T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normally required.

With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun.
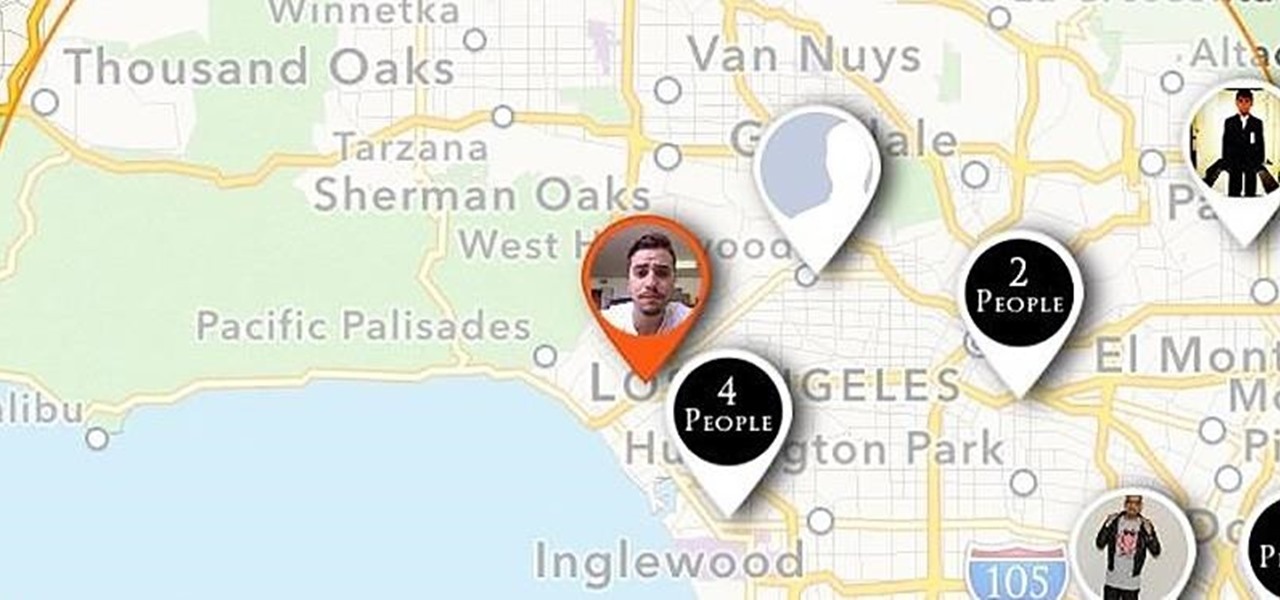
Imagine that Tinder fornicated with Facebook and had a baby. The product of that union would be the hideous, yet overwhelmingly interesting SocialRadar, an app dedicated to stalkers and stalkees.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

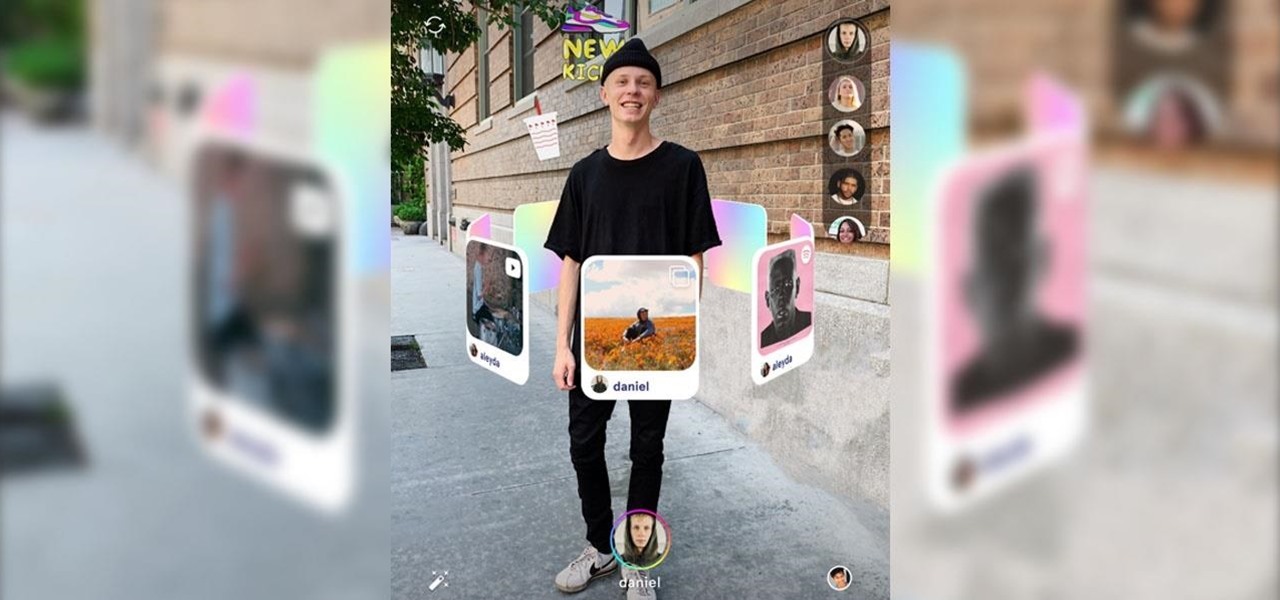
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

