Sometimes, you just don't want to hit the Power button to turn your screen off. In the current age of touchscreens, you've got to wonder why we even have physical keys anymore.

My favorite type of video game is first-person shooters, and the one that started it all for me was GoldenEye 007. There was just something about the controls, fast-paced action, and free-roaming environment that got me hooked.

The 8-bit NES may have ruled the late-eighties, but the SNES took over the early-nineties with its 16-bit graphics and 3D-like gameplay on titles like Star Fox and Dirt Racer. When 32- and 64-bit consoles came out in the mid-nineties, the Super Nintendo took a hit, but with the rise of the Internet, created a huge emulation community in the aftermath.

Walking into a bar or crowded dinner party can be intimidating. Being surrounded by a bunch of people you're unfamiliar with or trying to impress the smokeshow at the bar is no easy task...for most of us.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.
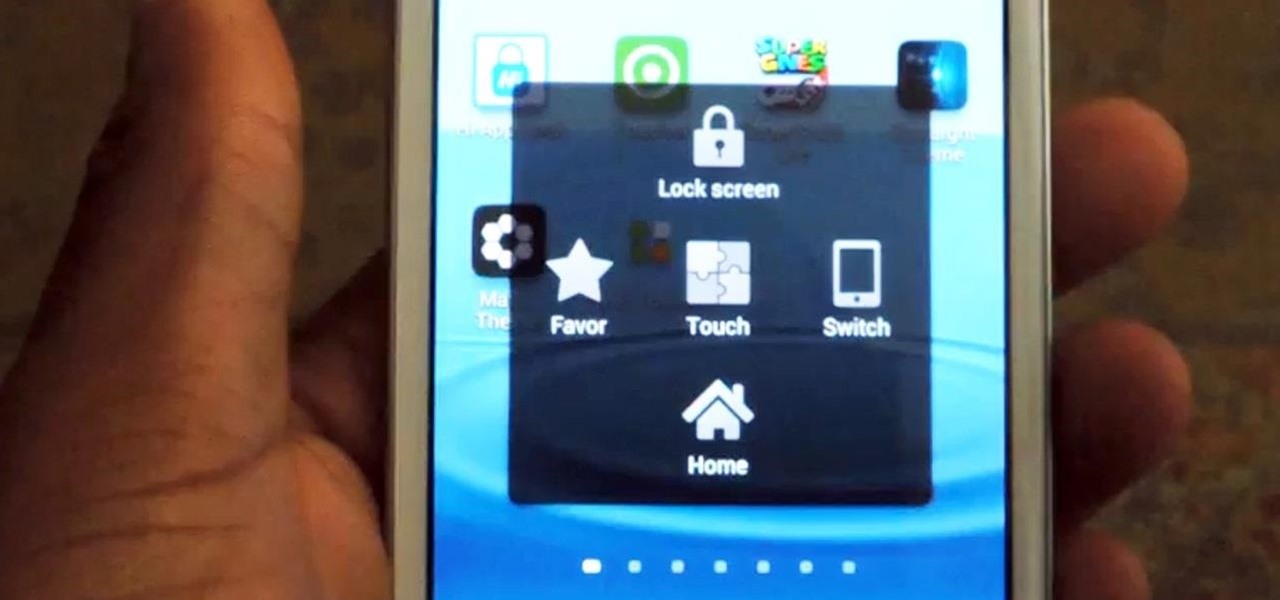
Dorothy had it right: "There's no place like home." This is especially true when it comes to using your Samsung Galaxy S3, or pretty much any other smartphone, whose most vital button is the Home key.

Particles, such as electrons, have a property called spin which can be measured at any angle, but when measured always results in one of two answers—up or down.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

Want to take vibrant photographs like this one? You won't find this filter in Instagram, and that's because it's a little more difficult than just slapping a digital filter on a solo photo. The extra RGB colors are created using a special strip device called the Harris shutter, invented by Robert Harris of Kodak.

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?

Before I really get into this article, it's important to note that you do not need a Steampunk persona (or "steamsona") in order to be a Steampunk, or wear Steampunk clothes. Some people like to pretend to be a different person when dressed up in Steampunk clothing, but that is entirely optional, and only to be done if it appeals to you. That said, even if you aren't actually acting as your character, it may still be helpful to have one in mind when putting together an outfit. Personally, I'v...

