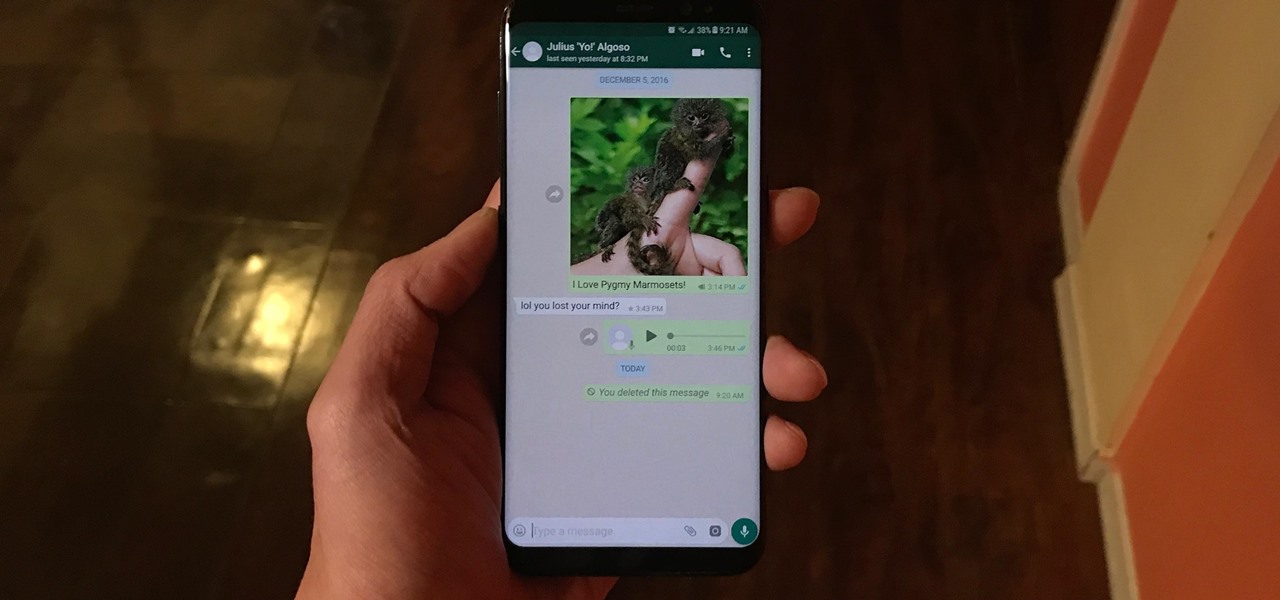
WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the sender, however, there are simple tricks you can perform to give yourself plausible deniability.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

When the Nintendo 3DS XL came out, I traded in my regular sized Nintendo 3DS for one — but I ended up hating it. The XL just felt big and unwieldy, and because the screens were larger (with the same resolution), it ended up looking blurrier than the regular 3DS. This, to a less severe extent, is the argument for the Galaxy S9 against the Note 8.

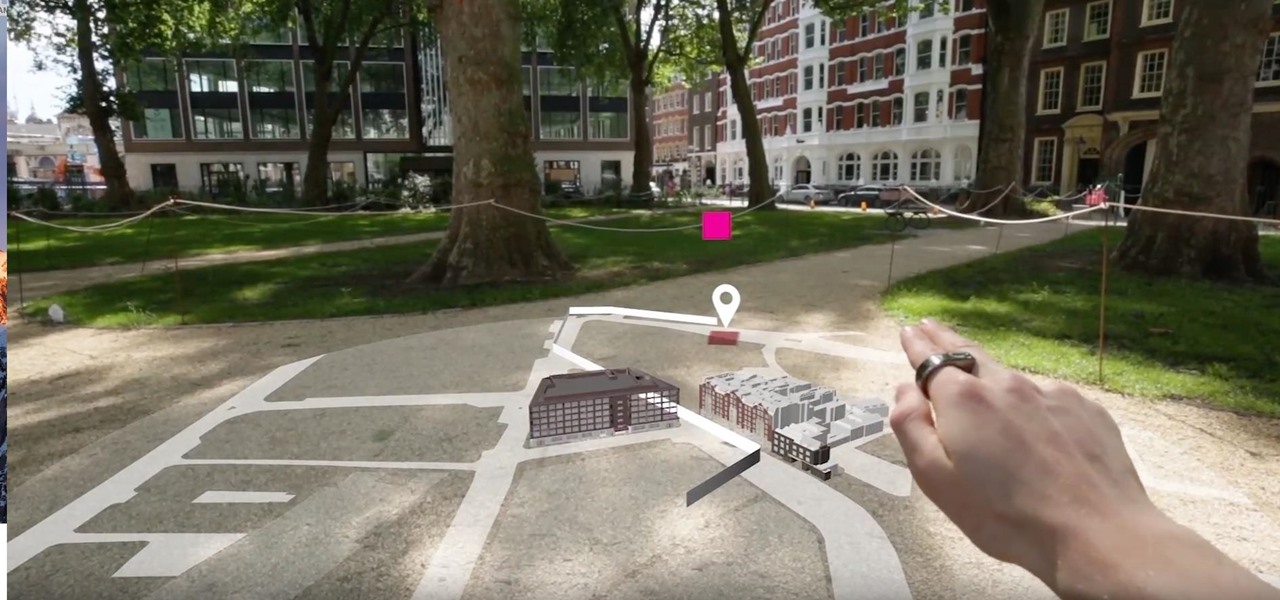
In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

