Snapchat's face tracking has certainly come a long way. This week, we've got an example of one effect that is nearly guaranteed to freak out your friends.
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

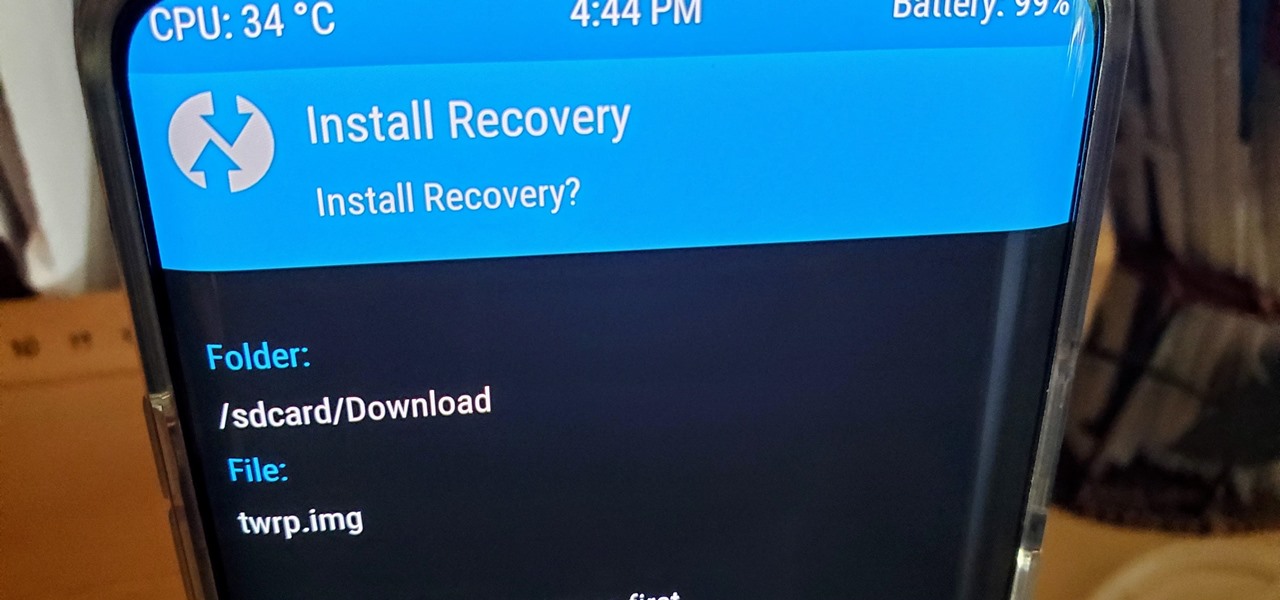
When it comes to modding your Android device, you'll want to be familiar with the TWRP name and what it stands for. It's a tool that you'll be using to make NANDroid backups or to install just about any mod file you can think of — the number of uses is quite awesome. You'll mostly be after Magisk for root access and potentially a custom kernel as well.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

One of the biggest downsides to rooting is that it can be a pain to update every month with each new security patch. With other phones, you might have had to fully unroot the device, maybe flash a stock recovery, or potentially even flash all the factory images to get a new update. Thankfully, OnePlus has made this process super simple for us modders.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Unlike VR, when you're talking about augmented reality, describing what an experience is like can be incredibly difficult — primarily because the experiences are even more contextual than relatively static virtual worlds that don't involve real-world settings.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

One of Android's biggest strengths is its flexibility. There's usually more than one way to perform the same task, which makes it easy to find an alternate method that works better for you. Android also has some hidden features that newer users might not be aware of, so we made this list to highlight lesser-known tips and tricks.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming.

When they first appeared, smartphones came with a promise to make our lives easier and make us more productive so we could have more free time and energy. But now, the average user spends almost 5 ½ hours daily on their smartphone. If that sounds like you, there are ways to use your iPhone more efficiently — without getting sucked into distractions.

