Chair massage is all over now, even airport terminals. A chair massage is wonderful when we don't have a table and we're in an office or in front of a computer at home. Learn the art of giving a chair massage in this health how-to video.

A facial massage can rejuvenate and soothe. Make sure your hands are clean to begin with. A lot of people don't like oil, having oil in their hands and putting it on their face, or they might be allergic to it or sensitive. So have a nice clean set of hands and starting with just saying hello to the head. Learn the art of giving massage in this health how-to video.

Shiatsu massage is increasingly popular. In shiatsu, we use the tools of our hands, especially our thumbs. We also use our elbows and forearms for rolling. Learn the art of giving Shiatsu massage in this health how-to video.

Massage yourself with oil to relieve stress and soreness. You don't really require that much oil. Our skin has a lot of oil already. Use a little bit of oil, rub it on your hands and go deep. Treat your muscles with self massage in this health how-to video.

Petrissage strokes are a special technique of massage. Petrissage is mostly kneading like you're kneading bread. Just like if you had a big loaf of bread and you're just kneading that bread, all that flour coming in. I'm using the bottom V, corner V of your palms, wherever your pinkie comes in to touch with your thumb, and that's basically what I'm using with my hands. Learn the art of giving petrissage massage in this health how-to video.
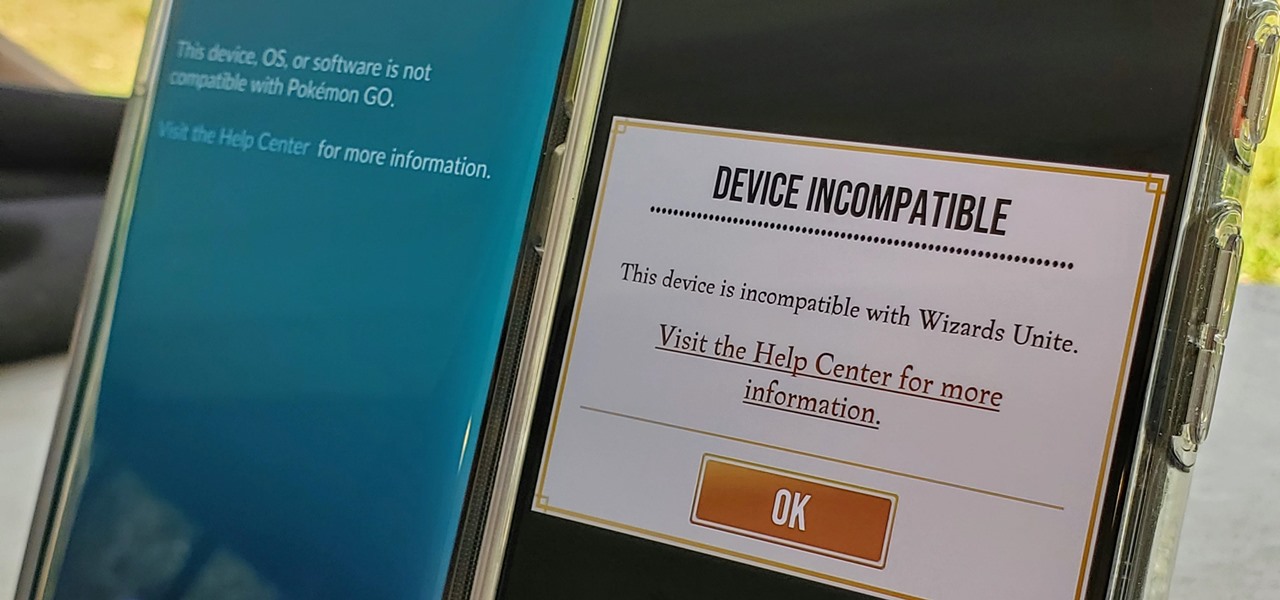
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

