4DViews, the volumetric capture company that films actors and performers in augmented and virtual reality for things like movies, TV series, and applications, has just released the app 4DViews: Raise Virtual to Reality, to demonstrate its technology for smartphones.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

According to multiple users on Reddit, the Pixel and Pixel XL's camera can have some serious auto-focus issues if you're using a certain type of case with Google's new flagships. When the problem occurs, your camera app will refuse to settle on a focus point, making almost everything in the frame blurry. Redditor HeshoMike uploaded a video of the phenomenon, and you can see it in action here:

Despite its battery issues, the Samsung Galaxy Note7 is one impressive piece of machinery. Packed to the brim with loads of RAM, a top-notch GPU, and one of the best processors on the market, this thing should be able to zip through any task you throw at it with lightning-fast speed.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.
If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

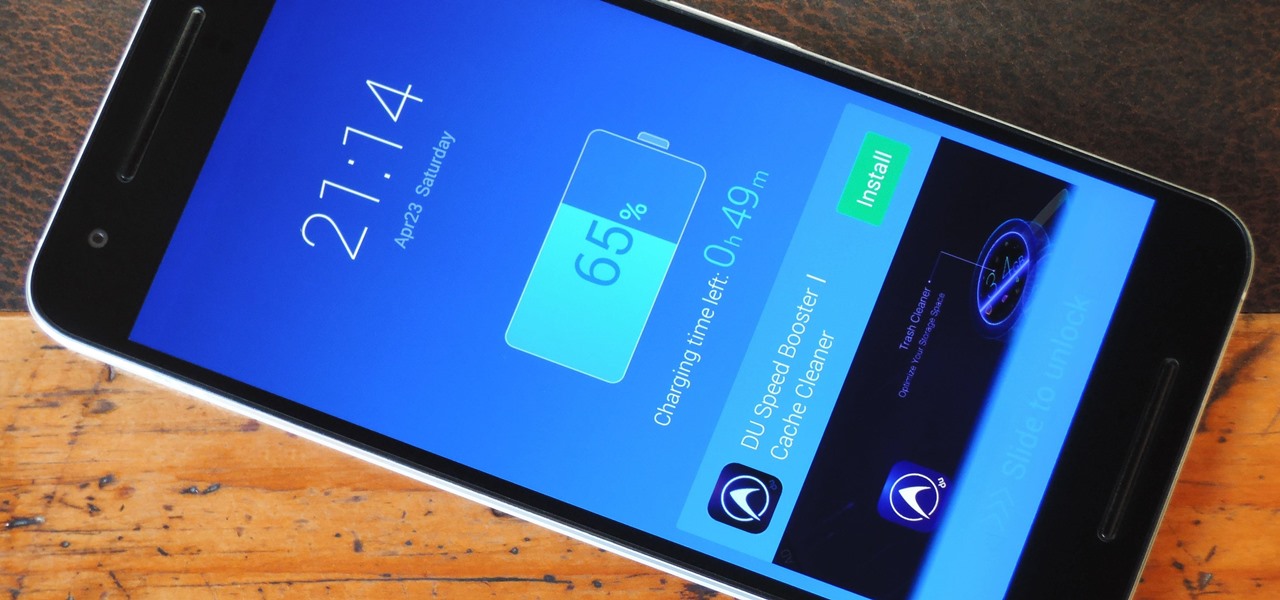
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.

