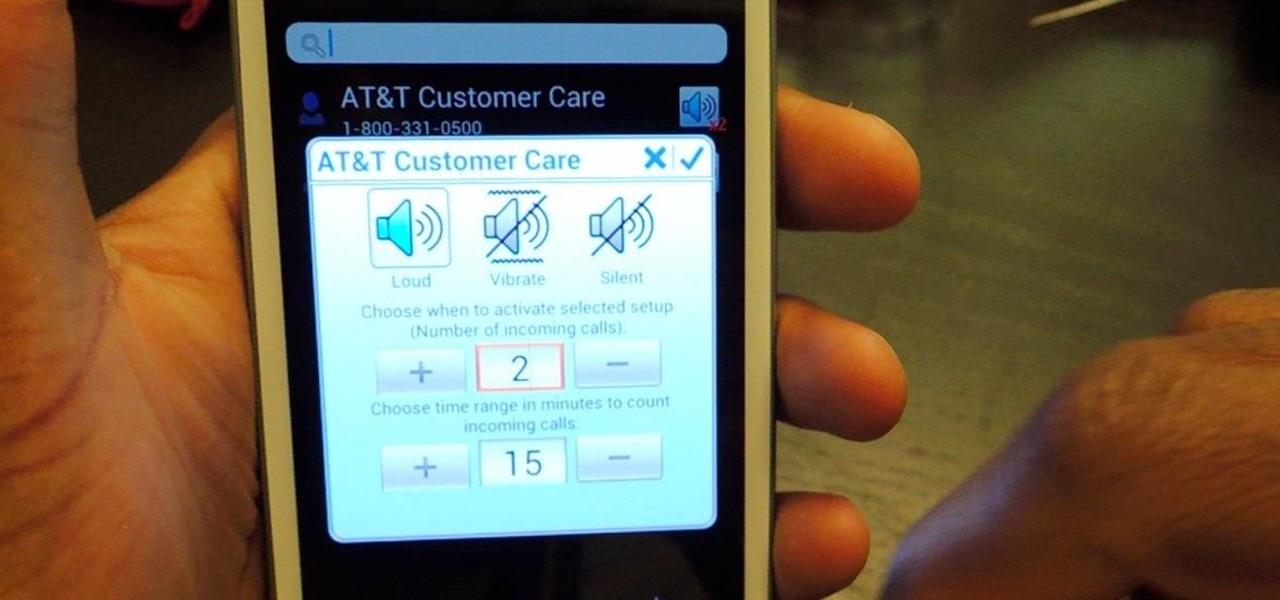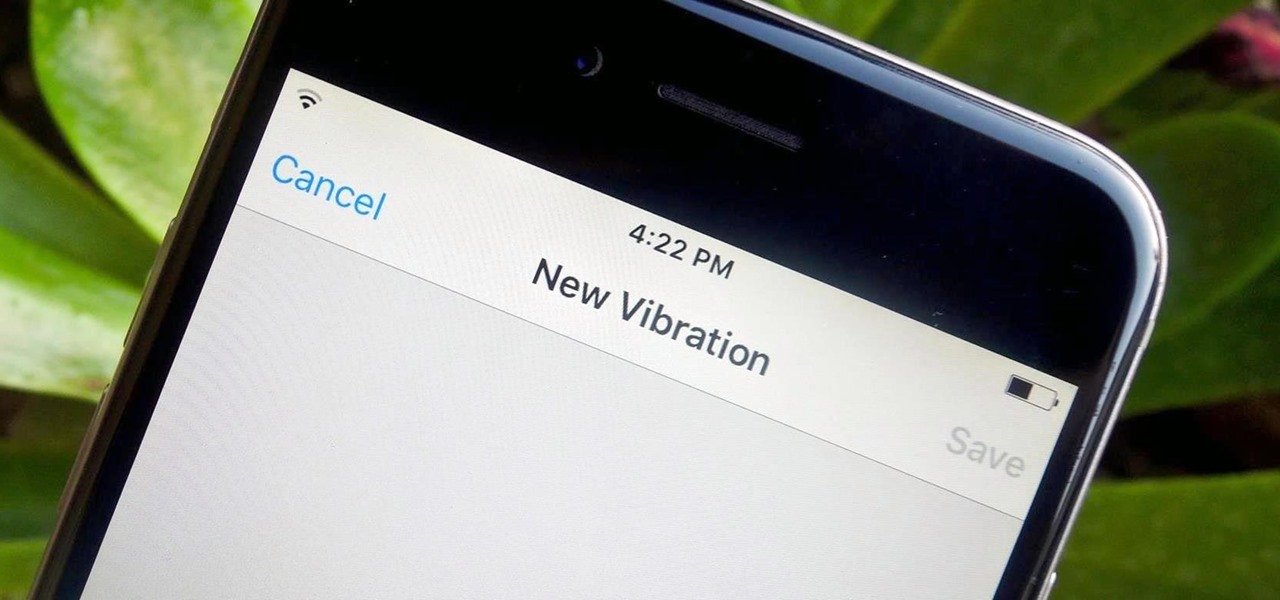
Certain contacts on my iPhone have special ringtones so that I know exactly who's calling or texting without looking at my screen (like Adele's "Hello" for all my exes). But when my phone is silenced and tucked away in my pocket, these contact-specific ringtones can't really help me out. Luckily, there's something else that can—custom vibration patterns.
If you don't like watching YouTube videos on your computer with your hand glued to your mouse, the next best thing is using keyboard shortcuts. They may not seem any easier than clicking, but once you get them down it's a whole other story. Plus, there are some features you might not otherwise use (I'm looking at you, speed control) unless the shortcuts existed.

