The great thing about competition is it drives innovation. But when a company tries to one-up its competitor, it's not always with something brand new. Sometimes, one party will draw heavy inspiration from the other — but hey, it's still all good, because the consumers benefit either way.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.
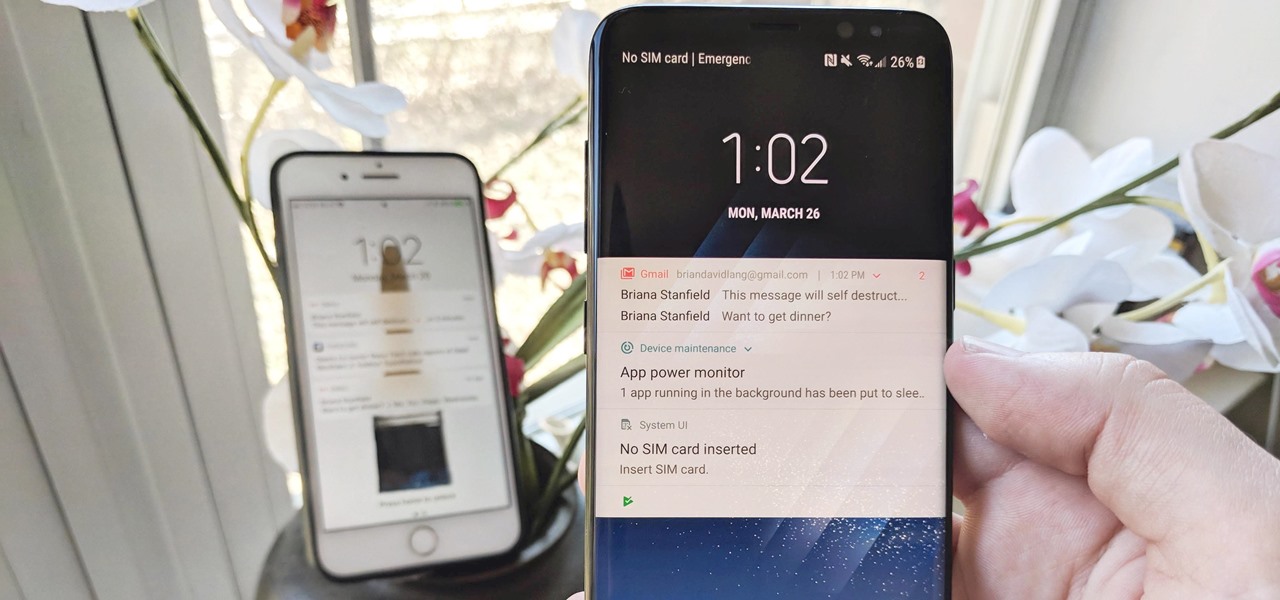
The iPhone vs. Android debate is almost as old as smartphones themselves. While there are a number of reasons to skew towards one operating system or the other, the Samsung Galaxy S9 models have a ton of great features that help set them apart from Apple's iPhones. The coolest feature, in my opinion, is the way notifications are handled.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

Because of quirks with cell radios and how Android was previously set up, custom ROM support for Galaxy S phones has been sparse these past few years. It's been almost nonexistent for US customers, while international users would see some ROMs. Thanks to Android Oreo's Project Treble, this will all be changing soon.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

With the recent launch of the LG V30 and the Pixel 2 XL, LG has reintroduced the world to POLED. This display tech was showcased at CES 2015 and billed as a rival to Samsung's AMOLED displays, then promptly disappeared from the market for two years. But now that two of the biggest flagship phones this year are using the technology, many folks will be wondering what makes POLED different.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

The hunt for the mixed reality use-case that wins over consumers' hearts and creates a critical mass is a problem every developer would love to solve. Not only would they find themselves rich and famous seemingly overnight, but they would also end up making one of the various possible hardware solutions a viable place for other developers to put their time and energy.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Coming up at the end of May is the world's largest conference and expo dedicated to all things augmented and virtual reality, the Augmented World Expo, more commonly known just as AWE. And this year, a few of us from NextReality are going to be there.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Ask anyone that works on the development of driverless vehicle technology and there is a very good chance that AutonomouStuff will have supplied something to their project.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Augmented, mixed, and virtual reality are all a little bit different, but as many expect—including Metavision—the continuum of our next realities will converge and give us one head-mounted display (HMD) platform that can do it all. If Vrvana, a Canadian company building AR and VR headsets, succeeds, that convergence could begin as early as next year.

The big day has finally come—the new iPhone 7 and iPhone 7 Plus have been officially unveiled. Apple debuted their new flagship devices at a keynote event in San Francisco on September 7, and as we've grown to expect, there are tons of changes in store for the world's top-selling smartphone.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.