Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.
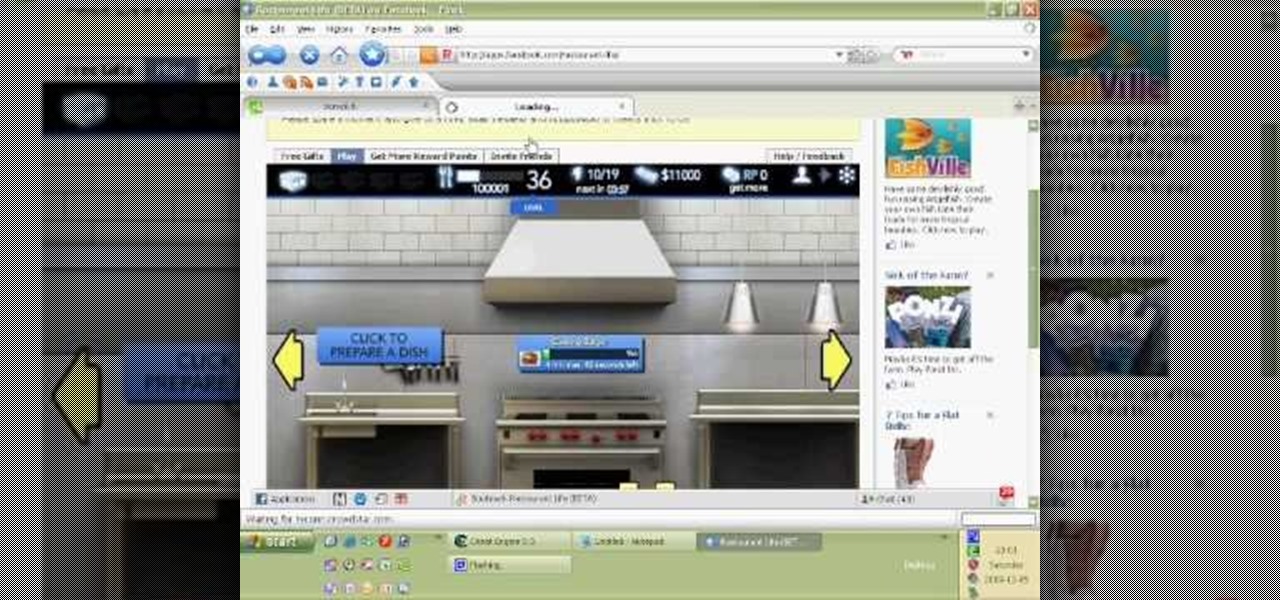
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this video tutorial, you'll learn how to use the Second Copy backup application, for the Windows operating system, to protect your most important data. For step-by-step instructions on installing and using Second Copy, take a look at this backup how-to.

VLC Media Player is one stop shopping for all your music and video playing needs. You can watch any audio or video formats from .flv, .wmv, .mov and more. If you are tired of having multiple softwares for playing different files, consolidate and use VLC Player instead. This tutorial shows you how easy it is to download VLC Media Player for any operating system.

This software tutorial shows you how to convert your Windows Movie Maker projects using conversion software so that they will play on a Mac computer or operating sytem.

Check out this video tutorial on Blender. You'll see how to successfully create a modeled skull in Blender.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

This step-by-step video tutorial shows you how to install CHDK onto your Canon digital camera. CHDK is a firmware enhancement that operates on a number of Canon cameras. CHDK gets loaded into your camera's memory upon bootup (either manually or automatically). It provides additional functionality beyond that currently provided by the native camera firmware.

Admit, you're curious. You want to know just what does it take to make a virus for the Mac OS X operating system. Check out this video to learn how to write a harmless virus for computers running Mac OS X.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

Have access to a Battistella T220P ironing table and, however improbably, wondering how to use it? Well, you're in luck: With this video demonstration, you'll learn how to operate the Battistella T220P ironing table in the service of ironing a shirt. For more, or to get started using your own Battistella T220P ironing table, watch this video tutorial.

General Pipe Cleaners Easy Rooter Junior is the right machine to clear washtubs, small floor drains, roof vents and other medium-size drains. This video will give you a general overview of the operating instructions and safety procedures for the easy Rooter Junior. Take a look.

Cool project to show how a capacitor operates!

A transom window is a traditionally fixed window over a door or an operating sash window. In this how to video, the experts form the DIY network prep and install a transom window in this historic home. Watch this tutorial and you can be installing a transom window into your own home.