HBO's Westworld has touched down on iOS as a mobile game, giving players the chance to manage their very own futuristic theme park set in the wild west. Unfortunately, the game is currently only available in select countries as a soft launch until its fully developed. But if you'd like to try out this game right now, there's a simple workaround to get Westworld on your iPhone.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Prior to Apple's earnings report on Thursday, the storm clouds were gathering as Wall Street prepared for bad news in the wake of reports of slower iPhone sales. But it turns out that those fears were mostly unwarranted. Apple managed to increase iPhone revenue during the December quarter, despite selling slightly fewer phones.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

While the public now knows much more about the Magic Leap One: Creator Edition today than it did yesterday, there's still a quite a bit that's unknown. One of the most significant questions — with any mixed reality product — is the field of view. How much of what we see through these glasses will contain the computer's virtual creations?

On Wednesday, Scope AR, makers of Remote AR, the augmented reality video conference calling and remote assistance solution, announced that the app is finally available for HoloLens. Next Reality had a chance to talk with the founder and CEO/CTO of Scope AR, Scott Montgomerie, inside this new version of Remote AR.

Thanks to Metaverse, it has never been this easy to create your own AR game.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

OnePlus just took the wraps off their new flagship smartphone, the OnePlus 5T. The phone has an impressive spec list, including a Snapdragon 835 processor, 6.01" FHD display at 2160 x 1080, 6 or 8 GB of RAM, 64 or 128 GB of storage, 3,300 mAh battery, and the awesome Dash Charging technology. This rapid turnover to a new device has many OnePlus 5 early-adopters angry and feeling duped.

We've all been guilty of sending messages that we instantly regret — be it a moment of anger or plain old drunk texting. More often than not, these silly texts result in unnecessary headaches for both you and your contact. Thankfully, WhatsApp has finally tackled this age-old problem by giving us the ability to prevent drama before it even gets started.

After announcing another massive round of funding to the tune of $502 million, Magic Leap is adding another powerful weapon to its creative arsenal: John Gaeta, the man who helped develop the iconic Bullet Time effect for The Matrix series of films.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others, such as the Chicago Cubs winning the World Series.

When Disney teased an augmented reality game called Star Wars: Jedi Challenges running on a headset from Lenovo, fans had more questions than Disney had answers. When? How much? Can I be a real Jedi?

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

How would you feel if the stethoscope used by your doctor to listen to your heart and lungs was teeming with potentially unfriendly bacteria?

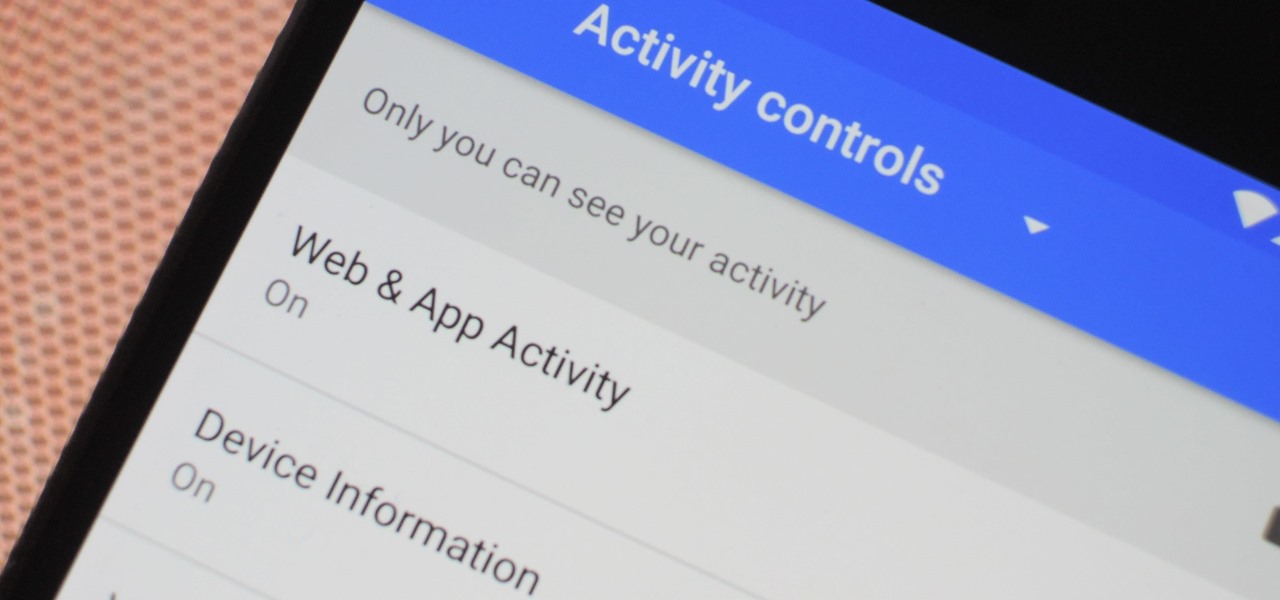
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

