While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.
We might think of Zika as a mosquito-borne virus that effects developing fetuses, but, it also can be passed through sex by either a man or a woman, just like herpes and other STD viruses. New research has shown that vaginal bacteria can inhibit sexually transmitted Zika virus and Herpes Simplex Virus-2 in women.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

The ride-sharing company Lyft has managed to secure $500 million in funding, which will certainly help its ongoing competition with Uber. According to recent reports, the cab firm is currently valued somewhere between $6.9 billion and $7.5 billion, but this still pales in comparison to Uber's estimated $70 billion valuation.

As someone who grew up adamantly complaining every time my parents dared to turn on talk radio in the car, I can admit it's a bit weird that I have a love affair with podcasts. I can't help it! Even though podcasts are essentially the modern-day customizable talk radio, I choose to defend my all-out obsession with pointing out how popular they are (I mean, SNL even picked up on the trend).

Great news, zombie killers! Zombie Gunship's long overdue sequel, Zombie Gunship Survival, has finally arrived for iOS and Android devices as a soft launch available for download in the Philippines—which means that with a little tinkering, you can play the new game in any country.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.

Can't stand seeing your Facebook news feed full of peoples' good news and awesome accomplishments? Those oversharing friends are, in a sense, hampering their great news simply by sharing it. If you hold back and keep your accomplishments from friends, you might find even more success than if you'd shared with your support network.

Over the past few years, indie game developers have gathered together to release their products in the widely popular Humble Indie Bundle, a collection that gamers can purchase for whatever price they want. It's a win-win for both. Developers get more exposure for their games, and customers get tons of games for whatever they could afford. Heck, charities even get a little piece of the pie.

There's nothing worse than holding an ice cold brewski on a hot summer day and having no way to open it. If you're a Bud fan, you'll have no problem opening the bottle because most mass-market beers have twist-off caps. But if you have a taste for finer, more expensive brews, you'll more than likely run into the pry-off caps. Pry-offs are used mainly because companies believe it provides a better seal against one of beer's greatest enemies—oxygen. Plus it's a cheaper alternative for craft bre...

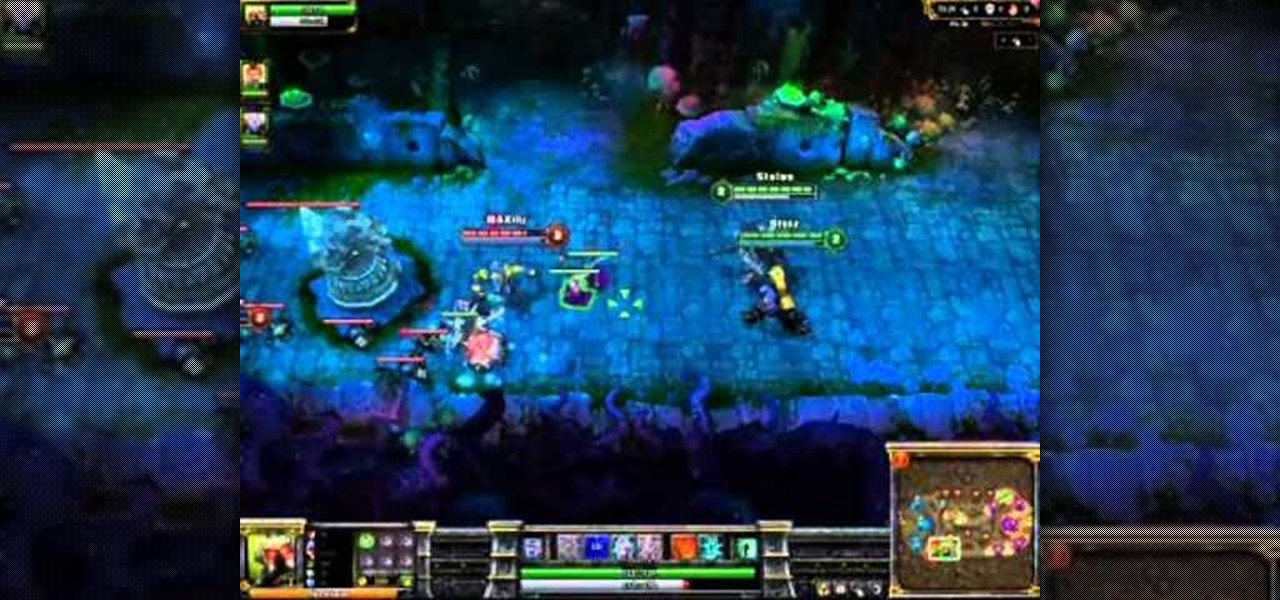
Katarina is one of the champions you can use in League of Legends, being able to both deal out damage and handle taking it herself. Here's a quick overview of what she can do, and the best way to incorporate this champion into a team game on the Fields of Justice.

Malzahar's strength is being able to damage over time. With his silence ability, he is also good at harassing the other team. Here's a video which explains what Malzahar can do as a champion, and then a demonstration of him in action on the Fields of Justice.

Laning is one of the more important phases during a battle on the Fields of Justice. This tutorial shows you the best way to use Nasus when you're trying to take or hold your lane. Make sure you choose the right abilities and items to make Nasus more than able to hold his own during your next game.

