JerkyRecipe.net provides a short preview of their online step by step video instruction and report on how to make beef, deer, or venison jerky. This homemade jerky can be made right in your own oven using 15 secret ingredients and by following step by step instructions which can be found in both the online video and printable report, all available for immediate use. A glimpse of what this delicious homemade jerky looks like can be seen in this preview video, offering up a tasty jerky recipe f...

Learn one of the world's most popular games. It's actually good exercise, too! Step 1: Decide who goes first
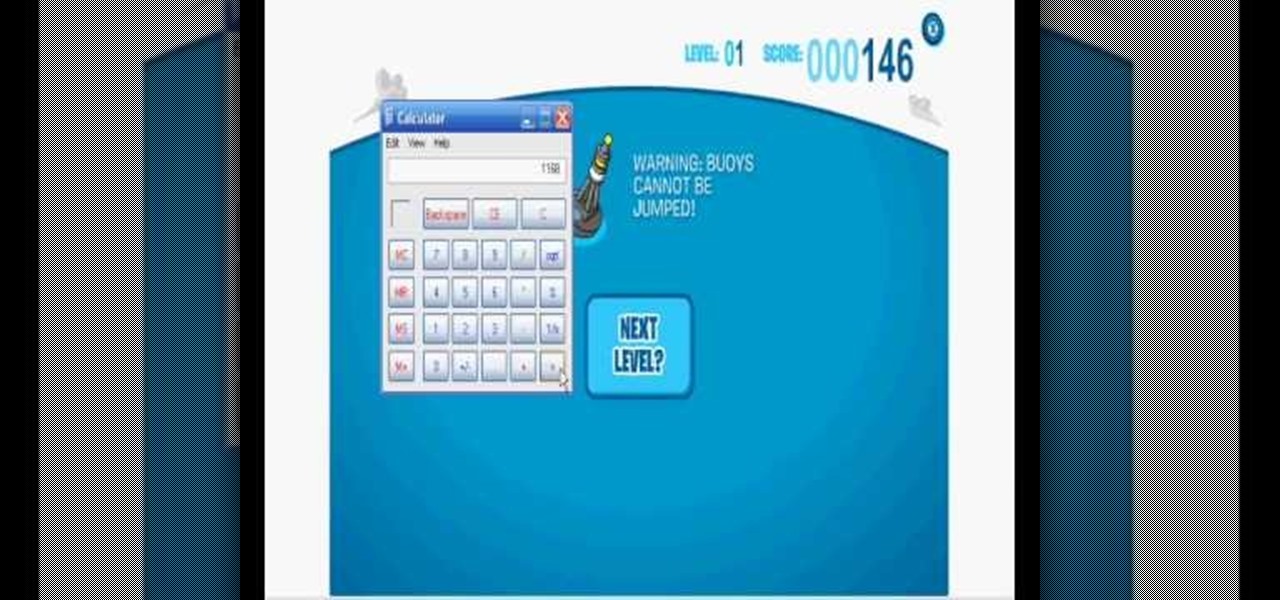
Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to hack Club Penguin with Cheat Engine (09/14/09). This uses Cheat Engine 5.3.
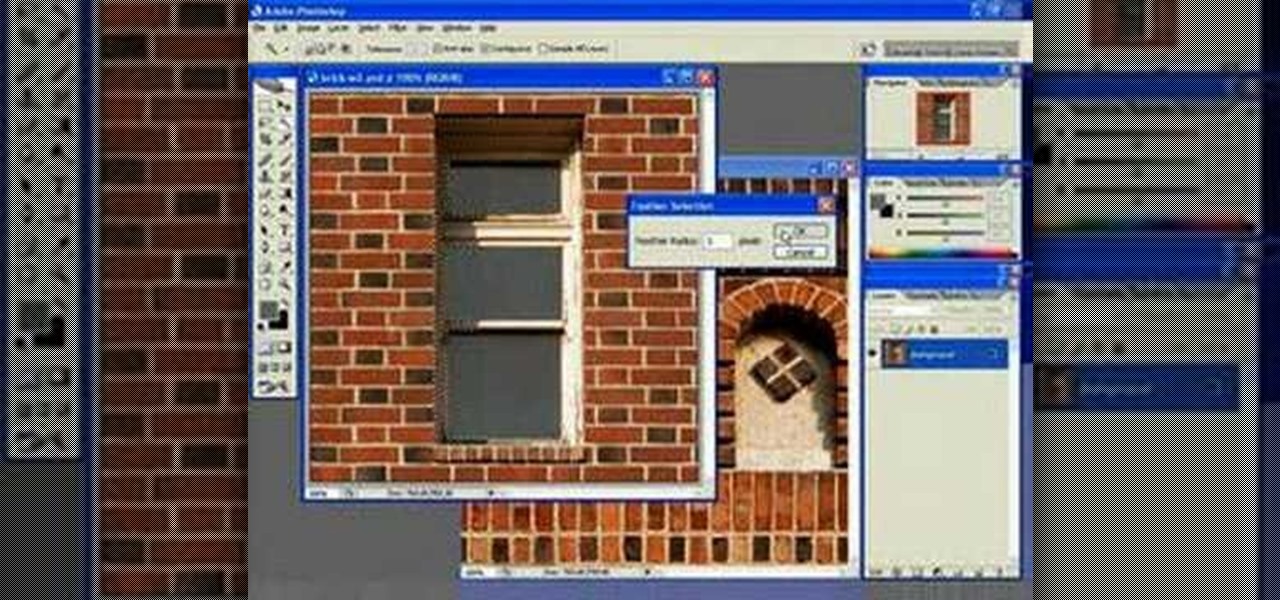
This Adobe Photoshop video tutorial teaches you how to remove or reduce shadows in Adobe Photoshop. This video is from the "Tiling Textures" course. See how to remove or reduce shadows in pictures.
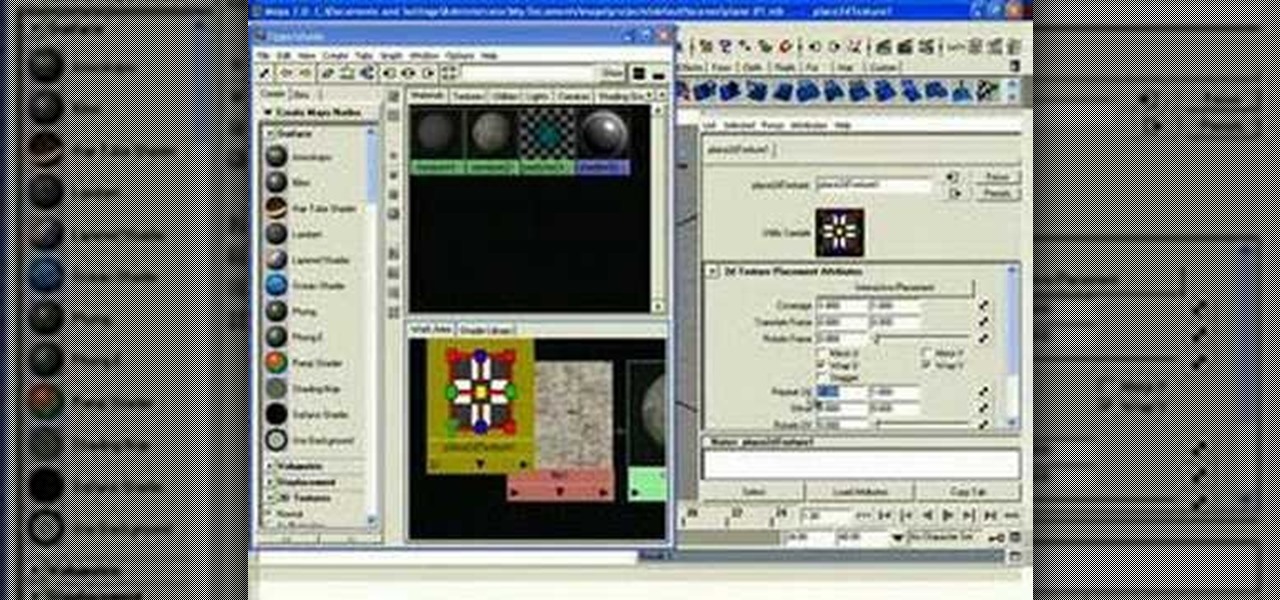
This Maya 7 video tutorial teaches you how to test Photoshop-made textures in Maya 7 from Autodesk. This video is from the "Tiling Textures" course.
This Adobe Photoshop video tutorial teaches you how to create an alternate texture in Adobe Photoshop.

