This "How-to" is how to survive your first night on Minecraft. This is for new Minecraftians to Minecraft. The first thing you want to do is find wood. This is very essential to survive your first night. Then, you want to make wooden planks. To craft anything, press E or I. After that, there should be a 2x2 box at the top. Put two wooden planks on top of each other. If you did this right, there should b four sticks to the right. After that, you want to make a Crafting Table. To make a Craftin...

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.
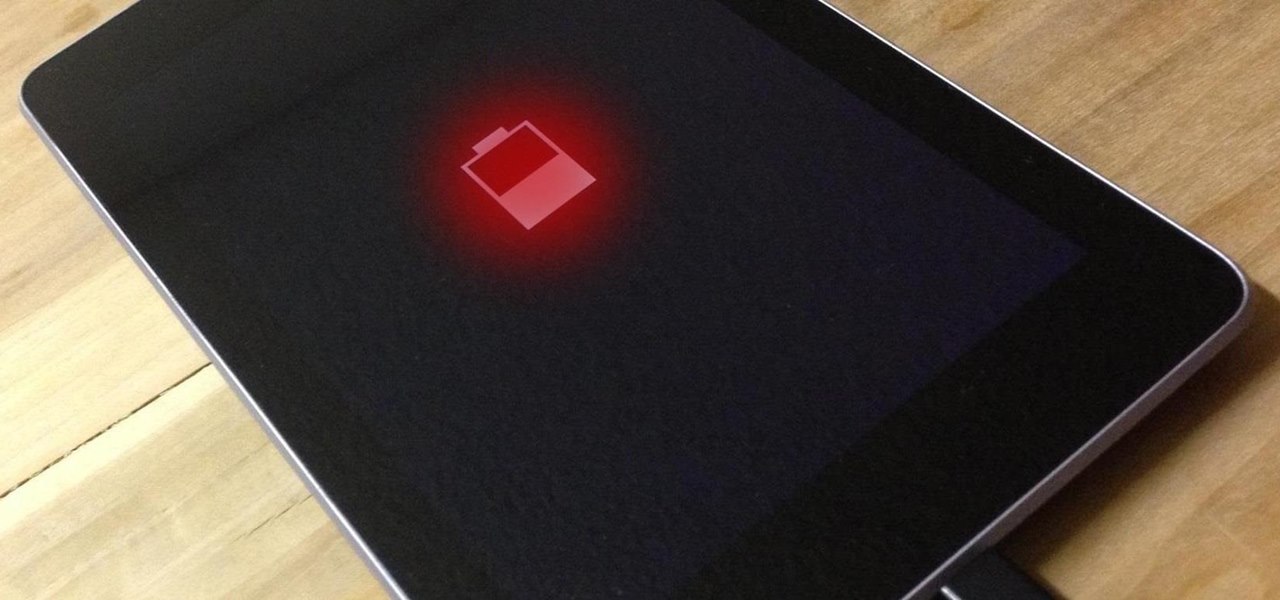
Like most Android devices, the Nexus 7 suffers from its fair share of battery gripes. Nobody wants to see that dreaded "connect charger" warning pop up on their screen. NOBODY. Yet it probably happens to you every day nonetheless. What can you do about it besides charge, charge, and charge? Well, there's actually plenty that you can do. You can manage your notifications better, keep your screen brightness low, and kill apps running in the background. Or, you could just optimize your battery t...

Thanksgiving is pretty much the only day out of the year when you can be a complete fatass. It's totally expected, if not encouraged. In fact, if you aren't stuffing your face with a bunch of delicious and unhealthy food, people start to look at you funny.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

If you've ever wanted to start learning to code but haven't known where to start, then one of the best places is with Python. It's great for introductory programmers, and it's also a must-have addition to the repertoire of anyone experienced in the industry. As of 2019, over eight million programmers have used Python, and the industry has only grown since then, so the best time to start practicing is today!

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

IT is a competitive field, and finding success requires more than knowledge of a couple of coding languages or knowing how to google really well. To stand out among your peers and competitors, you should learn everything you can and get as much diverse experience as is available.

