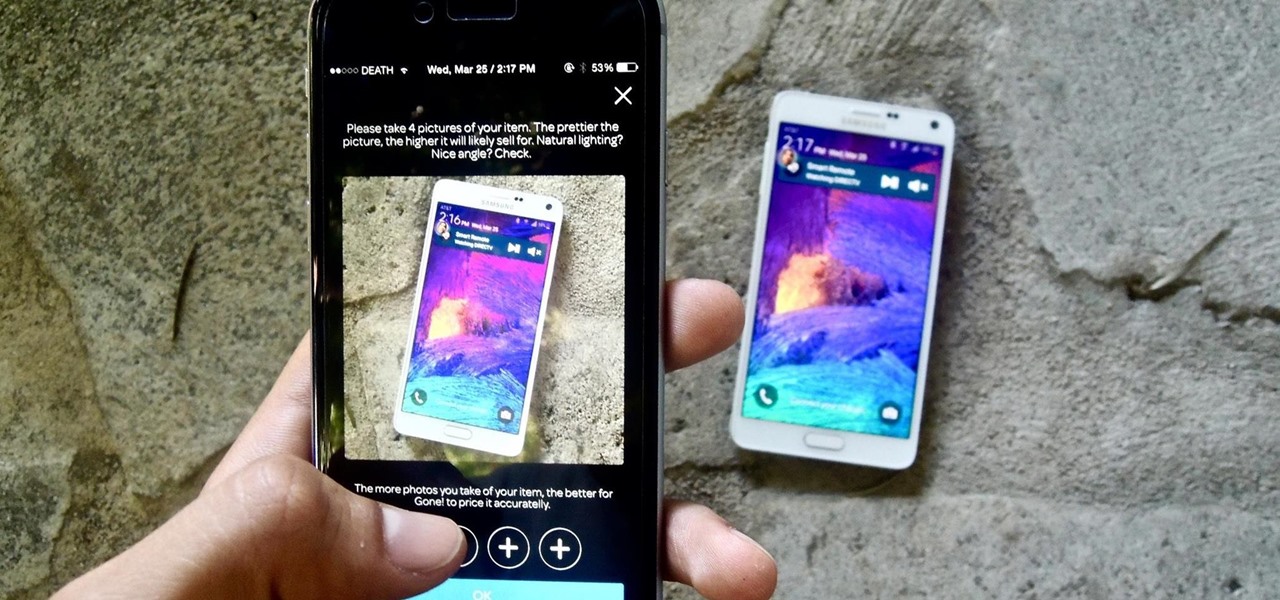
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

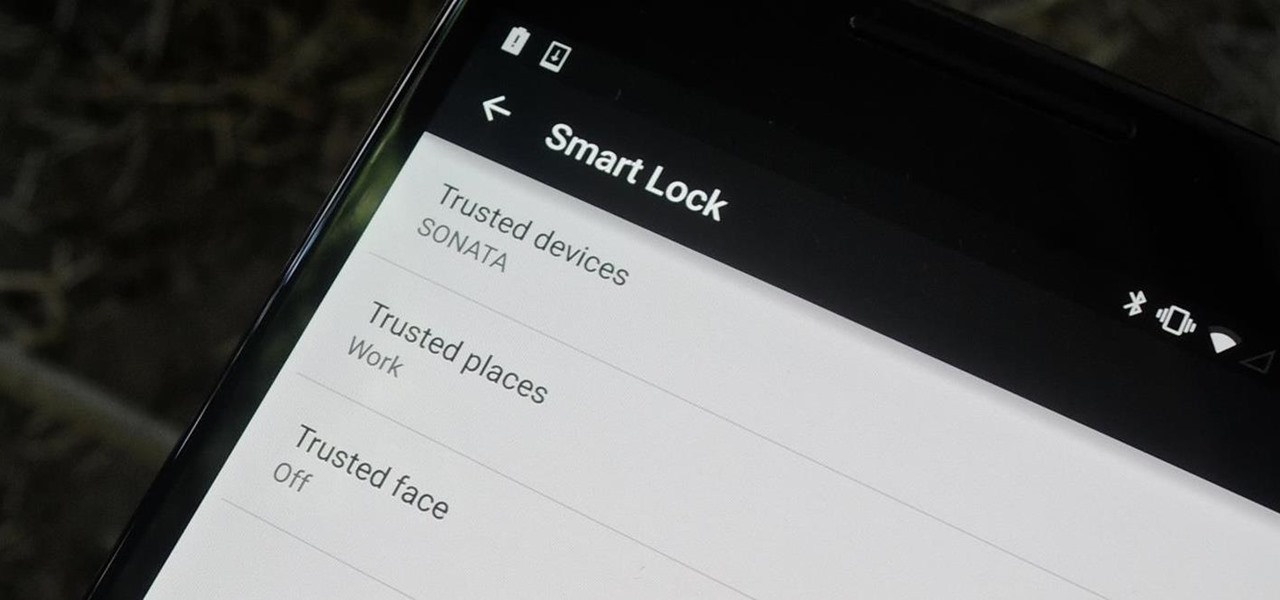
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

