We've got almost a full year until the next installment of Ghostbusters arrives, but in the meantime, it turns out that Sony is about to launch an augmented reality experience that will let fans use immersive computing to combat the franchise's whimsical apparitions.

For some, going to the dentist can be a terrifying experience, but a new use of augmented reality could go a long way toward making the trip feel more like it's worth the orthodontic angst.

Face ID is possibly the iPhone X's make-it-or-break-it feature. Apple is asking previous iPhone owners to put a lot of faith into their home button replacement, and so far, the results seem pretty good. That is until CNN tested the security feature with identical twins.

Prepare yourself for a trip back to the days when a Sega Genesis was your gateway to premium gaming. The mid-nineties classic, Comix Zone, has been soft-launched in the Philippines, and while it's not officially available for gamers in the states, you can install it right now with a little hackery.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

In this video I'm going to teach you 5 pranks you can get away with at school or at home On April 1st.

Salt is a miraculous substance. From the Ancient Egyptians to the Christian Bible, many cultures believe it to have mystical powers that can ward off evil, among other things.

Casting Angelina Jolie as Maleficent was a no-brainer on Disney's part. No one else could project beauty, elegance, and fear simultaneously just like the animated villain in Sleeping Beauty did. But what sets the character apart from other evil witches, or any other Disney character for that matter, is the sinister, yet gorgeous-looking horns and headdress. And with news that a Maleficent sequel is currently in the works, this will surely be a great Halloween costume this year.

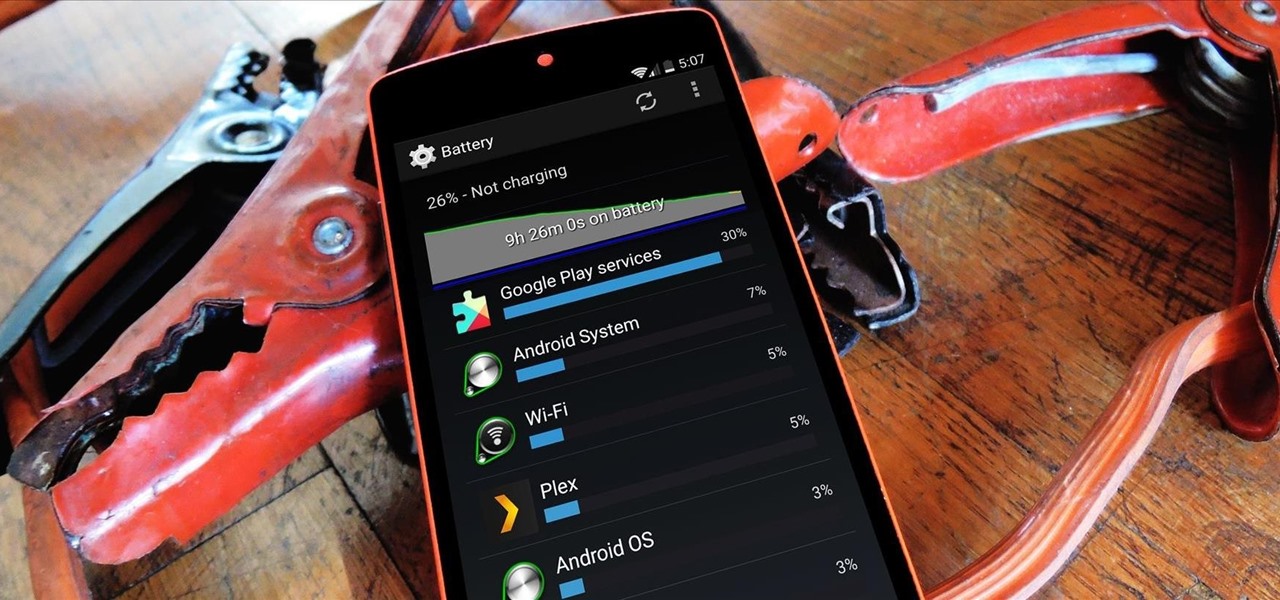
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.