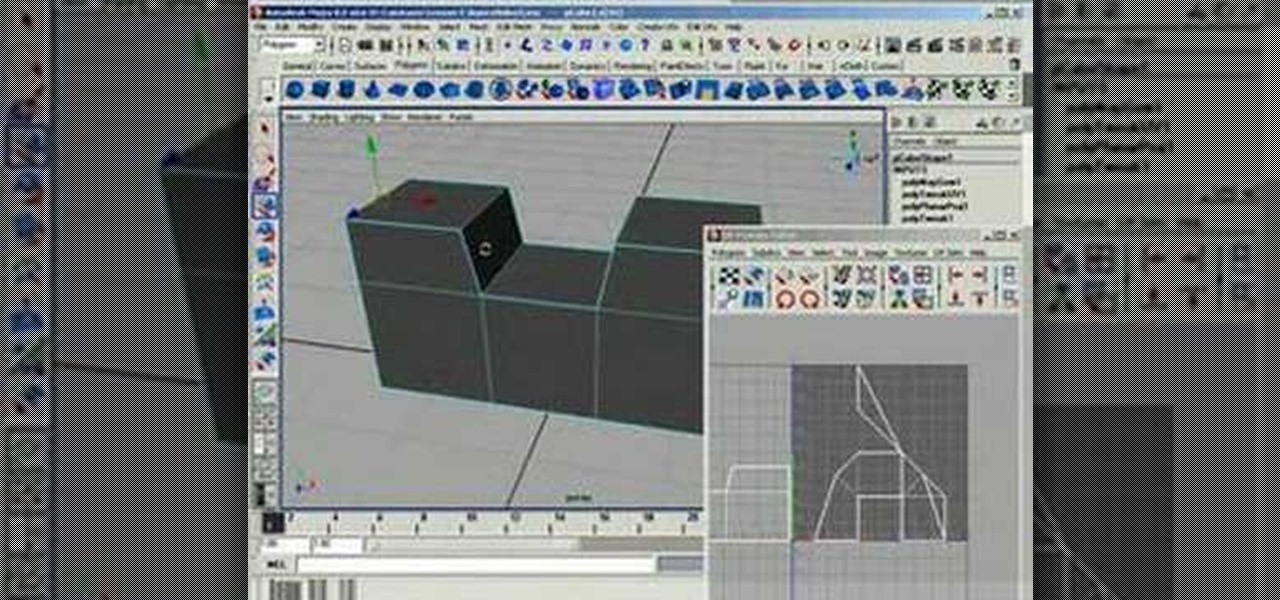
This Maya 7 video tutorial teaches you how to make and use UV space in Maya 7 from Autodesk. This video is from the "Maya Basics" course.

This Maya 7 video tutorial teaches you how to use light and camera choices in Maya 7 from Autodesk. This video is from the "Maya Basics" course.

