Nerds get a bad rap most of the time, but on Halloween, everyone wants to be one. However, not everyone knows how to geek it out without going too far. There is a limit, even for nerds, and these eight Halloween costumes are nerdy times pi.

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...
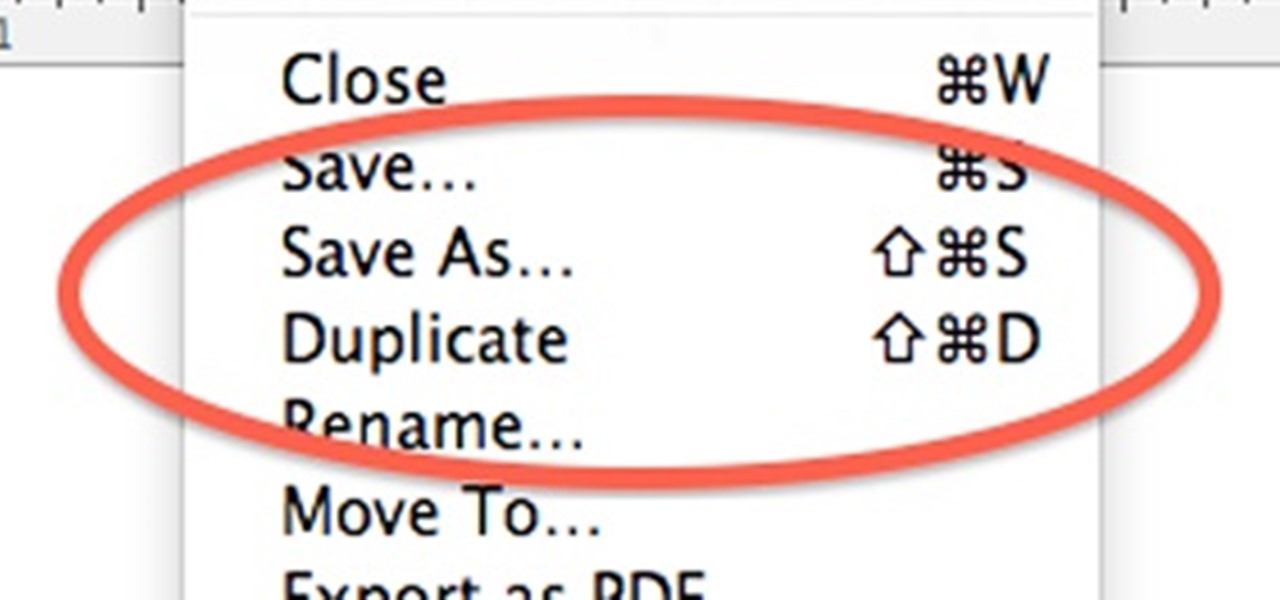
When OS X Lion (10.7) debuted last year, a lot of Apple users were dismayed that the "Save As" option had disappeared, replaced by the "Duplicate" function. Most felt that it just wasn't the same, so when Mountain Lion was released, the "Save As" option was brought back… sort of.

Are you going trick-or-treating this Halloween? Well, if so, and you're feeling a little lazy and a little evil, see how to scare the living crap out of little kids in order to get all of that Halloween candy for yourself. It's simple. Jump up and scare a bunch of children, they drop their trick-or-treat bags, you grab them and run. Easy as can be.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

The iPhone X is one of the most beautiful phones ever made, but the aesthetics stop just short of perfect due to one thing: That notch. It was a necessary evil since Apple had to incorporate a front-facing camera somewhere, plus it houses all the sensors for Face ID, but that doesn't change the fact that it looks a bit goofy.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

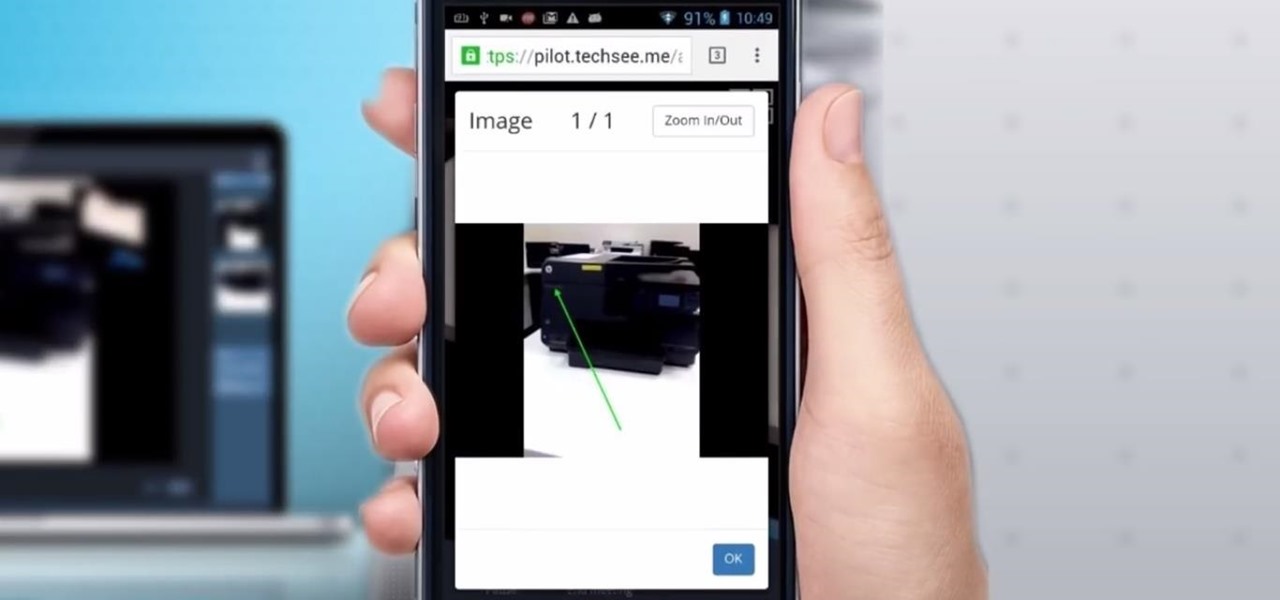
Four augmented reality companies made deals this week to grow their businesses. Two companies, TechSee and Car360, completed funding rounds, while DAQRI signed with a production partner and Decalomania landed a prime spot with a top retailer.