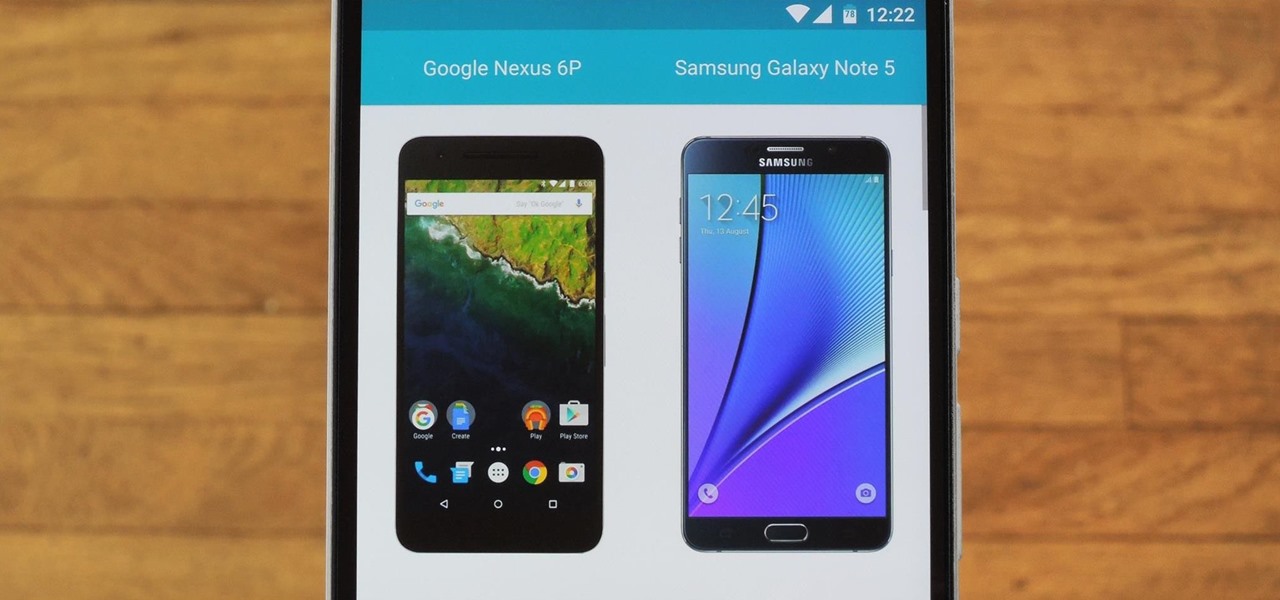
Shopping for a new phone is an entire ordeal. Even when you've narrowed it down to a few choices, comparing the finalists can be difficult, because specs and prices are scattered around on various different manufacturer websites, and if you're trying to do this on your current phone, most of these websites aren't optimized for mobile viewing.

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.

With audible alerts and subtle vibrations, the Apple Watch makes it difficult to miss incoming notifications. But soon enough you'll realize that not every notification is worth receiving on your Watch and can ultimately render the experience annoying under particular circumstances—like when your popular Instagram post floods in notification after notification.

Most custom ROMs are built from the freely-available source code of AOSP, so they share a lot of common ground with stock Android. The difference, though, is the fact that Google adds many minor tweaks and finishing touches to AOSP while creating the version of Android that ultimately comes pre-installed on Nexus devices.

I passed a cool looking bar the other day that I wanted to check out. When the weekend came around, I was ready to go, but for the life of me couldn't remember where it was. Not wanting to retrace my steps or drive around aimlessly, I gave up.

If you're like me (and everybody else probably), you probably have a few nights of reckless drinking that you wish your could take back, or at least turn down a notch.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

You don’t have to wait to get to the golf course to practice your strokes. You’re swing path and swing plane will improve by doing these exercise and ultimately leave you with a straighter hit. This drill can even be done inside.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

After closing its office last year, enterprise AR company Daqri has moved on to the final stage of its lifecycle with the liquidation of its assets.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

Halloween may be finished, but the augmented reality chills are not over yet for some people. Arachnophobes are bravely facing their fears by cozying up to augmented reality spiders for a university study.

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

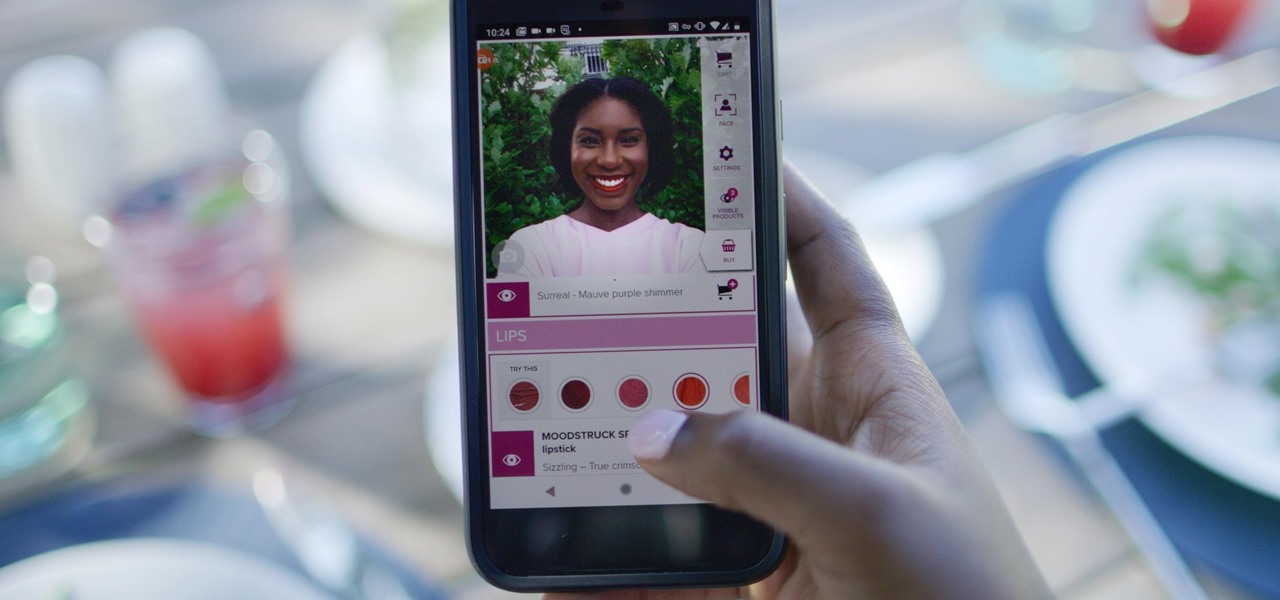
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