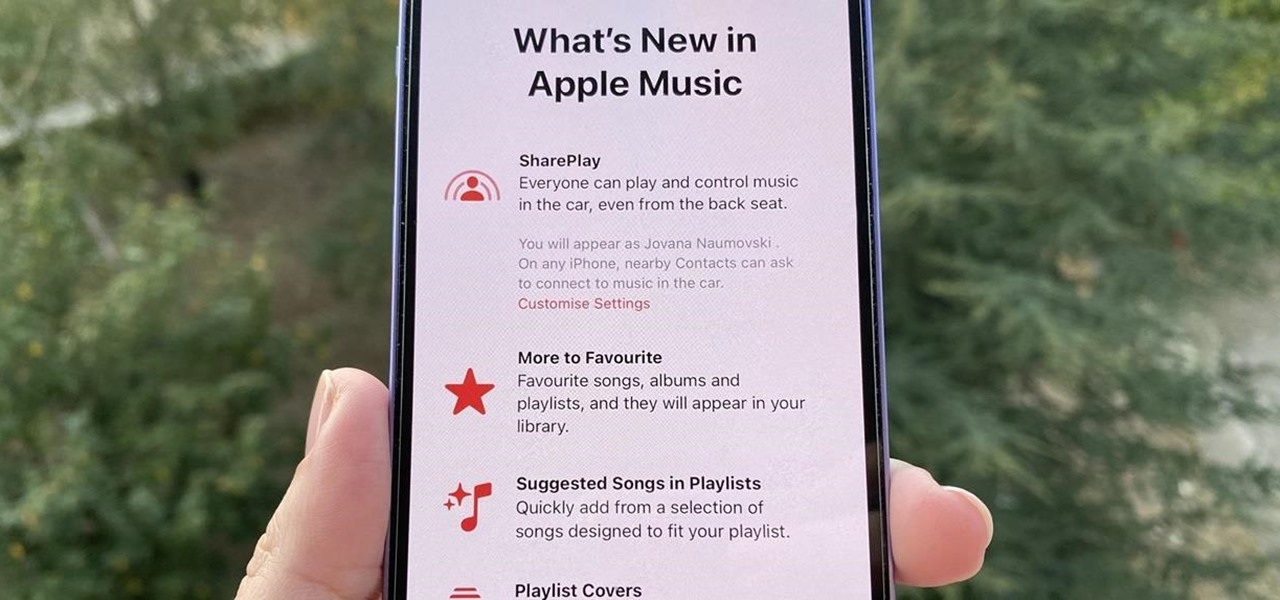
In case you missed it, Apple has added a lot of new features and enhancements to the Music app on your iPhone, changes that benefit both Apple Music subscribers and non-subscribers. Chances are, you haven't seen all the changes yet, especially since many of them weren't released when iOS 17 first came out, but we'll go over them all with you.

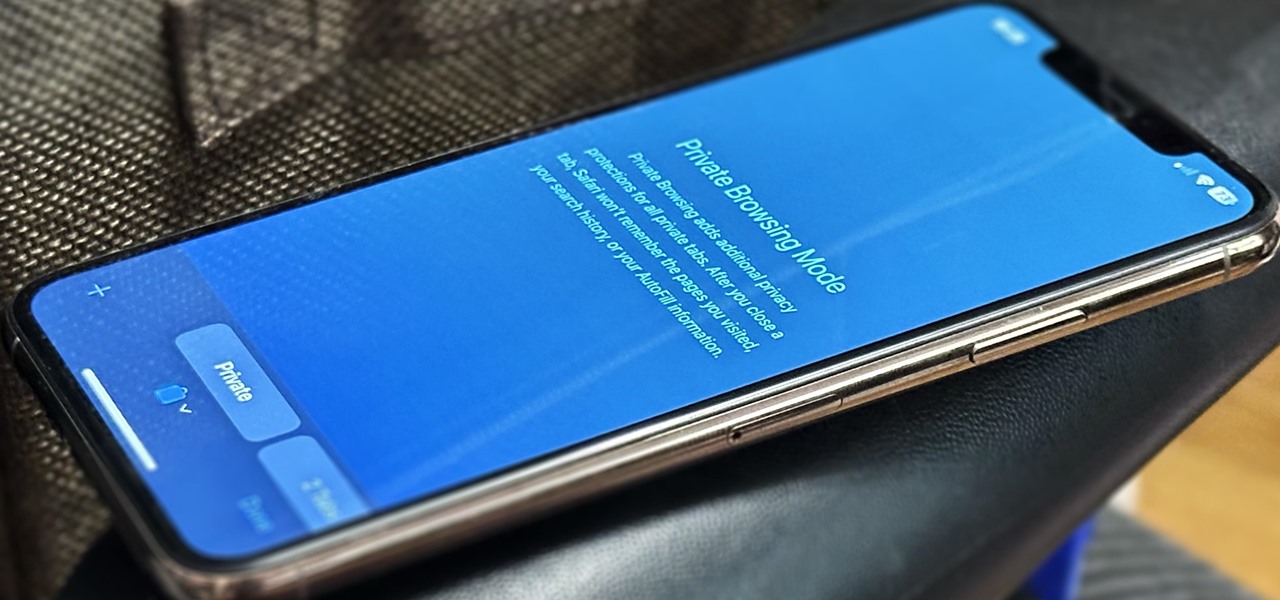
Private Browsing mode finally lives up to its name in Apple's huge Safari 17 update for iPhone, iPad, and Mac. So whether you search for things you don't want anybody to know about or want to ensure websites and trackers aren't eavesdropping on your activity, you'll want to update your devices pronto.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