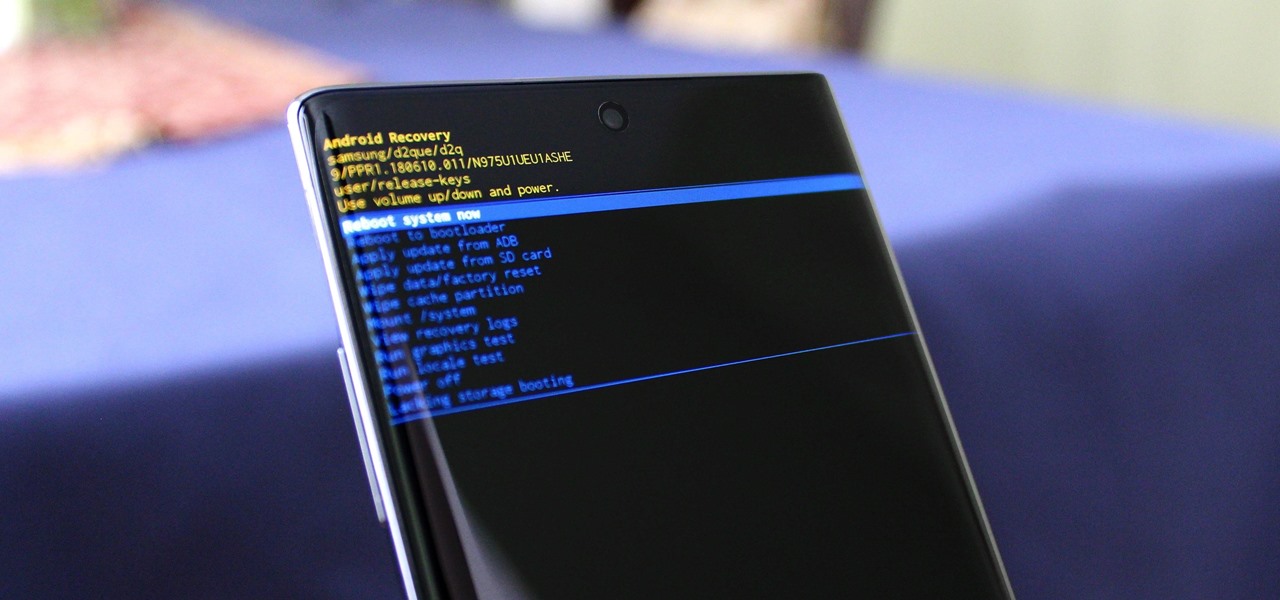
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

Fresh off shipping an augmented reality game for Magic Leap, Resolution Games has farmed another $7.5 million in funding through a Series B round.

