The stock weather widget preloaded on your Samsung Galaxy S4 is really great, but there's one thing that's missing—options. The weather widget shows just the right amount of information at a glance, and it's not too shabby looking either, but for us softModders, it'd be really nice to have more options. Well, today I'm going to provide you with a couple. Interestingly enough, this is a topic I first covered on the Samsung Galaxy S3.

What Is Dimensional Analysis? Dimensional analysis is used to convert units. It's the process of analyzing units to decide which conversion factor to use. It's used by multiplying units by conversion factors, rates equal to 1.

If you've got a Samsung Galaxy S3 or Galaxy Note 2, you probably either love or hate the Social Tag feature. Using facial recognition, much like Facebook does, it scans your photos and lets you tag a name to a face. If your device recognizes the face by itself, it will automatically tag it for you. If the person is in your contacts, it will give you the option of calling, texting, or emailing them. While it's a great feature for some, it doesn't always work perfectly. If the flash from the ca...

A vast number of studies ranging across time, continents, cultures, political systems, and religions show that when evaluating potential mates, women place significantly greater emphasis than men on material wealth, and that men tend to both display and exaggerate their financial status and prospects when around women.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

In an effort to help posters see the various ways that people discover their posts, Q&A site, Quora has decided to make who views each post, public, along with information on how each viewer came to see the question (ex: through an email, a followed tag, or other public stream). This would probably be an interesting, helpful, and universally liked feature, except for one thing...

Have someone shave all the hair on their head, but make sure to do it badly. Intentionally miss patches of hair on the eyebrows and head, and make sure to try to get some razorburn for that obviously-just-shaved look. You could also use an electric hair trimmer to leave a little bit of hair and make it even more obvious. Leave the hair on your arms or wherever else as if you forgot to shave it. The point is to be completely unconvincing.

Hotly contested video. The question remains, is the science behind the potato fire bonafide or bogus? We have yet to try it over here at WonderHowTo, and the comments thus far haven't indicated a solid verdict. Try it out and let us know! Is this a hoax? Or can you truly start a fire with a potato, salt and toothpaste?

Do you wanna be that person who stands out in a crowd? Our society dictates our fashion sense. We believe we all must look like who ever is the "most popular" in the media (TV, film, magazines etc.). Our choice to express our self is very limited because of the stigma of what patterns, styles and colors belong to which gender. I have found by adding just a hint of feminine flair to my person that I am able to catch peoples eye's faster than a supermodel walking onto a runway.

Introduction This is one of the things I am asked the most and there are so many different answers. It is hard to just tell you without know your computer's current speed or what type of hardware it has. So here I will talk about how to speed up a slow computer and how to keep your computer running fast.

The ComCoachVideo Tutorial is an online learning environment designed to help students improve their oral presentation skills. The website contains video clips illustrating effective and ineffective public speaking practices, as well as an interactive feedback component designed to foster students' ability to critically evaluate presentation segments.

I turned my first ear plug purely as a challenge when the question was asked on a turning forum and nobody could provide an answer. I didn't know much about them, only a general concept of the shape I was going after.

Despite the fact that you may not find this as a necessity, if you do follow this quick guide, you will wonder how you ever managed before. This tutorial is based on the assumption that you're using Google Chrome, so if you aren't, I advise you to download and install it. Furthermore, this tutorial is aimed towards beginners, however advanced users may also learn a thing or two.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

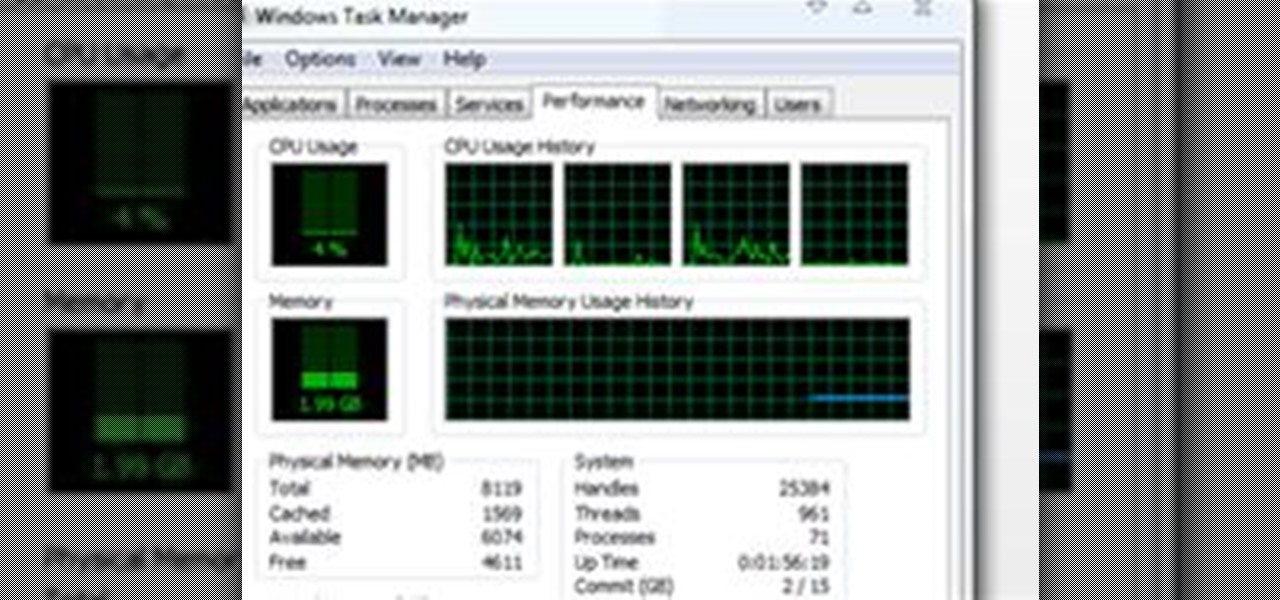
Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?

