
How To: Create a MySQL Server BruteForce Tool with Python
Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.


Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Hello there Nullbyte users! This will be my first article here.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

What's up guys! It's time to discuss strings in more detail. Review

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
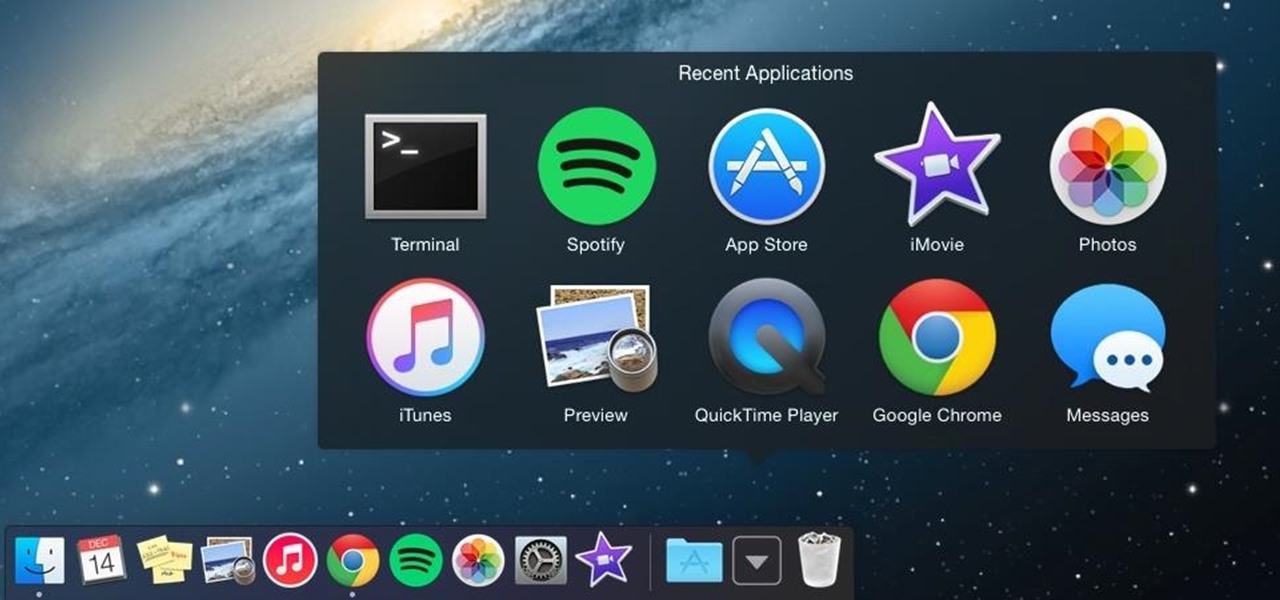
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

I was bored when I found this piece of literature: ==Phrack Inc.==

Hello again, ***UPDATE: Adding links to the other Two articles****

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.
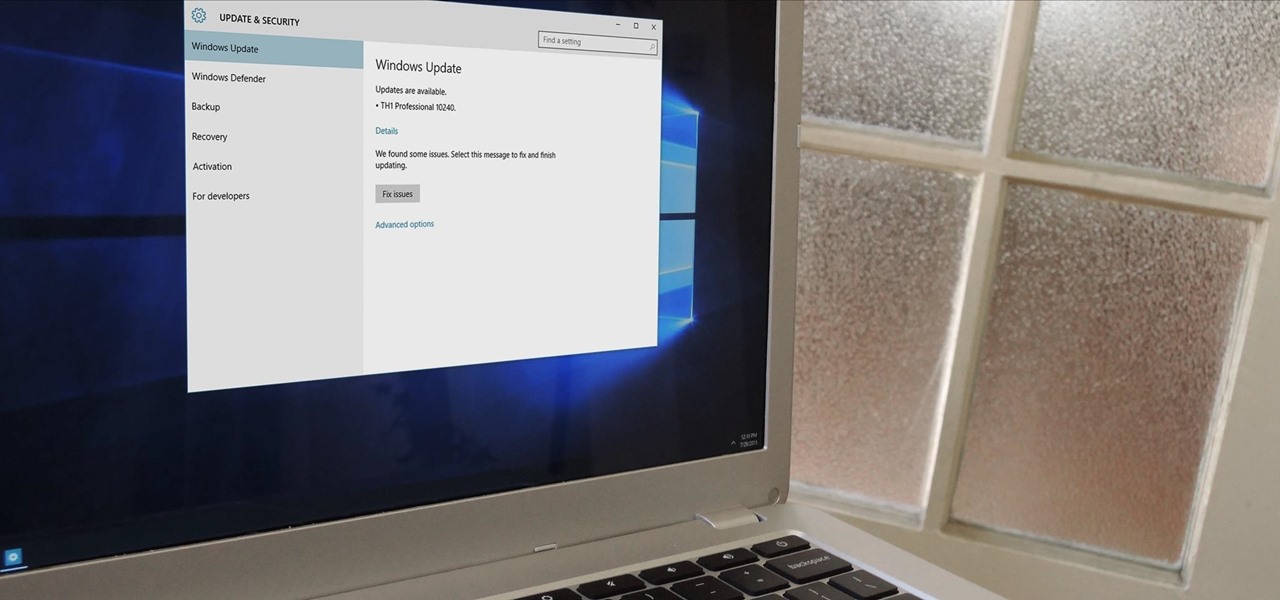
In a bit of a strange decision, Microsoft has made it to where some users don't have a choice in the matter of applying failed automatic updates. When a Windows or driver update comes your way and fails to apply for any reason, your computer will continue to attempt applying the broken update at seemingly random intervals. The Pro and Enterprise editions of Windows 10 will allow you to delay or stop updates altogether when something like this happens, but the Home edition has no such setting.

Why did I write this when they're tons of scanning tools available.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.
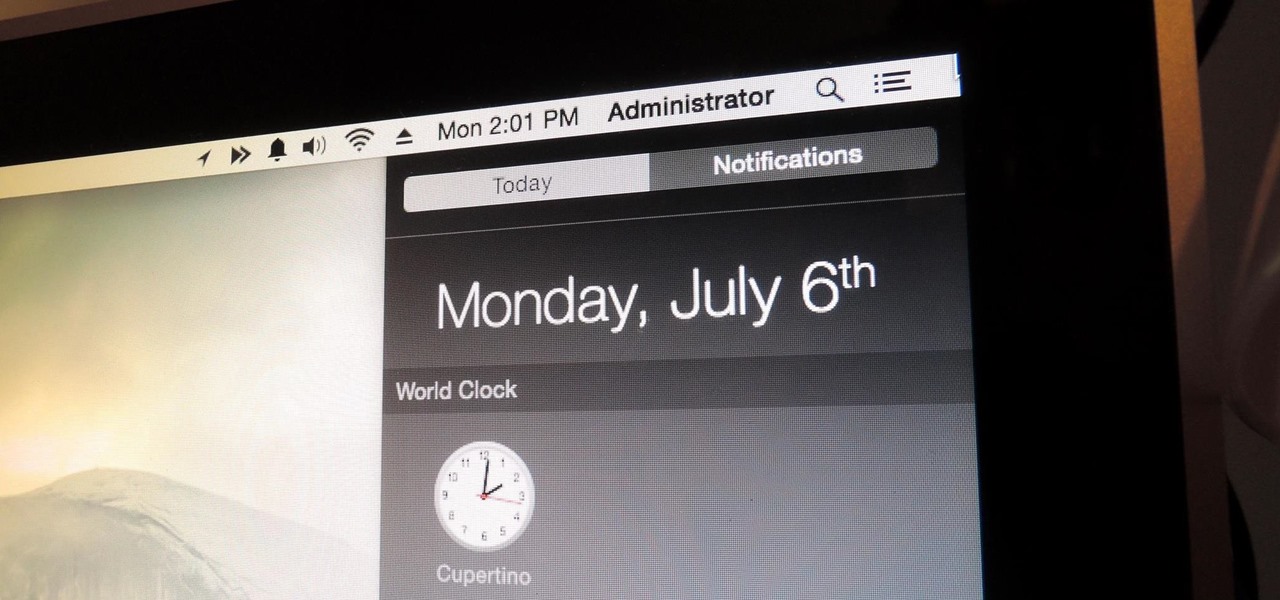
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.
Well, this is my first article so if it sucks tell me...lol!! Story Time
Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

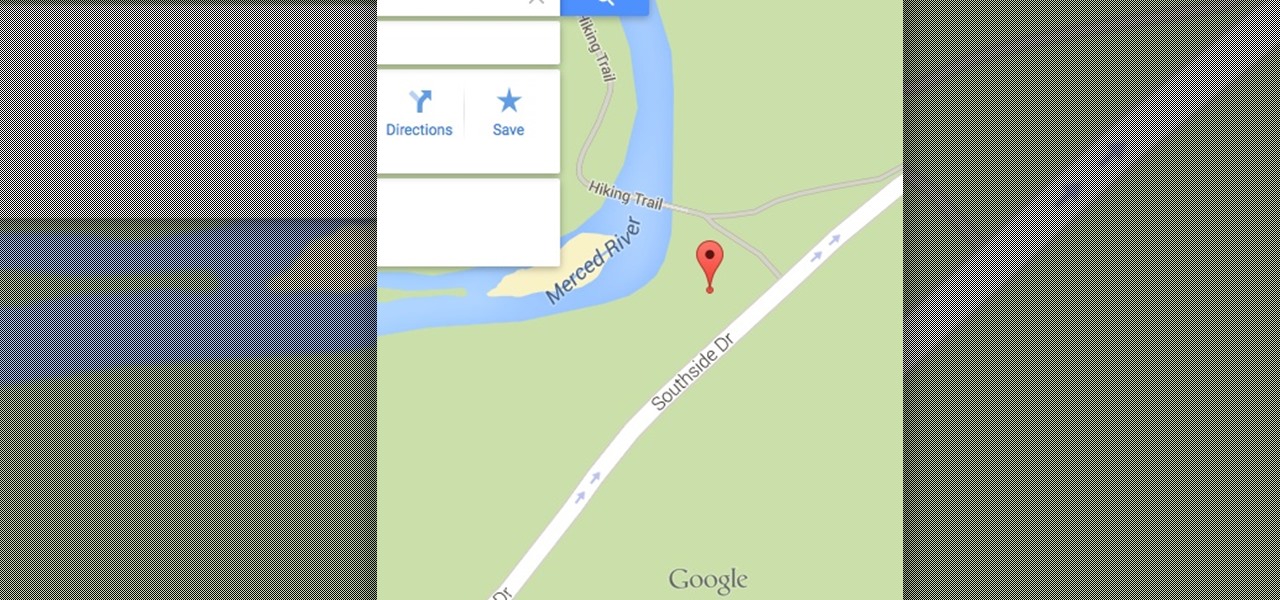
Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

A long time ago in a galaxy far, far away, a man by the name of George Lucas wrote an amazing trilogy about a new world and the power of the Force… and then subsequently ruined the franchise 22 years after the original release date.

Bringing lunch to work or school is a win-win situation. You save money, you eat better, and you create less waste. But while the virtues of brown-bagging it are undeniable, it also gets kind of boring after a while. How many times can you shove a container of salad or noodles into an insulated sack before you say screw it and buy a $12 burrito for lunch instead?