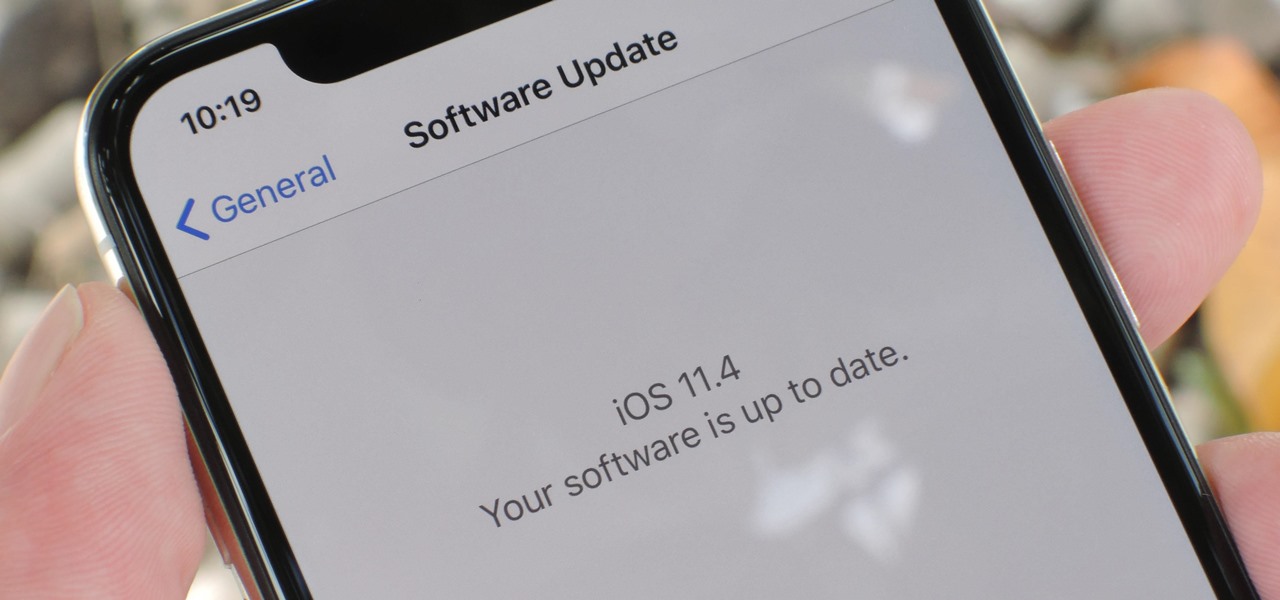
Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

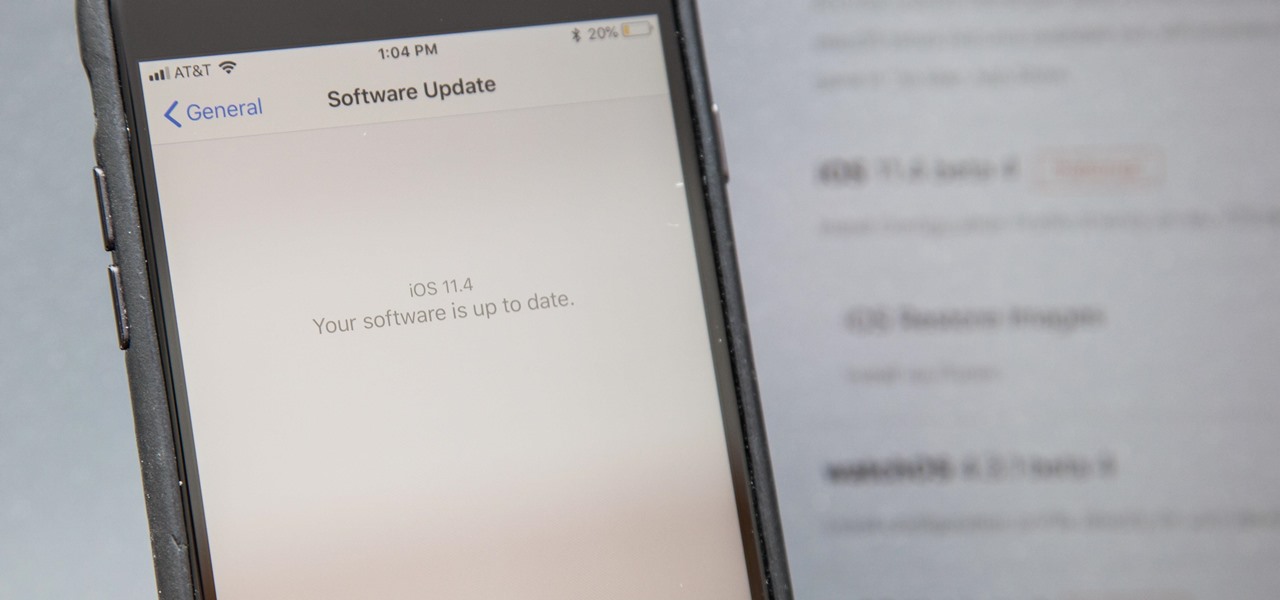
Apple is speeding things up in the iOS 11.4 development. The company released to developers the fifth beta for iOS 11.4 on Monday, May 15. Public beta testers got the update just hours later. The update comes just one week after the release of the fourth 11.4 beta, which introduced minor bug fixes and security patches to iPhone running the software. This beta version doesn't seem any different.

Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.

While VR promises to take gamers to another world, AR has the potential to bring the game elements into your own neighborhood or home.

This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.

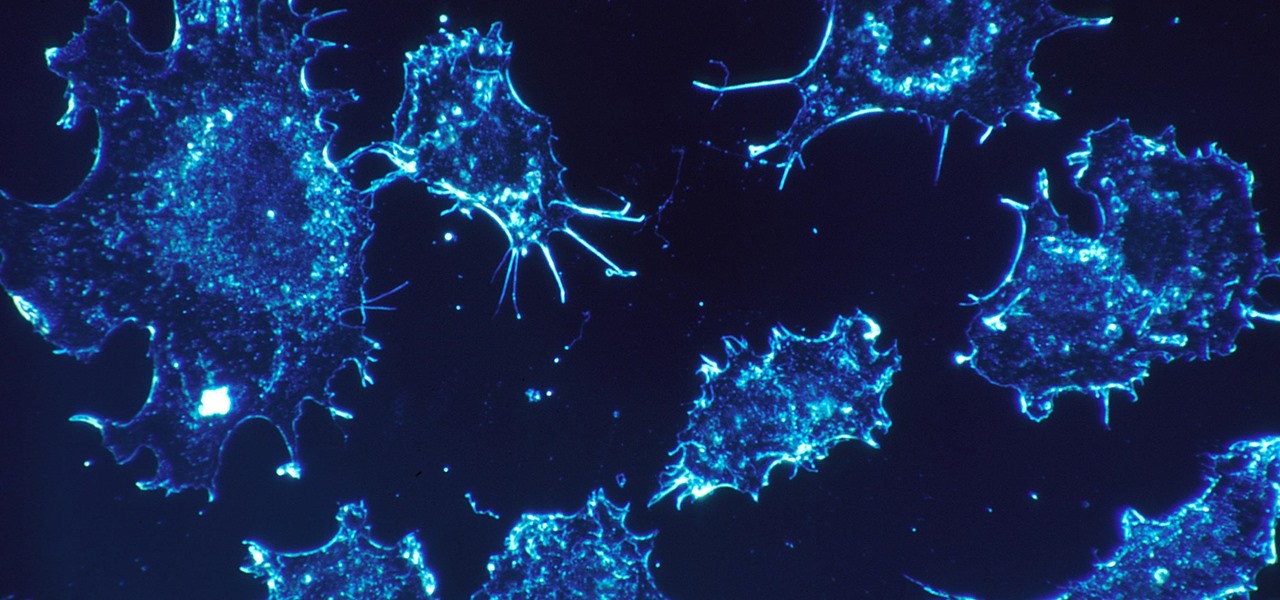
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

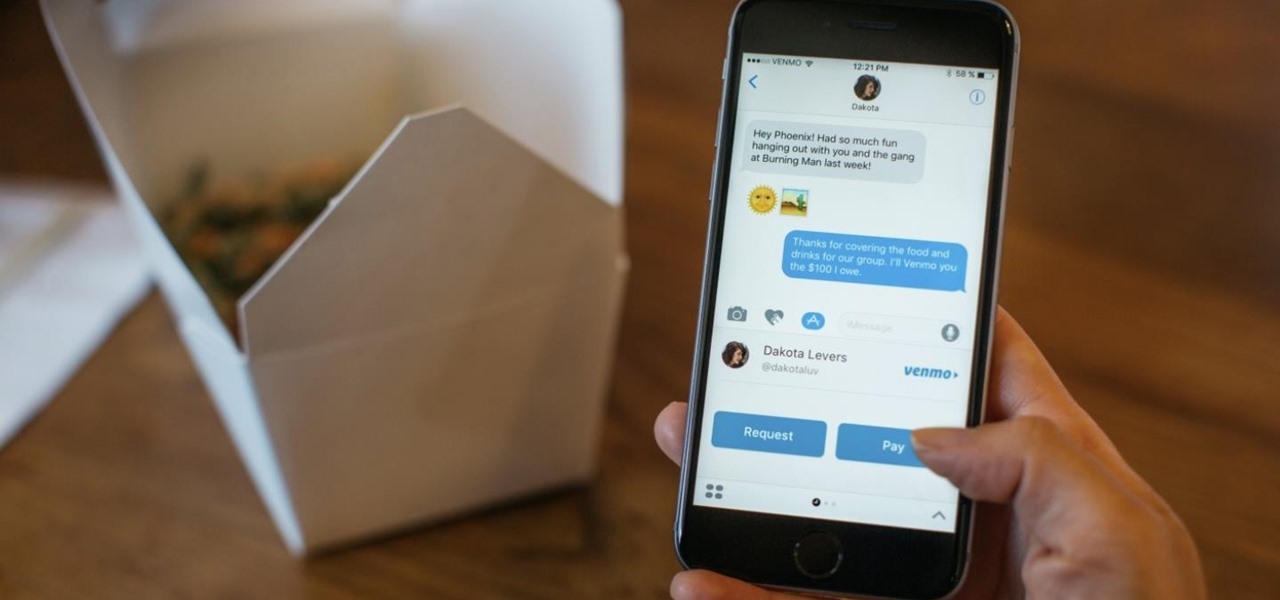
For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