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).
Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

Instagram is all about sharing and interacting with others, but sometimes we hide in the shadows and lurk. Whether their ex-lovers, current crushes, former high school classmates, or future coworkers, we silently view their content without them knowing. You can deny it all you want, but we've all lurked at one time or another.

Android L hasn't made its official release yet, but if you installed the early release using the Windows or fastboot method, you may have noticed some minor inconveniences, like the lack of a battery percentage icon and the absence of a Clear All option in your notification tray.

There are two scenarios that absolutely suck when someone calls you. The first is when you accidentally pick up a call you seriously didn't want to take. Debt collectors (thanks college), crazy exes, or that one guy from work. And the other is when you miss a super important call and can't get a hold of them afterwards.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Help Alan Wake uncover the mysterious disappearance of his wife in the small town of Bright Falls. This isn't your ordinary video game, so be prepared for a different kind of gameplay! And these videos will help you get through the first episode in Alan Wake on the Xbox 360. Not just that, but you'll see how to beat Episode 1 on Nightmare Difficulty!

One day, you may find yourself in an emergency situation where you need to undo the chain lock of your home's front door, or somebody else's front door. Maybe someone forgot the unlock it when exiting the back door. Maybe you're grandfather is having a heart attack. Maybe your wife is cheating on you. Whatever the reason, it's fairly simple to break in by undoing the chain lock.

This video is on how to install the LED light kit onto your Axon Racing anti-gravity razorback racer hover.