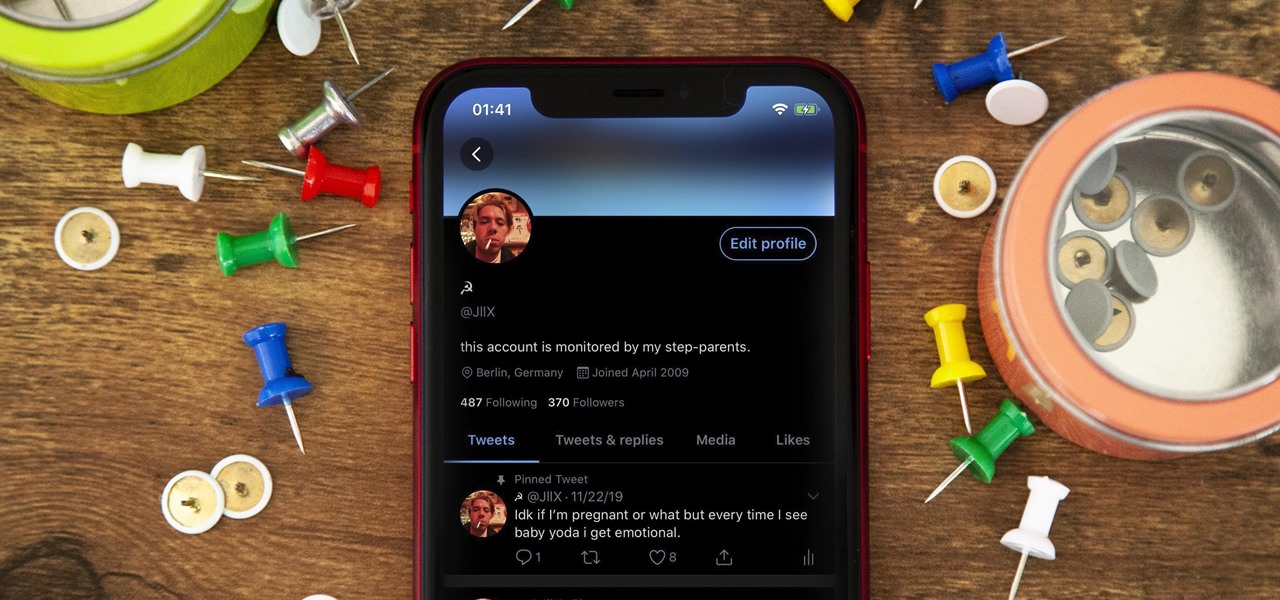
Pinning a tweet is a great way to get the point across because it's the first post people see when they visit your Twitter profile. When you pin a tweet, reply, or retweet, it sticks to the top of your profile, whether you create new tweets or not. It's the perfect spot to place one of your more popular tweets, a fantastic blog you wrote, or even just a joke that shows your personality.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

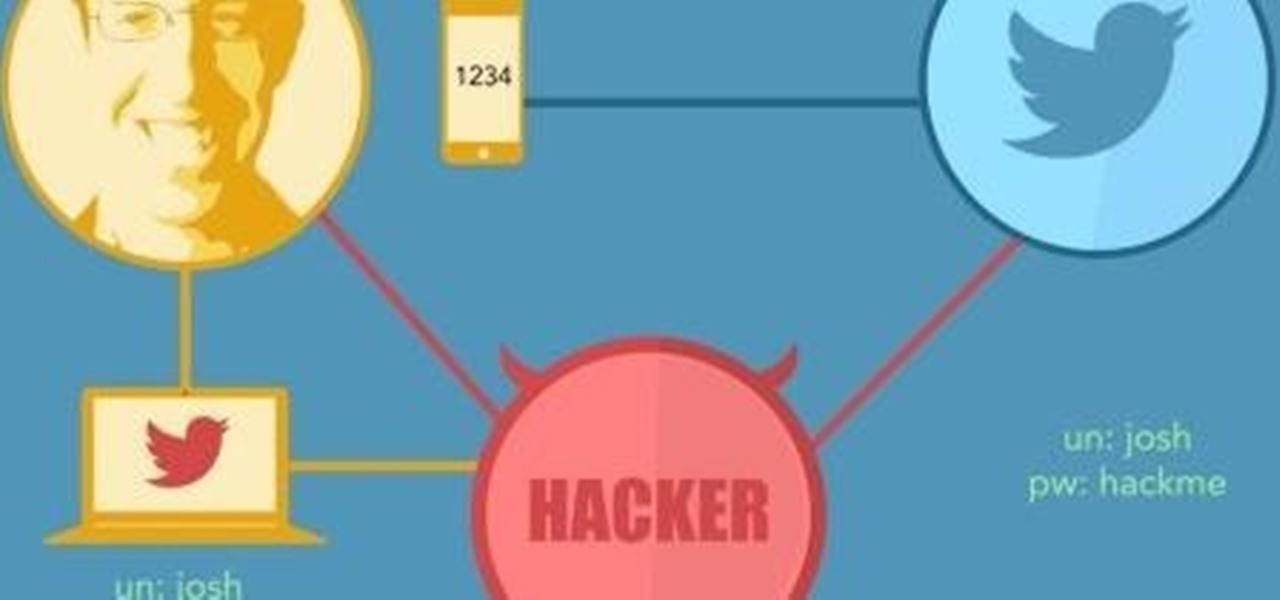
The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

It was only a few years ago when the idea of a 5+ inch display on a smartphone was unreal. With most hovering around four inches at the time, a phone that big seemed impossible to hold. We've come a long way since then, but it appears another wave of large displays will soon hit us, and they are all at least six inches.

It's Friday, April 6, and that means it's time to look at some of the hottest lenses from the past week created by Snapchat users everywhere. Some memes are evergreen, some dissolve within a week, but these lenses are blazing hot right now in snaps across the platform. If you don't want your friends laughing at your weak lens game, you've gotta try these out right now.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

A new stories archive feature appeared in the version 25 update for Instagram on both Android and iOS. This means you no longer need to save stories to your phone for later viewing, if you like doing that, but it also means all those stories are saved to your Instagram account whether you want them to be or not.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.

It has been an interesting few days in developer news. The Microsoft blog has been busy with information relative to the augmented reality space. Meta 2 has also announced an interesting development this week. Here is a collection of various tidbits that have been collecting up.

Building virtual portals are popular practice for developers to demonstrate the "wow" factor of augmented reality.

It's never fun when you install an app and then proceed to be bombarded with constant notifications. The SoundCloud app, while great in other regards, tends to have a bit of an issue on this front.

With the release of Apple's ARKit comes endless possibilities for education and learning. One of those possibilities is an AR rotating model of our solar system in your room, another is using AR to instantly know the nutritional value of food items.

If you want to share a video to Stories — but it's over 24 hours old — it may seem like you can't, but there's actually a simple hack on how to do just that.

Pokémon GO's augmented reality journey is continuing with Apple's newly announced ARKit. It's no surprise considering Pokémon GO is the largest mainstream augmented reality game, with 500 million downloads.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

Reddit announced this morning, April 7th, that it has finally released an official mobile app. You can get it on Android and iOS.

This tutorial is quite an epic, so get a cuppa, kick off your slippers, sit back and relax as we go through a few great inking & blending techniques.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Learn how to remove blackheads from nose and face, naturally at home! Video: .

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

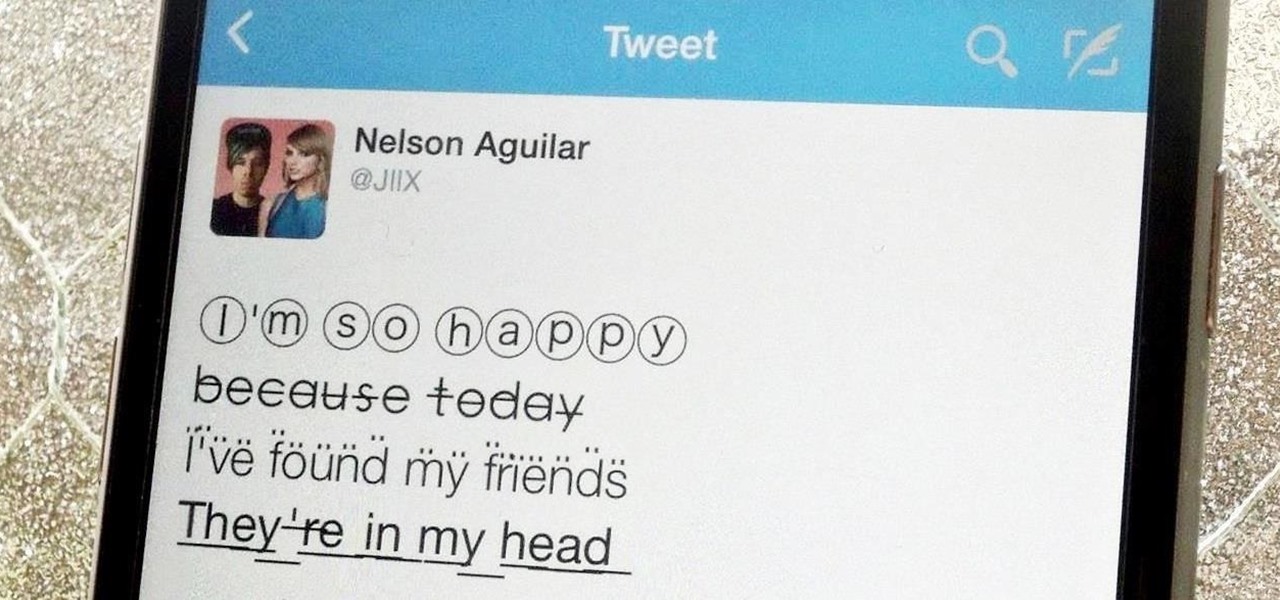
Aside from media, there's not a whole lot you can do in 140 characters to make your tweets stand out. You can use emojis, but they aren't exactly ground-breaking. However, now you can use Bedazzle, a Chrome extension from Gordon Zheng that'll allow you to add "rich text" to your tweets.

The bumper for bObsweep Pethair and Standard are installed the same way. It holds the sensors that allow Bob to see any obstacles in his path. If a repair of the wall detection sensors is needed, the steps for replacing the whole bumper are the same when working on either bObsweep model.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...