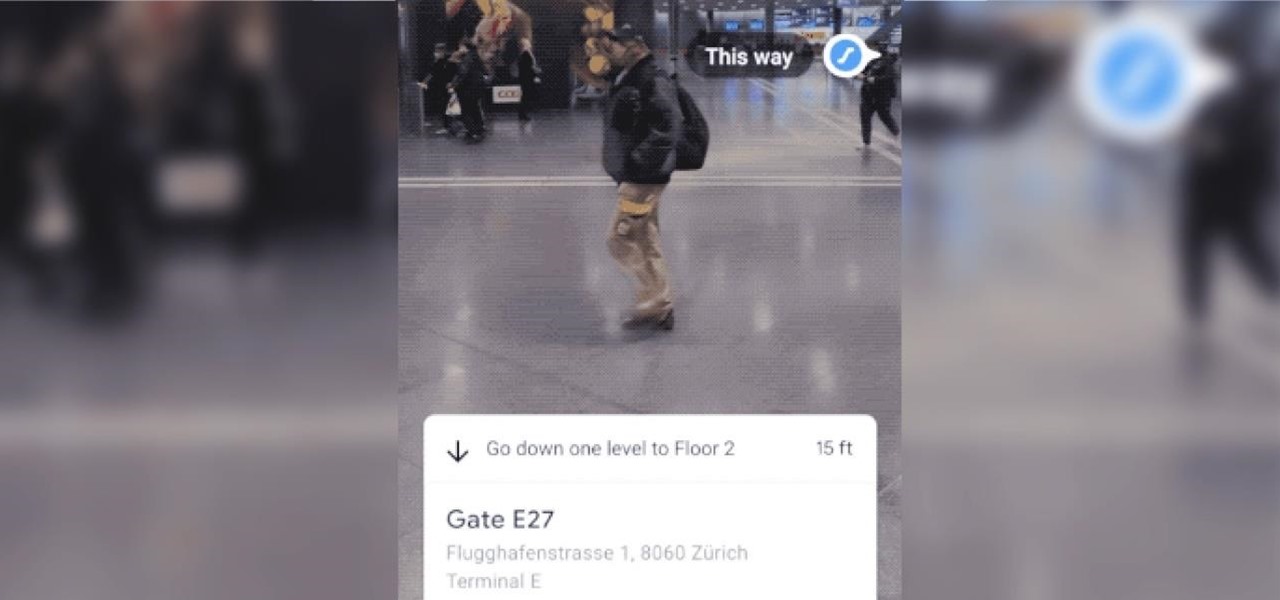
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

We all know IT development is a valuable skill to have. But being a certified professional in the world's most in-demand project management and development tools? That's enough to get the promotion or new developer career you've been dreaming about.

We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limited time, a YoData VPN: Lifetime Subscription is on sale for just $17.99. That's 69% off the regular price of $59.

Everyone needs a great website. Whether you want to launch the new business you've been dreaming about in 2021, increase your brand's web presence and bring it into the digital realm, or promote yourself and your portfolio, a fully optimized website is the way to do it — and the results can be life-changing.

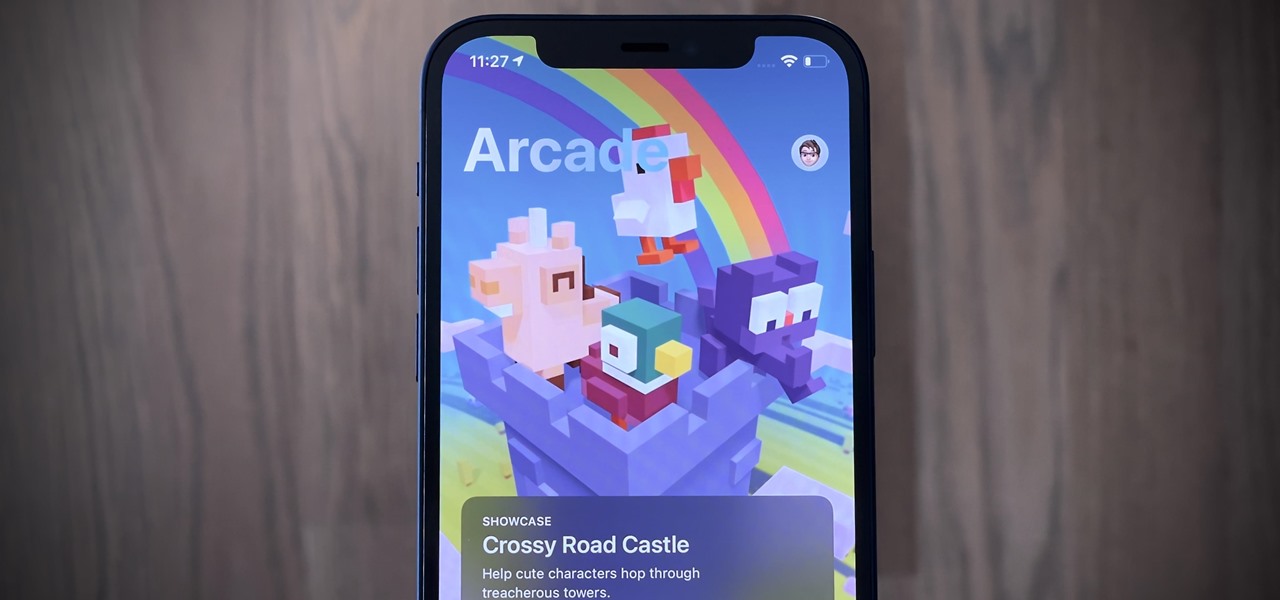
When it comes to mobile gaming, it's tough to beat Apple Arcade. With over 100 games and counting, there's something for everyone to play. That said, the ever-growing list of titles can make it difficult to find the games that are right for you. That's why Apple Arcade's sorting and filtering tools are essential for any subscriber.