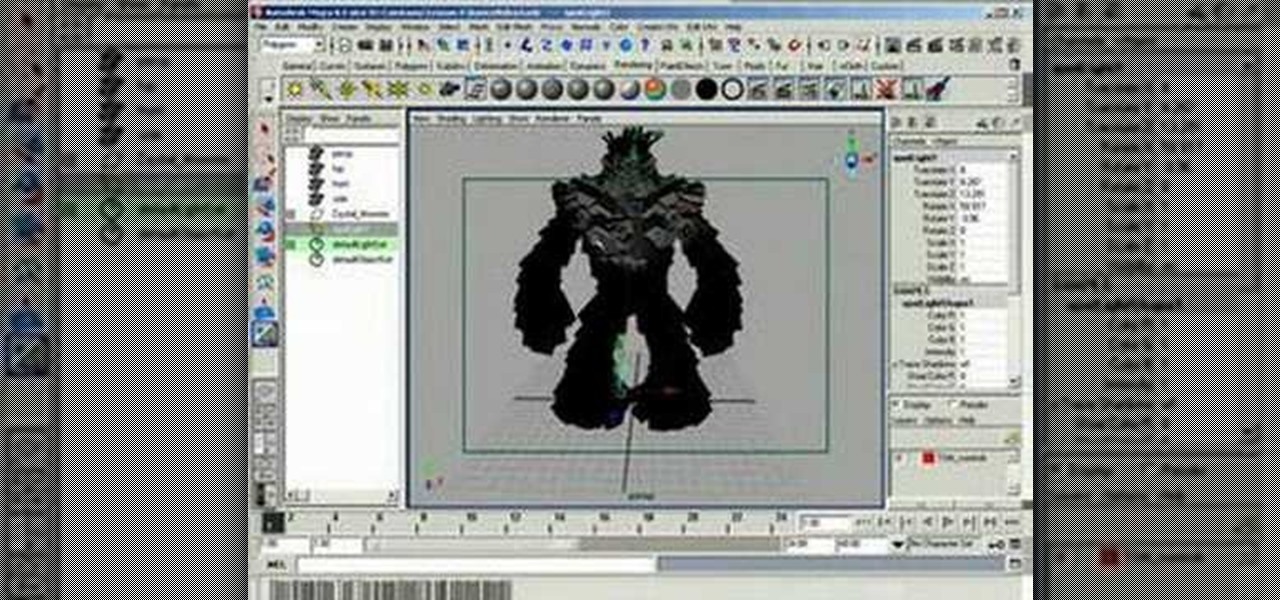
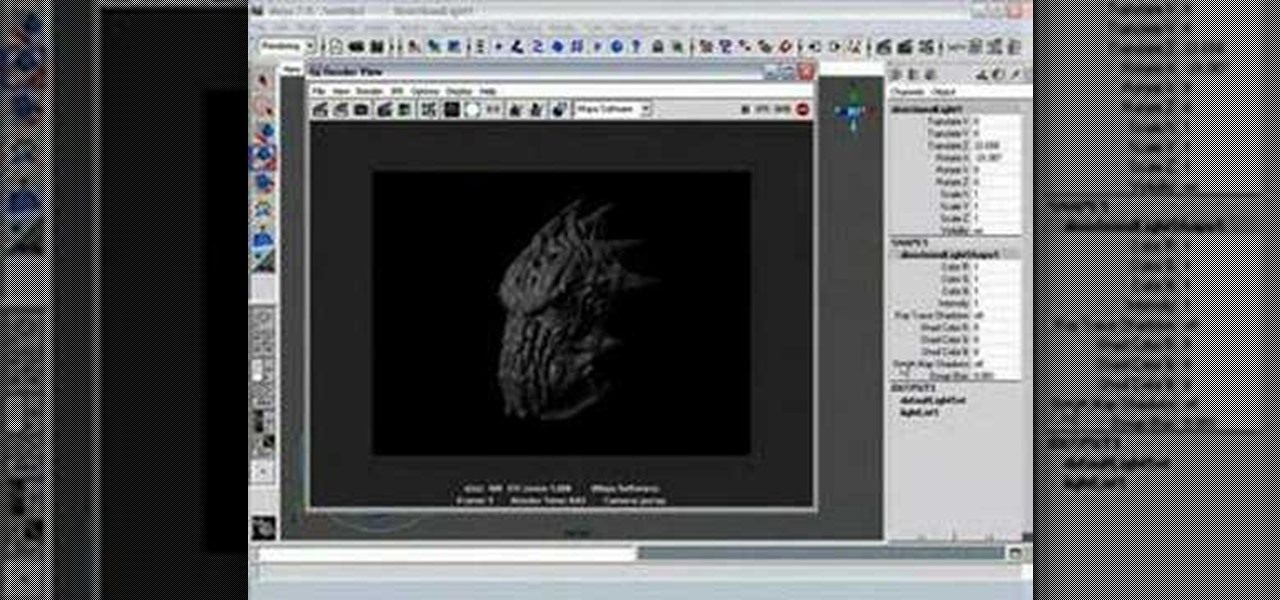
This Maya 7 video tutorial teaches you how to use four lighting techniques in Maya 7 from Autodesk. This video is from the "Game Lighting and Color" course.

