Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

In hopes of strengthening its growing augmented reality team, Apple has reportedly hired Michael Abbott, an engineering and investment veteran with past ties to Twitter, Microsoft, Palm, and others.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

While the consensus among some in the augmented reality community is that the Microsoft HoloLens is the best device available at present, it also remains the most cost-prohibitive option, with the development edition costing $3,000.

Digital imaging company OmniVision Technologies and the Hong Kong Applied Science and Technology Research Institute Company Limited (ASTRI) entered the CES fray this week with a new reference design for an augmented reality headset capable of 60 degrees field of view (FoV).

With a pair of new APIs and low-latency media servers, Twilio's Programmable Video platform could soon help ARKit and ARCore app developers build shared AR experiences between multiple users.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

Mixed reality developer Arvizio has updated its MR Studio software suite to integrate processing of 3D light detection and ranging (LiDAR) point clouds.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Beijing- and Seattle-based DataMesh have announced the release of a new enterprise geared mixed reality middleware — MeshExpert. This solution for collaborative interaction with dynamic data is made up of two primary components: MeshExpert Live!, a 4K mixed reality capture system built off of the Microsoft Spectator View, and MeshExpert DataMix, which offers the ability to blend different types of data with XR and mobile hardware.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Your target in level 3-13 of Angry Birds is not so much a pig fortress but a series of pig-defended hilltops. Still no problem for a properly trained bird army. Watch the video for a guide to beating level 3-13 with three stars.

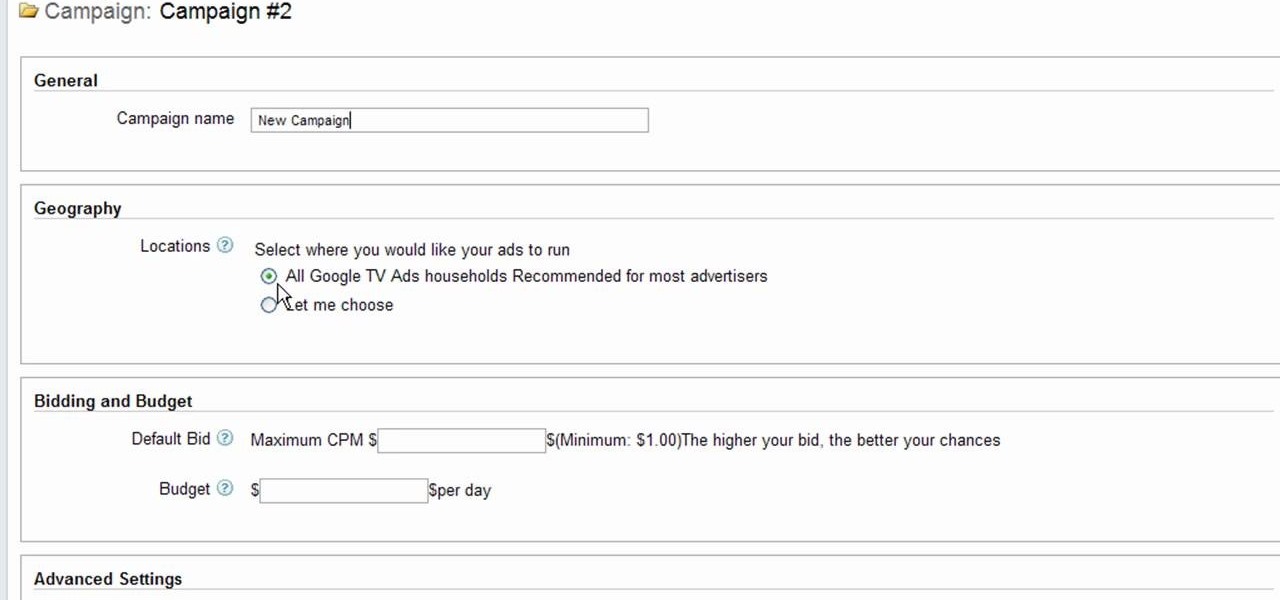
Interested to know how to start a new cable television ad campaign with Google AdWords TV Ads? This official video from Google will teach you how to use the new interface to determine just that. For all of the relevant details, and to get started creating your own televised advertising campaigns, watch this clip.

It's been a few years since Finding Nemo became the highest-grossing animated film of all time, but it's cultural appeal lingers on. If you want to capture some of that Nemo cuteness for your Halloween costume, watch this video to learn how to make a really cute Nemo costume with no sewing required.

The ground and pound is one of the most controversial aspects of MMA fighting, and is a great chance for you to do a lot of damage to your opponent. In this video UFC fighter Joe Lauzon will show you how to use an elbow technique from guard to defend yourself and get a solid elbow shot in at the same time, using Joanne from MMA Girls as his target.

Halo: Reach has so many tough to get achievements, but the easiest one that you can get pretty fast is the "Crowd Control" achievement, and you can get it on Courtyard using the target locator. In this video you will learn how to effectively kill off multiple Covenant drop ships to get the achievement in about five seconds!

