Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Silencing my phone always gives me mild anxiety; while my Android is muted, my girlfriend or boss may be trying to reach me with some urgent news or task. On the one hand, I want to enjoy some peace and quiet, but on the other, I don't want to come back to a phone with 100 missed calls and countless exclamatory texts.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

I can't begin to tell you how many times I've forgotten a special day or event. Once, I even showed up to class where everyone was turning in essays while I sat there empty-handed. Important dates sneak up on us. Especially one-time events we just can't wait for, like the release of a new movie when we count down the days, minutes, and hours.

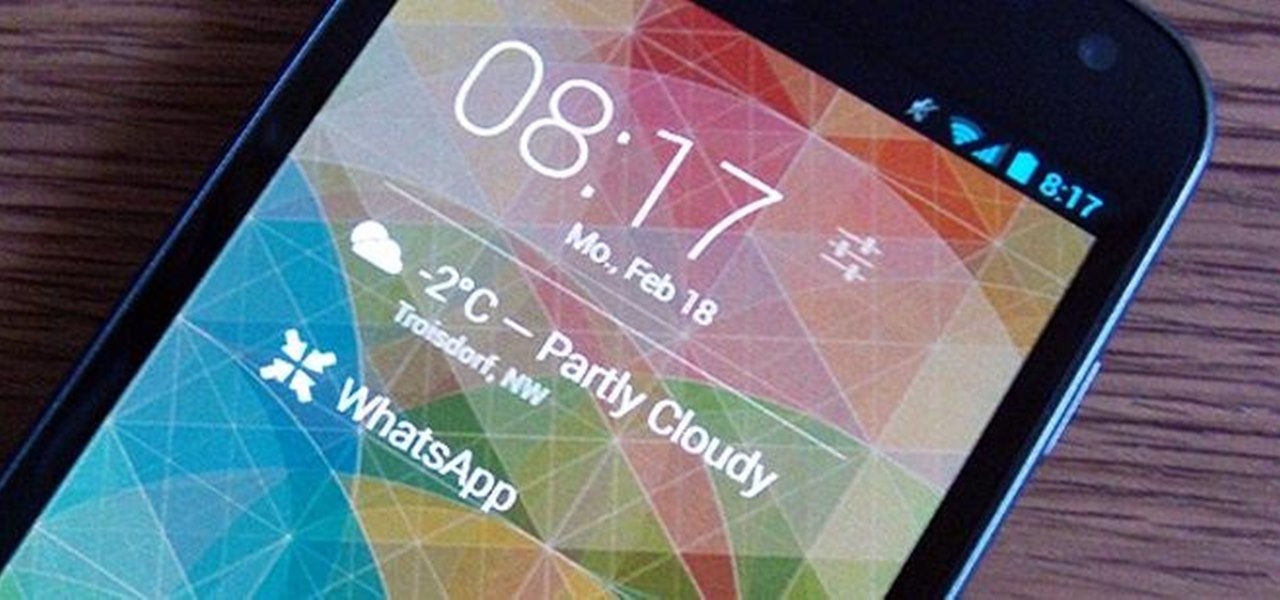
It's all about widgets. Widgets are one of the most important features on an Android phone—they can provide valuable information at a glance and are easily customizable.

There are so many things in life I wish I could've canceled without any repercussions, and I'm mostly talking about text messages.

Each & Every One of You (EEOOY) is a mock TV show pilot that teaches ordinary people how to make contemporary installation art. If these words strike fear into your heart or make you cringe with memories of seeing contemporary art and wondering what the hell it was all about, this show is for you!

This video is on how to setup the axon racing anti gravity razorback racer. it involves receiver installation, zeroing your servo with the trims and lifting the horn, programming the esc, installing the lipo, testing the unit, initial turn on.

Zooming in and out within Instagram Stories is a good way to take your videos to the next level. Whatever a next level is. Sometimes I just run out of words to describe how fun using Instagram is, so for today, I got "next level," which means whatever you want it to mean.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Even though the 88th Academy Awards have come and gone, there's a good chance you still haven't seen all the films that were nominated—or even those that won big.

Valentine's Day can seem like Singles Awareness Day if you're newly broken up, but that's all the more reason to treat yourself on this pink-and-red consumerist holiday. Whether you're happily single or bitter and bitchy, there's definitely something on this list of Anti-Valentine's Day treats to fit your mood. Remember: cake is still cake!