So you've decided to transform your drab backyard into a Japanese Zen garden. You've made the right choice. Yes, tire swings and crab grass can slowly kill the soul. That being said, a bit of planning lies ahead. This article offers a list of How To tips, culled from the Landscape Network and other professional Japanese style landscapers, for planning an effective Japanese style landscape in your home. Step 1: Research.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

I've had a thing against bananas ever since Mario Kart; not only do I believe it's the worst weapon in the game, but it's also a very funny-looking food. Nevertheless, bananas are a great source of potassium, and I can't overlook that.

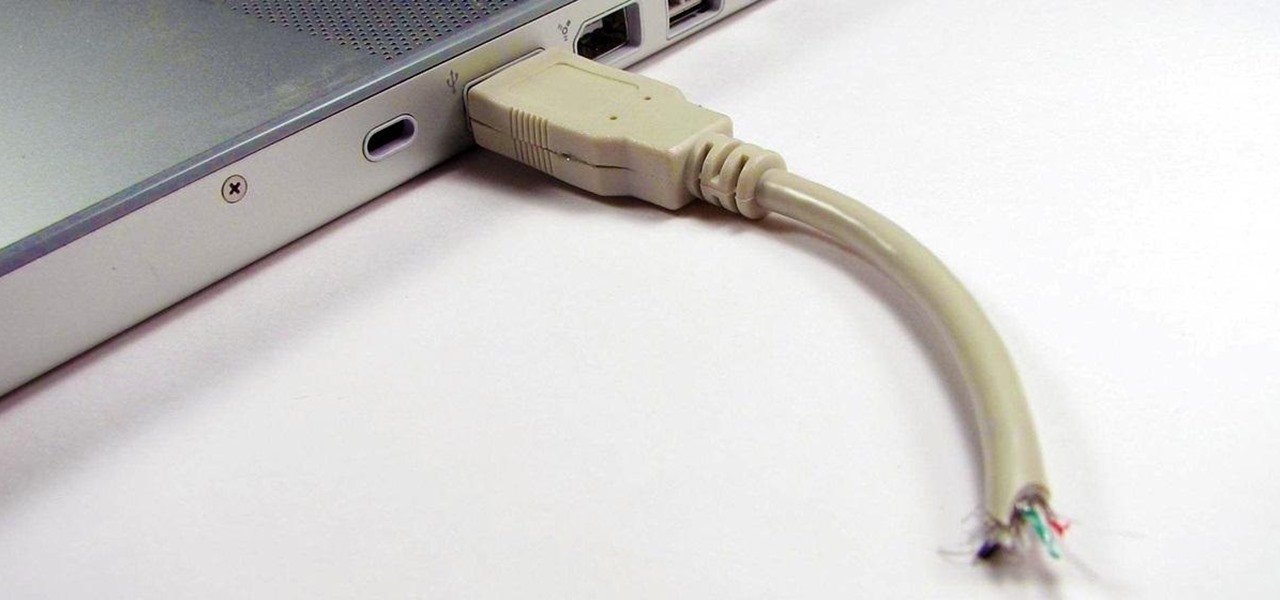
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

When Penguins Attack - TD hacks, cheats, glitches. How to hack the flash game When Penguins Attack - TD. Defend the human race against the onslaught of evil penguins. Watch this video tutorial to learn how to hack When Penguins Attack - TD with Cheat Engine (09/27/09).

With the success of Iron Man in 2008, a video game adaption quickly hit the market, so it's no surprise that when Iron Man 2 came out this year, that a video game would follow close behind. Sega released Iron Man 2 in a variety of gaming formats, including the Xbox 360, PlayStation 3, PlayStation Portable, Nintendo Wii, Nintendo DS, along with iPhone and other mobile devices. The story of the game takes place after the plot of the film, except the iPhone game, which mimics the movie's plot.

Did you just grab your copy of Splinter Cell: Conviction for the Xbox 360? Yes? Then you're probably already looking for advice on how to play the video game, and walkthroughs are the best way to learn, because you see everything, mistakes and all. See what to do and what not to do.

