In this series of instructional video clips you'll learn how to build the perfect tool kit for your home improvement needs. Expert Carolyn Saylors offers tips on choosing the right type of box to store your tools in, and shows you step-by step what tools are absolutely necessary to keep in your home. She explains the various types of screwdrivers, including torque and all-in-one models, the most commonly used types of pliers, wrenches and ratchet kits, drill bits, small saws, levels and hamme...

If you like 2D side-scrolling video games, then Shank's your man. Shank is full of "beat 'em up" action and combat, perfect for any gamer addicted to the old style of play. Shank is available on both the Xbox Live Arcade (Xbox 360) and PlayStation Network (PS3). But this Mahalo walkthrough for Shank is for the PlayStation 3.

How would you like to make your own lip balm/chapstick? It's easy to do with a few simple products. One way to do it includes beeswax, coconut oil, olive oil, raw honey, peppermint oil (for scent), and mineral powders (for colors). The tubes to put the lip balm in are available online if you want to use those instead of another container.

The 1960s were an important decade for men's and women's fashion. Learn about different 1960s retro fashion trends from a retro fashion specialist in this free fashion video series.

Lose weight with this handy Chindogu invention. Shaving Cream Man Solution show teaches us how to diet using the Mirage Meal - Mirror Bowl. You can purchase the children's book featured in this video by following this link: http://www.blurb.com/bookstore/detail/176116

No, not Charlton Heston. The only pudding he ever made was steak and kidney. I'm talking about Heston Blumenthal, world famous chef and pudding lover, and the man behind the "Heston"— a plum pudding with an orange hidden within, brought to you by Waitrose (see video below).

A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to the wrong person.

The beginning of autumn has delivered a number of new augmented reality developments, and we're on top of it.

After facing delays due to the COVID-19 pandemic, the Olympic Games are underway in Tokyo, but a surge in cases worldwide has taken the spectator out of these spectator sports.

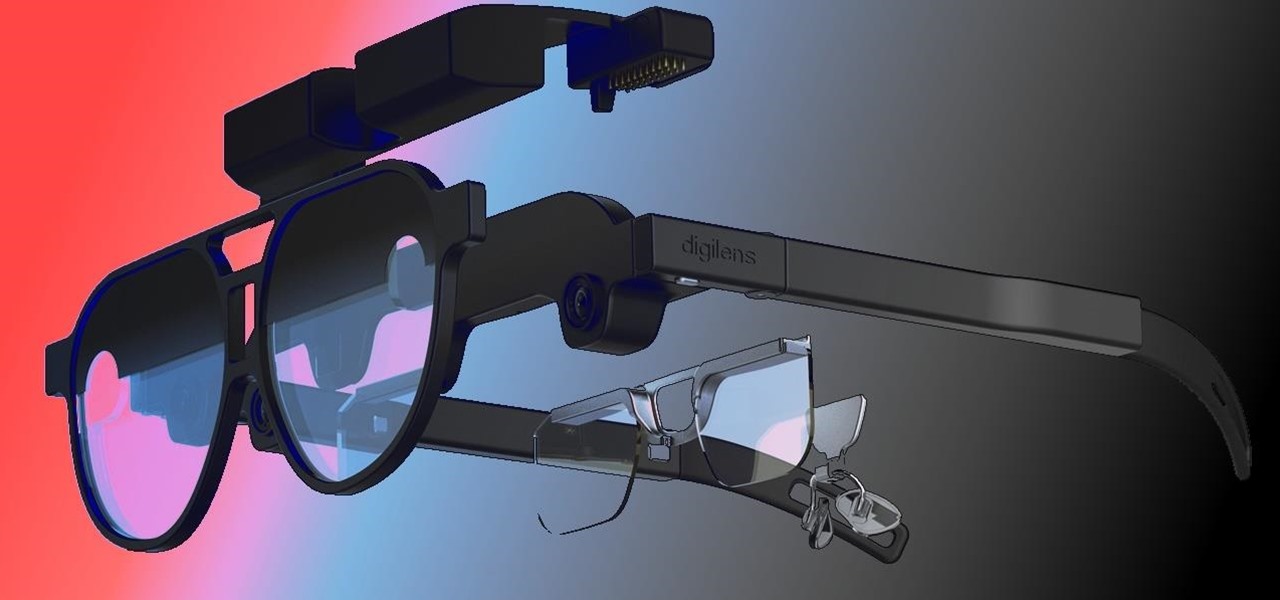
When it comes to the future of AR smartglasses, DigiLens has one word for you. Just one word. Are you listening? Plastics.