It can sometimes be difficult to win a solo queue game in League of Legends when paired with players you don't know. Here are a few tips and hints when you pick your champion in a way to compliment what your teammates are playing.

Learn intermediate Aikido techniques for defending yourself against kicks in this free Aikido training video series featuring 4th degree black belt Gary Boaz.

Learn how to defend yourself against someone who pushes you in the chest using the Aikido techniques in these Aikido training videos.

Aikido employs blocks, atemi, wrist locks, and principles of motion that allow you to defend a mid level punch or Mune Tsuki and gain control of your opponent. Learn intermediate Aikido techniques for avoiding and controlling an opponent's mid level punches in this free Aikido training video series featuring 4th degree black belt Gary Boaz.

In this video series, our expert Tres Tew will teach you about the histoy and different types of katana swords. Tres will then show you how to handle and wear the katan properly before teaching you how to block, strike, and defend with a katana.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

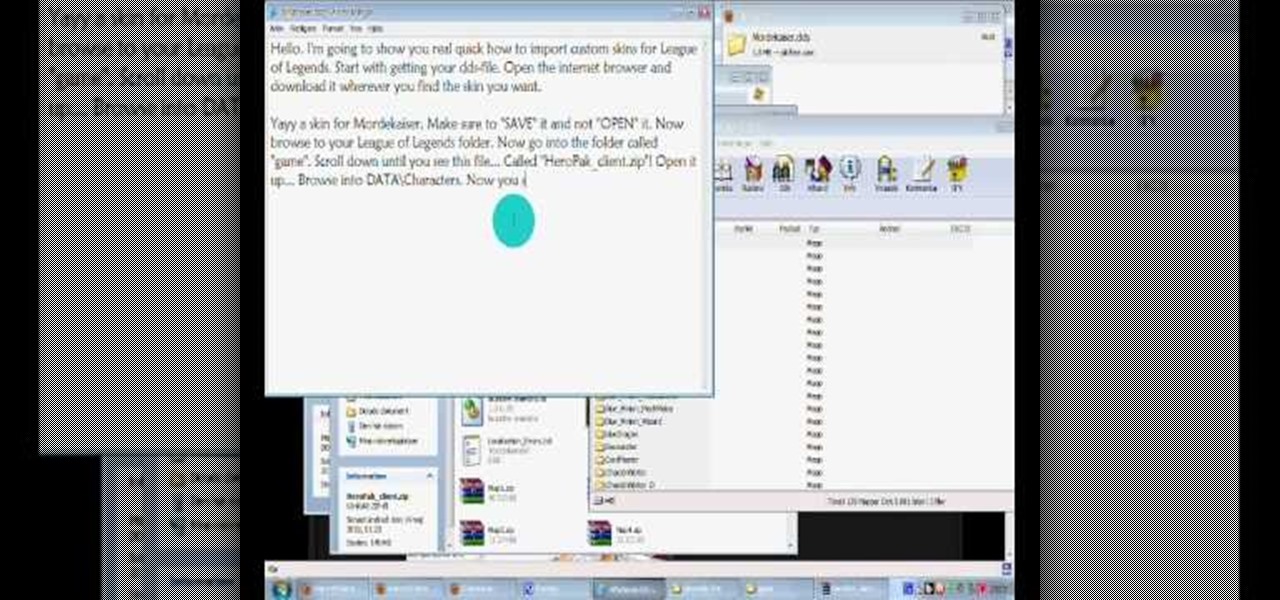
Give your League of Legends champion a new look! Alter the .dds files in the game directory so you can import custom skins. This video walks you through the process for obtaining and installing custom skins. Be aware that this will only change the way champions appear to you.

Getting someone in a wrist lock is sometimes the best way to defend yourself. See how to do the basic Aikido technique Kotegaeshi in this free Aikido training video series featuring 5th degree black belt and US Martial Arts Hall of Fame Inductee Fred Mastison Sensei.

Learn how to defend against headlocks, sucker punches, bear hugs, kicks, and more in this free training video series on mixed martial arts and standing self defense.

Practical self defense, MMA style! Defend against headlocks, mounts, grappling, choke holds, and more in this free video on mixed martial arts and self defense.

Joe Andrews will teach you how to play a hand of hearts, how to manage your spades, and how to defend against another player shooting the moon.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

With Huawei's recent emergence as the second largest OEM in the world, the company was poised to finally make a big push into the US market. Instead, their efforts were derailed by an unlikely foe, the US government. As a result, American customers will miss out on the newly-released Huawei P20.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

The year is 2018. You just received your own Magic Leap One: Creator Edition. What now? Rewinding back to today, we know of one specific app that will be available for Magic Leap's device, along with two others that could be tagged as highly likely. Paired with Magic Leap's own experiments and demonstrations, we can get a sense of what the playground for this new toy will offer.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Not all bacteria in the eyes cause infection. A group of researchers from the National Eye Institue has shown that not only is there a population of bacteria on the eyes that reside there but they perform an important function. They help activate the immune system to get rid of bad, potentially infection-causing — pathogenic — bacteria there.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?