HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.
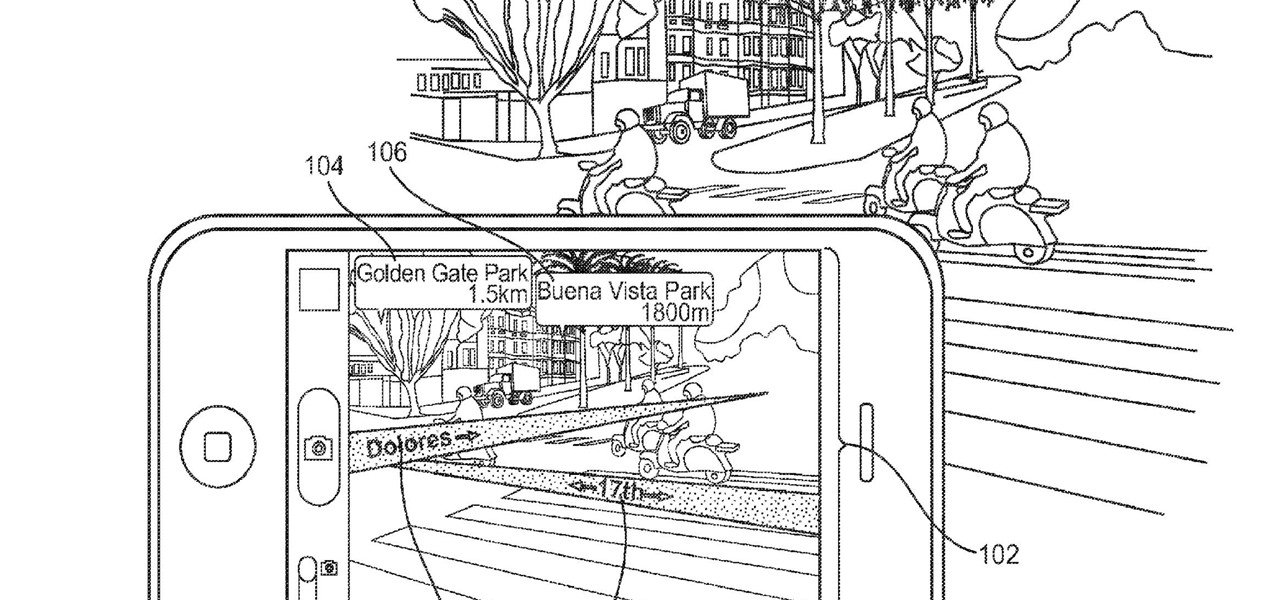
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

Google Assistant has introduced tappable shortcuts on the Google app for Android, iOS, and Google.com this week.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

If you've played the game Portal by Valve before, you've most likely popped one portal onto the ceiling and another directly below it on the floor, dropped your Companion Cube in, and then watched it fall forever. Well, now it has been done in real life, in an actual hallway, not in a rendered world.

If you're in the Windows Holographic community of developers, make sure to mark your calendar and set your alarms for February 8, 2017 because it's Windows Developer Day.

Leave it to some lazy college kids to attempt to figure out a way to brew a pot of coffee without leaving the couch.

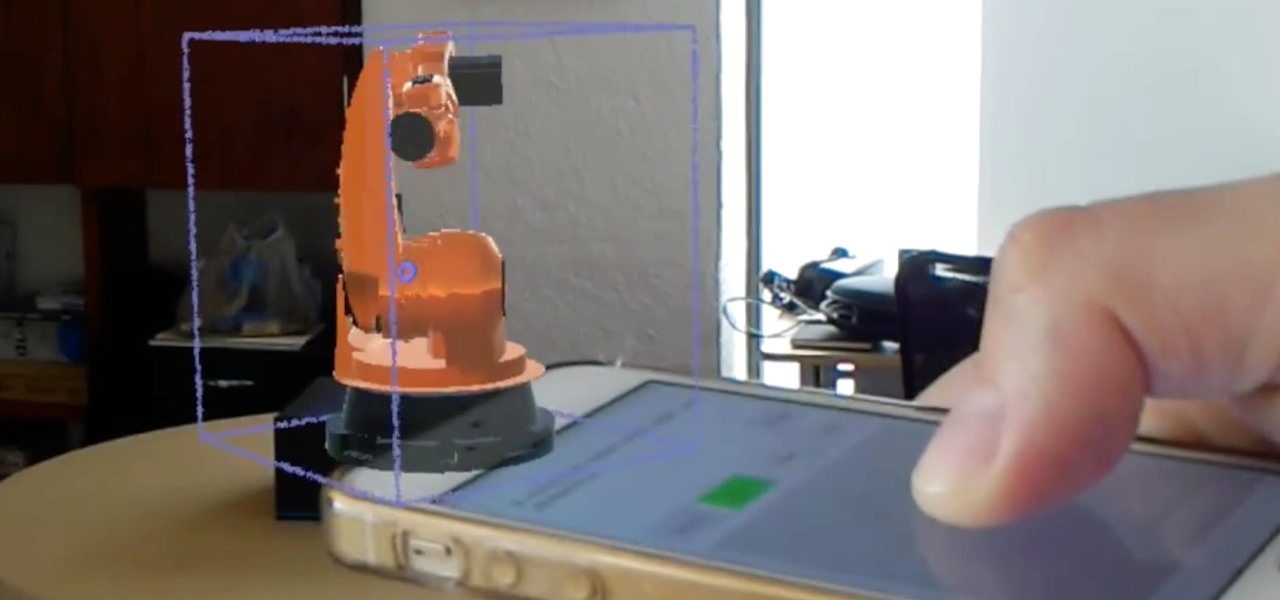
We've highlighted the projects of Wavelength Studios a few times over recent months for their work in the augmented and mixed reality space. Since receiving their HoloLens headsets, they've been hard at work on both development community projects as well as efforts for clients. This brings us to their latest work—a way to control holograms on the HoloLens with our pocket-based modern miracles, also know as smartphones.

