Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

Close talkers suck. While having an intimate, one-on-one conversation with someone is nice, being able to see every pore on his face is not. Plus, there are the inevitable spit sprinkles that shoot out of his mouth at every interjection.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

If you're having difficulty dispatching any of the Corrupted from 2008's Prince of Persia, this helpful battle guide from IGN might be just what you need. If forewarned is forearmed, this video tutorial will arm you to the teeth with the necessary knowledge to beat each of Ahriman's four lieutenants – the Hunter, Warrior, Alchemist & Concubine.

This is a video walkthrough of the "Prologue: Financial District" level in Mirror's Edge for the Xbox 360.

This is a video walkthrough for Chapter 1: Flight (PT. 1/2) in Mirror's Edge for the Xbox 360. The game has a realistic, brightly-colored style and differs from most other first-person perspective video games in allowing for a wider range of actions—such as sliding under barriers, tumbling, wall-running, and shimmying across ledges—and greater freedom of movement, in having no HUD, and in allowing the legs, arms, and torso of the character to be visible on-screen.

This is a video walkthrough for Chapter 2: Jackknife (PT. 1/2) in Mirror's Edge for the Xbox 360. The game has a realistic, brightly-colored style and differs from most other first-person perspective video games in allowing for a wider range of actions—such as sliding under barriers, tumbling, wall-running, and shimmying across ledges—and greater freedom of movement, in having no HUD, and in allowing the legs, arms, and torso of the character to be visible on-screen.

This is a video walkthrough for Chapter 2: Jacknife (PT. 2/2) in Mirror's Edge for the Xbox 360. The game has a realistic, brightly-colored style and differs from most other first-person perspective video games in allowing for a wider range of actions—such as sliding under barriers, tumbling, wall-running, and shimmying across ledges—and greater freedom of movement, in having no HUD, and in allowing the legs, arms, and torso of the character to be visible on-screen.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

This is the last of the Xbox 360 game Bayonetta, where it's all or nothing. In Epilogue - Requiem, you're playing a Jeanne. On verse one, you're on a motorcycle headed toward the camera. There are some enemies chasing you, so shoot them. You'll need to evade when they shoot at you. Ride in a serpentine (zig-zag) patter to avoid their shots. For more info, watch the whole gameplay.

There's only three verses to beat in this level on the Xbox 360 game Bayonetta. In Chapter 14 - Isla Del Sol, be careful, you may not be able to see Jeanne all the time. In verse one, you'll be piloting a missile. Left stick maneuvers, X and Y fire guns, A and B fire guided rockets, triggers evade. You can invert the controls on the options menu. Hold down the fire button, keep shooting your guns at all times. Save your rockets for harder enemies. For more info, watch the whole gameplay.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

It's really easy to binge-watch episode after episode, and that's exactly what Netflix wants us to do. Before you can even think twice, the next video is playing and you're stuck wallowing in the abyss of unintentionally marathon-viewing your new favorite TV show, and there's nothing you can do. Except there is something you can do — and it's as simple as disabling one little feature.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

At the beginning of regular gameplay in Grand Theft Auto 5, you play the role of Michael robbing a bank in North Yankton with his accomplices—shooting police and evading a high-speed train in the process. While you do revisit North Yankton during regular gameplay in Los Santos, it's strangely unavailable for online play.

How Get Paid for Donating Plasma. Donating blood doesn't pay, but donating plasma—the part of blood used to treat hemophiliacs and burn victims—does. See if you qualify.

When it comes to your cell phone, do you feel like you’re paying more and more for less and less? Get the upper hand with these tips. You will need:

In order to win at playing slot machines, you need to keep a few things in mind. Slot machines are not random. They are programmed to pay out at certain times, in certain amounts, and at certain intervals.

