
How To: Get a Co-Worker to Set Off a Stink Bomb!
This is just another crazy prank you can pull in the work place or at home to make time go by faster and have a little fun in the process.


This is just another crazy prank you can pull in the work place or at home to make time go by faster and have a little fun in the process.
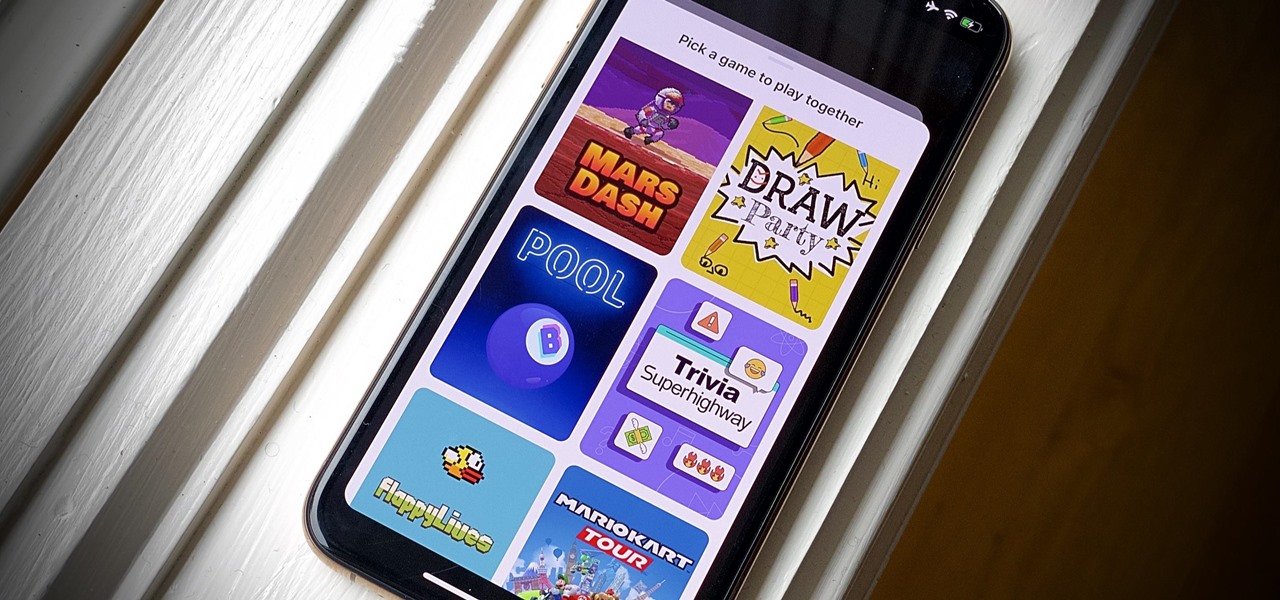
Even for those of us who enjoy spending time alone at home, at a certain point, it just gets boring. We all need social interaction, but with stay-at-home orders, that can be hard to come by. If you're feeling the itch to hang out with friends and have a good time, you should know there are plenty of free multiplayer games for iPhone and Android that will let you do just that — remotely.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Dr. Frank-N-Furter, the mad doctor played by equally strange Tim Curry, has one hell of a makeup look. Extremely darkened brows, matte black shadow extended out in an evil upturned cat eye, and two stripes of black shadow extended down the sides of the nose made his face look almost cartoonish.

Easttexas937 shows viewers how to properly use a Ouija board to get the best experience. First you will need a Ouija board and a pointer. If you want to make these two things, you should use lightweight glass and make sure you make the board properly. You have to have an open mind and good intentions when you go in to use the board. There also must be no secrets between the friends playing and you should not have a friend that is not trustworthy. This will keep evil spirits out. Always have m...

1. Shallow Bow You bump into someone in passing

Watch as Novastar and Gundamaniac demonstrate detailed wiring for a crystal focus board for Star Wars Lightsabers! Making your very own Jedi Light Saber may be a daunting task if you don't know what you're doing, but this four-part video tutorial will save the day from evil forces. To start off wiring the CF board, make sure you have your SanDisk on it already.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Thanks to "Mean Girls," we now know that Halloween is the only time you can dress like a slut and get away with it. Which means that if your concept of a witch costume still includes a crooked nose, warts, and a green face, then you're living way in the past, honey. Blast forward to the future—and the sexier side of things—by dressing up as a sexy witch this Halloween.

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Draw cartoons with realistic facial expressions to bring characters to life, capturing happy, sad, angry, evil and surprised looks. Learn to draw cartoon facial expressions from an artist in this free cartooning video series.