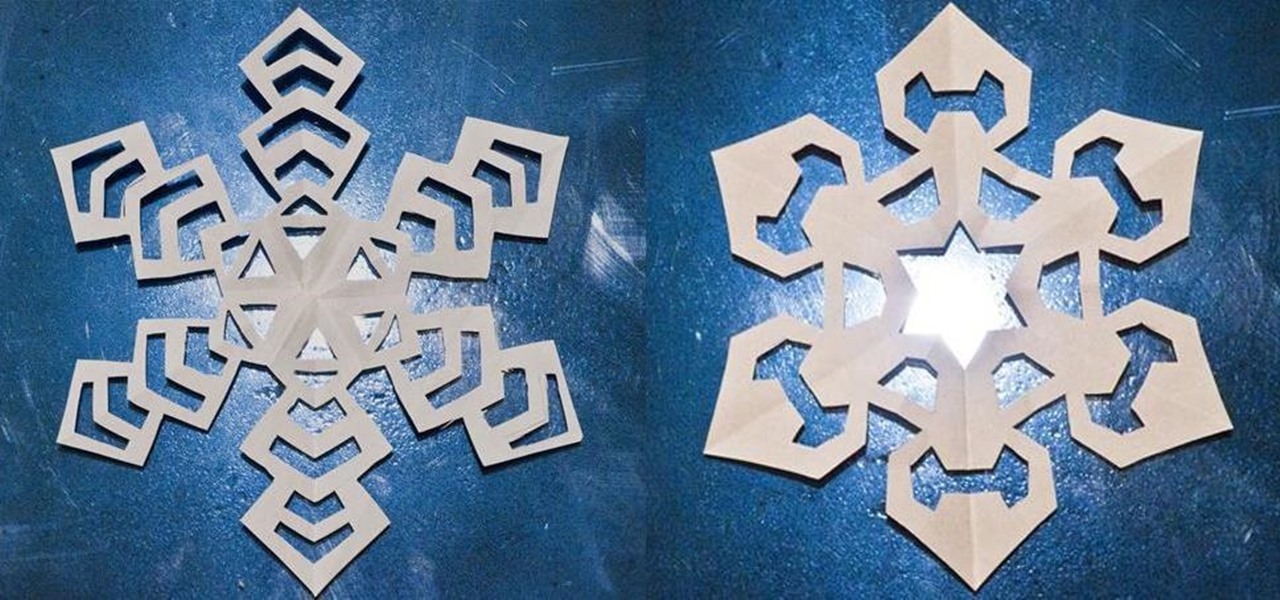
We've all made them. I remember making hundreds of paper snowflakes when I was in elementary school. You take a piece of paper and fold it in half, then fold it in half again. You now have a piece that is one fourth the size of the original. Now you fold it in half diagonally. You then cut slices out of the edges of the paper, and unfold to find that you have created a snowflake. The resulting snowflake has four lines of symmetry and looks something like this: If you fold it in half diagonall...

I'm a new parent and I just moved into a new home. The first thing I wanted to do was ensure my toddler's safety in his new digs. That meant buying a bunch of baby-proofing products from Amazon, realizing most were junk, then buying some more until I found solutions for all my needs.

Seeing that you probably can't go ten minutes without lying (according to this study), you're probably interested in becoming a better liar. The best way to do so is to learn what makes a bad liar, and then do the opposite.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Special evolves are always a pain. You just have to keep in mind that Pokemon only evolve when they feel ready, whether if they want to be stronger or even more beautiful; just look at Feebas. This video will show you exactly how to evolve Feebas to a Milotic in Pokemon Ruby, Sapphire, and Emerald.

Whatever the occasion, if you like cranberries then you're going to love this dish. Wow your family and friends with this delectable Thanksgiving side dish.

Each & Every One of You (EEOOY) is a mock TV show pilot that teaches ordinary people how to make contemporary installation art. If these words strike fear into your heart or make you cringe with memories of seeing contemporary art and wondering what the hell it was all about, this show is for you!

Make your own mayonnaise; it's mostly just eggs and oil, and homemade tastes better than store-bought. Watch this video to learn how to make mayonnaise.

This video is on how to setup the axon racing anti gravity razorback racer. it involves receiver installation, zeroing your servo with the trims and lifting the horn, programming the esc, installing the lipo, testing the unit, initial turn on.

Learn how to play "How To Deal" by Frankie J, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

The biceps tendon attaches the biceps muscle to the radius. Learn how to diagnose and treat a biceps tendon tear in this medical how-to video. Usually the area is painful, swollen and bruised.

Zooming in and out within Instagram Stories is a good way to take your videos to the next level. Whatever a next level is. Sometimes I just run out of words to describe how fun using Instagram is, so for today, I got "next level," which means whatever you want it to mean.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Even though the 88th Academy Awards have come and gone, there's a good chance you still haven't seen all the films that were nominated—or even those that won big.