Forget what you know about controlling augmented reality experiences. "Scroll" lets you interact with augmented reality using a much more subtle approach: A ring.

HBO Max's watchlist, dubbed "My List," is a great tool that lets you collect and sort the video content you're interested in. That way, you don't need to sift through HBO Max's enormous catalog every time you open the app — just open your personal list of saved titles and start binging.

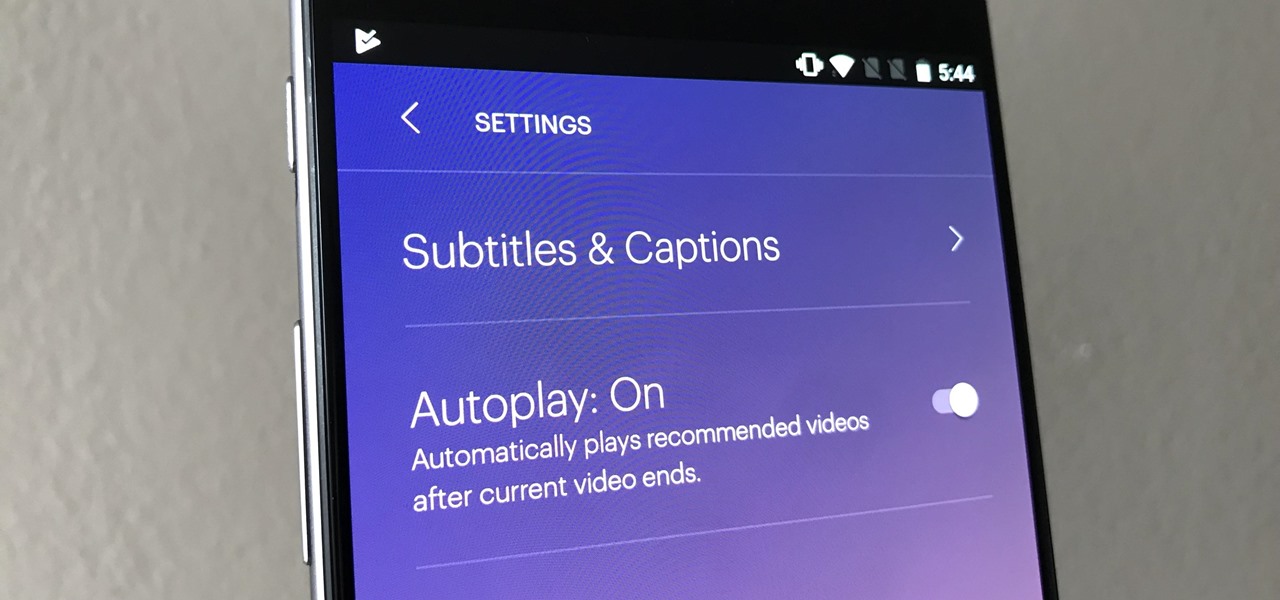
We use subtitles when we can't understand what's being spoken on screen, but most of the time it seems like those subtitles are out of our control. Maybe we find them too small, or even too large. Maybe the color is too faint, or the background too distracting. If only we could change the subtitles to reflect our own needs and styles ...