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

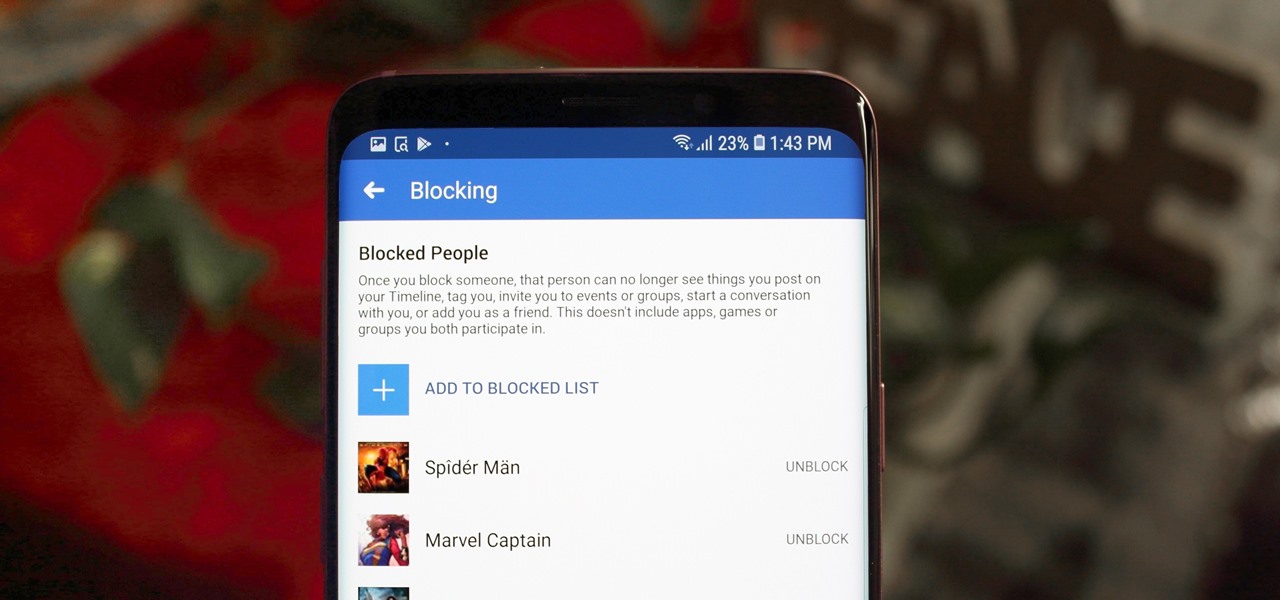
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

Tesla CEO and founder Elon Musk has repeatedly said this year all Tesla models made since October 2016 have the requisite hardware for "full self-driving" capabilities, yet the company has reportedly begun to add a second graphics processor (GPU) to its computer platform for Autopilot — without officially saying why.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

Lyft officially laid its stake in the ground to develop driverless fleets following its Friday announcement, but how fast it is catching up to ride-hailing competitor Uber's driverless initiative remains to be seen.

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

Mobile wallet Curve just released a new feature that lets you correct past mistakes. Sounds incredible, right? Unfortunately, the mistakes you can erase aren't things like forgetting to do an assignment in school, screwing up a job interview, or, well, your ex. However, you can switch the card you want to use to pay even after you've paid with Curve, and that's still pretty cool.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

The big Waymo versus Uber trial isn't scheduled until May, but the heat between Uber and Waymo is rising fast; Waymo wants Uber's driverless trials shut down by a court injunction, unless ex-Google employee Anthony Levandowski testifies in court.

