
How To: Remove Evidence from Your Computer
Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.


Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Apple released the first developer beta for iOS 13.5.5 on Monday, June 1. The update comes on the same day Apple released iOS 13.5.1 to the public, which patched the unc0ver jailbreak, and 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, in addition to other new features.

Although styluses and smartphones have existed together for years, the iPhone has always ignored the pairing. After all, "Who wants a stylus?" But ever since the Apple Pencil made its debut on iPad, the rumor mill has churned out the idea that an iPhone could one day see stylus support. That day will probably come with the release of iPhone 11, and there's a good indicator to make its case.
So far, iOS 13.4 hasn't been a disappointment. From new Memoji stickers, a refreshed Mail toolbar, and even the beginnings of controlling your car with your iPhone, Apple's latest iOS update is looking like a good one. That's why we're excited that Apple just released the third 13.4 developer beta today, one week after the release of the second one.
Apple released the first public beta for iOS 13.5.5 on Monday, June 1. The update comes just hours after Apple seeded developers their first 13.5.5 beta, as well as the public release of iOS 13.5.1, which introduced a patch for the Unc0ver jailbreak exploit. It was a big day for iOS software.

If the oil pressure gauge on your car is acting erratic, you might think that the fuel pump or filter on your car is bad. Assuming is not the way to fix your car, and in this video you'll learn how to figure out what is causing your low oil pressure, possibly saving you having to replace your filter and pump.

Holmes’ Psychiatrist Worked for Pentagon-
Donnie Hoyle shows us how to edit video frames in Photoshop. So if you suck at Photoshop check out this tutorial and learn how to edit video frames like a pro. This is extra helpful if you need to remove yourself from incriminating video camera evidence.

In this video tutorial two-parter, you'll see how to dissect the female reproductive tract of a mature laying hen for an anatomical look.

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

The best evidence that UFOs represent spacecraft from other worlds consists of grainy photographs, blurry videos, and anecdotes about things that go bump in the night. In this episode Michael Shermer shows how easy it is to fake UFO photographs, enlisting the help of children and disposable cameras to create convincing photographic evidence that even fooled experts!

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

So you need to find the p-value for your hypothesis test. To do so, employ the spreadsheet program Microsoft Excel. Using a simple formula, you can easily determine the p-value for your tests and thereby conclude strong or weak support of the null hypothesis.

This video shows the procedure to draw a face. The video shows various stages to draw a face. These include drawing an egg on the paper, dividing the egg into various parts by horizontal lines, drawing the nose and lips, drawing the eyes and ears. The video cleverly deals with issues relating to the evidence of not being a professional. The video shows the various choices that can be made by the artist in drawing the face like the pencils to use.
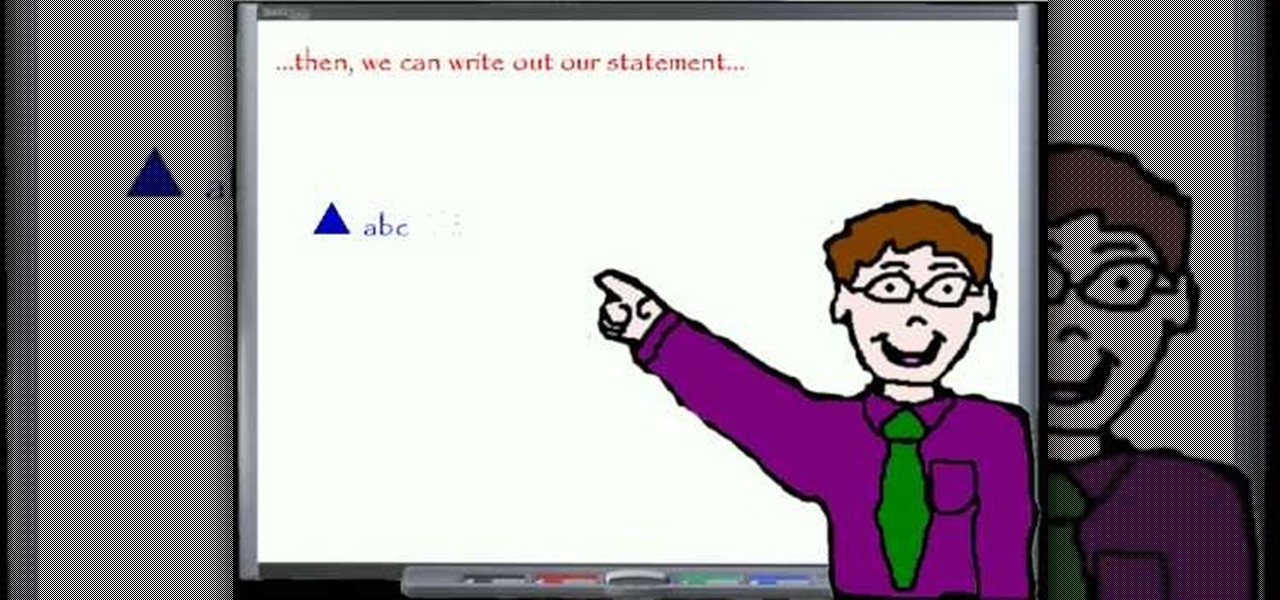
In this "Math Made Easy" geometry episode, you learn how to prove that two triangles are congruent (equal) by using the "side-side-side" evidence. By using "side-side-side" to prove that two triangles are congruent, you are stating that all the respective corresponding sides of two triangles are equal in length thus proving the triangles are congruent. The narrator in this tutorial provides you with definitions about statements, proofs, and congruency. This becomes useful when setting up a ta...