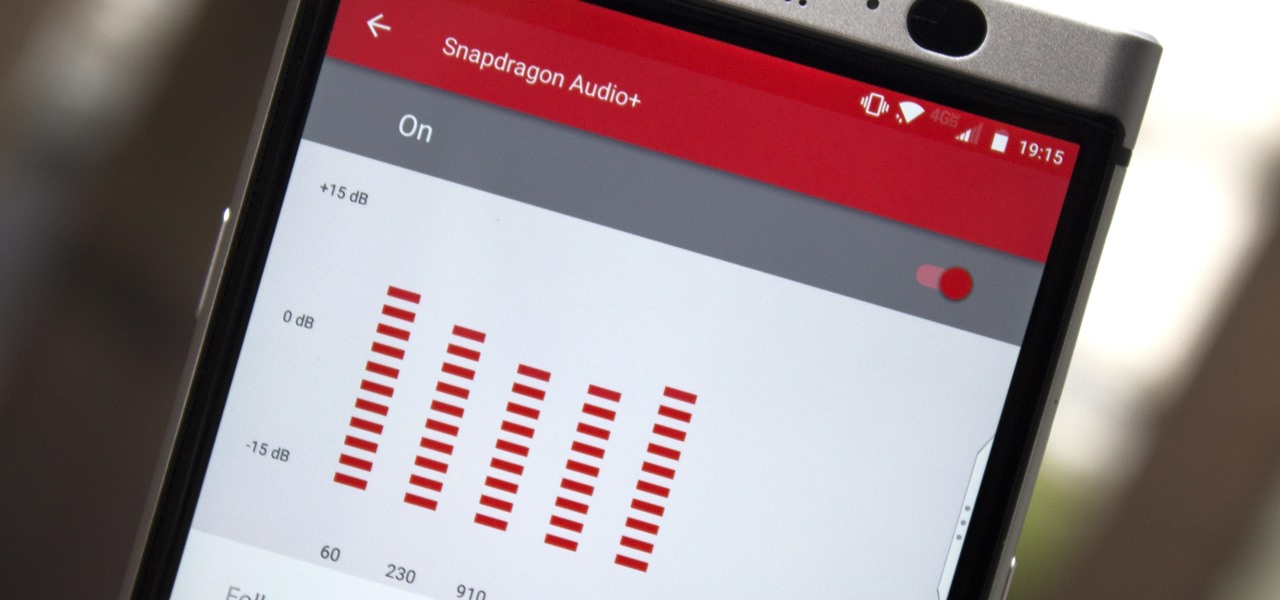
You may not know this, but the Spotify app will let you add a bit of personal touch to all the music you stream. Unlike many other music streaming services, Spotify actually has fantastic equalizer support on both iOS and Android.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

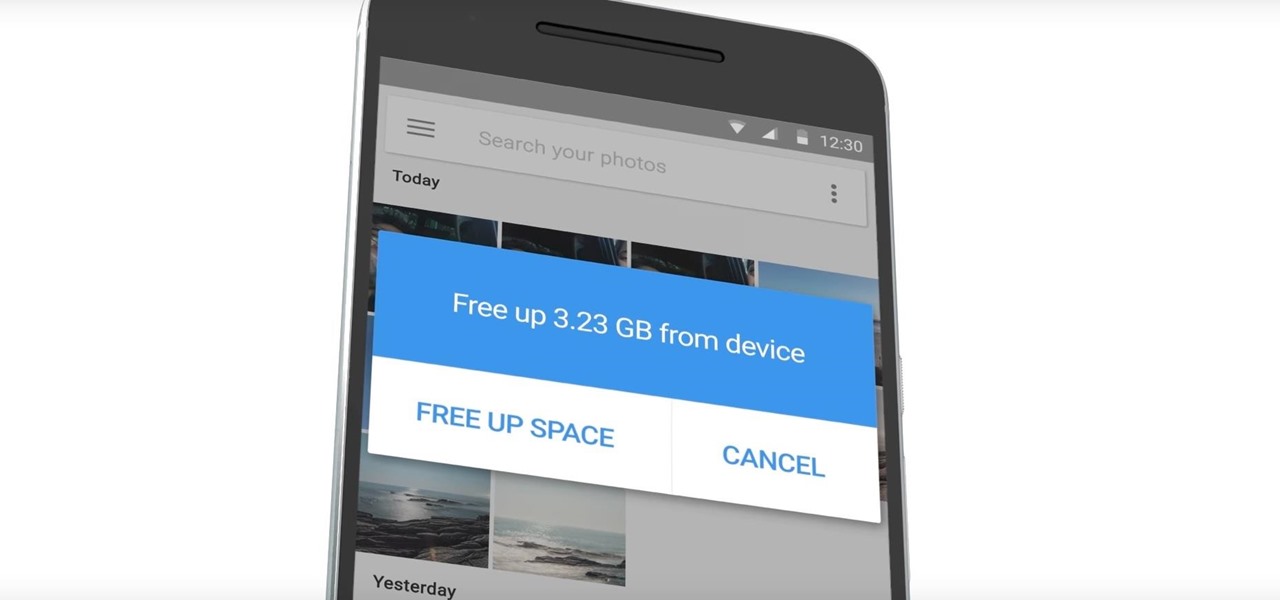
Well, get ready to have your battery depleted if you use Google Photos. The backup app has just removed the "Backup While Charging" feature in their app.

