As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

If I were to write a snickerdoodle FAQ list, the top question would undoubtedly be "Do I really need to use cream of tartar in my snickerdoodle cookies?"

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Even those of us most comfortable in the kitchen can be daunted by the idea of cooking for a whole houseful of people. Whether you have a large, well-equipped kitchen or a small one with just the essentials, it can prove to be quite a task to prepare food for a dozen or so people. It takes a certain type of recipe that allows for mass production, in respects to both technique and ingredients. And what I've provided below includes several recipes that you might normally make for just a family ...

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

Welcome back, my greenhorn hackers!

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

As I've explained before, black app backgrounds save you a bit of battery life on your Samsung Galaxy S5. This is because the AMOLED display on your S5 does not have to power pixels or a backlight for portions of the screen that are black.

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

Admit, you're curious. You want to know just what does it take to make a virus for the Mac OS X operating system. Check out this video to learn how to write a harmless virus for computers running Mac OS X.

Watch this instructional knitting video to hang a cast on comb on a knitting machine. Watch this video a few times to master this little trick. You may want to reference some written knitting instructions in addition to following these visual guidelines.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to decrease the size of your knit piece. Use a single prong tool to unhook and tie off a single stitch on either side of the piece before completing each row to gradually decrease the width of the knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to crochet cast on. This is one way to cleverly weave your yarn onto the knitting machine and begin the piece of knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to crochet a cast off. This is one way to cleverly remove your work from the knitting machine and complete the piece of knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to weave a cast on. This is a cast on that many people find difficulty with. You may want to reference written instructions in addition to watching this knitting video.

If you use a knitting machine to knit your projects, follow this simple example to knit ribbing. This instructional knitting video demonstrates how to e-wrap for double bed knitting and transfer the carriage. You may want to reference some written instructions in addition to watching this knitting video. With a little practice, you can make it look as easy as this.

This is a stop action video showing the construction of a complete model RC helicopter from beginning to test flight. Written directions can be a little tricky to follow, so this how-to video serves as a great visual guide to help put together a remote control helicopter. Watch this video hobby tutorial and learn how to build an RC T-Rex 500 helicopter.

Follow these visual instructions to fold a letter into a cute, compact arrow shape. If you ever passed notes in class, this folding method falls among some of the more sophisticated styles. When practicing folding a letter into an arrow, make sure to write on it so as to be sure to conceal the letter's content during the folding process.

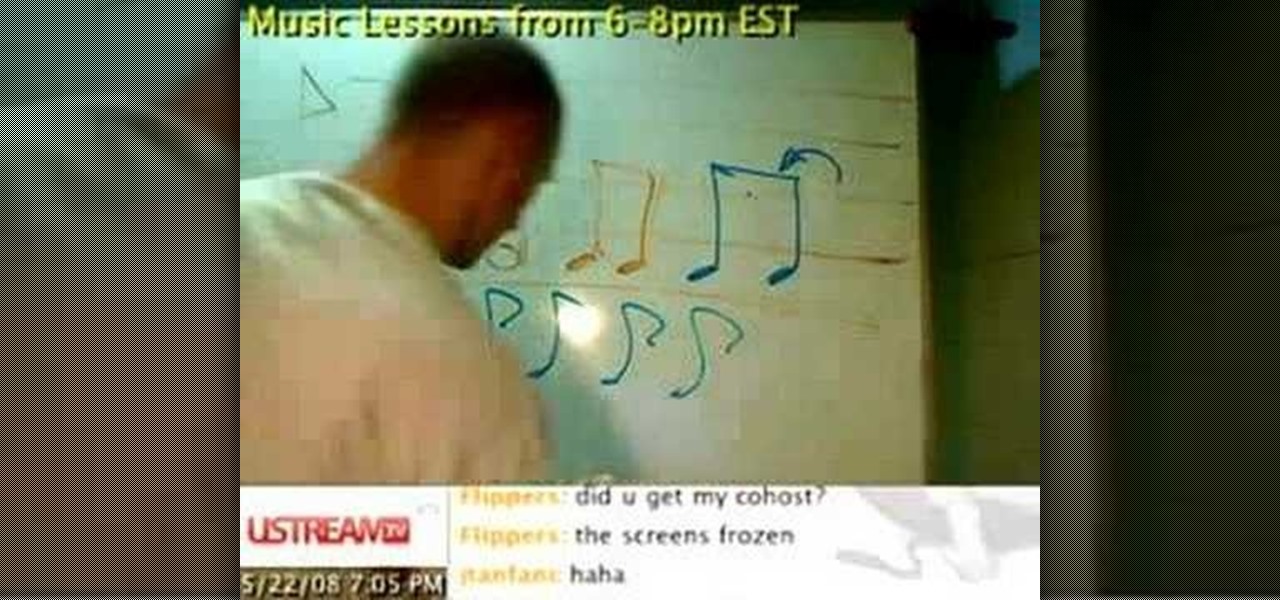
Connecting the flags on eighth notes, sixteenth notes, etcetera, is very important to neat, legible music. This how to video teaches you when to connect the flags in the music notes. Learn how to read and write music better with this music theory tutorial.

This language tutorial teaches you how to create words with the letters from the Arabic alphabet. Write, read and understand the structure of words in modern standard Arabic with this how to video.

Learn how to play the most famous of ALL ancient Jewish melodies on King David's Lyre; "Hatikvah" - "The Hope" This ancient melody was later to be made the official National Anthem of Israel.

In this lesson, Misterduncan reads a short story, which he wrote himself. It is called "One Good Turn".

A marriage proposal in multiple languages such as Spanish, Portuguese, Hindi, French, Japanese, Russian, and English.

Tell a loved one "You're always on my mind" in many languages such as: Spanish, Hindi, French, Russian, Japanese, and English.

Let's practice some finger spelling this time faster! Look at the signer and write down the words he finger spells in American Sign Language (ASL).

Let's practice some finger spelling. Look at the signer and write down the words he finger spells in American Sign Language (ASL).