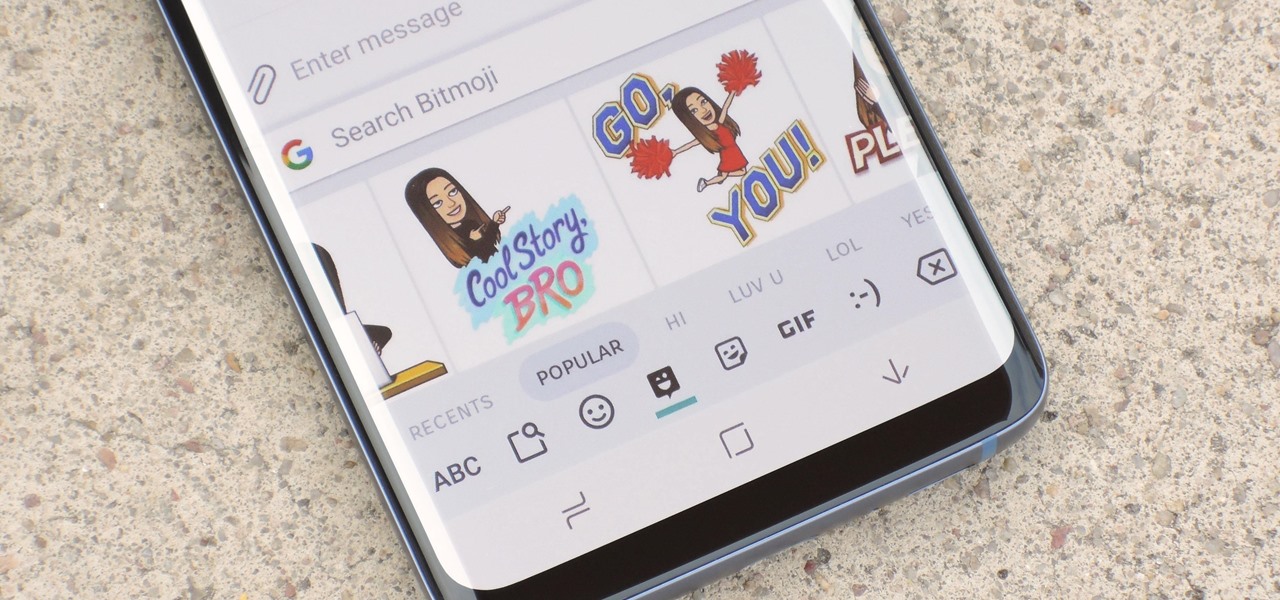
Bitmoji are personalized emoji that look like you and can be used to make funny memes or snappy replies. Normally, you have to find one of these reaction emojis in the Bitmoji app, then use Android's share menu to send it to the app where you ultimately want to post it, but there's a much better way.