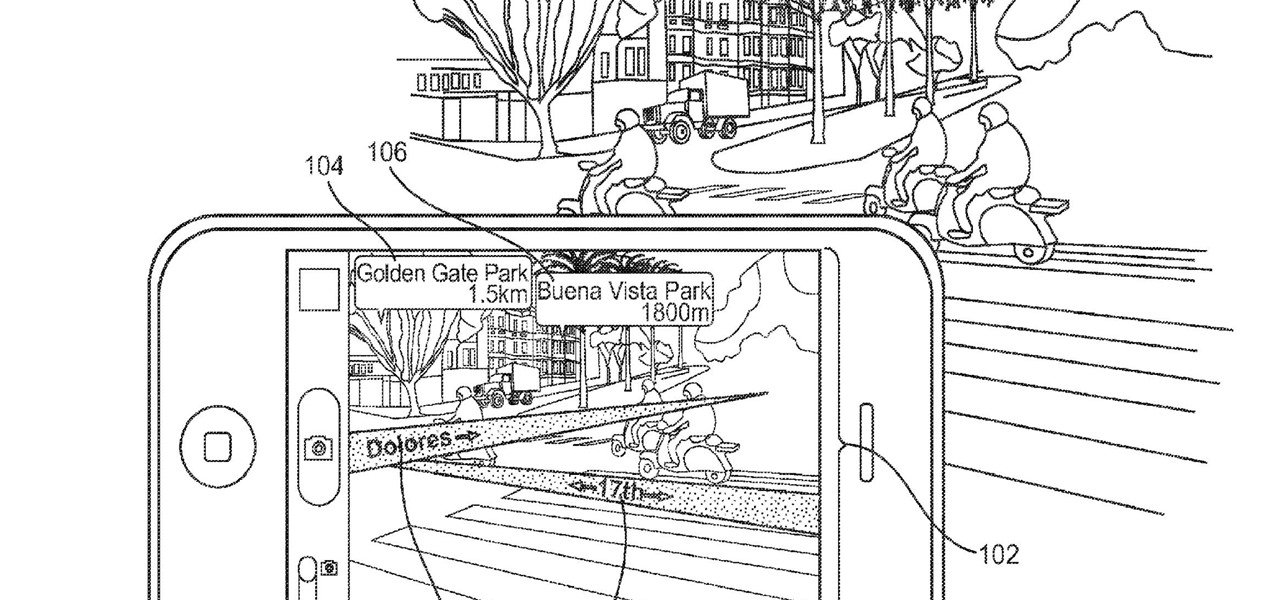
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

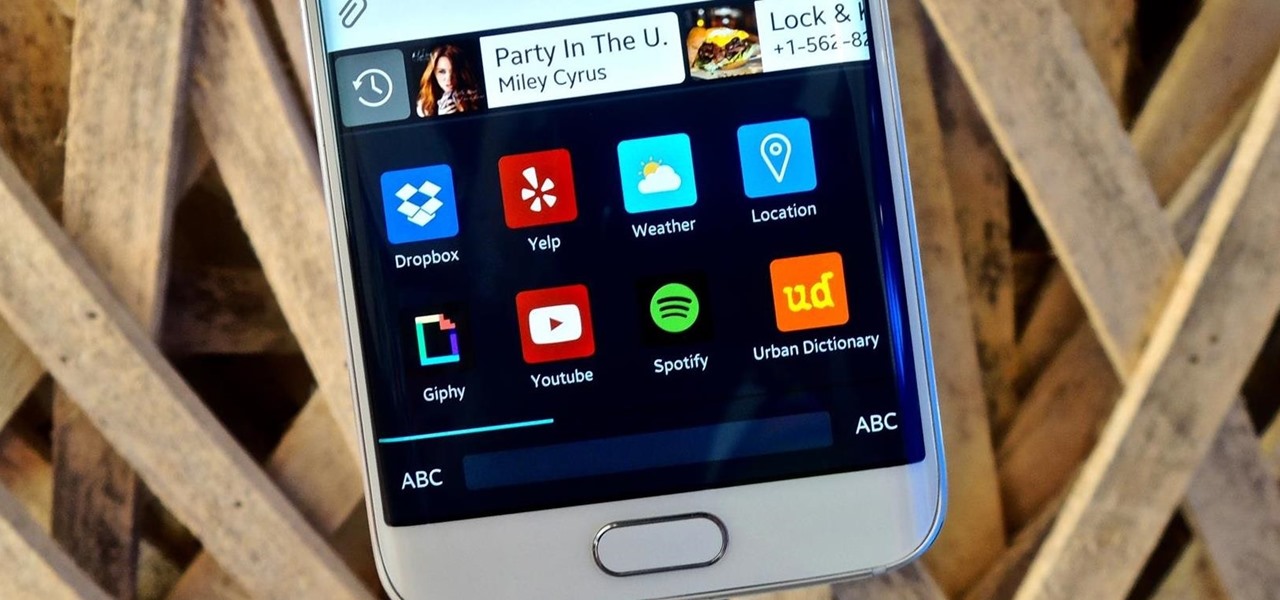
In addition to sharing emojis and GIFs, most of us also probably share various types of links through email or text, whether it be for a Google Maps location, a bar or restaurant on Yelp, or an awesome song on Spotify.