Hangouts are one of the most fun features in Google+. As long as you have a webcam and a microphone, you can "hangout" with up to 10 of your buddies on Google+ and do just about anything. Of course, sometimes it can get kind of awkward when you are hanging out and you don't really have anything to say. This problem can be mitigated if you host hangouts with a plan.

OK, so you don't necessarily have to make ammonium nitrate to have ammonium nitrate — ammonium nitrate can simply be obtained from fertilizers and instant cold packs. Making homemade NH4NO3 can be much more expensive then buying it, but this method is not meant to be a viable route, it's an exploration of science and chemistry.

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:

Create some form of shocking underpants Get multiple people to play a game of jeopardy

This article will show you how to make a shutter release cable for a Canon camera. It took me about half an hour once all of my materials were gathered. I came in at a total of about eight dollars. It has three switches and buttons. The black button on mine triggers the auto focus. The red button triggers the shutter. Finally, the switch triggers the bulb mode, or long exposure. This can be used to take astronomical photos that show the movement of the stars in the picture. The release cable ...

Ever since high school, I've been preparing my own taxes. Each year it gets more and more complicated, which results in me filing later and later, avoiding it until I have the time or just can't wait any longer. I even resorted to using TurboTax online to help do some of the grunt work for me these past couple years, but that hasn't stopped me from being lazy about it. I have yet to file my 2010 taxes, but I will very soon. Tomorrow, in fact—before TurboTax raises their prices.

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.
This book surprised me. I read it for 2 reasons. 1) It seemed like one of those decently famous books that I should probably have read.
Some interesting news this week, from Obama's new political ad, to the $20,000 payments by Cardinal Dolan. Take a look:

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

As some of you Mad Science readers will remember, we recently covered the separation of water into hydrogen and oxygen using electrolysis. Passing a current through water can rend it apart, but we can also recombine that oxygen and hydrogen to make electricity! This is the principle behind those vehicles run by hydrogen fuel cell engines.

If you live in an urban environment, chances are that you've seen this: It's a program started by the FBI to prevent terrorism and general thievery in peaceful and innocent communities all around America. I myself have seen a lot of these, and my previous apartment community was part of this 'program'.

If you have never heard of Team Fortress Two here is your chance to play! Before we get into anything complicated, there are some basics you should know.

Balloons are fun, but the helium ones are always more entertaining. So today, we're going to learn how to make hydrogen gas by combining toilet bowl cleaner with aluminum foil. With hydrogen, you get the same lighter-than-air properties of helium, plus it will explode! Historically, this has proven disastrous, but for our tiny-scale experiments, it will be safe and fun!

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Ever wondered how other players can get so much awesome enchanted gear in such little time? Struggling to gain experience orbs and need an efficient way to do so with very few casualties? In this tutorial, we will be going over how to build a quick XP farm with a zombie spawner (though any spawner will do). Setup

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

How to Read a Poem Poems can be read many ways. The following steps describe one approach. Of course not all poems require close study and all should be read first for pleasure.

In this article I’m going to talk about specific issues about optimizing your website, making it more clear to Google and other search engines exactly what your website is about. As I've discussed in previous articles this is very important for people when they are searching. We're going to talk first about keyword phrases and how they fit into search engine optimization. You are going to be using keyword phrases in a number of different ways. First you have to figure out what your keyword ph...
1.) If you do not know something, keep our mouth shut.* No-one, I repeat no-one, is interested in your uneducated guesses about why something is the way it is, or why someone did something a certain way. At best, you will trick them into temporarily thinking you know what you’re talking about. At worst, you will convince them that you are speaking the truth and they will perpetuate your bullsh*t to others. Do not contribute to making the world a more foolish place just because you had to say ...

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.
In my early life I was deeply impacted by the work of physician and psychoanalyst John C. Lilly. I still have my dog-eared copies of The Mind of the Dolphin (1967) and Programming and Metaprogramming in the Human Biocomputer (1968). Lilly's work, with dolphins and the development of the sensory deprivation tank, has formed the basis of movies, music and television productions.
Sergio Peralta Advisor: Jessica Davis