In this video series, watch as professional makeup artist Matt Cail teaches how to do scary clown makeup for Halloween. In this step by step makeup lesson learn how to apply the base paint, how to add triangles and fake blood, and really turn clowns into an evil thing. Take a walk down horror lane and pay tribute to IT and John Wayne Gacy Jr. thanks to the help of the experts at ExpertVillage.
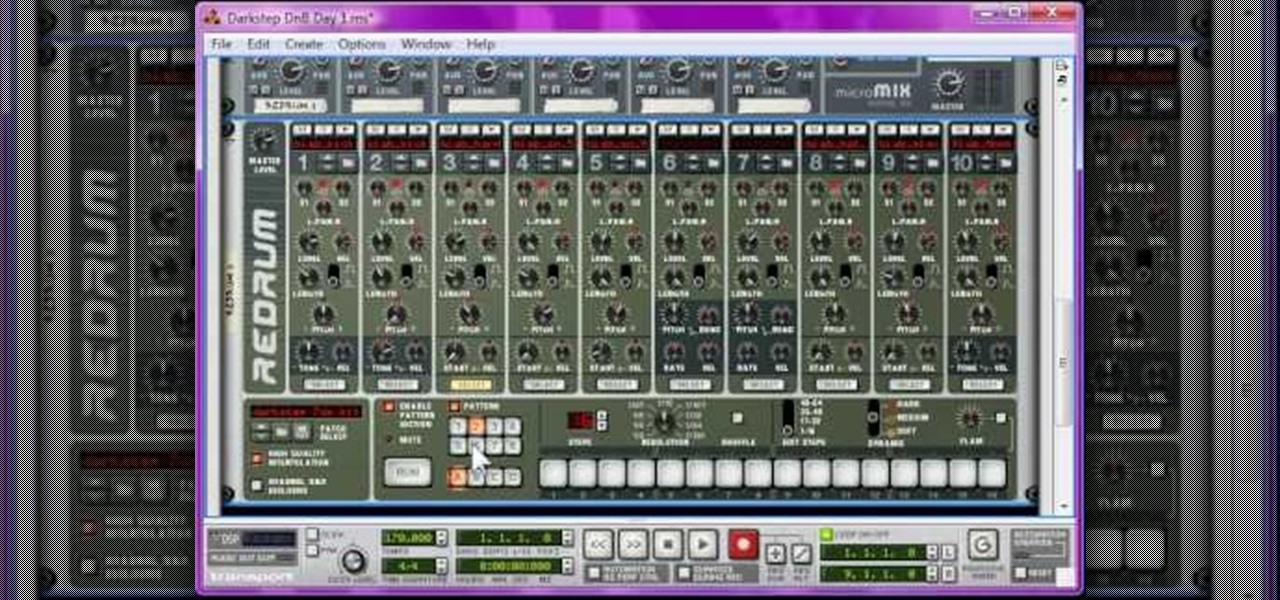
Drum and bass was originally a lighter style of jungle, but now has become dark again with the advent of dark DnB, otherwise known as darkstep, neurofunk, techstep, or darkcore. It sounds pretty evil, but you can still dance to it, and in this video you'll learn how to produce a darkstep track from start to finish using Reason 4.

In this tutorial the author shows how to find out a Cool XP Easter Egg hidden in the XP which comes by downloading the latest update of widows update. The author now opens Internet Explorer and visits the windows site. Now he quits the explorer and holds down both the Control key and alt key and right clicks on the desktop seven times. Now keeping the control key pressed, he releases the alt key and right clicks the desktop and chooses the option 'Create ShortCut'. Now he releases all the key...

Tech companies are embroiled in controversy this week. No, not the hearings on Russian interference in last year's election; in this case, it's all about the burger emoji.