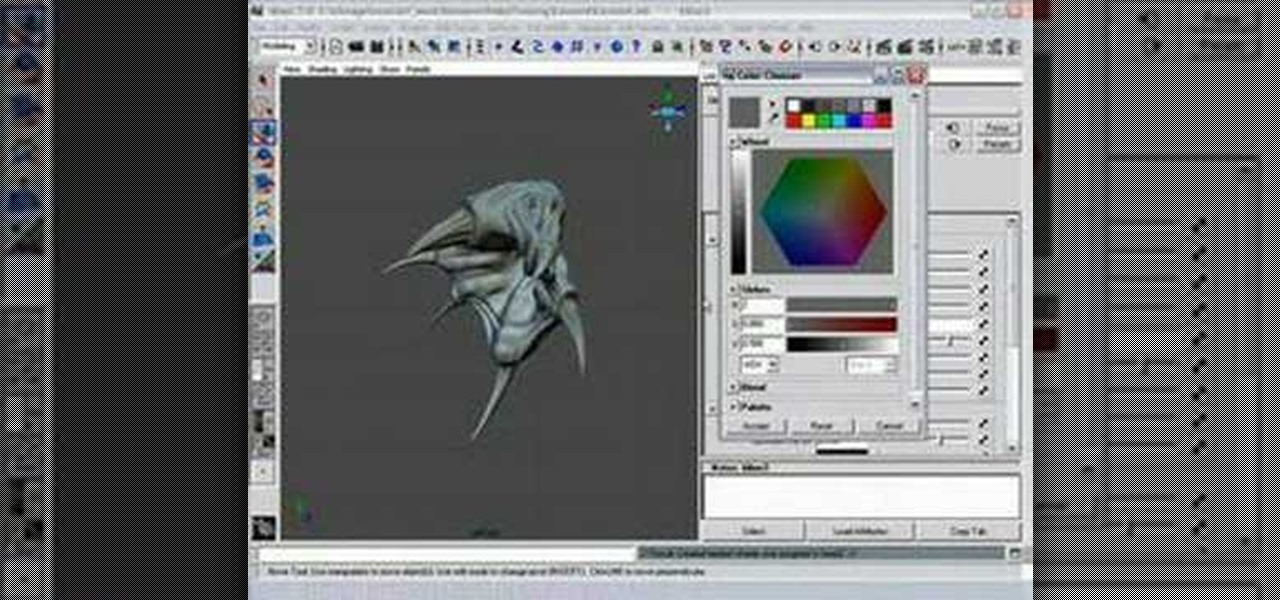
This Maya 7 video tutorial teaches you how to construct a metal shader in Maya 7 from Autodesk. This video is from the "Game Lighting and Color" course.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Time to get started playing League of Legends! This recently released game is a completely free to play multiplayer online battle area game. Play a powerful summoner and pit your chosen champion against your oppnents and defend your tower! Here's an easy guide to getting started playing League of Legends.

