While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

The original iterations of the Terminator film franchise have served as the inspiration (via the heads-up display of the T-800) for future augmented reality dreams, so it is fitting that the current crop of AR gives the latest installment in the series a promotional boost.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

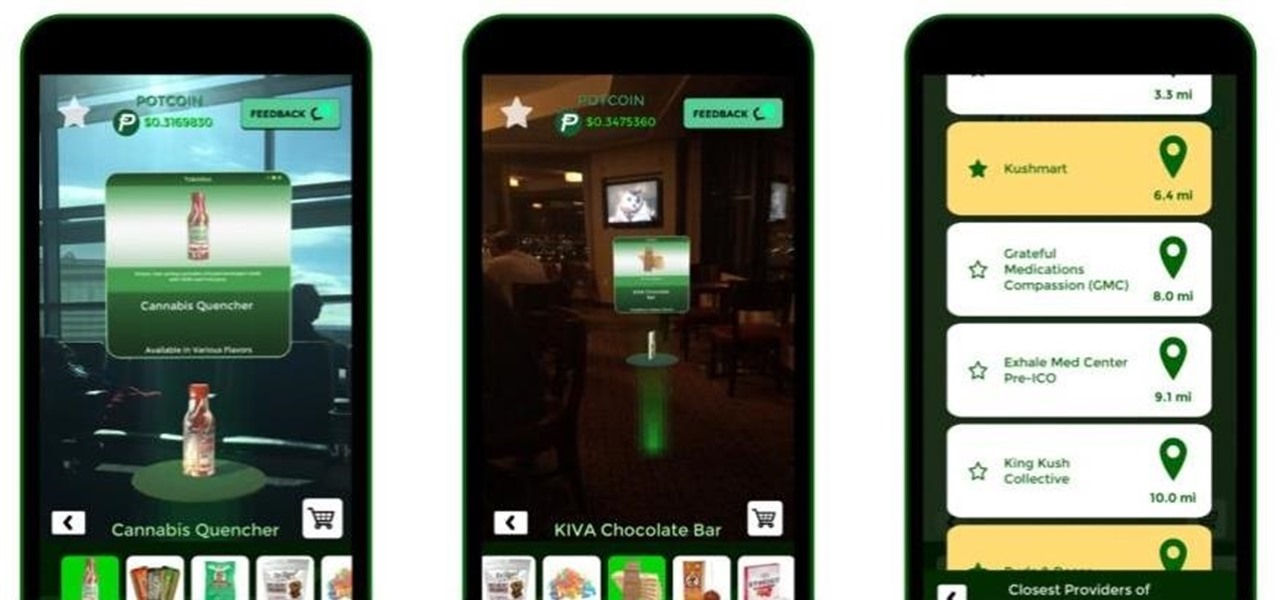
If there's one augmented reality app idea that should have gone up in smoke, it's probably Tokédex, an app that brings cannabis to the world of AR.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

Phuket, the island in Thailand typically associated with paradise and most recently, illegally-run hotels, now has a different problem—a stray cat with the claws of death.

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

The Last Supper, or L'Ultima Cena, is a mural painted by Leonardo da Vinci in 1498. It is considered one of the greatest paintings of all time, and if you live in the San Antonio, Texas area, or are willing to travel, you can get it shaved into the back of your head.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

If you're a fan of the Metal Gear video game series, an obvious Halloween costume choice would be Solid Snake, the protagonist of nearly all of the games. However, an even better option would be Big Boss, aka John, Ishmael, Vic Boss, The Man Who Sold the World, and Naked Snake, among many other aliases. He's was once a good man, but better known as the nemesis to Solid Snake. The below costume by YouTube user Erick Zeros showcases Naked Snake in his good era, in Metal Gear Solid 3: Snake Eate...

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

It's late and dark, I'm playing Dying Light, and, admittedly, I'm a little creeped out. Working as a grown man's night-light, this is one instance where I actually appreciate the light bar on my PlayStation 4's DualShock controller. But outside of a few particular instances, I generally find it to be quite a nuisance.

Android 5.0 "Lollipop" has only existed for a few months, but a leaked version of Samsung's take on the firmware has already been spotted in the wild. This update came straight from Samsung, and brings with it a plethora of new features, including greatly improved performance and a revamped TouchWiz UI.

In 1999, Robin Williams starred in Bicentennial Man, a movie in which Williams played a robot named Andrew Martin, taking care of a family as a their nanny and personal assistant. For almost 15 years, I have waited for my Andrew Martin, but until now, I have been disappointed. Luckily, Jibo is on the job!