People are going nuts with their iOS 14 home screens. One look on social media shows just how creative people can be with their home screen widgets and customized app icons. That said, maybe you aren't looking for a crazy setup. Maybe you're someone who wants a simple, clean home screen. Friend, this trick is for you.

Your iPhone's Voice Memos app is an easy tool for quickly recording lectures at school, jam sessions at the studio, or just verbal notes to yourself. While it's a straightforward app, there are several hidden features you might not know about that can improve the quality of your recordings.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

Despite some early and optimistic predictions that the world would have returned to normal by now, the surprisingly stubborn and resilient coronavirus continues to upend and alter how we live our lives when it comes to working from home instead of the office.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

For those not used to it, working from home can be a difficult transition. Everything around you can be a distraction, and distance from your boss and coworkers means less pressure and incentive to get things done. So it's not surprising to see a major drop in productivity during a period of self-quarantine, but your phone can help you stay on track instead of sidetracking you.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

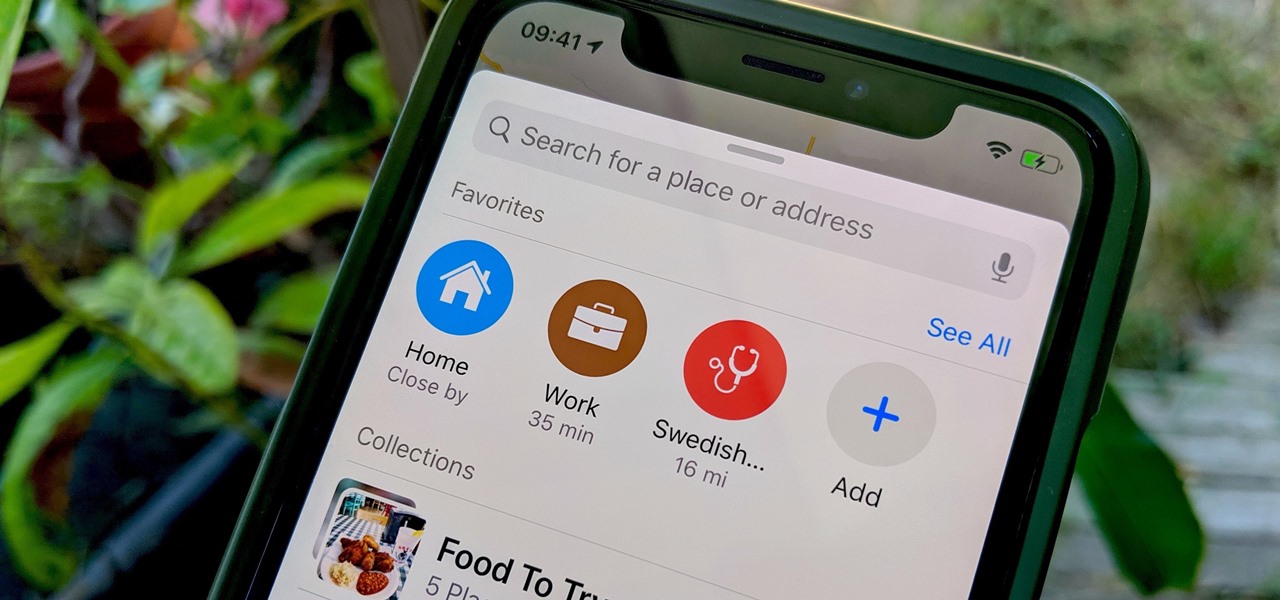
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