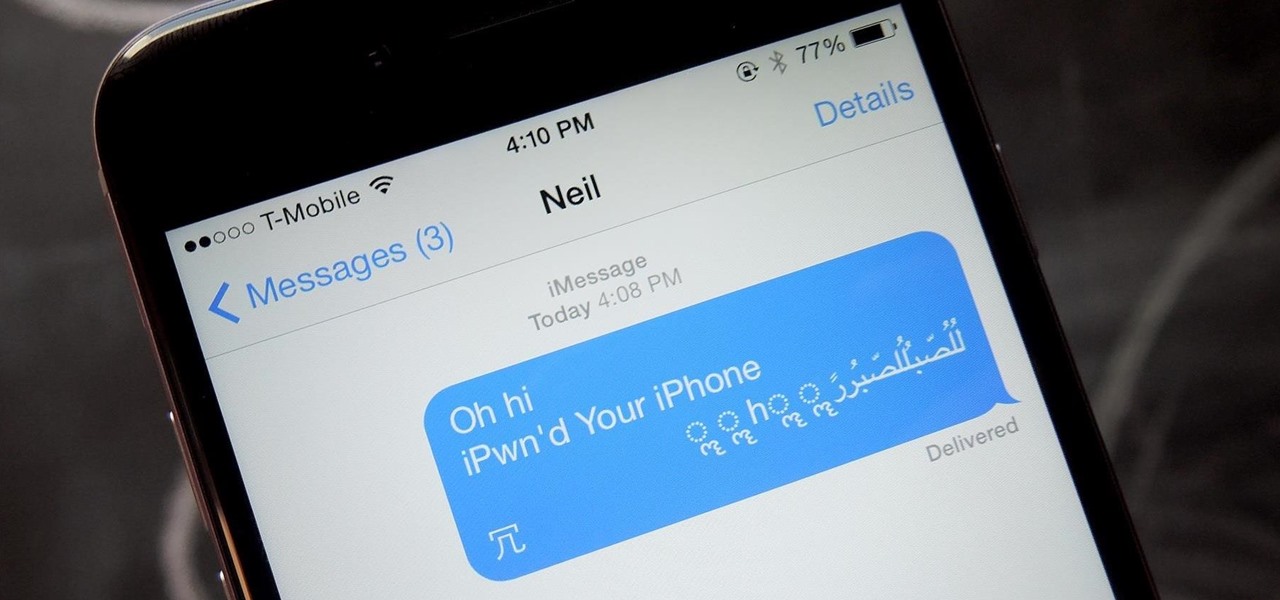
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

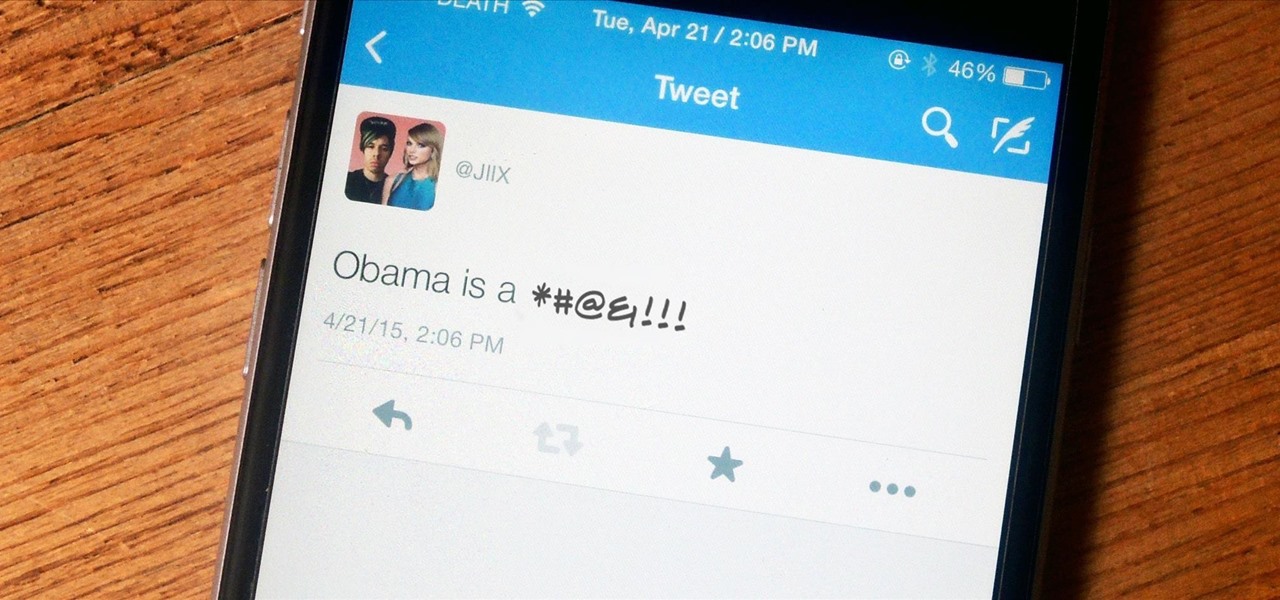
One tweet can get your fired from your job. At least, in the cases of Gilbert Gottfried, Rashard Mendenhall, Ozzie Guillen, and Mike Bacsik, who were all either fired or forced to resign from their jobs after posting regrettable tweets online.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