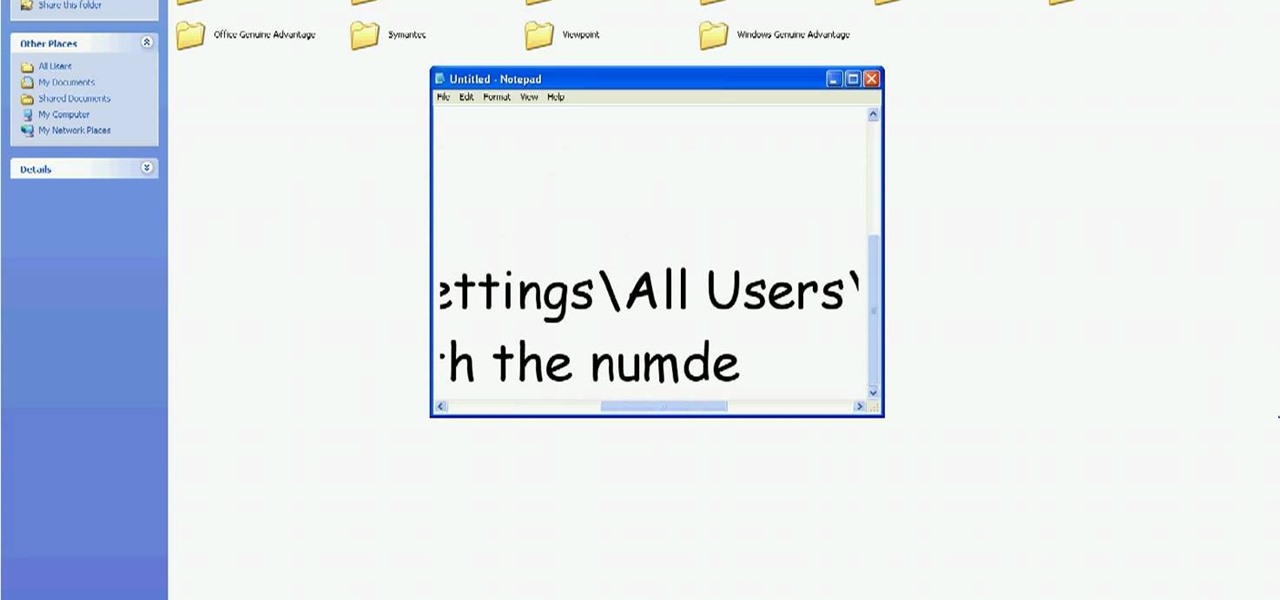
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

Have you noticed some issues with your Apple iPod Touch, like performance issues (speed) or errors (frozen screens)? The first thing you always want to try to resolve these types of issues (especially freezing) is a simple little reset feature on the iPod Touch, available by pressing and holding the Home and Sleep/Wake buttons. If you this doesn't work, you can try restoring the software via iTunes. If that doesn't fix the frozen iPod, then you'll need to contact Apple or a repair technician.

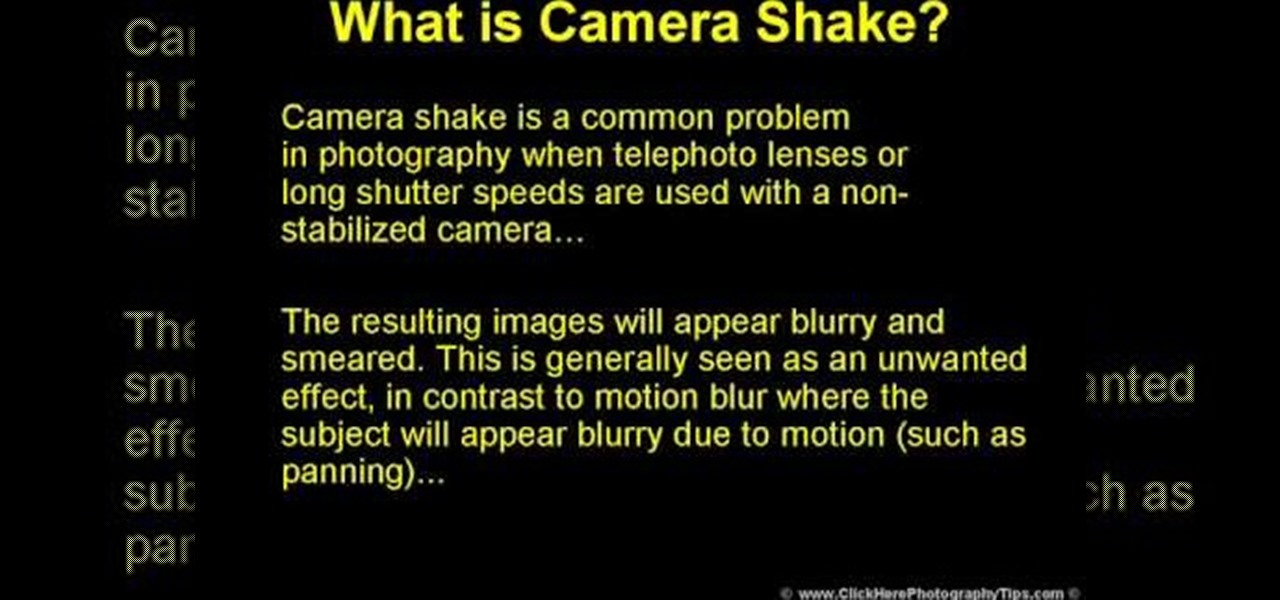
Camera shake is often an unwanted effect in photography, when a telephoto lens or long shutter speed has been used for a camera that hasn't been stabilized. The images subject to camera shake appear blurry and smeared, which is often considered an error - though some photographers find artistic value in camera shake and purposefully try to cause the effect in their art.