Two Corpses in One Grave is a difficult achievement in Halo: Reach if you don't know where to look on mission 3. You will have your chance right after you acquire the Target Locator when two Wraiths show up for the killing! Just be sure to aim straight and true and you will be alright!

Thanks to modern technology, we don't have to visit our nearest Target or Rite Aid to get our pictures professionally retouched and printed. With many printers offering photo-quality ink and paper companies that offer photo-quality paper, you can use your home printer to create professional-grade photos.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.

Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

If you want a tight, lean stomach and obliques so sculpted you'd make Jillian Michaels jealous, then the only way to get what you want is to complete alternating days of cardio with strength training.

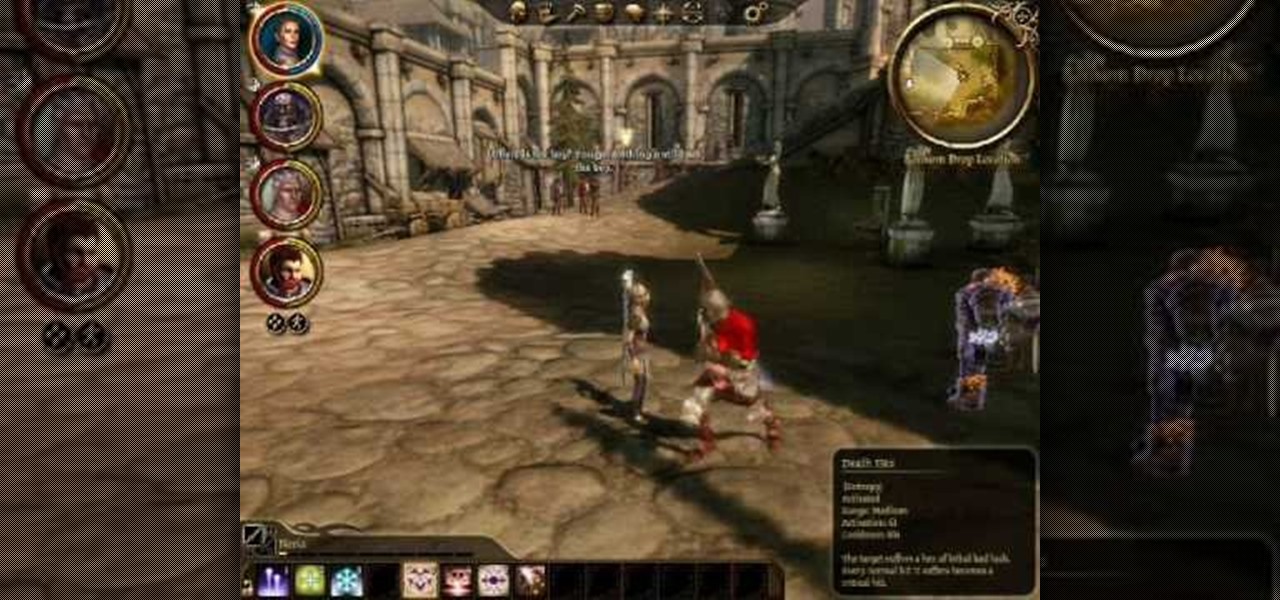
By combining different spells on the same target, or combining spells with other effects, you can do some devastating damage in Dragon Age: Origins. Turn your mage into an archmage by mastering effects like Paralysis Explosion, Grease Fire and more (including the deadliest, Storm of the Century)!

If shield kicking is legal in your game, here's how you can safely and effectively kick your opponents shield (and perhaps even knock them down). Know what's a good target, and a good way to deliver the kick without exposing your leg to be hit in turn.

This next video, is a great blend of woodworking and technology. In the tutorial, you'll be finding out how to create a wooden frame for the small digital picture keychains that can be bought from stores like Target and Best Buy. It's a great gift idea for parents, relatives, or just for you. So check it out, take notes, and good luck!

Practice lineout throws for rugby from the Ford Academy in Australia. Throwing the rugby ball with two hands overhead. It is important to focus on targeting, speed and your teammates. A lineout throw is made when the ball goes out of bounds and you need to reenter it into play.

Want to improve your tennis skills? Check out this instructional tennis video that demonstrates how to hit a tennis ball across the court in this video tennis lesson.

Check out this instructional baseball video that demonstrates how to play infield. This video offers a few tips for fielding ground balls. Learn how to make a play on a grounder from a professional in this baseball video.

There is not better way to get in shape and target trouble zones than with the help of some experts in fitness and some simple workout equipment. In this how to video tutorial SELF Magazine shows you how to tone and sculpt your body with a simple beach ball. Tone difficult areas with tilt-a-whirls, dipsy dos, squeeze play, close reaches, reverse lunges, pendulums, hold your own and tummy toner exercises.

Don't have time for a workout? Then watch this how to video to learn how to do a five minute workout that will get you six pack abs. These exercise will target your upper abs, lower abs, and obliques.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

A year and change into its shift towards enterprise customers, Magic Leap has updated Lumin OS and the corresponding Lumin SDK with some key prerequisites for the business sector.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.