The Unity 3D engine is not only responsible for facilitating the creation of 60% of AR and VR content but it also plays a significant role in producing the immersive stories that increasingly push the boundaries of cinema.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Suddenly, Magic Leap's lawsuit against Nreal, as well as its barrier to entry in the Chinese market, appears to be as insurmountable as The Great Wall itself.

It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.

Apple's iOS 13 is nearly here. After four months of beta testing, the latest iPhone software update promises over 200 brand new features, like system-wide dark mode and an overhauled Reminders app. That said, it'll be shortlived, as Apple plans to release iOS 13.1 as a supplemental update just 11 days later. In fact, the company just seeded developers the fourth beta for iOS 13.1 today, Sept. 18.

Despite hints hidden in internal iOS 13 code, Apple did not unveil its long-rumored smartglasses at its annual iPhone launch event on Tuesday.

Augmented objects in the classroom are closer than they appear. Within celebrated the close of summer with Wonderscope's unveiling of a fourth installment in its iOS app, titled Clio's Cosmic Quest.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Magic Leap and Samsung are putting their money where their augmented reality plans are, with the former acquiring an AR collaboration technology and the latter funding a waveguide display maker.

If Google hasn't already demonstrated that it is serious about augmented reality, then it made it abundantly clear at the Google I/O keynote on Tuesday.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

While the long awaited HoloLens sequel is scheduled to arrive later this year, Apple may force Microsoft to share the AR wearables spotlight, if reports of the company's first entry into smartglasses territory end up coming to fruition.

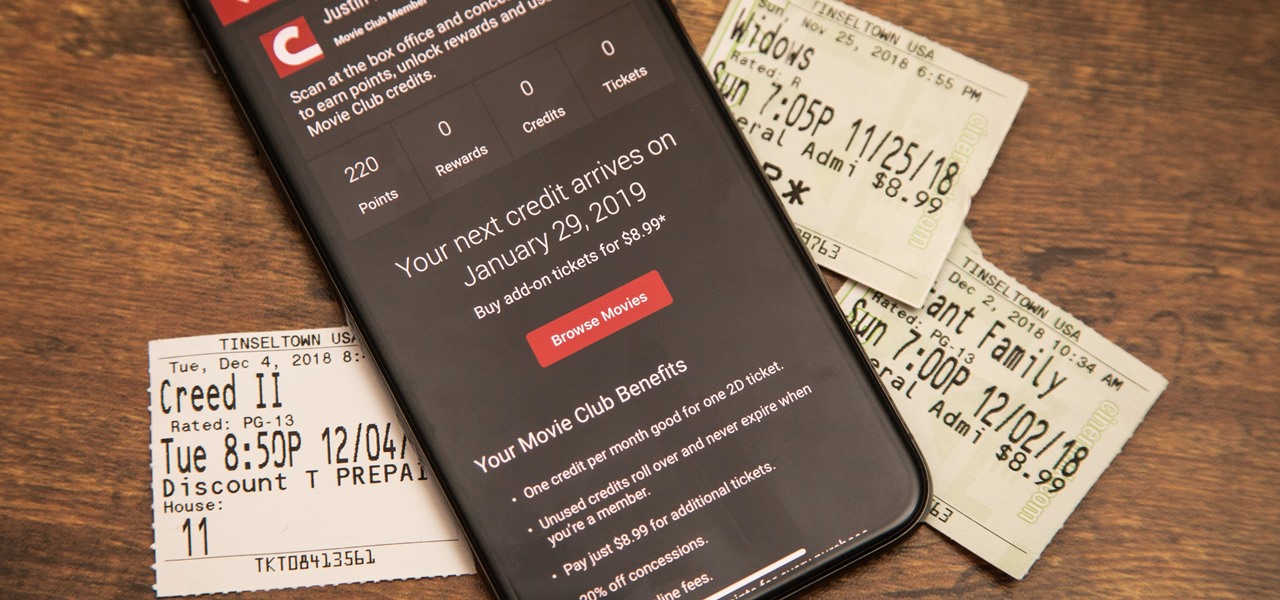
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan worth it?

Another contestant has emerged in the race to deliver a mainstream augmented reality car navigation system, with Silicon Valley-based Phiar picking up $3 million in seed funding to launch its own artificial intelligence-based mobile app by mid-2019.

Ingress, the godfather of location based-AR games developed by Pokémon GO creator Niantic Labs, is getting a new lease on life via Ingress Prime, a reboot of the game built on the Niantic Real World Platform.

A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

Augmented reality experiences for consumers, for the most part, are relegated to mobile devices at present, but creation and development of those experiences is still a province of desktop computers.

For those of us who love to multitask, picture-in-picture mode is a godsend. The feature, introduced in Android 8.0 Oreo, lets you enjoy videos in a floating window overlaid on top of another app. However, while the OS does have native support, only a select number of apps support the feature.

While it has been slower to arrive than a walker limping through thick Georgia mud, location-based augmented reality game Walking Dead: Our World finally has a confirmed launch date: July 12.

As summer is upon us, new musical Snapchat lenses are as well. This week has entries from Maroon 5, Simon and Garfunkel, and Snow Tha Product with entertaining visuals to match. As kids start to leave school for the summer, expect the lens scene to be kicked up a notch with anticipation.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

Noted analyst Gene Munster is predicting that Apple's initial entry into the augmented reality wearables category will be a year later than previous reports have estimated.

It appears we're in the midst of an augmented reality art boom, because in the same month that the famed Christie's auction house launched its mobile AR app, leading art gallery and art seller Saatchi Art has also announced its entry into the AR space.

Mobile gamers are well aware of this, but zombie shooters have become pretty stagnant and unimaginative in recent years. Too many entries in this genre feature the same cookie-cutter gameplay, but thankfully, Gameloft aims to change this. The company has soft-launched Dead Rivals in a few countries, and with a little work, you can try the game yourself right now.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

Google just released Android 9.0 Pie, but the Android community is already working its magic. Developer Quinny899 quickly ported the updated Pixel Launcher from the new build, so you can try it out on other phones right now.

While the company is adamant that the Magic Leap One: Creator Edition will ship this year, currently, it seems its CEO is more interested in striking deals with content partners than releasing details about the headset.

Now that we finally have vertical plane recognition in ARKit (at least on a developer level until the spring iOS 11.3 release), the real promise of mobile augmented reality is beginning to come into focus on iOS. But a new report indicates that a major near future advancement of ARKit that could change everything has been put on hold by Apple.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

For those who thought the action in Pokémon Go was a bit too pedestrian, Father.io wants to recruit you for a multi-player, first-person shooter that unfolds on the streets of your own city.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

One of Android 8.0's central themes was battery improvements. Google implemented background restrictions and a few other under-the-hood changes, but the biggest battery-saving measure was almost user-hostile: A static notification that tells you when any of your apps are running in the background.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

The Xposed Framework lets you modify your phone's software like nothing else. But because of how powerful this tool can be, it seems like things are always in development. This is certainly the case with many Xposed modules, to the point where some have several alpha and beta releases before they go mainstream.

The Google Assistant comes in several different flavors. There's the baked-in Google app on Android, the dedicated Google Assistant app on iOS, and the Assistant-powered Google Home smart speaker. But no matter how you access it, your Assistant will only get better if you take some time to personalize things.

The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

Yogurt is more than an excellent source of protein, calcium, and gut-healthy probiotic bacteria. A protein isolated from probiotic lactobacillus bacteria in yogurt is capable of inhibiting drug-resistant bacteria.