One advantage to using Apple's ecosystem is Continuity, which allows you to move files, media, and tasks seamlessly between all your Apple devices. It even lets you use one device to help with actions on another, like unlocking your Mac with your Apple Watch or using your iPad as a second display. Now, things are even better with Continuity with Handoff's new FaceTime functionality.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

If you've ever been in a crowded, noisy place, chances are you've dealt with having to talk louder just so the other person can hear, and vice versa. You can alleviate this headache in the latest Pixel update by using the Sound Amplifier app's new conversation-geared tool.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Apple just released the second public beta for iOS 14.5 today, Wednesday, Feb 17. The update comes just one day after the company seeded developers the second 14.5 beta. Because of that, we've had 24 hours to sink our teeth in beta 2's new features, like 217 new emoji, Apple Music lyric sharing, Apple Music UI updates, and new Shortcuts options.

Apple released the second developer beta for iOS 14.5 on Tuesday, Feb. 16. The update comes 15 days after Apple seeded developers the first 14.5 beta, which included a slew of new features such as default music app support, compatibility with PS5 and Xbox Series X controllers, and more.

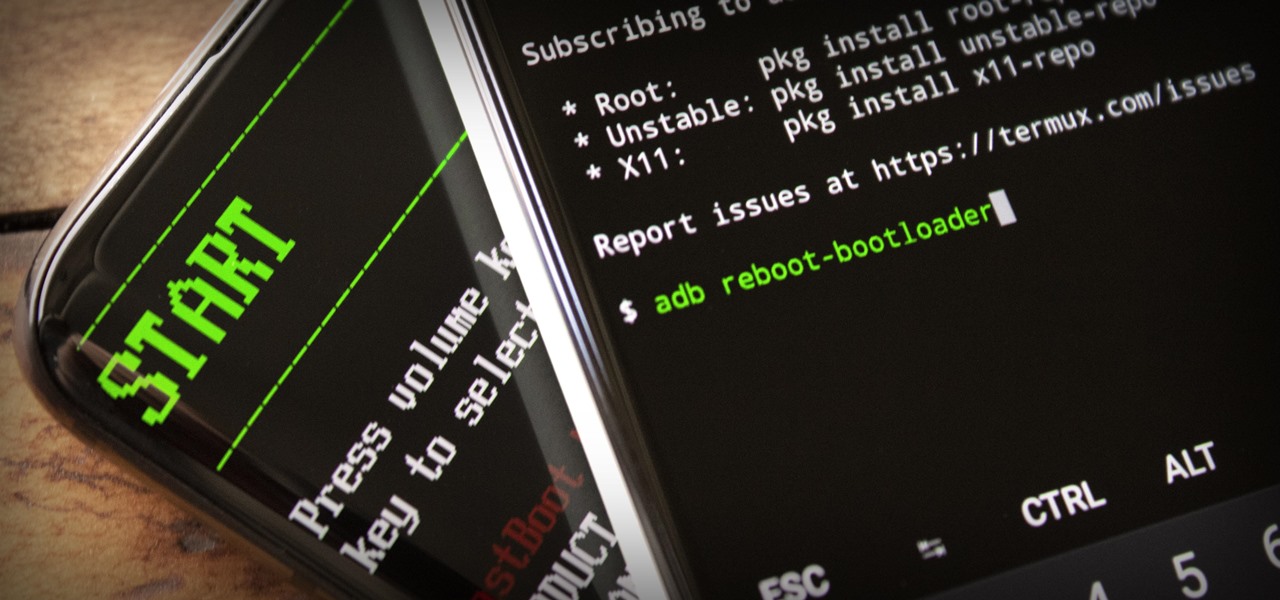
ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.

