The Samsung Galaxy Tab 2 (7.0) 4G LTE on Verizon has only been released for a couple months now with good reviews. It comes with dual cameras, memory expansion, and very quick 4G LTE speeds, without needing a contract. While most users are satisfied with the tablet as is, there are others that prefer rooting the tablet in order to install their own custom ROM. Now you can do it with the Samsung Galaxy Tab 2.

Keeping your operating system up to date is essential to keeping it bug-free and running properly. Windows regularly pushes out patches and security fixes through Windows Update, so making sure to turn on Automatic Updates or checking at least once a week is strongly advised.

Since the release of iOS 6, there has been a bit of an uproar over some of the new features (the new Apple Maps replacing Google Maps) and certainly over the glitches that always come attached with new operating systems. Downgrading Your iOS

Lightning has struck, but not everyone is excited. Apple's new 8-pin Lightning connector for the iPhone 5 has replaced the aging 30-pin connector. Many users have concerns that their current third-party devices will no longer operate properly with the smaller all-digital design, not to mention the expensive price tag for each adapter. What Does This Mean for the User?

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Imagine… being able to watch television on your PC. And imagine being able to stop, pause and record those television shows. Well, in Windows 7 it's totally possible. This video shows you the possibilities of Windows Media Center.

Work is commonly composed as a Microsoft Word document but if you would like to convert that document into a PDF file that any operating system can ready you will need to follow a few simple steps.

A computer’s safe mode is useful when fixing problems or saving work after, say, your hard drive malfunctions. Safe mode can easily be accessed as your computer starts up and is a useful tool to have in your belt.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Is your power drill making a funky high pitched noise when you try to use it? Or why your chuck on your drill doesn't spin? You first reaction may be to throw it on the ground in anger, but this could actually be simple fix. Sometimes, the gear switch can get stuck in-between gears, and can be fixed by simply moving the gear switch back and forth on your drill. Try that and see if it fixes your battery operated power drill.

There may be a time when you want to run a program for 24 hours straight. If that app happens to quit unexpectedly, you have some options to get it going again without having to manually reopen it. Check out this video on how to restart a crashed program automatically on Windows. You need WatchDOG.

John Leeke demonstrates using steam to remove heavy paint build up from wood surfaces in this five minute video. Steam paint removal softens the paint film so it can be more easily scraped away. It works well with the heavy paint buildup commonly found on the exterior of older buildings during house restoration and historic preservation projects.

The future of the HoloLens 2, according to Microsoft, is all about enterprise use cases. But that doesn't mean some of the more creative-minded HoloLens developers won't bend the top-tier augmented reality device to their own designs. The latest example of this trend comes from Japan.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

San Francisco-based augmented reality company Scope AR has made building AR instructional content for mobile devices and AR wearables as easy as throwing together a PowerPoint deck, primarily via its WorkLink platform.

The company augmented reality that Rony Abovitz was trying to build at Magic Leap apparently wasn't working out the way he hoped it would. That company, built on dreams, music, and future-looking entertainment, rather than truly new technology, came with a $2,300 price tag for a device using dynamics most mainstream consumers have never even tried.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

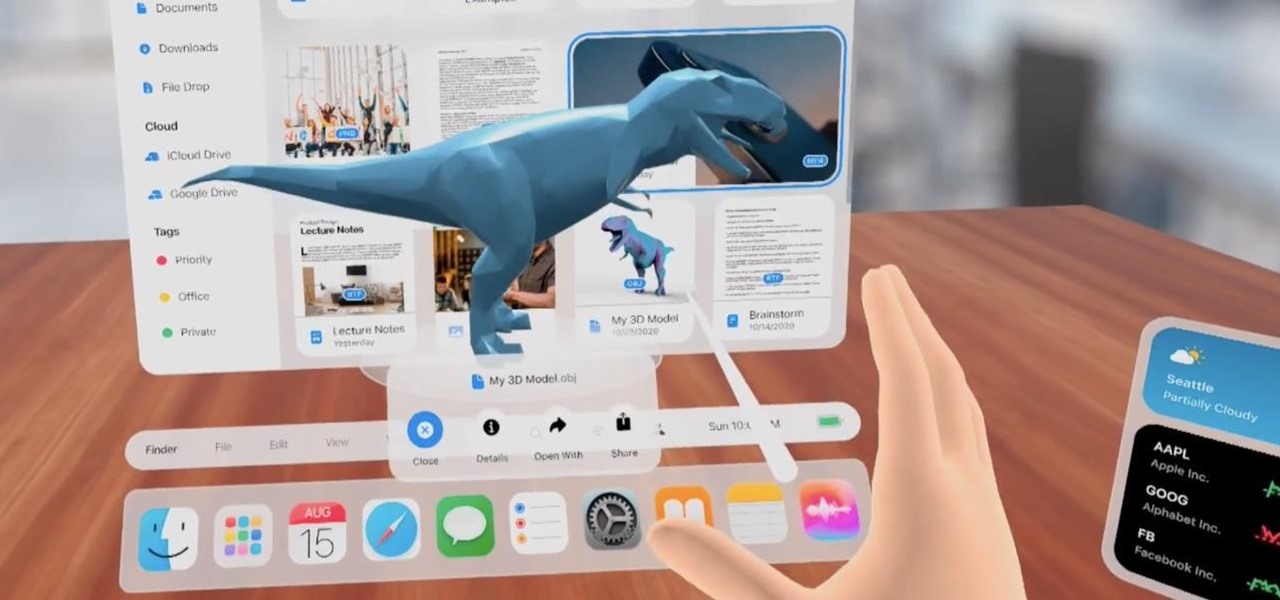
One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

If you play 3D Pinball on your Windows operating system, then you might be happy to know this hack. This pinball game, officially called 3D Pinball for Windows: Space Cadet, was available on Microsoft Plus! 95, and everything up to Windows XP. It was dropped from Vista.

IT is a competitive field, and finding success requires more than knowledge of a couple of coding languages or knowing how to google really well. To stand out among your peers and competitors, you should learn everything you can and get as much diverse experience as is available.

When life hands you lemons, make lemonade. At Magic Leap, the lemons are the COVID-19 pandemic, and the lemonade is a new solution for virtual meetings born out of social distancing.

The focus on augmented reality over at Apple is, so far, restricted to the iPhone and the iPad. But if some of the most reliable analysts in the business are to be believed, we'll probably see some kind of AR or VR wearable from the company later this year.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

If you had a phone in 2004, there's a pretty good chance it was a Motorola RAZR. The iconic phone is the tenth highest-selling of all time, and it marked the height of the flip phone era. Now that the technology has caught up, Lenovo (Motorola's parent company) is bringing it back in a big way.