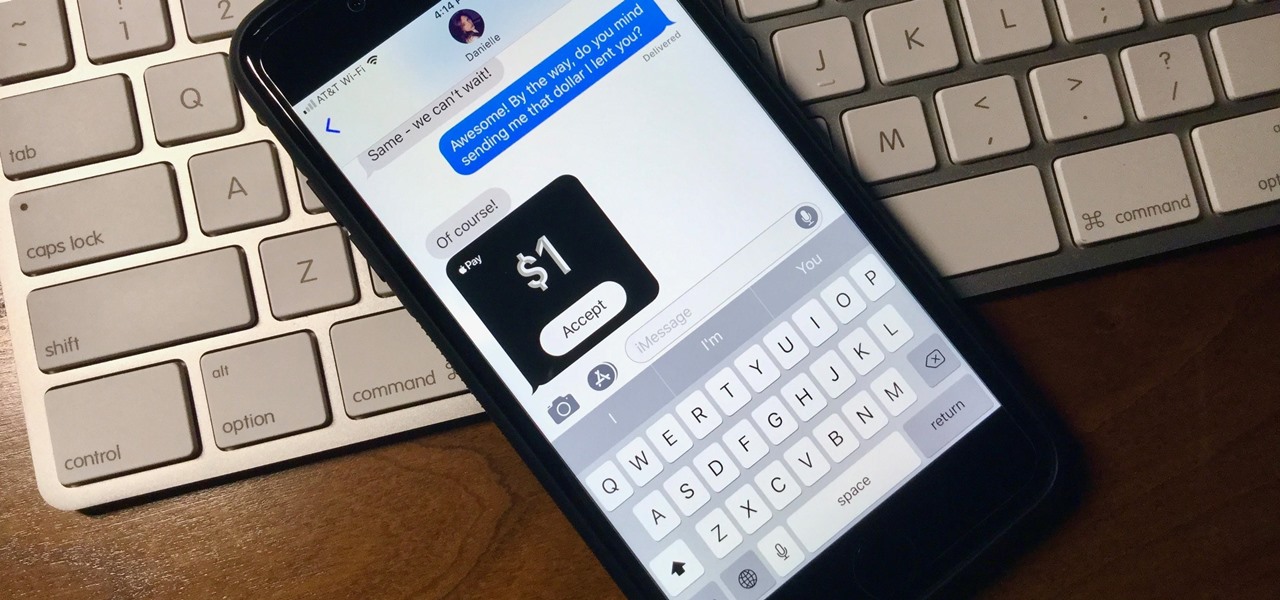
Now that Apple Pay Cash has arrived, you (hopefully) might end up getting sent some money right from inside an iMessage. If so, that money gets added to your Apple Pay Cash card in iOS 11.2, which you can use just like any other card in your digital wallet. If you're not so lucky, you can still add money to the card yourself without having to wait for a contact to send you money first.

Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

Baseball fans can now leave their wallets behind at specific stadiums throughout the country. A new upgrade by Appetize to the foodservice and retail technology used at ballparks means you can now use Apple Pay to make purchases at 5 Major League Baseball stadiums.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

Your job is to defeat Sapientia in this fight on the Xbox 360 game Bayonetta. In Chapter 13 - The Cardinal Virtue of Prudence, attack the red sphere over Sapientia's head. This fight starts with Bayonetta on the ocean, on a surfboard-like object. Sapientia will use two attacks. The first attack starts with his fin sticking out of the water, like a shark. He will then jump into the air and dive at you. Just keep moving in a straight line to avoid this attack. For the second attack the camera w...

You don't need flying broomsticks or magic balls to play this version of the game – it's tailor-made for muggles like us.

Ilyce Glink with ExpertRealEstateTips tells us about how often home owners ask her "How much should I pay a contractor before he or she starts the job?". The one who will be answering this question is Line Epstein, Vice President of Baker Construction Group. "You should never pay your contractor in full before the entire job is completed" -he says. "Not that he's going to run off with your money, but you want to keep some incentive to get the job done right. You should give a deposit of 5 to ...

