Elliott Smith was more than a great songwriter; he was a great guitar player. This video guitar lesson presents a step-by-step walkthrough of Elliott's "Angeles." While this tutorial is geared toward intermediate and advanced players, even beginners will find much to take away. For more information, and to get started playing Elliott Smith's "Angeles" on your own guitar, watch this how-to!

Elliott Smith was more than a great songwriter; he was a great guitar player. This video guitar lesson presents a step-by-step walkthrough of Elliott's "Memory Lane." While this tutorial is geared toward intermediate and advanced players, even beginners will find much to take away. For more information, and to get started playing Elliott Smith's "Memory Lane" on your own guitar, watch this how-to!
In this case modding video tutorial, you'll learn how to install a cigarette lighter-style 12-volt accessory outlet into a PC case. Charge your cell phone and other accessories directly from your case with the hack outlined in this video. For detailed, step-by-step instructions, take a look!

This instructional knitting video will show you how to knit a hat using a fixed circular needle and bulky weight yarn. These step by step knitting guidelines cover casting on, knitting in the round, decreasing, and weaving in the ends. If you are a beginner, you may want to avoid thin yarns to save time and knit a warmer hat.

Draw scary cartoon witches for Halloween cards and birthday cards. You might be able to use a dry erase marker to trace the drawing steps directly off of the computer screen. Of course, you can only participate in this practice if you have a glass computer screen. Otherwise, use paper.

This how to video shows a calming singing lesson for improving your voice. You will learn how to sing a three step scale with this tutorial. This exercise is an excellent way to learn improved vocal tone and breath control. With the tips from this voice lesson you can learn how to sing a 3 step scale.

Knotting tips from an expert! Learn how to tie essential knots for any camping, hiking or sailing trip in this free video clip series on the outdoors.

Remodeling your home or backyard can be expensive, but you can save some money by doing it yourself. If you are re-tiling your patio steps you can grout them yourself. In this Home & Garden how-to video you will learn how to grout your newly tiled backyard steps.

Learn how you can sharpen your mower blade with this step by step tutorial. After time and use your lawn mower blade will dull. Watch this how to video and you can safely and easily sharpen your lawn mower blade.

Create a simply beautiful beaded wire ring in minutes with this step by step guide. This delicate ring design will look simply lovely with any style of bead. Be creative. Learn how to craft this beaded wire ring by watching this video jewelry-making tutorial. Get beading!

Want to learn how to line dance like a cowboy? This country western tutorial teaches the basic steps of line dancing such as the jazz waltz, the grapevine and the kick ball change. Follow these simple steps and you will be slappin' leather in no time.

Check out this step-by-step guide on how to create a little elephant! Use sugarpaste mixed with CMC (Tylose/Tylopur) for this elephant. Ready made gumpaste will do the same job!

Scary Dave, leatherworking master craftsmen, shows how to make this painted and etched leather cuff bracelet. Follow along with these step by step directions and learn how to craft a beautiful leather bracelet with a feather pattern.

This is a medium difficulty juggling technique known as Mills' Mess. Always practice each step before moving on.

This is an advanced juggling technique knows as Rubenstein's Revenge. Always practice the steps before trying the whole thing. This is advanced level.

Here is a step-by-step guide on how to spring of in a sailboat

Tying the Lefty's Deceiver - a classic baitfish pattern and "go-to" pattern in saltwater. Capt. Corey P shows us the step-by-step construction of this HIGHLY effective saltwater fly pattern.

Do you want to learn to play drums for the very first time? Watch Mike Michalkow's step-by-step training video to get started. It will guide you through four simple patterns that form a basic rock drum beat.

A simple step by step method to make Freeline Skating look easy!

Check out this video for a step by step process on how to use just one piece of paper to make a book with 16 pages. (Do it the origami way!) You can even make it into a flip book later.

Learn how to make delicious sushi like a real chef. You may think sushi is just raw fish, but you’d only be half right. It’s actually the combination of fish and rice – and how it’s combined is an art form in itself.

