Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.
The CEC, Canada Experience Class, is a new program to help a person who has held residency in Canada gain permanent residency status. The program realizes that, by going to school or living in Canada while working, many people have the skills necessary to make the transition to live in Canada permanently. To qualify for CEC, you must be a temporary worker living in Canada for at least two years with two years of skilled working experience. A second way you can qualify is by being a foreign gr...

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

You have many great memories to share. Why not collect them all in one book? Learn the fun and meaningful craft of scrapbooking. In this video how-to, learn how to get started on your scrapbooking adventure.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Since it's introduction, iPhone has become the standard for design and ease of use, redefining what's possible on a mobile phone. And now with iPhone 3G, this revolutionary device gets even better, offering even more advanced capabilities. iPhone 3G works with fast 3G cellular and wi-fi networks around the world to keep you connected wherever you go. With its integrated GPS technology iPhone 3G makes it even easier to find where you are and where you're going. iPhone 2.0 software includes sup...

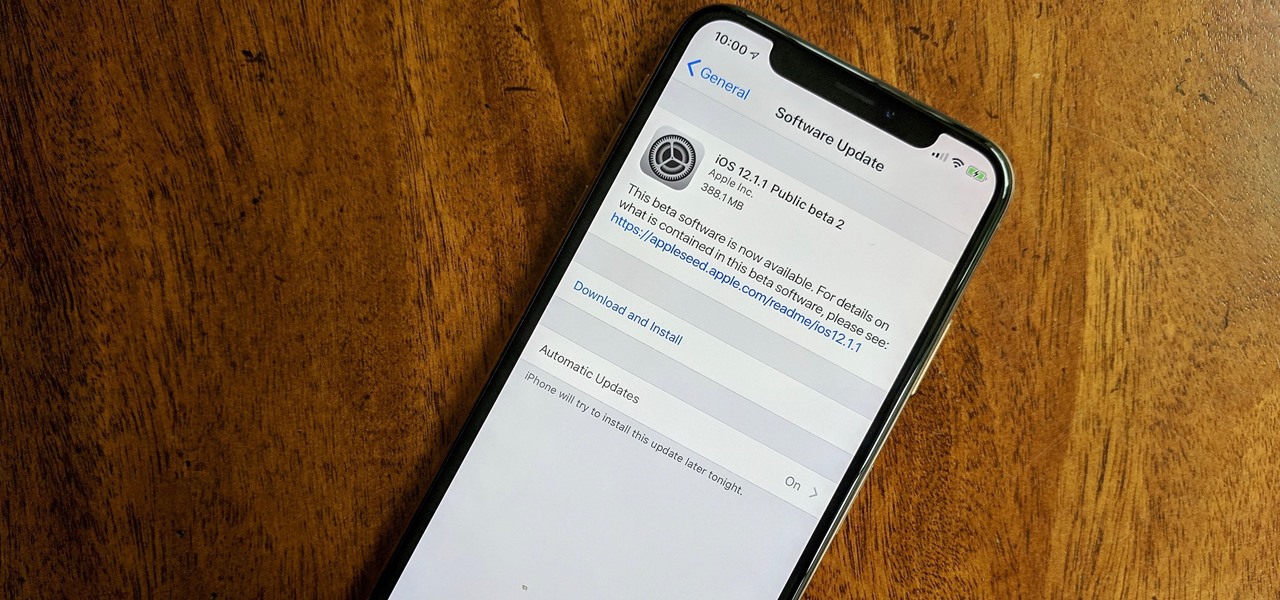
Registered iOS developers received their first taste of 12.1.1 dev beta 2 on Wednesday, Nov. 7, and public beta testers received the iOS 12.1.1 public beta 2 shortly thereafter.

The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

UPS gives you all the tools you need to take away the complications and confusion of international shipping. UPS provides simple, step-by-step online instructions and helps guide you through the required documentation to reduce the likelihood of customs delays.

Video: . » Iran Threatens to Block Tankers in Response to Oil Import Embargo Alex Jones' Infowars: There's a war on for your mind!.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

You Tube user go to guy enterprises teach you how to make glue bound paperback book. You will print you book on a4 paper, 2 pages per side, on each side. That means you'll have 4 pages in total on a sheet of a4 paper. Fold the paper in the middle and make stacks of the pages. You will also need an adjustable wood placement for the pages. Make sure you also have a piece of card stock for the black cover. Then align everything up, clamp it down to make the pages staying tight. On the spine of t...

If you're a normal, non-corporate video conferencing user, you may not have heard of BlueJeans, but in the corporate world, the software has long been a major staple when it comes to remote meetings.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

The enterprise applications powering the adoption of the HoloLens 2 are only just ramping up as developers continue to work with the still relatively new hardware.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

Apple might not be ready to unveil its rumored-yet-unconfirmed smartglasses. But the iPhone's current depth-sensing hardware is proving to be useful for both smartglasses makers and mobile AR apps.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.

The week of the annual Consumer Electronics Show is supposed to be filled with good news for the augmented reality industry as AR headset and smartglasses makers show off their new wares.

Investors continue to bet on augmented reality, both for short-term returns and long-term plays. This week, Niantic reportedly picked up another round of funding from Samsung and others, based on the success of PokémonGO and the prospects for future revenue. Likewise, investors see value in WaveOptics, whose waveguide displays could make consumer smaller AR smartglasses possible within the next year.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

We have seen Kickstarter-launched wearables before, but this one is particularly unique and may even have you blinking a bit in wonder when you see how it functions.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

While some widely praised immersive computing initiatives at Google are shutting down, over at Epic Games things are just ramping up, and it involves quite a bit of cash available to indie augmented reality developers and startups alike.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.