Learn how to play "Heartless" by Kanye West Ft. T-Pain, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

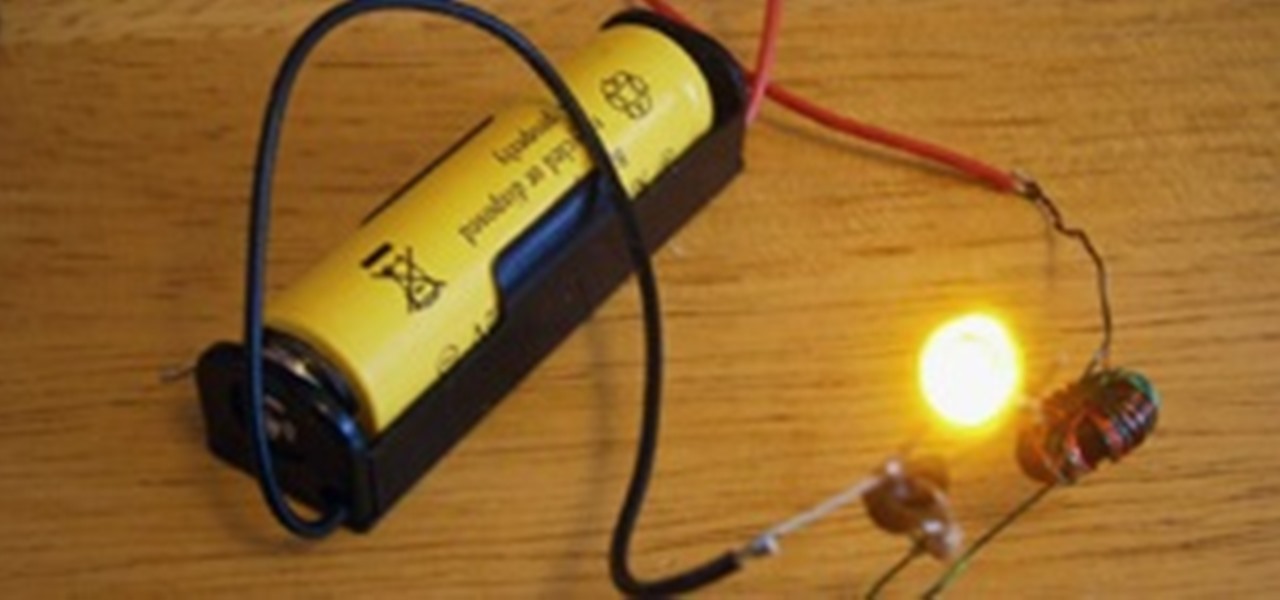
Just about every household gadget we own runs on 1.5 volt batteries of one size or another. Wouldn't it be great if you could reuse all of those dead AA, AAA, and D batteries after they've passed on? It turns out you can make a simple circuit called a "Joule Thief" to reanimate the undead flesh of your deceased batteries and create a zombie battery.

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

At long last, the magical world of Harry Potter has received a mobile game worthy of its name. Harry Potter: Wizards Unite is the game in question, and is set to touch down worldwide on June 21, 2019. For the longest time, however, the game has been available as a soft launched game for testing, and with a little tinkering, you can actually try it out right now before its official release stateside.

The era of smartglasses designed for consumers has officially begun, as shipments of North Focals began arriving at its stores this week. And the company now has plans to expand its retail footprint.

The Power Rangers universe is massive, spanning numerous shows and movies that feature different heroes — from the original dinosaur-themed Mighty Morphin Power Rangers, to Power Rangers Samurai, and so on. To tie it all in, Nexon has soft launched Power Rangers: All Stars in select countries ahead of a worldwide release. But you can try the game out right now thanks to a simple hack.

So, it's Halloween time, and you feel like playing around with some augmented reality apps? Well, you've come to the right place — if you have an iOS device.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even baby formula. Hell, there's even an entire book dedicated to the history of food swindling.

There are myriad wrong ways to cut an onion, a few right ways to cut an onion (including this one)... but only one ultimate way to dice onions, and that's what I'll be sharing with you today.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.