Having a bed bug infection in your car is extremely rare. However, if you suspect bed bugs in your automobile, check all of the cracks and crevices for any bed bug evidence. However, even if you don't find anything that doesn't rule out that they are there. What you can do is take your car to get fumigated. Other than that, the only thing that will absolutely kill the bugs is to let your car get very hot on a sunny, summer day.

Austin Paranormal Investigations shows how
There's a lot of evidence that suggests that life can be better down where it's wetter, and in fact, it's hotter under the water. If you'd like to move under the sea, in Minecraft at least, check out this video to learn how to build an underwater room.

Follow Crazy Chris' instructions, and crazy antics to make your own Monster Footprints. All you need is some wet ground, some gullible friends, and a hunk of Styrofoam. Chris shows us how to cut out Styrofoam monster feet, strap them to your shoes, and go tromping through the forest. He uses these fake prints to show how easy it is to make false claims about Big Foot sightings, and explains how no convincing evidence for these creatures has ever been put forward.

Does dentistry sound of interest to you? If you don’t mind spending the day in other peoples’ mouths, dentistry might just be the career for you. In this video, learn what steps need to be taken to break into the field of dentistry.

Having trouble staying organized? Need some tips on cleaning our your garage? How about getting rid of evidence? The DIY's Guys are here to help. In this episode see what you can do with dryer sheets besides get rid of static cling. Keep shoes smelling fresh, the garbage smell under control and the couch scented with laundry dryer sheets.

Do your roommates constantly steal your toothpaste? Give them a surprise - by filling the tube halfway with toothpaste (you can add food coloring to make the evidence more clear), some baking soda and vinegar in a small ziplock bag, when they try to use it the next time, the contents will be blown out onto their hands! Use this as inspiration for one of your April Fools Day pranks!

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

The main complaint for this 1999 Jeep Cherokee, 4.0L, is that the Low Coolant Light keeps flashing on and that it keeps needing coolant. Nothing seems to be leaking on the ground, so where's the leak going? After doing the normal pressure test to spot the leak, and the combustion gas leak, and the overnight test, nothing seemed to work. The coolant leak could not be identified. So, it must be the cylinder head, right? But you need evidence of that first. Watch and learn how to prove your theo...

In this tutorial, we learn how to get a Canadian Permanent Resident card. The residence card will identify you and your name as a resident of Canada. If you do not have a card when entering Canada, you have to obtain a new PR card within 30 days and have a new Canadian address. If you need to replace or renew your PR card, you must file an application as soon as you lose it. This information will need personal information and residency information. The fee is 50 Canadian dollars. If you need ...