The iPhone has a setting that will obfuscate the content of notifications on its lock screen until you're recognized by Face ID. Google implemented this same feature in its Pixel phones, but many Android devices have no such option. At least, not by default.

We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly but deliberately worked to build itself into a viable competitor in the enterprise space via its wearable display technology.

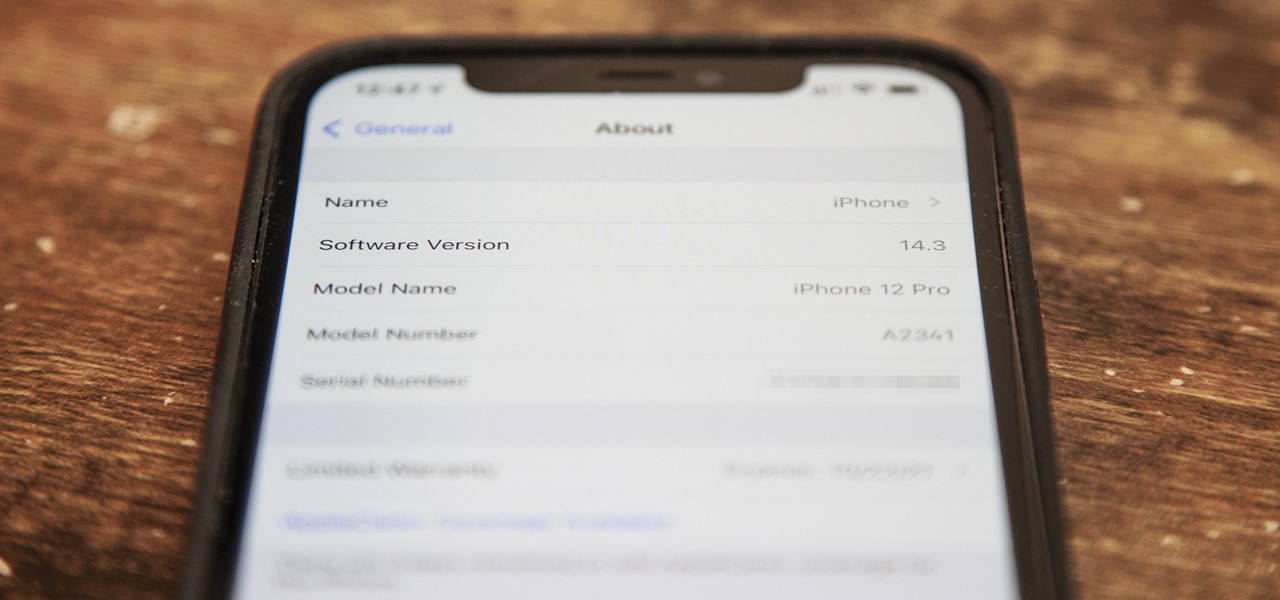
Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iOS 14.3 to use all of its features.

Apple's first release candidate for the iOS 14.3 beta came out on Dec. 8, but there must have been a serious bug in the system because iOS 14.3 RC 2 followed it just two days later on Dec. 10. These builds highlight everything that you should expect to see on the stable version very soon.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

Even though the Music app took a backseat during Apple's initial iOS 14 announcements, there's a lot going on in the updated app. Some of the new features and changes apply only to Apple Music subscribers, while others apply to your own music library, so there's something for everyone.