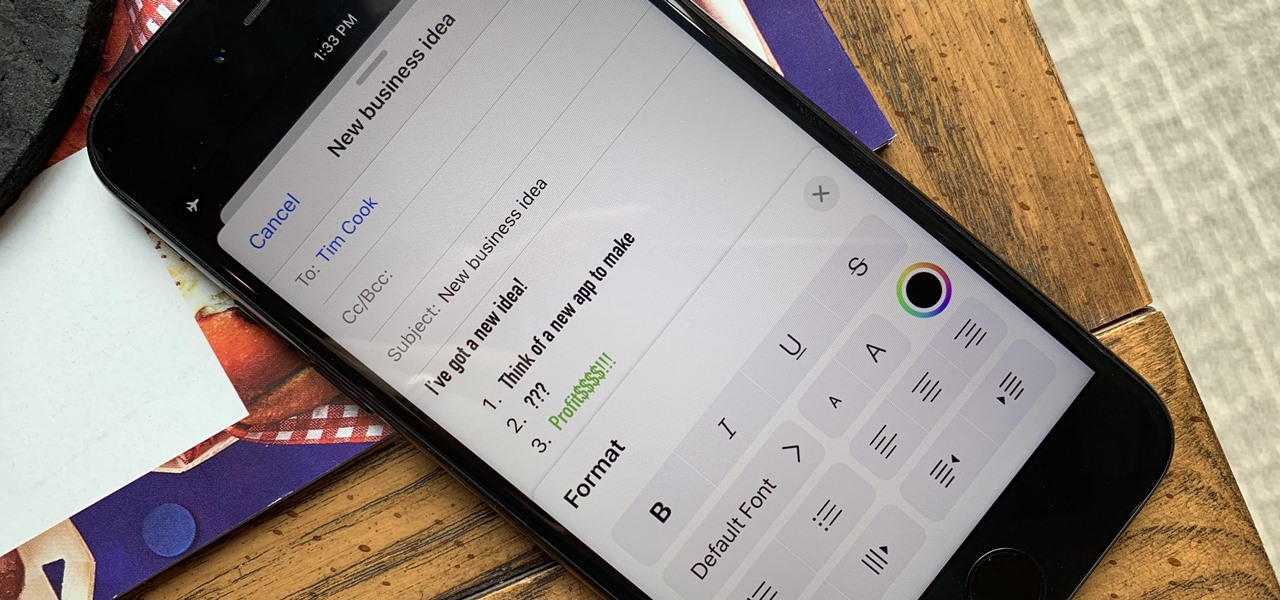
Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

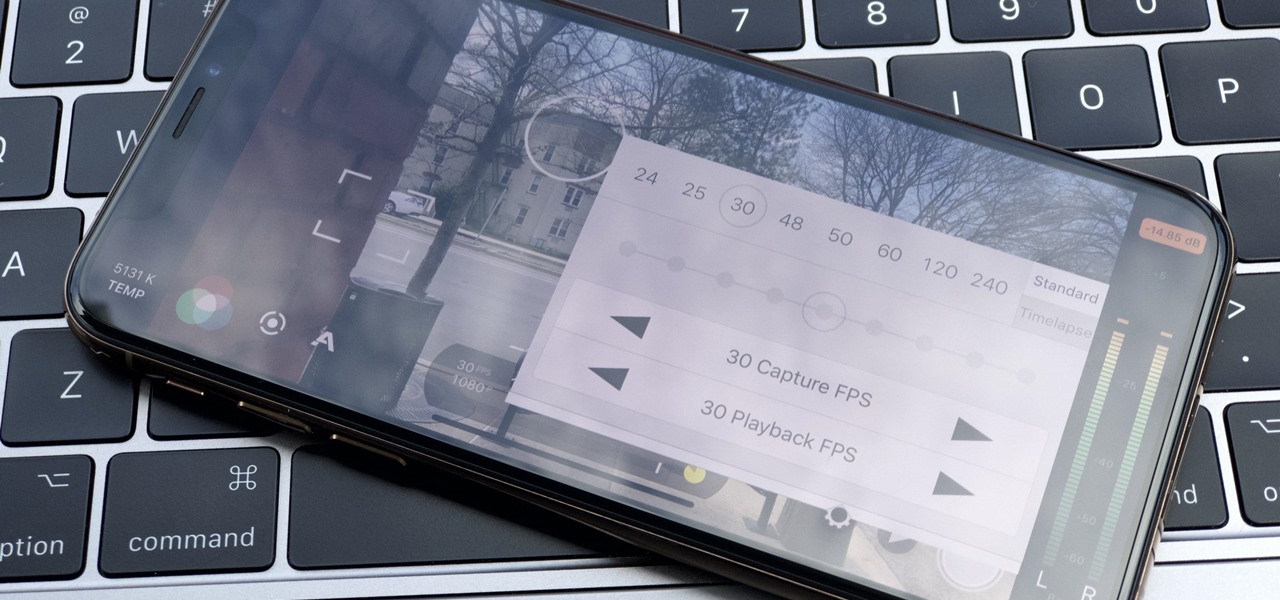
The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.