Valentine's Day can seem like Singles Awareness Day if you're newly broken up, but that's all the more reason to treat yourself on this pink-and-red consumerist holiday. Whether you're happily single or bitter and bitchy, there's definitely something on this list of Anti-Valentine's Day treats to fit your mood. Remember: cake is still cake!

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

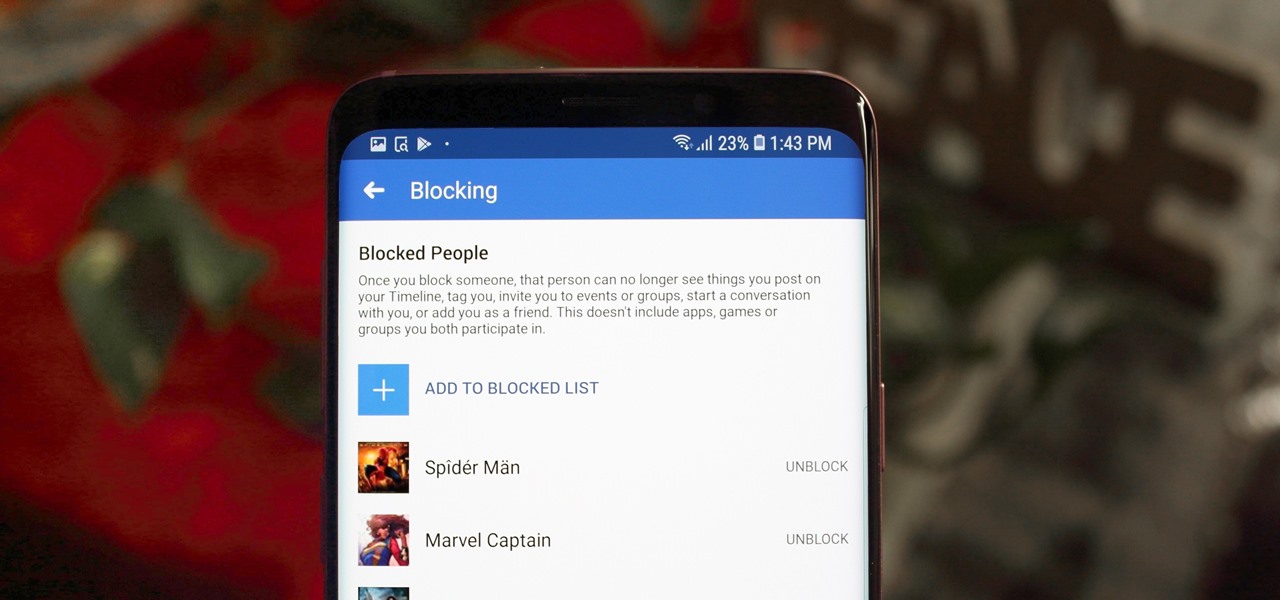
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

Tesla CEO and founder Elon Musk has repeatedly said this year all Tesla models made since October 2016 have the requisite hardware for "full self-driving" capabilities, yet the company has reportedly begun to add a second graphics processor (GPU) to its computer platform for Autopilot — without officially saying why.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

Lyft officially laid its stake in the ground to develop driverless fleets following its Friday announcement, but how fast it is catching up to ride-hailing competitor Uber's driverless initiative remains to be seen.

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

Mobile wallet Curve just released a new feature that lets you correct past mistakes. Sounds incredible, right? Unfortunately, the mistakes you can erase aren't things like forgetting to do an assignment in school, screwing up a job interview, or, well, your ex. However, you can switch the card you want to use to pay even after you've paid with Curve, and that's still pretty cool.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

The big Waymo versus Uber trial isn't scheduled until May, but the heat between Uber and Waymo is rising fast; Waymo wants Uber's driverless trials shut down by a court injunction, unless ex-Google employee Anthony Levandowski testifies in court.