When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to grow into something that enlightens everyone involved. The community around an idea can actually make or break these new ventures — and this applies to augmented and mixed reality as well.
Android O has finally arrived—well, it's technically a beta version, but that isn't stopping Android enthusiasts from going crazy about it. The first Developer Preview was released earlier today and is available right now to install on Nexus and Pixel devices. While Android O doesn't have an official name or Android number yet (we're betting on "Android Oreo"), Google has released a feature list and a blog post explaining almost all of the new changes and features.

General Motors acquired Cruise Automation in March 2016 for a reported $1 billion (well, at least $581 million). GM President Dan Ammann made a point of being in the press release photograph with Cruise founders Kyle Vogt and Daniel Kan (see photo below). On January 19, 2017, Vogt posted on Twitter: "Took GM Pres. Dan Ammann for a ride in a Cruise AV."

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

To some people, Thanksgiving is merely quality time with family and friends that they can't get throughout the rest of the year. To others, it's that one time when it's okay to be a greedy hog and get hammered all weekend long.

There was once a time when everyone scoffed at the turmeric tonic tea sold at the coffee shop I work at. Funny, because as of recently, we seem to be selling out. How can this be explained? Beyoncé must have been spotted buying turmeric beverages on the cover of some celebrity magazine. That's got to be the only way to explain its sudden popularity, right?

The decadent, chewy, fresh-from-the-oven brownie is a classic American dessert. US History Scene states that the first brownies ever made were a result of socialite Bertha Potter Palmer's request of her chef at Chicago's Palmer House Hotel in 1893 "to create a dessert that could be tucked into a box lunch for ladies to eat while attending the Columbian Exposition."

During our high school years, one of us (hint: her name starts with a B) worked at Cold Stone Creamery. She loved working there, and from this love emerged a fascination with adding creative ingredients to plain ol' vanilla ice cream.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

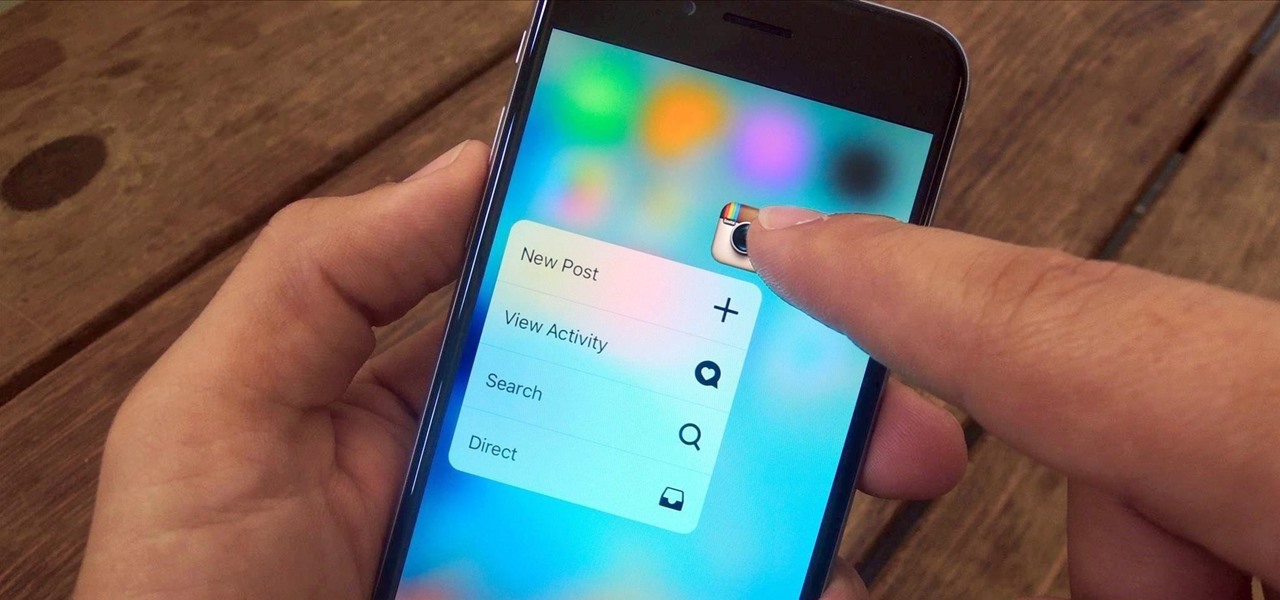
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

