No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually been around for 20 years now. Watch the video below to see how the colorful roll is created.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

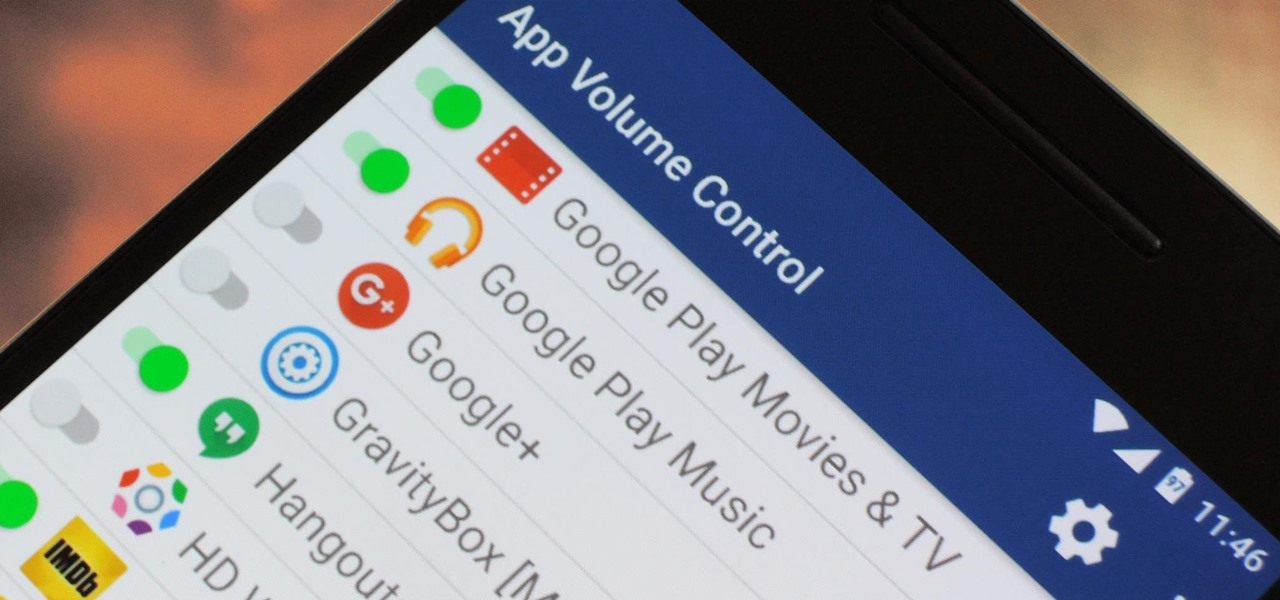
You can do practically anything with a modern smartphone or tablet, so it stands to reason that the apps you have installed may serve vastly different purposes. Picture a game and a video player sitting right next to each other in your app drawer—odds are, you want the sound turned up while you're watching videos, but would prefer that the game was muted or a little lower. As a result, we're constantly tweaking volume levels to get the best experience.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

My daughter moved into her first apartment last year, a huge rite of passage in any young person's life. With a mother and two grandmothers who are good cooks (to say the least, in the case of the latter), it's not surprising that she turned to us for some advice about how to improve her own skills in the kitchen. Without question, the single best piece of advice we have given her is to employ mise en place each and every time she prepares a meal.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

Sooner or later, you're going to come across a person at work that you don't like—or someone that doesn't like you. This can result in uncomfortable tension, insulting gossip, and a disrespectful attitude, to name just a few of the negatives. But it doesn't have to be that way. The next time you're having a workplace conflict with a particularly challenging coworker, the best thing you can do is keep your mouth shut, and here's how to do it.

Being Jewish is kind of tough this time of year. Folks are putting up their lights, stringing popcorn and cranberries, and decorating trees. Those of us who don't celebrate Christmas start to feel a wee bit left out in the cold. Yes, some families give out presents on each of the eight nights of Hanukkah, but the truth is that it's not a major holiday on the Jewish calendar.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

There are rules that cooking in general always follows: cakes should be fluffy. Steaks should be heavily seasoned, and nowhere near a bottle of steak sauce. Every stock should start with aromatics (onions, carrots, & celery). And, until very recently, meringues should always be made with egg whites.