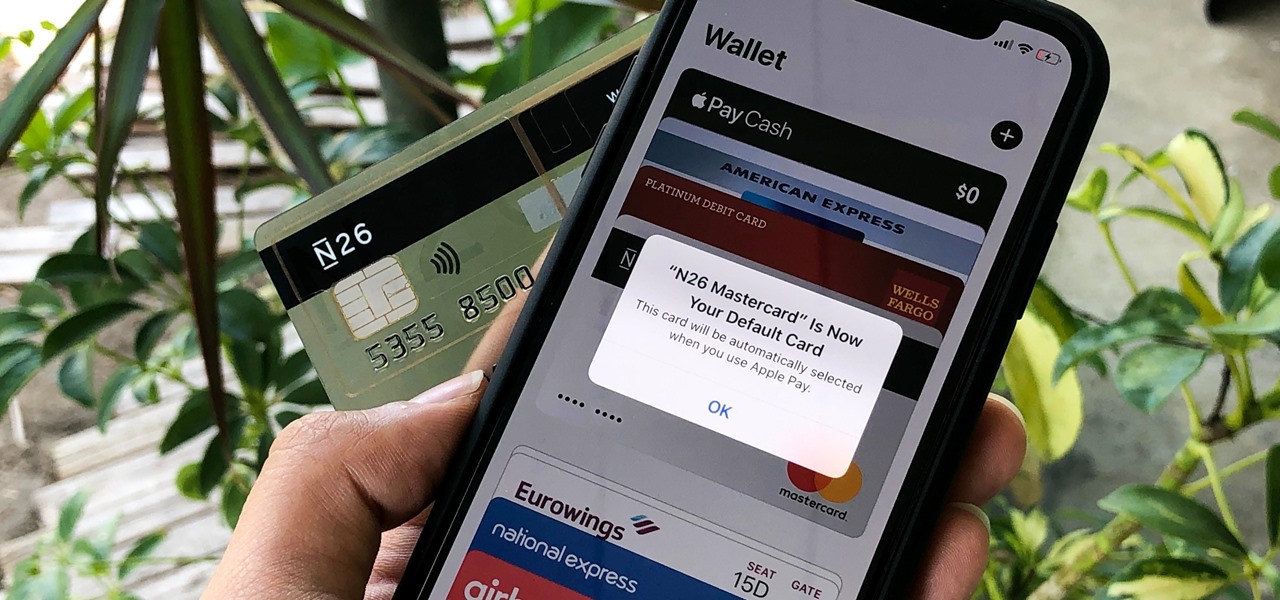
Using Apple Pay in stores to make purchases is as easy as holding your iPhone near the NFC reader and authenticating with Face ID or Touch ID. That method uses the primary payment card in Apple Wallet automatically, and your primary card may change from week to week based on your spending, so you'll probably need to change it periodically.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