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

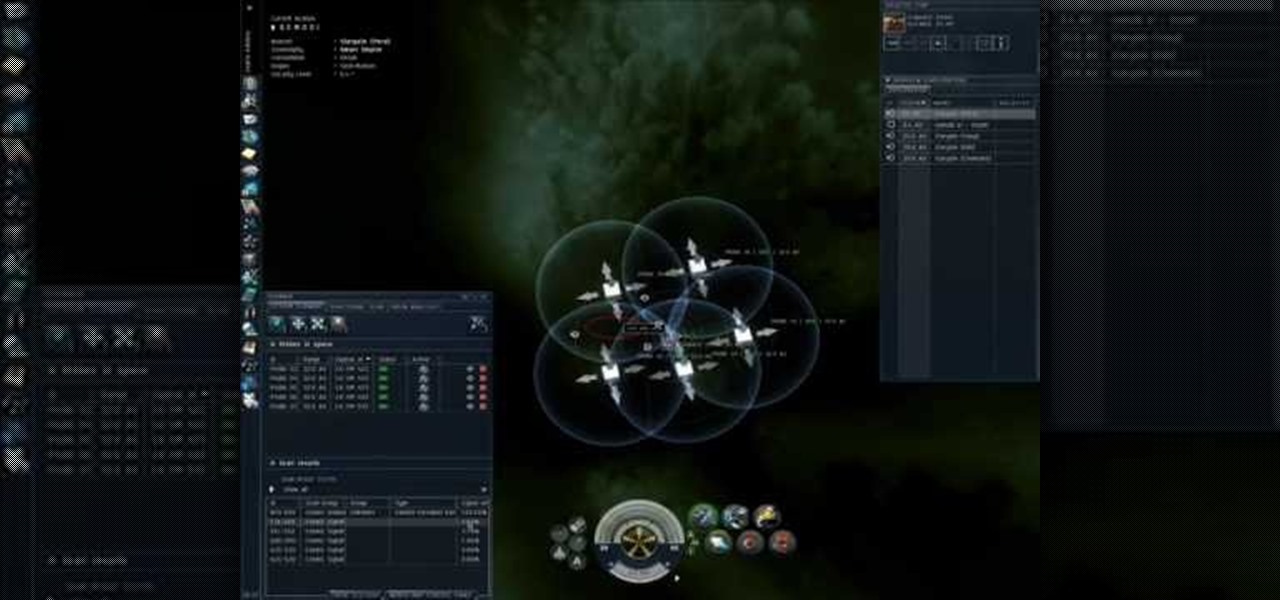
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.

It's no secret that Apple's Notes app supports attachments such as photos, videos, and web links, as well as other file types like PDFs, word documents, spreadsheets, locations on a map, and audio tracks. While images, videos, and document scans are simple to add on an iPhone or iPad, other file types aren't as easy — at least until you know how.

When Steve Jobs introduced the first iPhone, he pointed out that the biggest problem with physical keyboards on mobile phones is that they're always there, whether you need them or not. Now, 17 years later, a new company is bringing us full circle, giving us the best of both worlds: a physical keyboard for iPhone that can disappear whenever you want.

The experience of actually using the HoloLens 2 can be difficult to describe to anyone who hasn't had a chance to directly interact with the device in person and be blown away by its immersive capabilities.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

A year and change into its shift towards enterprise customers, Magic Leap has updated Lumin OS and the corresponding Lumin SDK with some key prerequisites for the business sector.

Next year, fans of Mario Kart will be able to experience the game in real life with the assistance of augmented reality.

This week, developer Niantic began rolling out a new feature called AR Mapping to Pokémon GO that has bigger implications on the realism of augmented reality in mobile gaming and beyond.