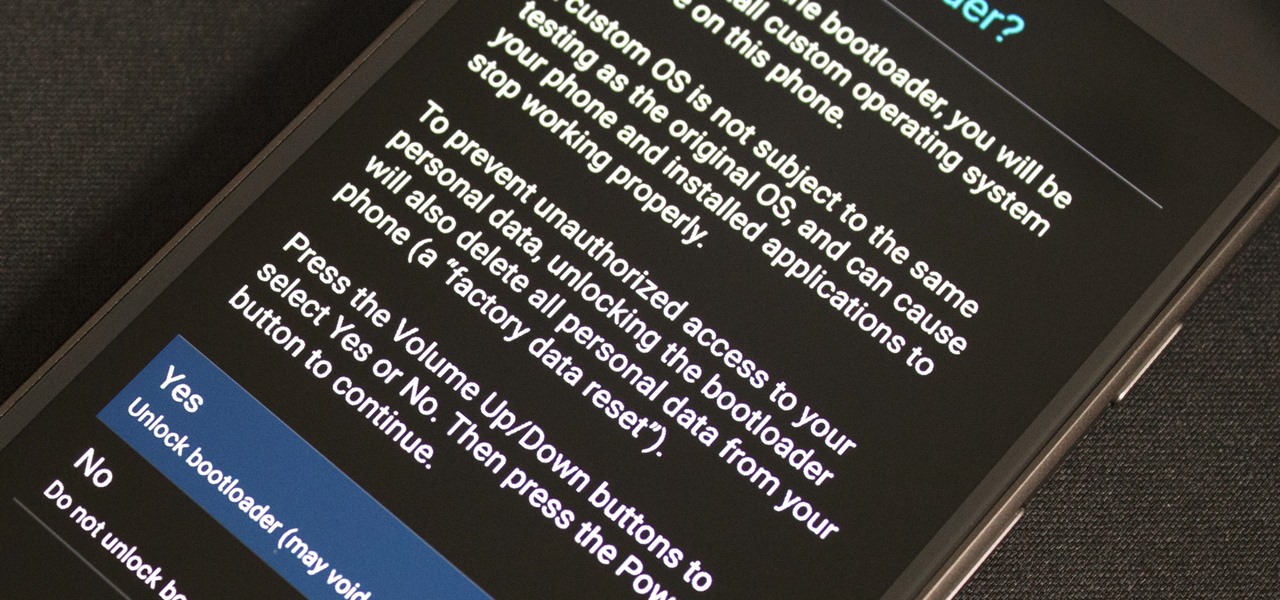
Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

After you have registered to this site,sign in then to start missions. Basic Missions
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

While most people build collections of things with intrinsic value such as coins, stamps, or rare post cards, I collect wine corks—the natural ones, not the plastic kind. Corks are a natural product harvested from the cork oak tree. It takes the better part of 10 to 12 years before a tree can have its bark manually removed for the production of cork. Thankfully, no tree is harmed in the process and in 12 years, the tree bark can be harvested yet again.

We always want to find more ways to help brilliantly lazy cooks make great-tasting food and save money and time in the process. Luckily, our Facebook fans are invaluable sources of information when it comes to getting cool tips, behind-the-scenes info, and more.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

I've been using the Photo Sphere Camera from Google on all of my Android devices ever since it came out on Jelly Bean 4.2, which lets me create riveting 360° panoramic images.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Like many other smartphones these days, your Samsung Galaxy S4 is built to handle multitasking like a pro. With a 1.9 GHz processor and 2 GB of RAM (specs comparable to laptop computers just a few years ago), this powerhouse of a phone can switch between apps with supreme ease.

Why can't I see who is stalking my Facebook profile?

Amongst the many rumors emerging about the upcoming Samsung Galaxy S4, one that seems like a fairly sure bet is the inclusion of Google's Photo Sphere feature.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.