If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

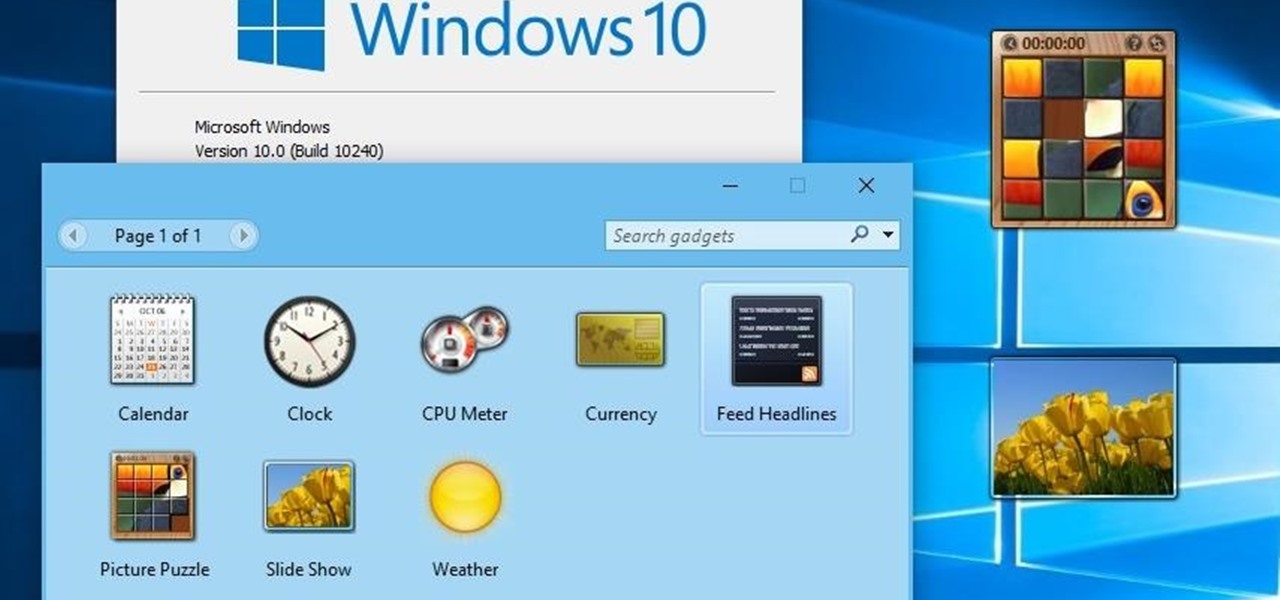
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Hi there, nullbytes :) I've recently seen many questions regarding VMs with Kali, and personally I prefer using a Live Boot USB to get Kali without removing my system (and for many reasons).

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot less messy than granulated sugar, and you can measure the exact amount you put in your drink no matter what.

