Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with a little guidance, you can create dishes that are tasty homages to the cuisines you love to eat. In this two-part article (second part here), I'll cover both categories and sub-categories of some of the most popular ethn...

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Sangria... the elixir of summer. When properly prepared, there are few things more refreshing and magical. If you're looking for a way to mix things up and "get out of the bottle," try one of these lovely libations before the warm weather ends: peach-mango sangria, pineapple-basil sangria, watermelon-raspberry sangria, or blueberry-plum sangria.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

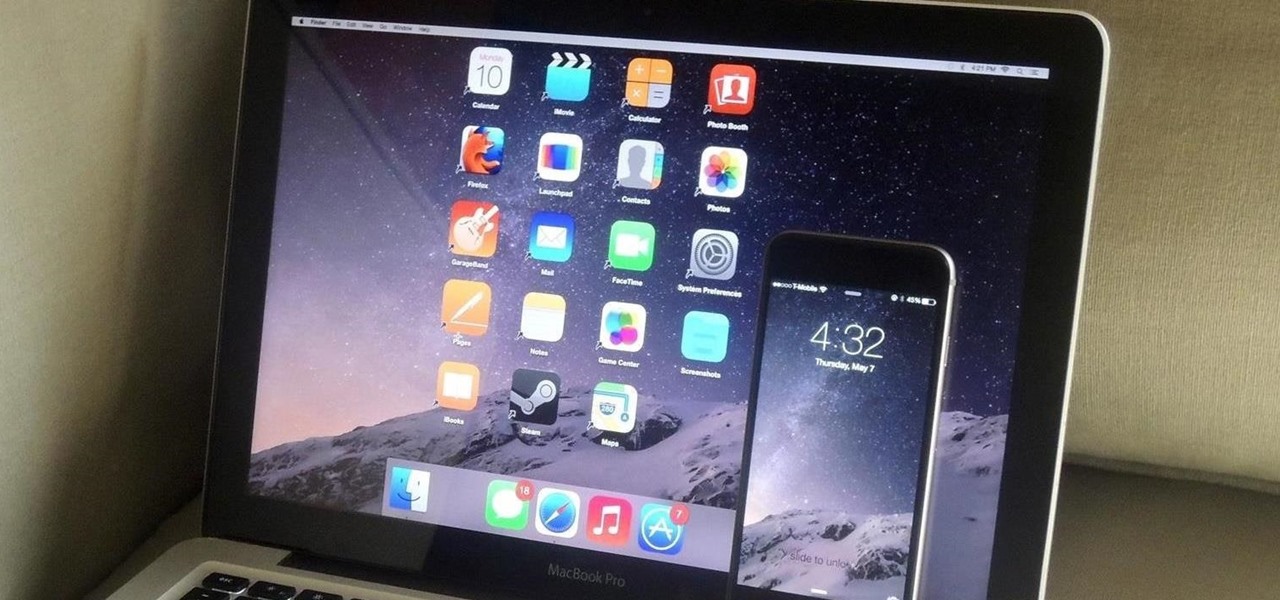
Is your Mac starting to feel messy and sluggish after using iOS 8 on your iPhone every day? Even with all of the iOS-friendly features built in to Mac OS X Yosemite, your Mac can still feel kind of "old" in comparison to an iOS device—but it doesn't have to. Using the tips and tricks below, you can easily make your Mac desktop or laptop look and feel like iOS 8 in no time.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

As the cooler weather starts rolling in your pet will need more than just his natural coat to keep the shivers away. Take him out in style by designing a simple yet elegant tailored coat that will fit him perfectly. Here is an easy lined tailored coat with a nice thick comfort strap to keep him snug. Watch this video and follow the accompanying written instructions.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

The Nexus 5 is the current Google flagship packed with the latest and greatest of all things Android, but what if you never made the leap from your Nexus 4 smartphone?