Tired of grandpa's baseball card collection rotting away in your attic? Well, unlike his pop bottle collection, baseball cards could yield a decent amount of income for you, if you know how to sell them. There are different outlets available for selling an individual baseball card or card collection. Know how to sell the fruits of your hobby and avoid getting ripped off.

JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. Again, far left Pepsi, near left Pepsi, near right Mountain Dew and far right Mountain Dew. This hack will allow you to see the stats, set the price and see error logs.

There's a great new web game called Epic Duel out on the internet, and everybody's playing it, but not everybody's hacking it, except you! Outshine them all with this EpicDuel cheat with Cheat Engine 5.5.

Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. You will need a friend or relative of the recipient. Send her favorite. If she’s ever mentioned a favorite flower, buy that. You’ll get bonus points for listening to her. If you have no clue, ask a friend or relative of hers ...

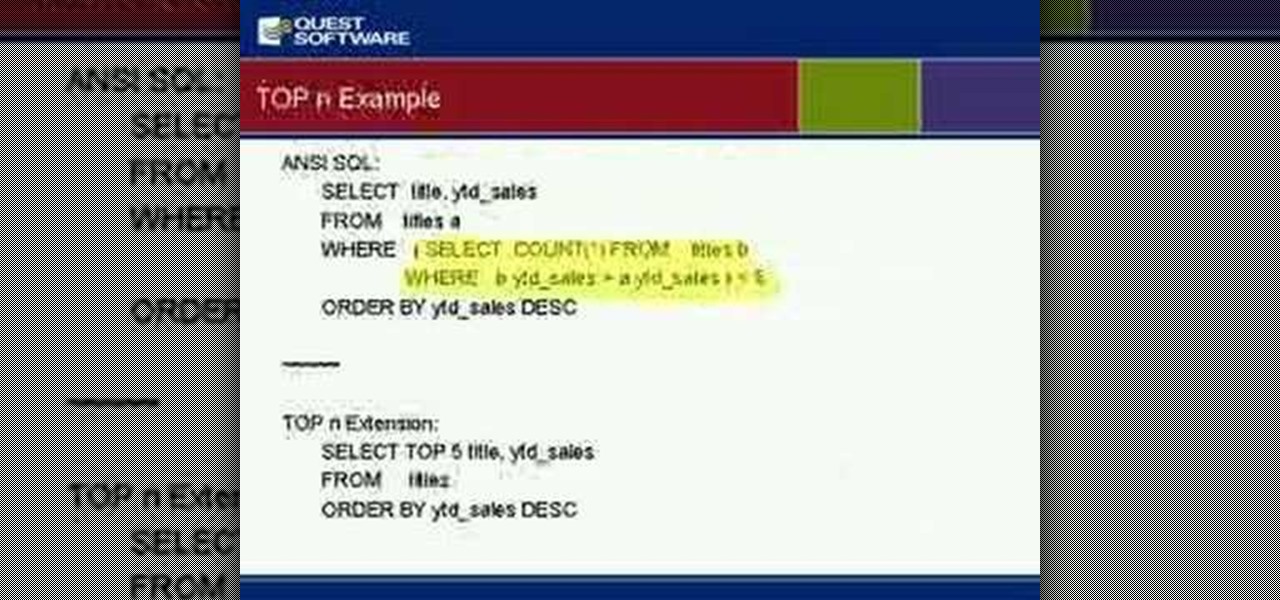
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