The Paslode Framing Gun is operated by a gas cartridge and battery so an air compressor is not needed. The tool also has a large range of nails available for different job requirements from 50mm To 75mm. Watch this video tutorial for a demonstration on how to use a Paslode impulse framing nail gun.

This video tutorial shows how to assemble an automatic Lego crossbow. Learn how to build and operate an automatic toy crossbow made out of Lego bricks.

If you've never heard of Blender, maybe you should get it and watch this video tutorial on how to use the curve tools in it. Great for 3D modeling and animating.

If you're going to do this, be careful, as your fingers get close to operating high voltage devices & potentially fatal current! Remember that TV's can store a lot of energy for a long time, so don't be poking your finger everywhere - even if the TV is off.

The Titan hitch receiver lock is a lock for all 2 inch receiver hitches. This is a simple padlock style lock. What you do to operate it is pull the protective cover off, take the key and give it a little bit of a turn. This video walks you through it.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

With Google's new Pixel 4, we now have another device in the pool of phones designed for normal-sized hands. The other major player in this segment is as big as it gets — metaphorically. Apple's iPhone 11 Pro is the small phone to beat, but can Google be the one to dethrone it?

With its 3D engine being responsible for approximately 60% of augmented and virtual reality experiences, Unity is continuing to place a premium on tools that not only keep developers working in its development environment but also make their workflows easier.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Every fall, we can expect a few things: leaves changing colors, cooler temperatures, and Samsung and Apple releasing new phones that fanboys and fangirls will argue about until the following year. This year, Samsung is mixing it up, releasing two phones in the Galaxy Note series. Let's see how the larger phones compare.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

The Apple rumor mill is getting its first real workout of 2019, and this time the whispers are more exciting than usual.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

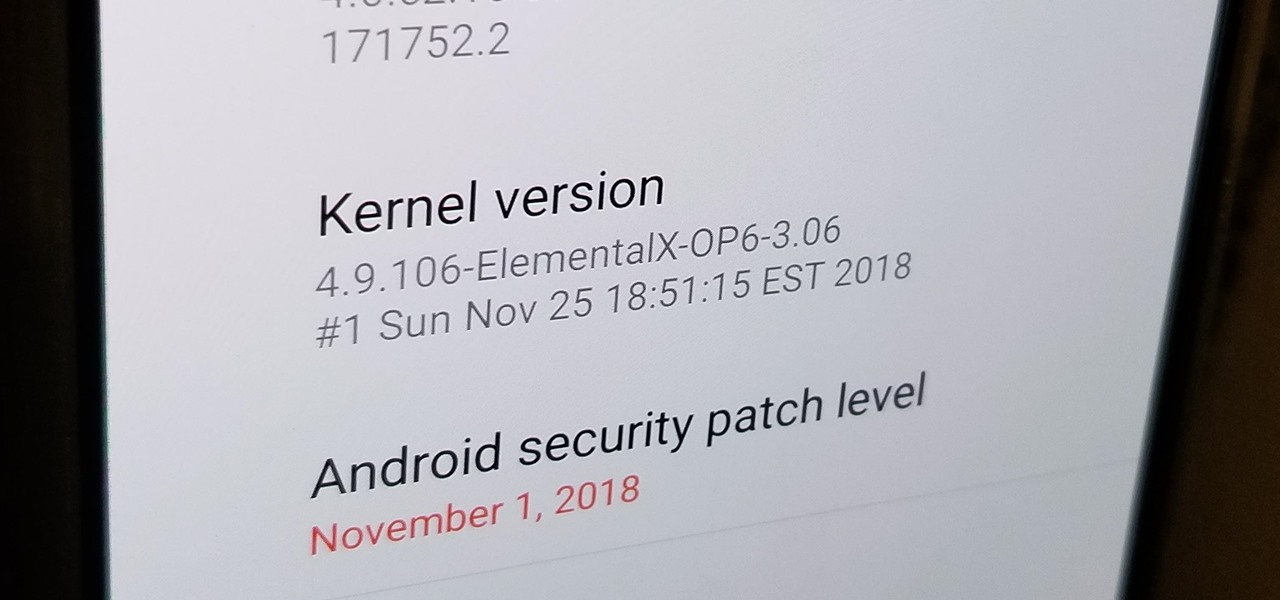
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customizations, and it allows you to have full control over how your system performs.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.