This tutorial is for everyone who has been waiting for a solution to stream web videos to a Chromecast by using an iPhone or iPad. It is easy as a cakewalk.

Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't work as advertised.

You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

App-locking apps have been around for a while, but none have had quite the panache of developer Fazil Kunhamed's latest offering, Oops! AppLock. While others use a PIN or password to restrict access to apps that are installed on Android, AppLock uses a stealthy volume button combo.

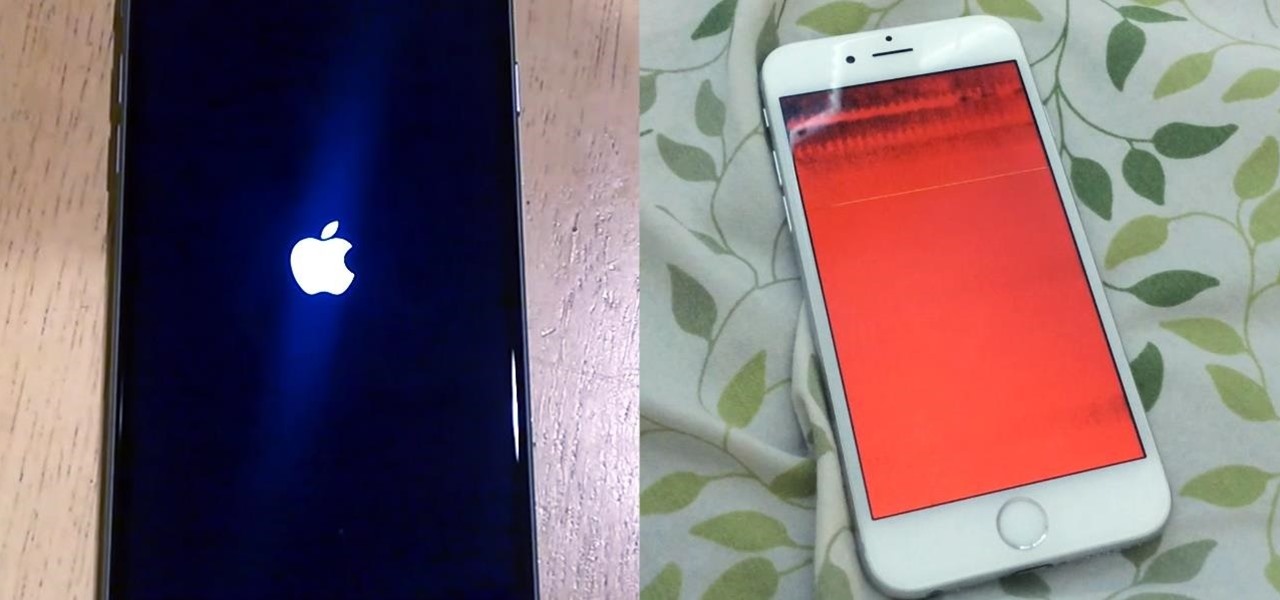
We recently ran into a serious iPhone 6 issue here in the Gadget Hacks office, where the device was stuck in an infinite bootloop with intermittent red and blue screens (of death?) and an unresponsive touchscreen and buttons. From what we can tell, we weren't alone, though some are experiencing only one or a few of the issues we've had.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices yet. While there are ways to port BlinkFeed over to other devices, it's reliability is dependent on the ROM, sometimes causing bugs and crashes.