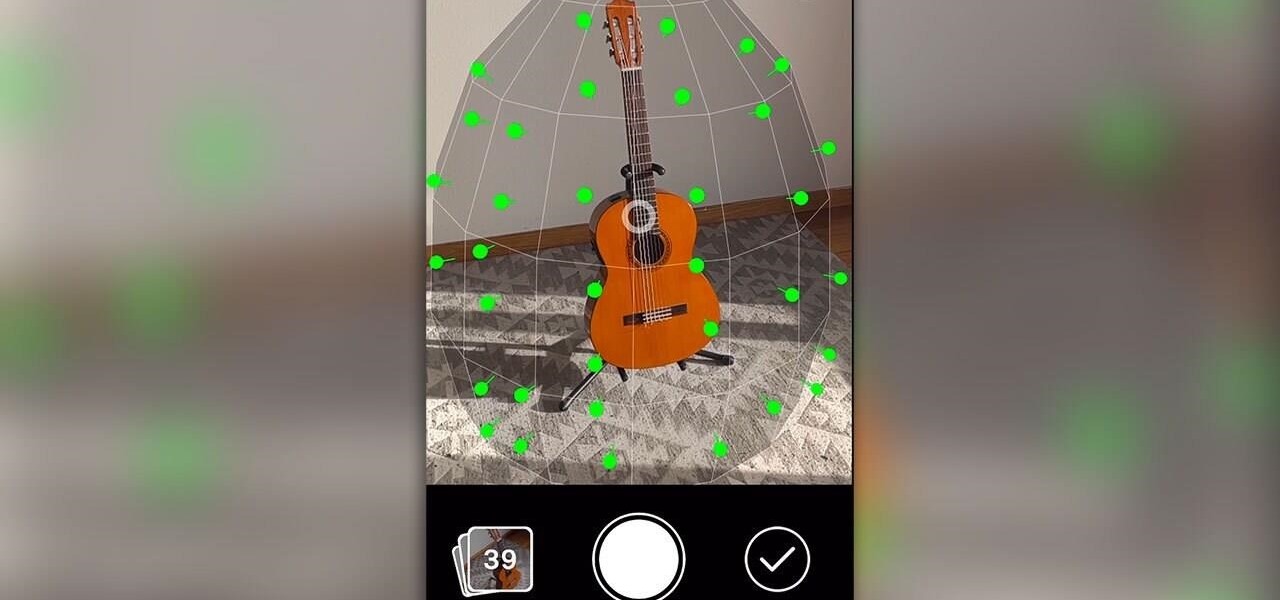
One of the more exciting augmented reality announcements Apple made during its WWDC keynote on Monday came in the form of Object Capture, a new 3D scanning feature coming to macOS Monterey.

ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills.

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

If you're using the default Samsung Keyboard on a Samsung Galaxy smartphone or Gboard on a Google Pixel or any other Android device, here's a cool trick you should know about.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a reality check because you can start browsing Twitter and Reddit on your Apple Watch right now.

We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.

One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones released in the US. We pride ourselves on being fair in our reviews and roundups, but that doesn't mean we don't have preferences.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Magic Leap is making it easier for developers to share their spatial computing experiments with other Magic Leap One users.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

In the last few years, the HoloLens has become a popular tool for use in medical procedures and training. But recently, the Magic Leap One has gained momentum in the space as well when it comes to medical use cases.

A new profile on Apple's exiting design chief Jony Ive, the man behind many of the company's most successful products, paints a fuller picture of what led to his departure.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Two years ago, Facebook founder and CEO Mark Zuckerberg kicked off the F8 Developers Conference keynote with augmented reality and the introduction of Facebook's AR camera platform, now known as Spark AR.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

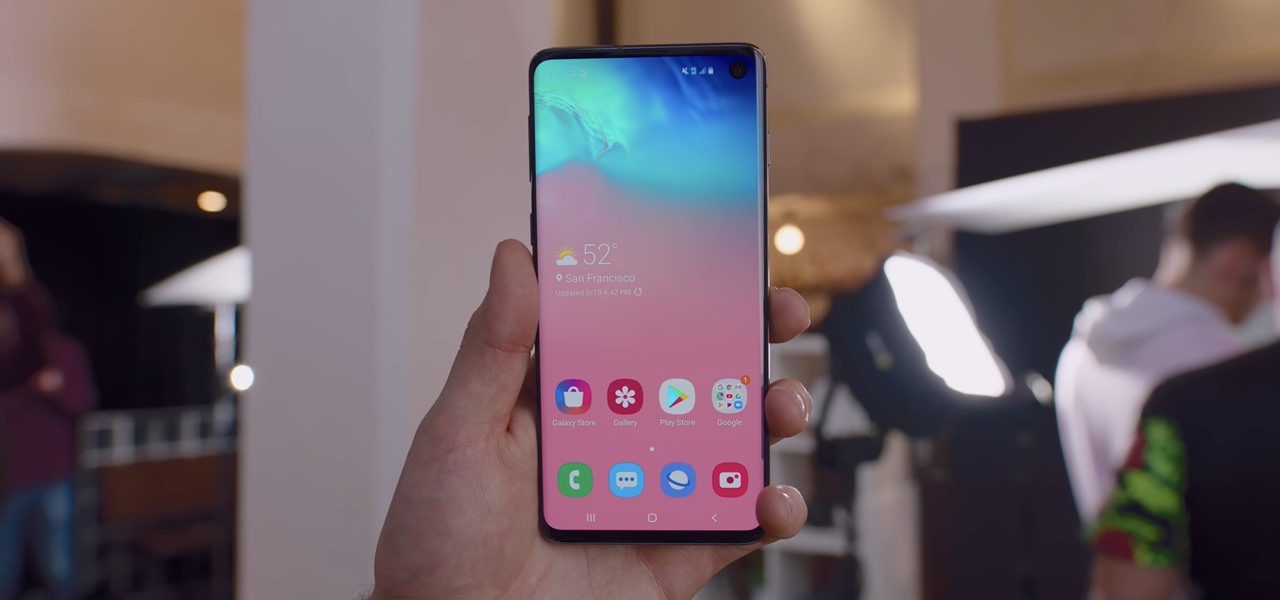
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Occasionally, a not-so-great movie also does something so right that you have to forgive some of its sins and give it a little love. Such is the case with the latest film from Keanu Reeves, Replicas, which takes a HoloLens-style device and gives us a look at how future research labs might use that kind of augmented reality device, sort of.

The team at Magic Leap just got a millennial-style boost with the announcement that financial news network Cheddar is coming to the Magic Leap One.

One the leading game developers for the PlayStation 4 and Oculus Rift platforms, Insomniac Games, is finally releasing its first major augmented reality title: Seedling for the Magic Leap One.