Day of the Dead, or Día de Muertos, is a Mexican holiday celebrated on November 1 or 2 each year to honor the dead. It's often lumped in with Halloween, and while some people do dress up in costumes, the day is much more focused on remembering the lives of friends and family members who have passed. People who are unfamiliar with the holiday sometimes consider one of its most pervasive symbols, the sugar skull, rather morbid. And special makeup effects artist Rick Baker is no stranger to the ...

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

You know that guy who does the cheesy card trick to get the attention of all the girls at the party? Well, we kinda hate that guy don't we? But, if we could be that guy, it might not be so bad.

Roughly five million years ago, humans split off from chimpanzees, who had in turn split off from gorillas five million years earlier.

Christopher Nolan's Batman trilogy has been one of the most successful film series of all time, so it comes as no surprise that everyone wants their own real-life versions of the Dark Knight's gadgets and vehicles.

Small containers are useful for many things. They're good for storing snacks if you have children, as well as holding coins or odds and ends. But those regular store-bought containers are lame—who wants to keep their stuff in a Tupperware dish or old butter container?

Wolverine (AKA Hugh Jackman) looks so deliciously perfect in his spiked out hair and scruff that women all over want to be with him and guys want to look like him. While his rock-hard abs, perky derriere, and sculpted biceps take months of hard work to achieve, you can get his beard look in just a few minutes by checking out this hairstyling tutorial for guys.

Everyone does it. And, apparently, everyone does it late. Procrastination is a problem that affects everyone, from middle schoolers waiting until the last minute to put together their science project to grown men who wait until an hour before to write their marketing pitch.

In this tutorial, we learn how to draw Ironman. First, draw the outline of the body, make sure to include the heart in the middle of the body and the squares to make it look like metal on the outside. From here, start to add in the finer details on the body as well as the features on the face. Once finished, erase the background lines and then color in the background of the drawing. After this, color in the character with the appropriate colors and then define the features. This will finish u...

In this tutorial, David Wygant teaches us how to flirt with women at coffee shops. First, find the right place you want to go! If you think that going to a sports bar is a good idea, think again! Go to a place like the one you see in this video, "Tea Palace". There will be a TON of women inside places and cafes like this. If women are together, they will most likely be trash talking about men. You can easily start a conversation with a woman or group of women if you are in a place like this. ...

In this tutorial, we learn how to meet guys everywhere by changing your body language. If you are sitting down with a woman during an afternoon, you need to change your body language to attract men. Don't get too close to the girl and move away from the open edge of the table. You want to notice the surroundings near you and keep your body opened up to people coming up to speak with you. Invite energy over to you and keep a smile on your face. You can carry on a conversation but also invite a...

In this tutorial, we learn how to attract a women at first glance. First, find a guy that you think dresses really well and dress just like them. Don't jam your body into something that doesn't fit you, find something that fits you well. A woman wants a man that looks completed, not someone that looks like he needs to be changed. Fashion is a statement to the woman that is your own personal brand, it shows the woman who you are. Get your clothes together and go out there to get the woman that...

In this tutorial, we learn how to be powerful & get inside a girl's head. To pick up a girl, you need to be confident and engage a girl. Women over the age 22 want to be engaged and want guys to be confident with them. They also want men to listen to them! Getting the phone number, getting her to think about you is what its all about. When you go in weak and don't listen to a girl, she is not going to respect you or think about you later on. Use these tips to help get a girl, enjoy!

Mermaids have long beguiled unassuming man, even back in Ulysses' time when their beauty and mesmerizing songs led him and his ship crew astray, sinking their vessel. Pretty and shimmery, a mermaid is also an ideal of beauty for many young girls.

Girls always want they don't have. We know lots of girls with freckles who prefer to cover them up, which there are those of us who wish we had a few cute ginger spots on our faces.

In this video we learn how to say "I love you" in Korean. Korean people generally don't say "I love you" because it's not a verbally expressive culture. You wouldn't often say "I love you" to a Korean woman or man. Learn how to say this by first learning how to say each of the individual words and then put them all together. Remember that there are no pronouns in Korean, so don't try to say them in the word. If you want to change the punctuation you will have to change how the words are said....

In this tutorial, we learn how to attract women with your emotions. Don't make the mistake that being stoic or not showing emotions is a strong and manly characteristic. You want to show a woman that you are emotional, just not too emotional. Show the range of emotions that you feel everyday. Show that a real man will be happy, sad, mad, and anything else! This will make you look more authentic to a girl and powerful because she will see that you are yourself around her. This will make women ...