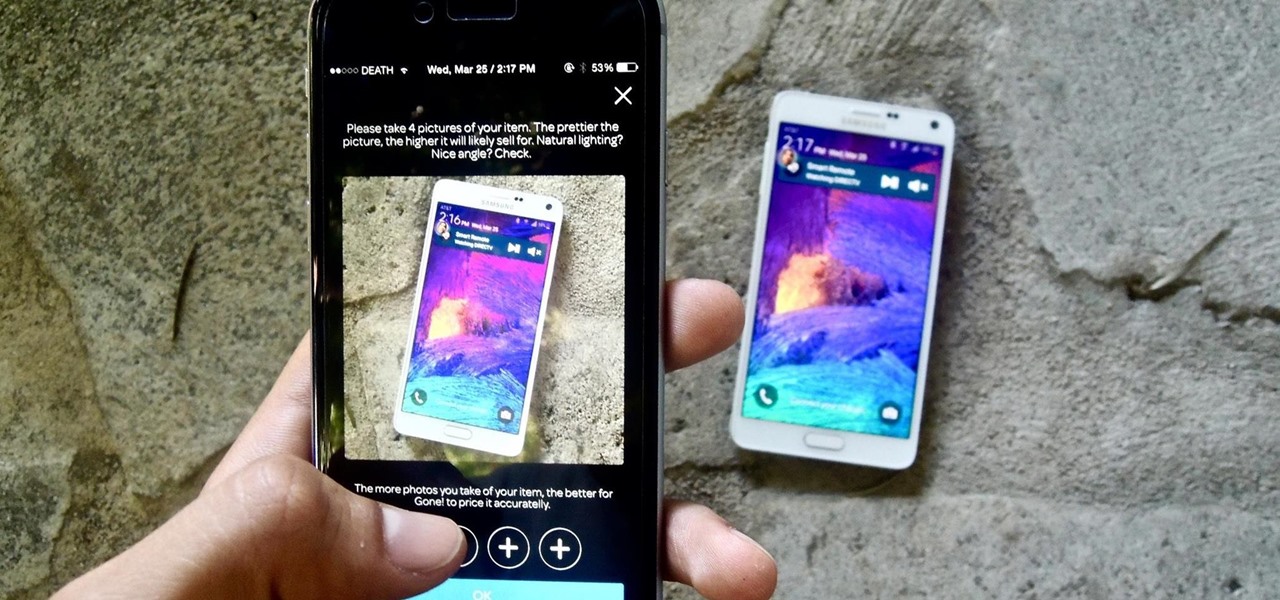
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

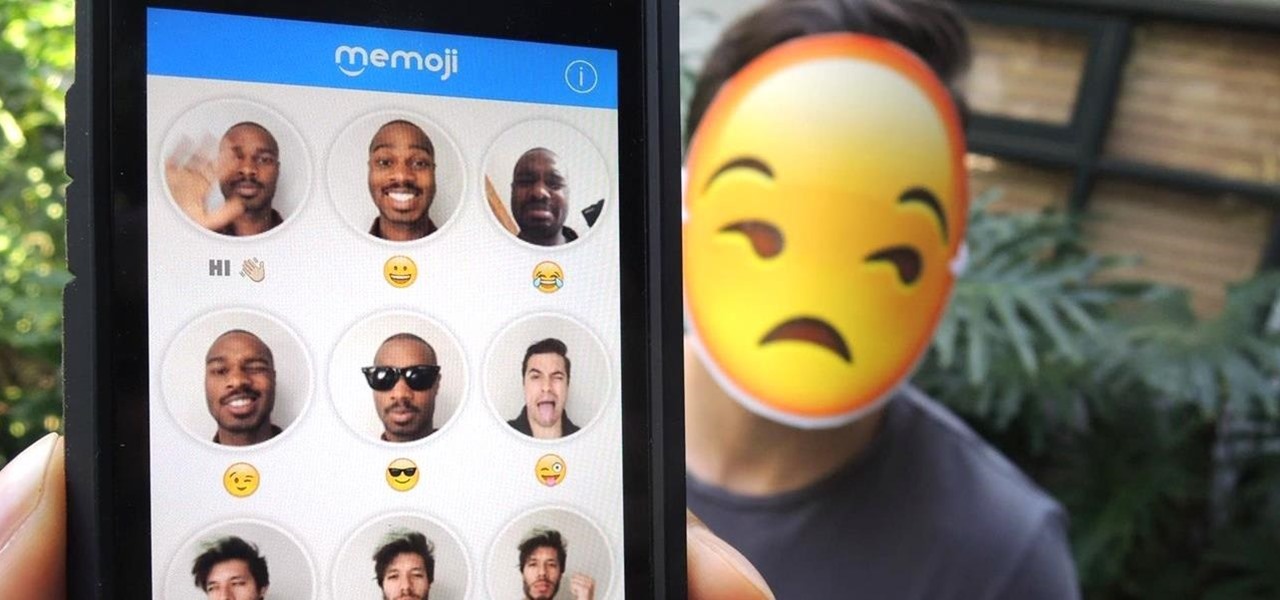
Yes, emojis are the [insert poop emoji here]. They can help improve your love life and even let you portray emotions in a more diverse and well-rounded way now. But combining emojis with GIFs? Well, that's some next-level [insert poop emoji here] right there, and with a new iOS keyboard from Puppy Ventures, that next level is finally here.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"