According to multiple users on Reddit, the Pixel and Pixel XL's camera can have some serious auto-focus issues if you're using a certain type of case with Google's new flagships. When the problem occurs, your camera app will refuse to settle on a focus point, making almost everything in the frame blurry. Redditor HeshoMike uploaded a video of the phenomenon, and you can see it in action here:

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

Every recipe on the face of this planet (okay, maybe a slight exaggeration there) ends with the same six words:

After many months of endless speculation over the mysterious augmented reality platform Magic Leap, software engineers worldwide have been waiting for any news of what development environment this amazing technology might use. Thanks to Paul Reynolds, the former Magic Leap Senior Director of SDKs and Apps, we no longer have to guess. Just like existing mixed, augmented, and virtual reality platforms, developers will be able to use their experience with Unity and the UNREAL engine.

The one big question remaining about Google's upcoming Pixel phones has finally been answered: Yes, the Pixel and Pixel XL have unlockable bootloaders—at least, if you buy directly from Google.

Now that Google has announced its new Pixel smartphones, folks who rushed to buy an iPhone 7 might be experiencing a bit of buyer's remorse. The new Pixel and Pixel XL are packed to the brim with cutting-edge features and top-notch hardware, and Google seems to be taking direct aim at the iPhone 7 with its Pixel marketing (and their groan-worthy jokes during the keynote).

We're all for heaping piles of shredded cheese on our tacos, but what if all that cheese could actually be the taco shell instead? Since this was perhaps one of the more profound food questions we've had in a while, we wasted no time getting to the kitchen and tackling this cheesy challenge.

A lot of folks complain about the extra features Samsung adds to Android, but while there are some benefits to the slimmer stock Android, the TouchWiz firmware on Galaxy devices definitely has its own advantages.

As you get barbecuing this summer, you're likely to encounter a few grills that aren't exactly the cleanest. At parks or campgrounds and even on your friends' grills (or, um, your own), no one wants to place food on gunked-up grill grates.

Onion scrubs, salt and olive oil blends, a baking soda slurry... despite the many methods already out there to clean your (old or brand-new) cast iron cookware, there's one you may not have considered: using a potato.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

When it comes time to buy a new smartphone, the sheer amount of options on the market can make you feel overwhelmed. There are Android devices of all shapes and sizes with different functionalities and price points, and now, even Apple has three unique iPhone models to fit various budgets.

This delicious new trend is the lovechild of everyone's two favorite foods: hamburgers and sushi. Yeah, that's right... meet the sushi burger.

Let's set the scene: you're at home, it's late in the evening, and you have a hankering for those deliciously decadent chocolate-wrapped squares of ice cream goodness. You could drive to the store and pick up the usual pack of Klondike Bars in the ice cream aisle... or, you can easily make these babies in the comfort of your own home with only three ingredients for a fraction of the cost—in any flavor you want! The choice is obvious. So, without further ado... Ready, set, Klondike!

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

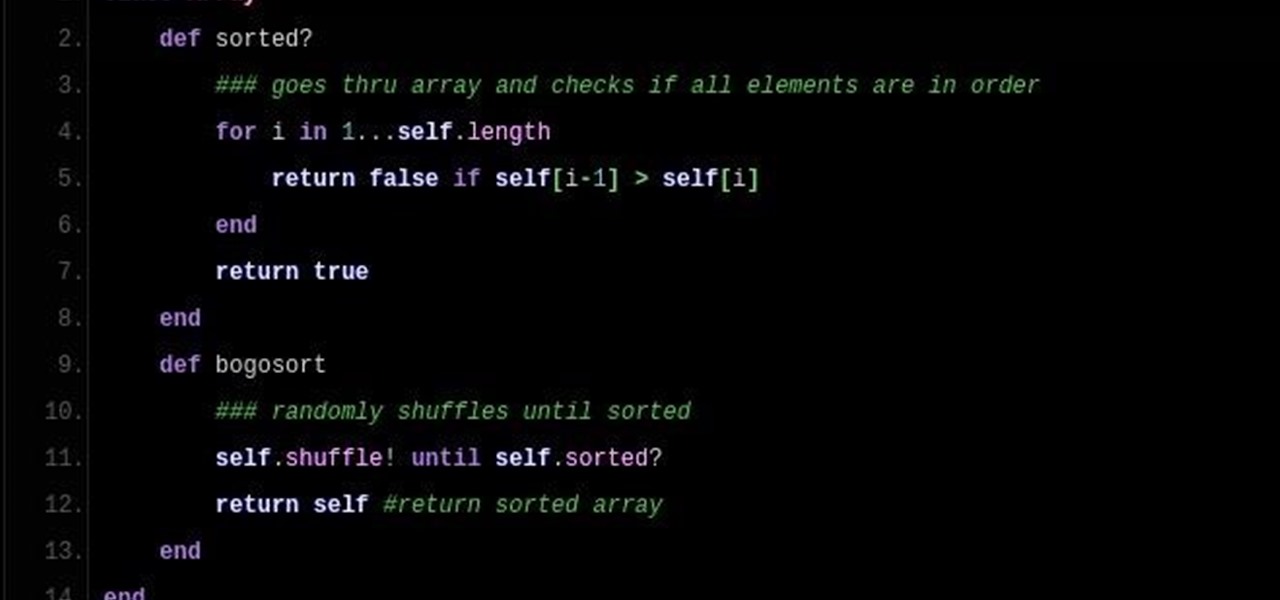
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.