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my greenhorn hackers! I've been writing these Linux tutorials in an attempt to fill the void in the education of some aspiring hackers into the Linux operating system. There is a lot to know, and in this tutorial, we'll look at Linux file permissions. Step 1: Checking Permissions

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

Ever since China's Nreal unveiled its Light smartglasses at CES two years ago, an army of look-alikes have emerged from the Asian nation.

One of China's largest smartphone makers, Oppo, just took the wraps off its new design for augmented reality smartglasses called AR Glass 2021.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Now that Google has announced its new Pixel smartphones, folks who rushed to buy an iPhone 7 might be experiencing a bit of buyer's remorse. The new Pixel and Pixel XL are packed to the brim with cutting-edge features and top-notch hardware, and Google seems to be taking direct aim at the iPhone 7 with its Pixel marketing (and their groan-worthy jokes during the keynote).

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

While I prefer Android in my personal life, I've had the opportunity to work in the Apple ecosystem. One of the coolest features I've come to rely on is AirDrop, which makes it easy to beam content from mobile devices to desktops and vice versa. Thankfully, Android now has an equivalent.

Smartphone videos get better and better each year. Seven or eight years ago, who would have thought iPhone and Android phones could support 4K video recording. Some phones can even shoot slow-motion at 960 fps. But no matter the resolution or frame rate, a phone's rolling shutter can make quick movements in front of the camera appear wobbly, distorted, or with artifacts.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

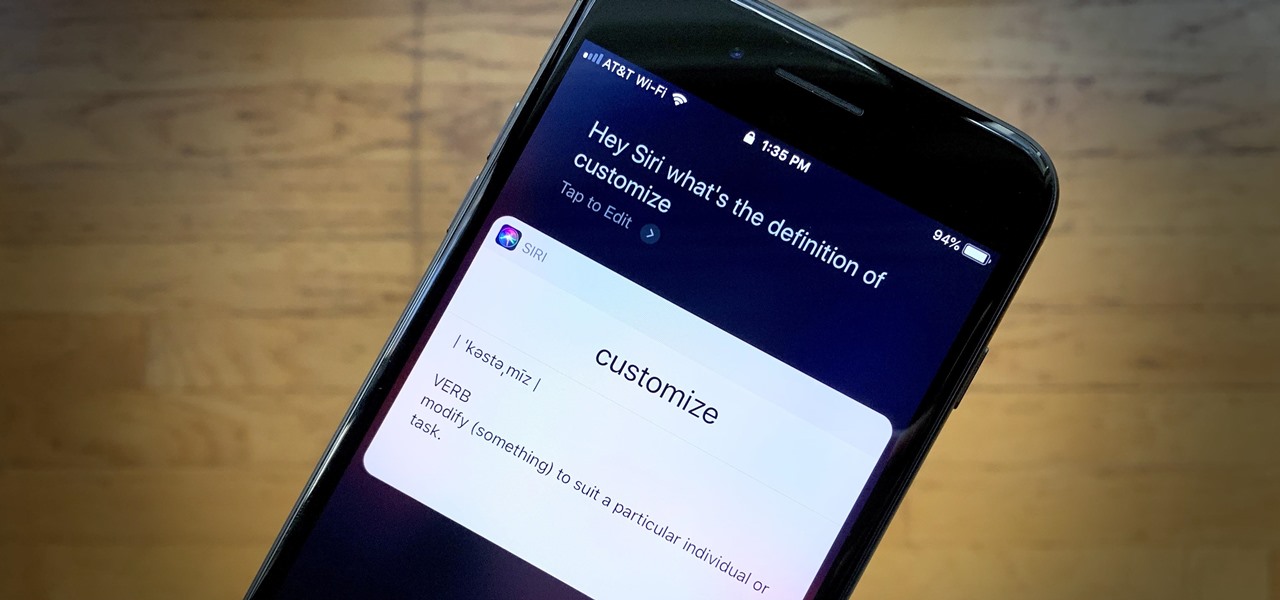
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.