If you're someone who loves to read, you've probably read a book that made you want to hop into the story and live in the world that wasn't your own. Reading has a way of letting us escape into other worlds and experience things that we normally wouldn't be able to. Augmented reality is similar in that way. Which is why it makes sense that the two would be combined to create an incredible, immersive new way of reading.

We're year-round pesto eaters. We eat pesto outdoors in the summertime on a light pasta with a glass of rosé. We eat pesto in the wintertime by the fire atop a bowl of soup with a warm mug of tea. We eat pesto with scrambled eggs for breakfast, pesto-slathered sandwiches for lunch, and baked pesto chicken for dinner.

The magic of an ice cold popsicle on a hot summer's day is undeniable, whether you're a child or a kid-at-heart. Neon-colored, store-bought popsicles may have a special place in your memory, but homemade popsicles are pretty hard to beat. Here's how to create delicious frozen treats that will both delight your inner child and tickle your adult taste buds!

We can't resist a good peanut butter cup—especially when it's homemade. But it's not just the peanut butter or the chocolate that makes us pledge our undying love to these sweet treats over and over again. Nope. What really drives us wild about them is their shape. Yup: we love candy cups.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

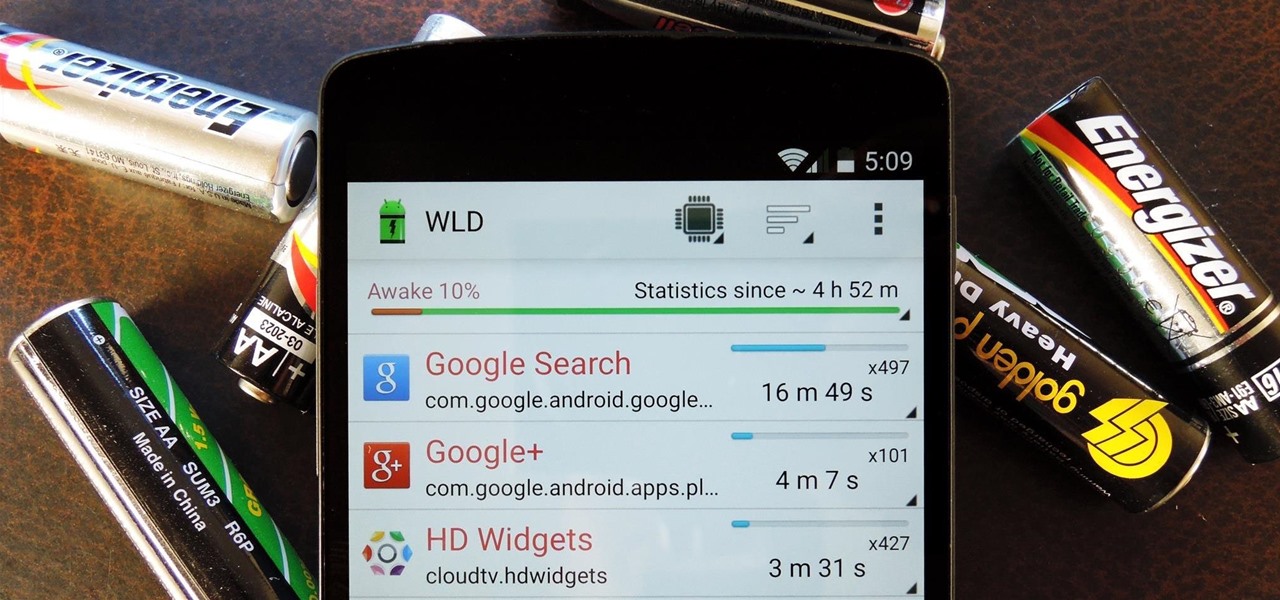
When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

I'm sure that there are plenty of people out there who have no idea what a plague doctor is/was, so I'll start with an explanation.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

I can imagine you sitting there thinking to yourself, "I've played a lot of games! I bet he won't have any that I don't know about!" Well, that's entirely possible. I'm only drawing from my own personal experience here, so you may, in fact, know of all these games.

Darth Vader is the legendary sci-fi character from the Star Wars movies. Everyone has heard of the Star Wars Trilogy, right? The older ones from the 70's? Darth Vader is the primary antagonist from those intergalactic space flicks. DragoArt has this video tutorial on how to draw Darth Vader from "Star Wars". Get more detailed instructions on the step-by-step cartoon drawing here.

This Naruto character is a very sinister and evil one: Orochimaru. At one point in time, he was considered a prodigy and was one of Konohagakure's Sannin. The Sannin is a group of three students of Hiruzen Sarutobi. The three members were a part of Team Sarutobi and they were Jiraiya, Tsunade, and Orochimaru. If you want to learn how to draw this dismal Orochimaru anime/manga character, it's really quite simple. DragoArt has this video tutorial on how to draw Orochimaru from Naruto. Get more ...

For the dedicated prankster, April Fool's Day is no joke. Nothing will stop them from coming up with the cleverest, most elaborate prank the world has ever seen. Or at least—their victim.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.