This is a great how to for all users in Final Cut Pro X 10.1.2 Video: .

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Due to its constant delays and lack of public invites, the OnePlus One is the equivalent of a unicorn in the Android community. I was lucky enough to win an invite in the OnePlus Storm of Invites promotion and have loved every minute with my new Nexus Killer since receiving it.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

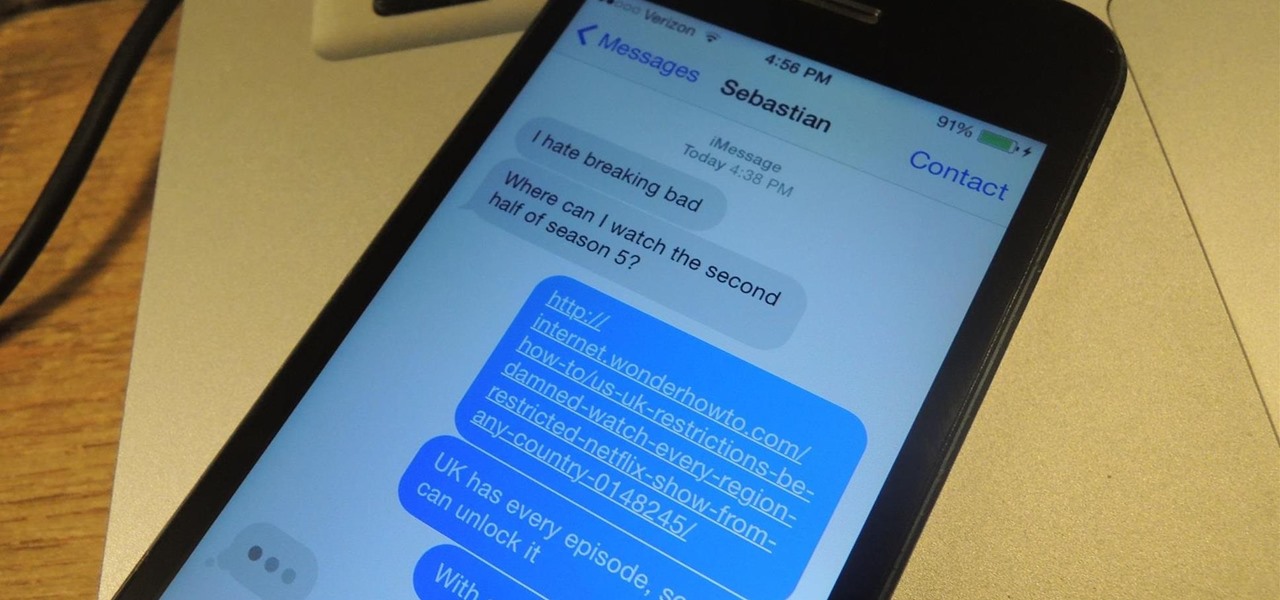
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

Unlocking your Samsung Galaxy S4 so you can use a different SIM card isn't the easiest thing in the world. In the states, unlocking cell phones was actually illegal, despite the White House's disapproval, though, a recent bill has making its way to the House floor and has made it legal again.

First of all I am glad that I was able to find this website and become part of it. So far I love it. Recently Playstation created a competition where a person has to show how online gaming is good. Pretty simple right? You can enter with an image or a video, however I do not think that an image can really show the fun of online gaming. I have created a video which does show some of the good parts of online gaming and I also tried to keep it fun. I would really appreciate if you would have a l...

UPS Tracking provides several convenient ways to track packages online, including on-the-go with your mobile device. Track your package using UPS Quantum View Notify to get real-time updates on packages in your supply chain or send delivery notification alerts.

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.