You never want to stop learning. Whether you're facing a career pivot or want to better understand the vocation you've chosen, there's always room for growth. The most successful workers are those who make education a lifelong pursuit.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

With the massive popularity of online clothing brands like Missguided and Fashion Nova, it seems that shopping in-store is a thing of the past. I admit that I love browsing from the comfort of my own bed, but there's something to be said for actually going to a store, speaking to people with similar tastes and penchants for shopping. Fortunately, with Frenzy — Shopify's new app for iOS — you get all of the convenience of online shopping, plus the opportunity to interact with other users in pe...

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

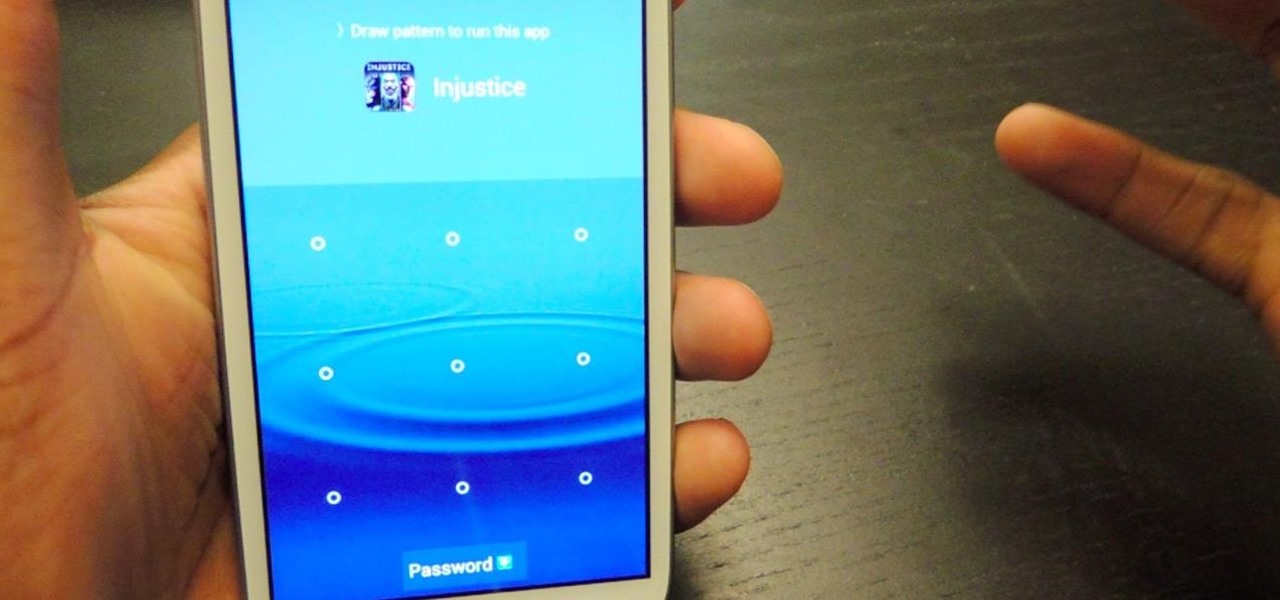
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.
This how to will show you how to program a fairly simple Hacking bat file. First open notepad.