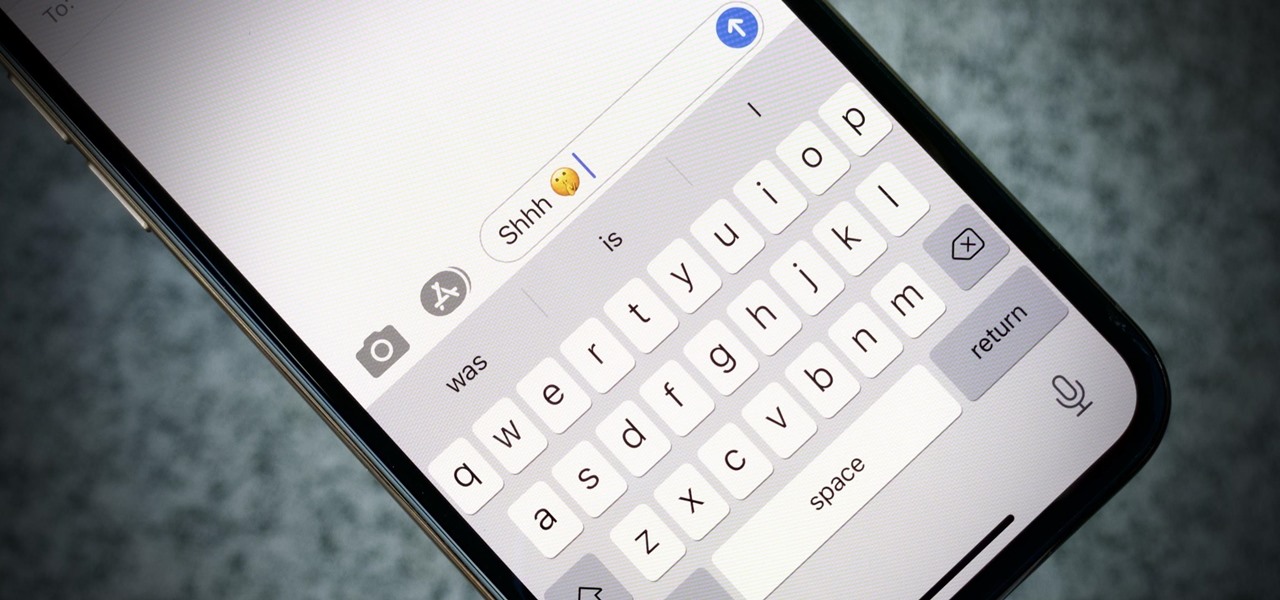
If you're in an active Messages chat, writing a large email, or have a lot of notes to jot down, you might be acutely aware of just how loud your iPhone's keyboard can sound — especially with AirPods or other headphones on. "Click, click, click, click, click, click." If the fake keyboard sounds are driving your crazy as you type, there's something you can do about it.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

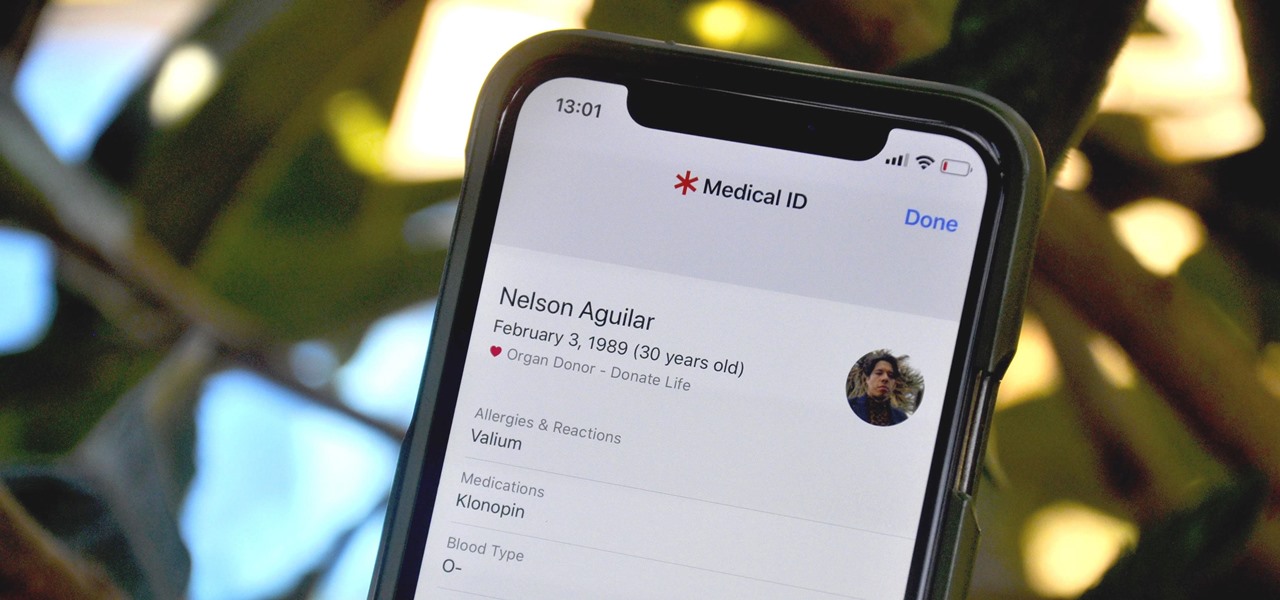
You can't predict the future, but you can prepare for it. On the off chance that you get hurt in a car accident, take a nasty tumble, fall down a cliff, have a seizure, or get struck by lightning, it's always good to carry up-to-date information about your health in case you can't speak for yourself. A physical medical ID wallet card or bracelet can provide the information, but so can your iPhone.