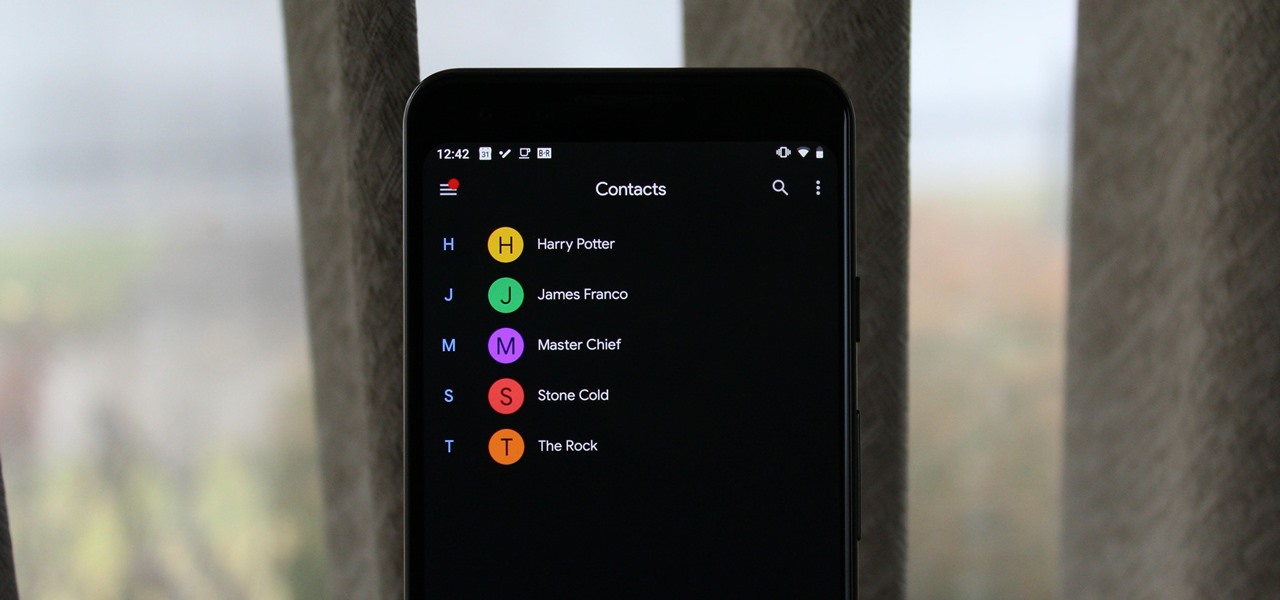
With the rise of OLED displays, Android users have been begging Google for a true system-wide dark mode for years. While a system-wide solution is still somewhat unlikely, Google has given in by providing a dark mode for certain apps, including Contacts.

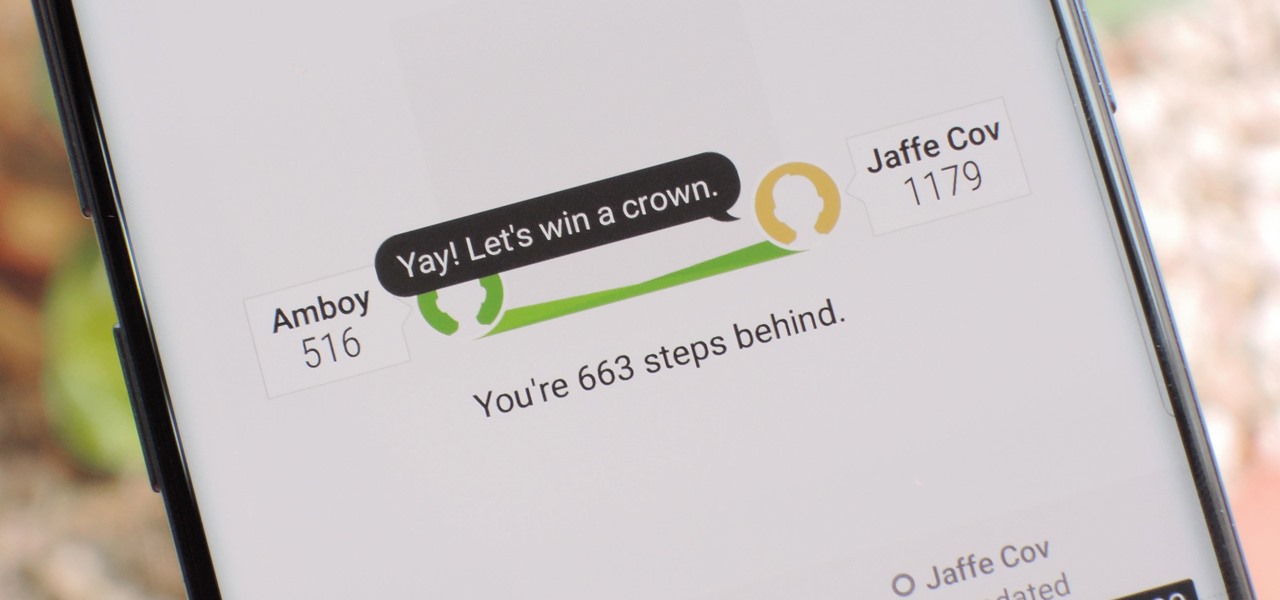
When you're trying to get fit, friendly competition can go a long way towards keeping you motivated. Samsung Health has a great feature for just that, letting you challenge your friends or even complete strangers to bring some excitement to an otherwise routine workout experience.