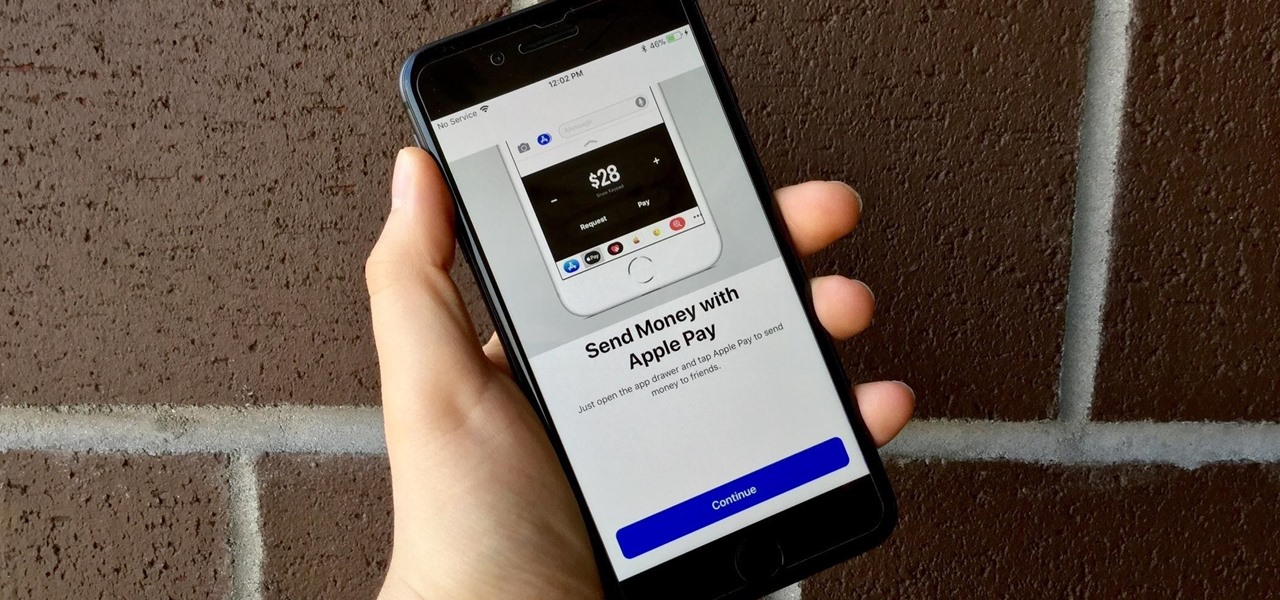
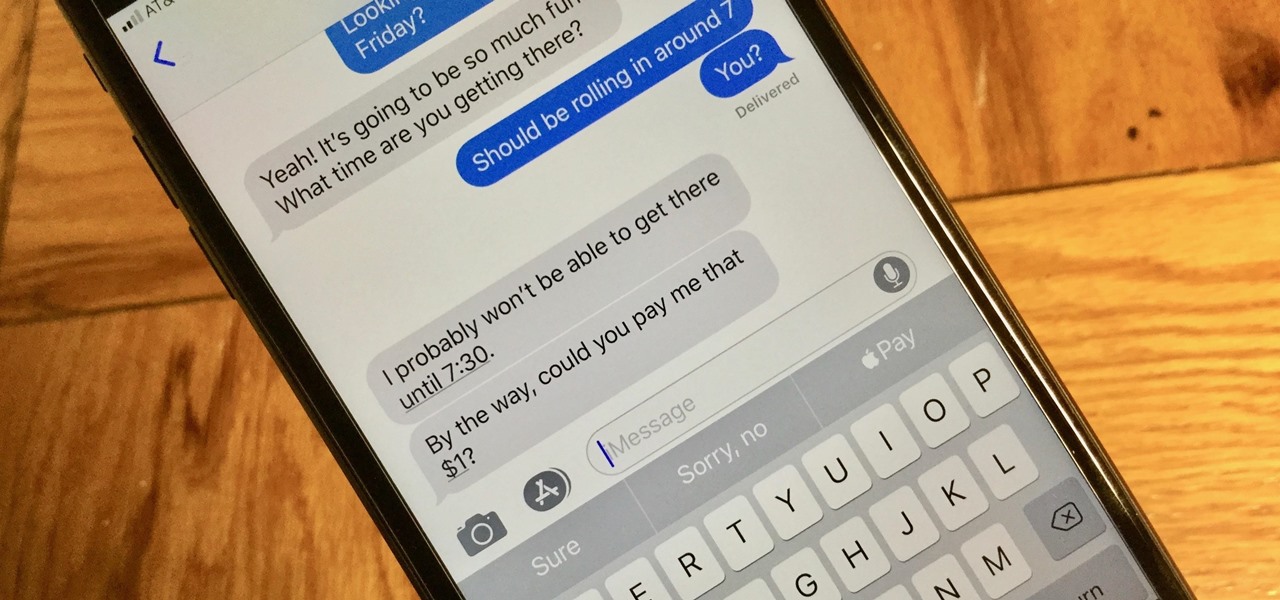
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

What happens when somebody sends you Apple Pay Cash inside of an iMessage? Do you have to add it to your Apple Pay Cash card on your iPhone manually or does it miraculously appear there automatically?