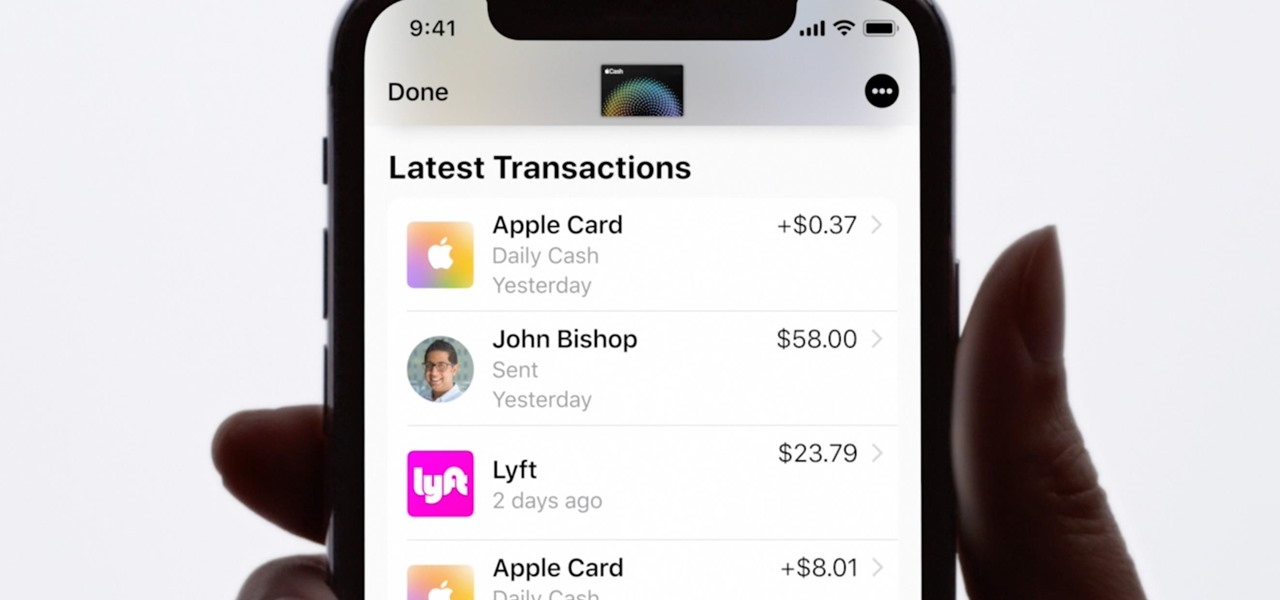
Apple Card is the iPhone OEM's big leap into the credit card market. Its low barrier to entry and ease of use make it an appealing option, especially for those who often pay for goods with Apple Pay. To get the best rewards possible, make sure you use the Apple Card at stores where you can get 3% cash back.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

If there's been one signature design element for Apple's iPhones, it was the circular Home button. It served as the "everything" button for each iPhone model until last year's iPhone X, but now, it's completely absent from the iPhone XS, XS Max, and XR. Should you be worried? Short answer: No.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

If you're looking for a new Reddit client on your iPhone, look no further than Apollo. Launched with iOS in mind, Apollo is a free app that offers an exceptional Reddit experience, but some of its excellent features — as well as some necessary ones — are hidden behind its "Pro" paywall. Are these extras worth your money?

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.