WaveOptics, makers of diffractive waveguides, has inched closer toward getting products featuring its technology to market through a production partnership with a consumer electronics company whose clients include Google, Microsoft, and Sony.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

The shifting sands of immersive computing, currently fluctuating between augmented reality and virtual reality, can be hard to navigate if you're only versed in one of the platforms. But a new series of videos from Leap Motion paints a picture of a near future world in which AR and VR will seamlessly merge together, forcing us to change the way we see both.

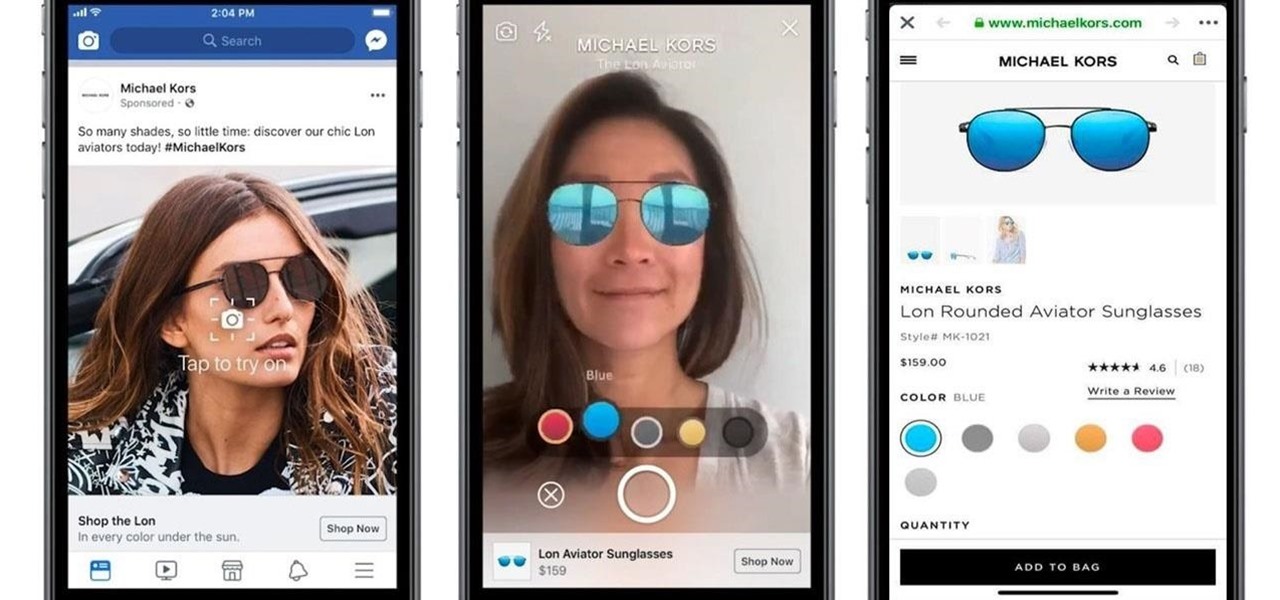
Facebook is preparing to make augmented reality experiences for brands more visible in its mobile app with Tuesday's introduction of augmented reality ads in its News Feed.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

If you're on a limited data plan, you no doubt set Google Photos to only back up over Wi-Fi on your Android device. In recent months, however, there have been many complaints that Photos won't actually back up your pictures when you get back home and connect to your network. Thankfully, the fix is fairly simple.

Samsung's Galaxy S9 was recently announced with features like AR Emoji and Dual Aperture, but great functionality lives underneath them — such as the ability to have your home screen auto-rotate to landscape mode. It's a nice feature, but with a little work, you can already do this on any Android phone.

On Tuesday, NBA Commissioner Adam Silver joined Magic Leap CEO Rony Abovitz on stage to unveil a partnership between the two companies.