In this video tutorial, viewers learn how to write a document-based question essay. Data base question essays evaluates student ability to formulate and support an answer of documentary evidence. Each document based question is broken into 2 parts: short answer and essay. The short answer assess student ability to analyze student documents individually. The essay assess the student ability to synthesize and create an essay based on an assortment of documents. The essay should contain an intro...
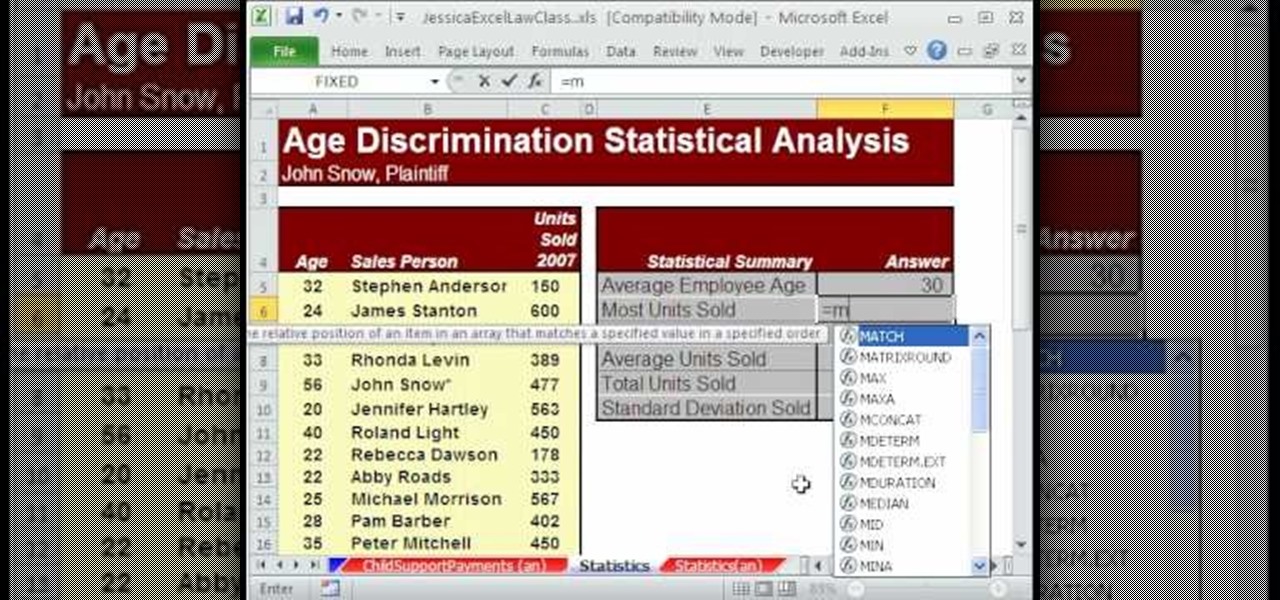
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 532nd installment in their series of digital spreadsheet magic tricks, you'll learn how to use the AVERAGE, STDEV, MAX, MIN and SUM function to add statistical data. Specifically, this video lesson discusses how to sum and average evidence in an age discrimination case.
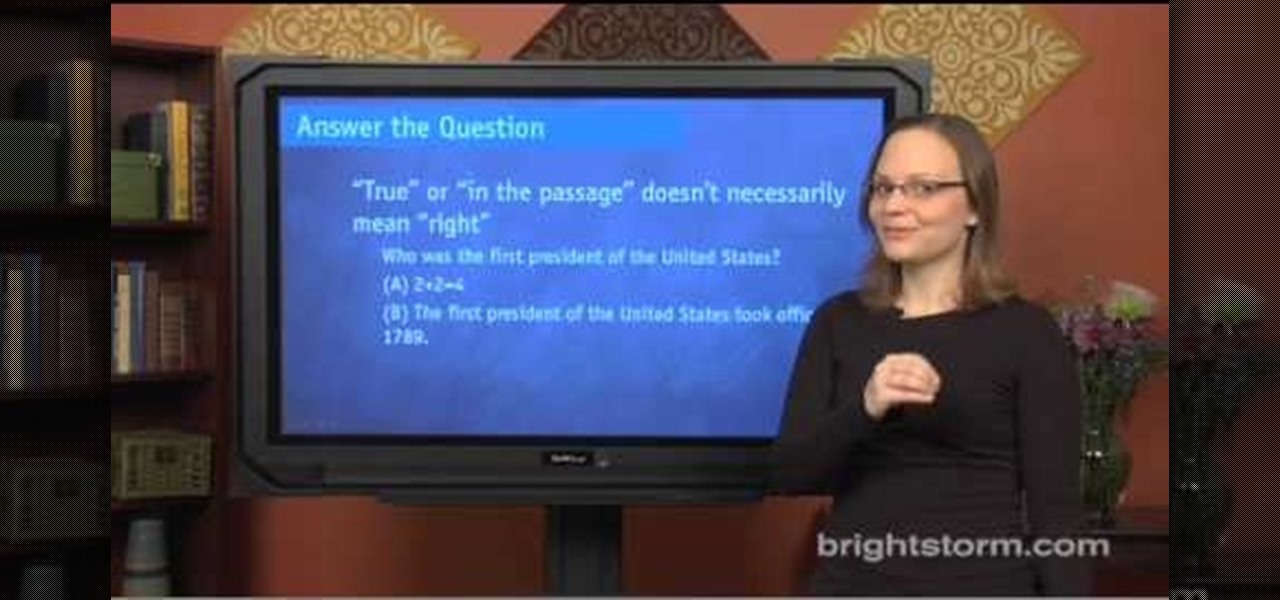
In this Education video tutorial you will learn how to avoid wrong answers on the SAT critical reading area. Five principles to keep in mind are rephrase the question and predict the answer, answer the question being asked, find evidence in the passage, extreme answers are suspicious and finally remember a little wrong is all wrong. To rephrase the question, read 2 lines before and after, ask the question in your own words and find the answer choice that best matches your prediction. Now comi...
This video describes the art of writing argumentative essays. In other words it narrates how to improve arguments of an essay. It starts with an analysis of classic examples. The speaker begins by criticizing the style of paragraph and how to improve the suggestions. He explains how to omit errors and form your arguments in commanding manner. Finally, he says how to come a conclusion by adding solid evidence. At the end of course he will show you how to transfer a old matter into a classic ex...

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Have something you want no one else to find? The best hiding places are in plain sight. Follow these steps to create a shockingly sly storage space.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.