Augmented reality dogs have been a big hit with developers using Apple's ARKit. RoVR hit YouTube a few days ago and people have been clamoring for it ever since. Not to mention the Good Dogs Game created by the people behind the famous We Rate Dogs Twitter.
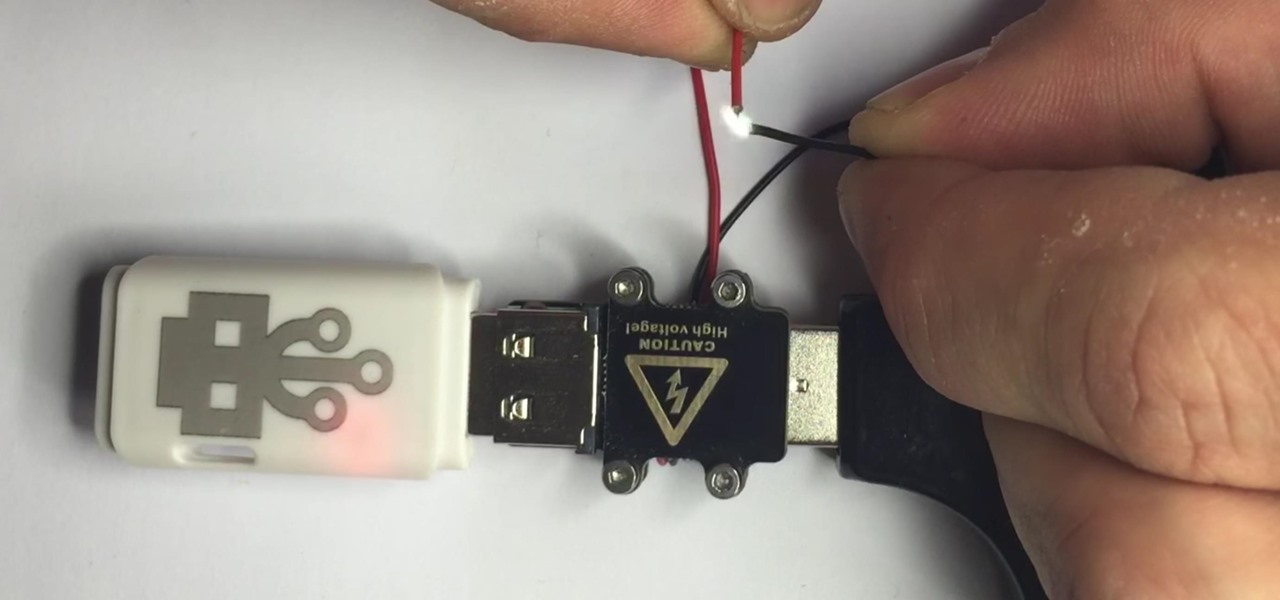
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Facebook announced at its F8 Developer's Conference on April 12th that, in addition to the VR-ready Oculus Rift we have today, it plans to bring Augmented Reality (AR) into the fold of their social machine.

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

Guardians of the Galaxy wowed moviegoers this summer with its sassy, strong team of intergalactic superheroes. From Groot, the ever-growing tree, to Rocket, the rough-around-the-edges raccoon, the film had an unending supply of unique characters—but no one stood out as much as Gamora.

Throughout history, almost every superstition dealing with evil has had something to do with left hands. In the seventeenth century, it was thought that the Devil himself baptised his followers using his left hand. Today, studies show that left-handed people are more likely to be schizophrenic, alcoholic, delinquent, dyslexic, have Crohn's disease and ulcerative colitis, and a slew of other medical problems. To top it all off, left-handed people have an average lifespan that is 9 years shorte...

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

If you ask me, one of the best things about winter weather is drinking warm beverages to beat the cold. Coffee is my favorite, but hot chocolate is a close second. Whether it's the just-add-water mix from a pack or a spicy homemade Mexican variety, there's something comforting about sipping on warm, liquid chocolate. Looks delicious, doesn't it?

If the number of apps designed to make getting out of bed easier tells us one thing, it's that people hate waking up. Whether it's because you're dreading going to work or school, or just stayed out a little too late the night before, it's almost never fun.

Stormtroopers were once the elite soldiers of the unstoppable Galactic Empire that ruled the Universe. Then little ol' Luke Skywalker came along and destroyed the Death Star, ending the evil empire forever. Since then, poor Stormtroopers all over the world have been left without work (maybe it's the economy). Out of the entire year, Stormtroopers have only a few select days of recognition, such as Star Wars Day and Halloween, where they come out of the woodwork to celebrate their once beloved...

For those of you who are wondering how to put games like Resident Evil onto your PSP, look no further. This video shows you how to play CSO, ISO, and PSX Eboots on your PSP using ChickHEN and CFW.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

You buys bananas, but you never seem to eat them because by the time you get your banana craving, they've morphed into soft gooey black apparatus of evil. If you're bananas are blackening quicker than you can scarf them down, next time, slow down the ripening process by separating them instead of leaving them in a bunch. Fresh!

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

You must ONLY conduct this experiment if you are experienced in using combustibles and understand the risk. Fire is very dangerous and can seriously burn you. Seems harmless at first, but believe me, these are bubbles turned evil. When ignited, the bubbles pop almost instantly, and all the propane is released in a huge fireball.

Usually, flying into unknown territory would mean riding into the "danger zone", but Paramount and Snapchat are taking the trip anyway with one of Summer 2020's most anticipated movie sequels.