This tutorial goes over how to perform ni-cho zai. This kata utilizes 2 zai (sais), and the video includes the bunkai, or step-by-step analysis.

Step by step instructions on how to make an air conditioner using parts that cost less than $40.

Therefore, those tires still need to be changed from time to time, because of a flat, or because the tread wears out—or maybe just for the purposes of an upgrade. In this motorcycle maintenance video series, learn how to change a tire on your bike. Our expert mechanic will walk you through the process, with tips on what tools to use, how to remove the carter pin and axle nut, how to loosen chain bolts and punch the axle, types of tires to choose from, how to replace the tire and properly alig...

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.

What if you went to an art installation at one of the coolest venues in New York that you could then take with you anywhere in the world?

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

The mystery surrounding Overture, an app that showed up in the Magic Leap World app store along with the latest Lumin software release, has been cleared up.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Fresh off of shipping version 2019.1 in April, Unity has already dropped the beta of 2019.2, and it has a bunch of new AR Foundation toys to test.

Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

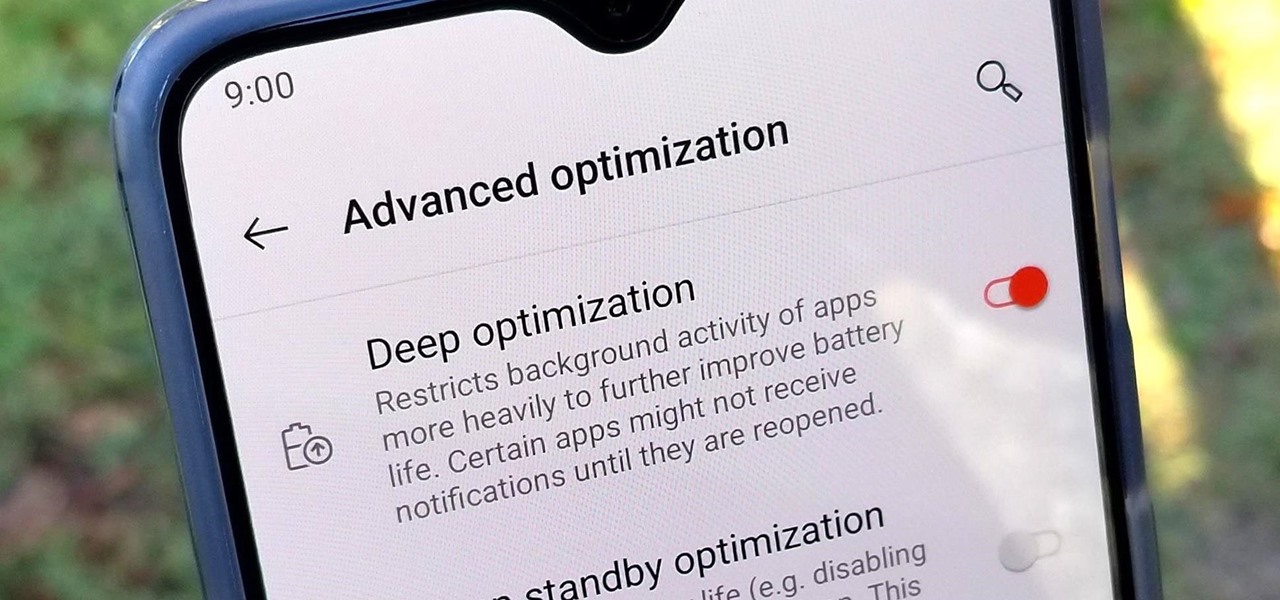
OnePlus is known for pushing the boundaries of what we thought was possible for a mid-range price. One of the best things about OnePlus phones is that their battery life is fantastic in general, but to achieve this, Oxygen OS will disable or delay notifications by default once your phone goes into deep sleep mode. You will not be notified until you wake the phone up — this could be an issue for some.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.