It's not the bacteria itself that takes lives and limbs during invasive flesh-eating bacteria infections. It's the toxins secreted by the group A Streptococcus bacteria invading the body that causes the most damage.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

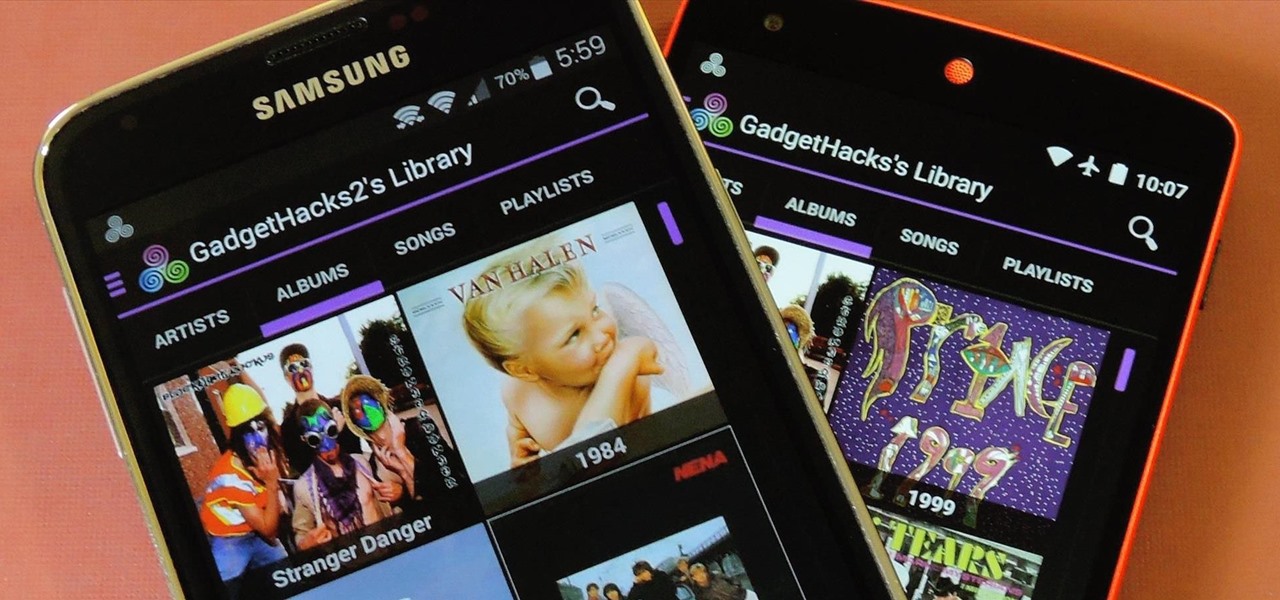
If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

Apple announced support for mobile driver's licenses and state identification cards in Apple Wallet back in 2021, and Arizona was the first state to jump on board in 2022. Fast forward to now, and only eight states let you add a driver's license or state ID to Apple Wallet on your iPhone and Apple Watch. It has been a slow rollout, but more states are coming or are at least showing interest.

Cloud computing has come a long way since the days of simple online storage and server networking. Virtually every major company in the world now relies on complex cloud computing infrastructures to reach customers, innovate products, and streamline communications. Their reliance on advanced cloud computing platforms is only going to grow in the coming years.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

Now that the Magic Leap One is out in the real world, the mystery behind the company lies not in whether it will actually ship a product, but when it will ship a consumer product. Or, does CEO Rony Abovitz steer the company in a different direction first?

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.