Unless you're waiting in line for your iPhone 6 or iPhone 6 Plus, it's a sure bet that you'll be sitting by at home for your new device to get delivered today.

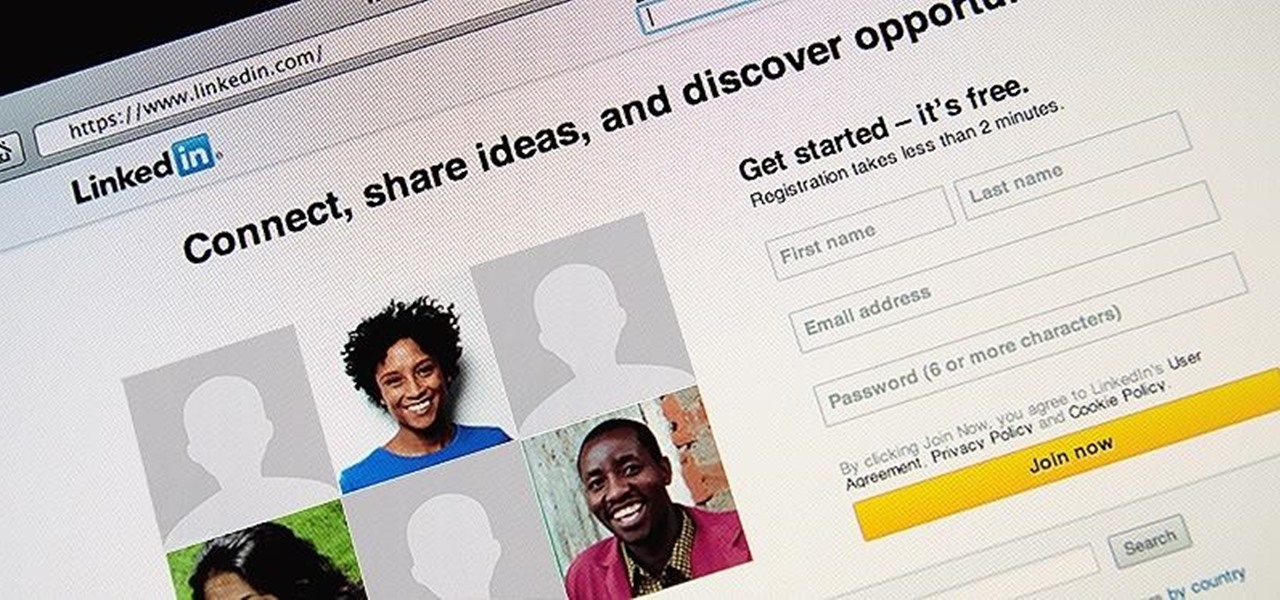
Log in to your LinkedIn profile, and you'll immediately be prompted to check out who's peeked at your profile. With one click, you can discover how many recruiters, companies, and random people have viewed your online resume.

When I was moving into my current apartment, I had to store some of my things in my ex-roommate's garage for over a month while I was getting settled. One of those things was my dresser. Upon moving it into my new place, I realized something was horribly, horribly wrong—none of the drawers seemed to fit quite right anymore (if they fit at all). The combination of the differences in temperature and humidity in the garage caused them to swell and change shape. Several months later, they fit bet...

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf