
Unless you've been living under a rock for the past few weeks, you're probably well aware that the Android world has been buzzing with excitement over the recently debuted Android L preview build that was released for the Nexus 5 and Nexus 7 at Google's I/O conference.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.
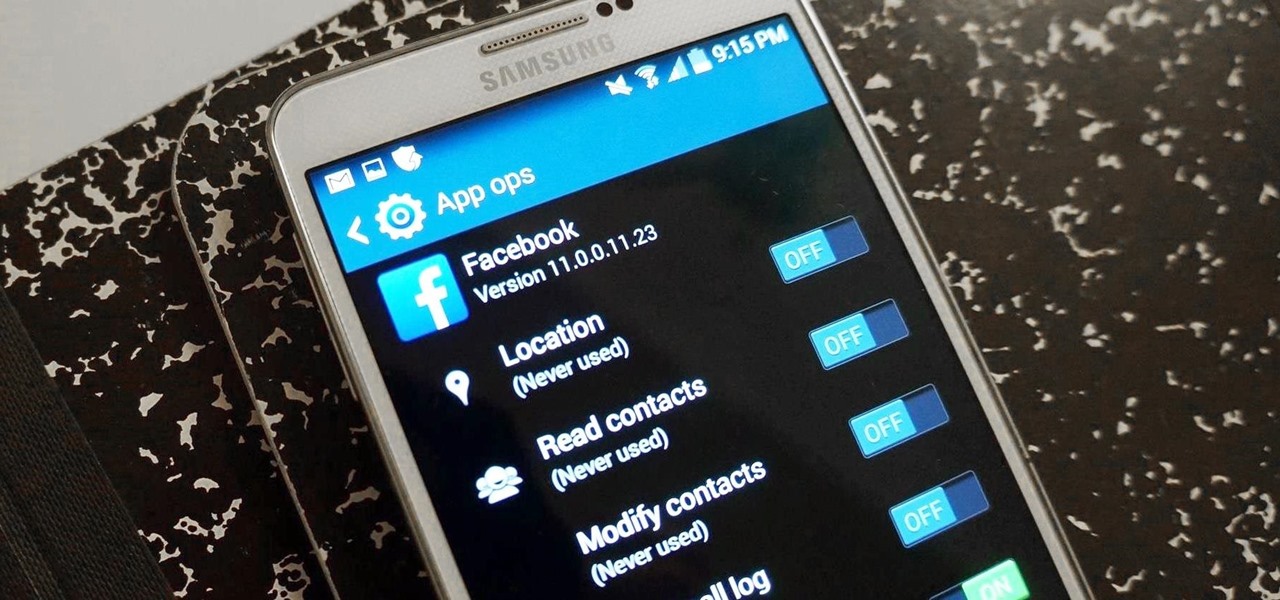
It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

We've already shown you how to dunk a regular-sized Oreo cookie while keeping your fingers pristine, how to upgrade Oreos into different desserts, and even make them into lazy ice cream sandwiches. Now we're going to introduce you to a few other essential Oreo hacks that will give you a brand-new outlook on a classic snack.

Your status bar is a hub of essential information, displaying things like battery life, signal strength, and missed calls and texts.
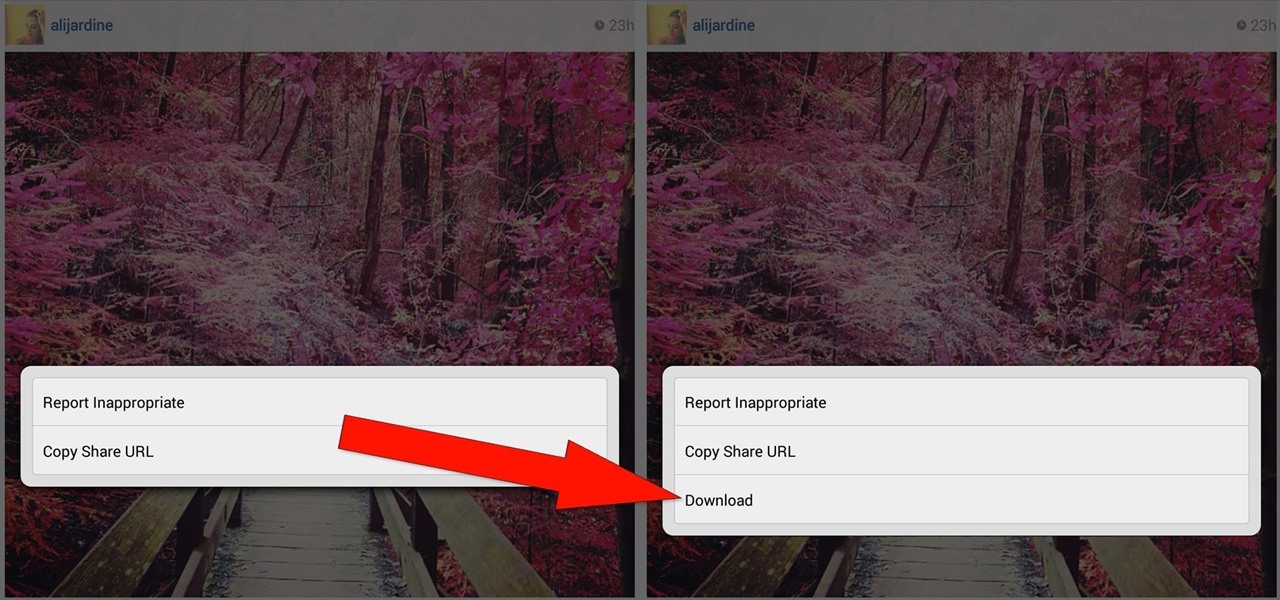
These days, everyone's snapping selfies, taking pics of their latest meals, or sharing pet trick videos on Instagram for the whole world to see. It's not only fun to shoot photos and videos for Instagram, it's inspiring to look at everyone else's creativeness in your feed.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

"Cheating is for losers" is only something that losers like to say. If you want to smash your friends and fly up the leaderboards, though, sometimes you have to go that extra mile.

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Hello! I want to share a few hints about staying literally cool when the temperature of the air outside rises incredibly. So, if you're in a very hot area, please continue reading!

Darts in fashion design collect fabric and add texture to a garment, and a fashion illustration needs to communicate darts well to sell. Learn to draw darts for fashion designs from a pro designer in this free fashion illustration video series.

Sign language, an often overlooked language, is incredibly beneficial to know and fun to learn. American sign language is very easy to learn for native English speakers and requires only a modicum of dedication, but the benefits of knowing sign language are immense. Imagine being able to communicate with someone who is often ignored because they cannot hear or speak the same language as those around them.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Defense is essential to playing basketball well. Learn basketball skills and strategies in this video basketball lesson which will show you how to guard your yard.

So you don’t need to have a full on conversation but you do want to relay some information to someone. A text message the perfect option to get a short message across using your cell phone or even just to say hi.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can make way for such things as TWRP, Magisk, custom ROMs, and many other device-specific mods just the same.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple might not be ready to unveil its rumored-yet-unconfirmed smartglasses. But the iPhone's current depth-sensing hardware is proving to be useful for both smartglasses makers and mobile AR apps.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Apple has several ways for you to communicate in the Messages app aside from texting — and that includes audio messages. You can send a voice recording via iMessage by long-pressing the microphone icon just right of the input field and speaking. However, by default, these audio messages self-destruct after two minutes, which isn't good if you want them archived.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.






