At the eMerge Americas investors conference in Miami, Florida, Magic Leap founder and CEO Rony Abovitz previewed details of the launch of their highly-anticipated device.

Do you know what your smartphone is made of? I've had smartphones for years, but if you asked me that question I'd probably respond with "Wi-Fi." For uninformed consumers like myself, it may shock you to know just how much goes into creating a smartphone.

Despite what you may have heard, sleep is NOT for the weak. It's essential, not to mention it makes us feel a hell of a lot better in general. But for some, getting to sleep is easier said than done. In fact, about 50 million to 70 million people in the US have a sleep or wakefulness disorder, according to the CDC.

We were really rooting for you this time, BlackBerry! With the phone company having minimal success in the past with smartphones, the BlackBerry KEYone was extremely promising. That is until YouTube Reviewer JerryRigEverything discovered a fatal flaw, the phone's screen popped off with just a bit of pressure and then stopped working. So...there's that.

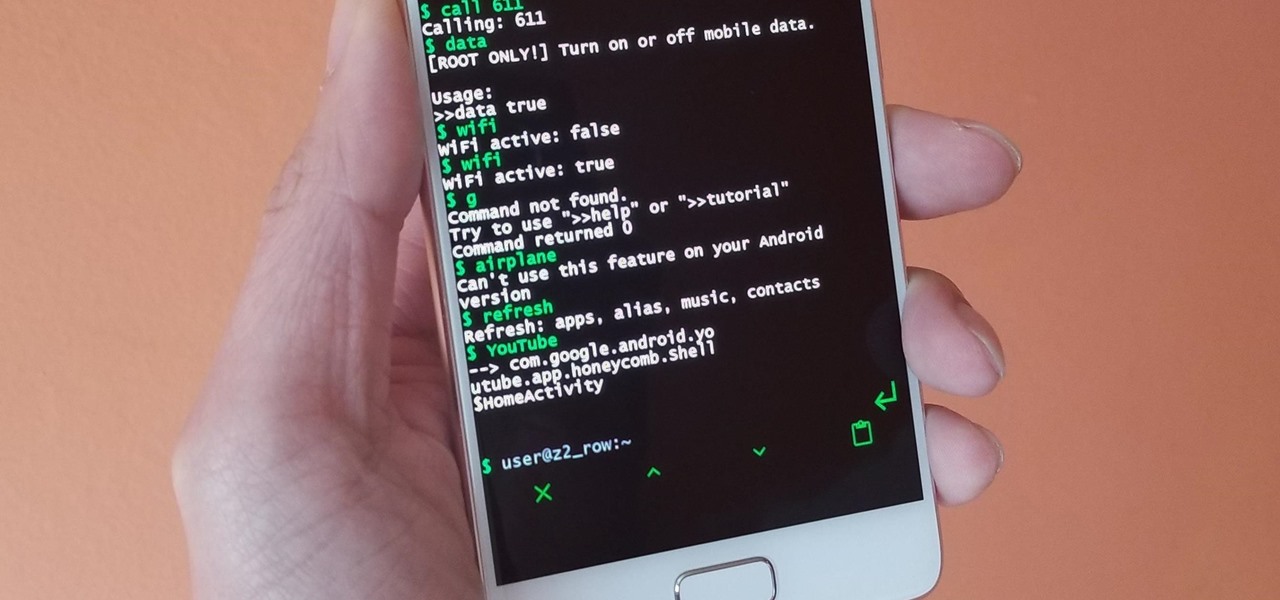
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

Ben & Jerry's addicts rejoice: Microsoft just won a patent for AR glasses that could help to combat overeating. Physical restraint is still needed to keep me away from that ice-creamy goodness, but a little virtual voice saying 'DON'T DO IT' could definitely help when the cravings come.

The driverless competition is heating up as Detroit automakers attempt to woo tech talent away from some of Silicon Valley's biggest players.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Microsoft has always been pretty good with customer service, especially from the developer's end point. In recent years, since Satya Nadella took over as acting CEO, the level of customer and developer care has become something much more. This software giant has gone out of their way to learn about what works and what doesn't and to adjust.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)