Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

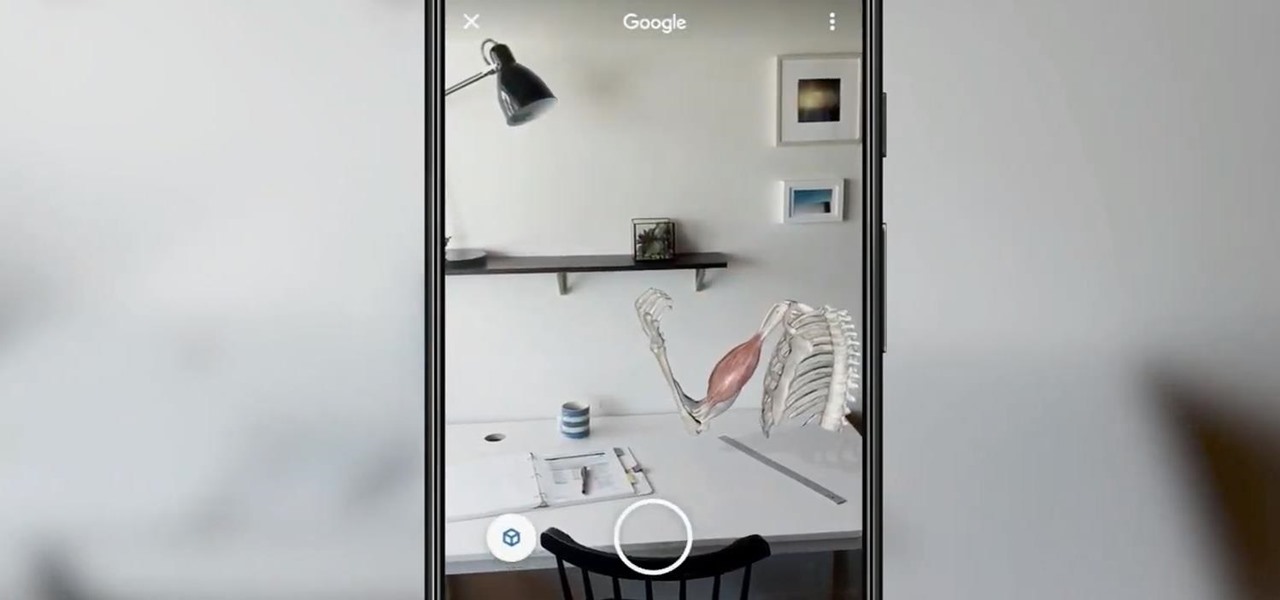
It might sound odd to call interior decorating exciting, especially if you're not a professional within that industry. But that's exactly what it is when combined with augmented reality.

If Google hasn't already demonstrated that it is serious about augmented reality, then it made it abundantly clear at the Google I/O keynote on Tuesday.

Now that we've had a few days to recover from the VR geek versus augmented reality nerd battle between Oculus founder Palmer Luckey and Magic Leap founder Rony Abovitz, we can get back to taking a closer look at the Magic Leap One. This time, we take a very brief dip into the Abductor app.

Microsoft is adding another important piece to its growing immersive computing arsenal by putting its newest Mixed Reality Capture Studio in the center of the movie business: Hollywood.

Luxury automaker Mercedes-Benz has joined the growing list of automakers adopting augmented reality to provide an assist to its manufacturing operations, in this case, via the Microsoft HoloLens.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

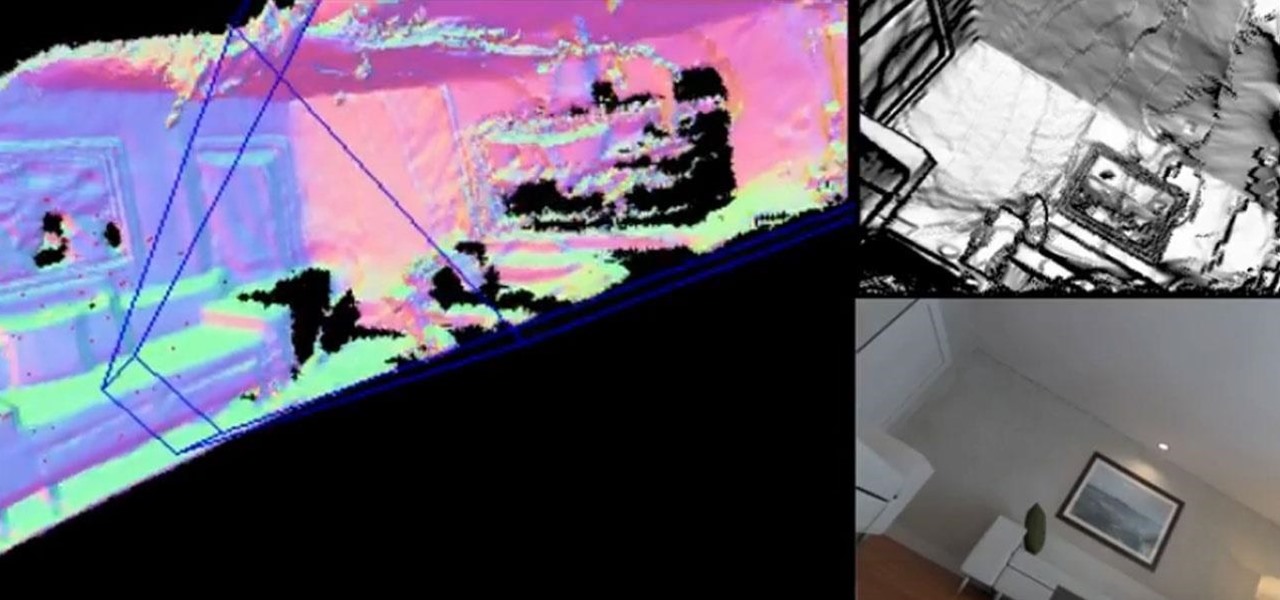
Augmented reality startup 6D.ai is now accepting applicants for the closed beta of its 6D SDK. While operating in the background on a smartphone, the computer vision platform captures a dense 3D mesh in real time using just the device's camera (such a feat typically requires a depth sensor).

According to Indiana Jones, certain things belong in museums, but, thanks to augmented reality, you can now see some of the ancient treasures of the world in your own home via the Civilisations AR app from the BBC.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

To the best of my recollection, Fruit Ninja was one of the first touchscreen games that appeared to really take advantage of the new paradigm of user input, turning the player's finger into a produce-slicing katana.

How would you feel if the stethoscope used by your doctor to listen to your heart and lungs was teeming with potentially unfriendly bacteria?

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

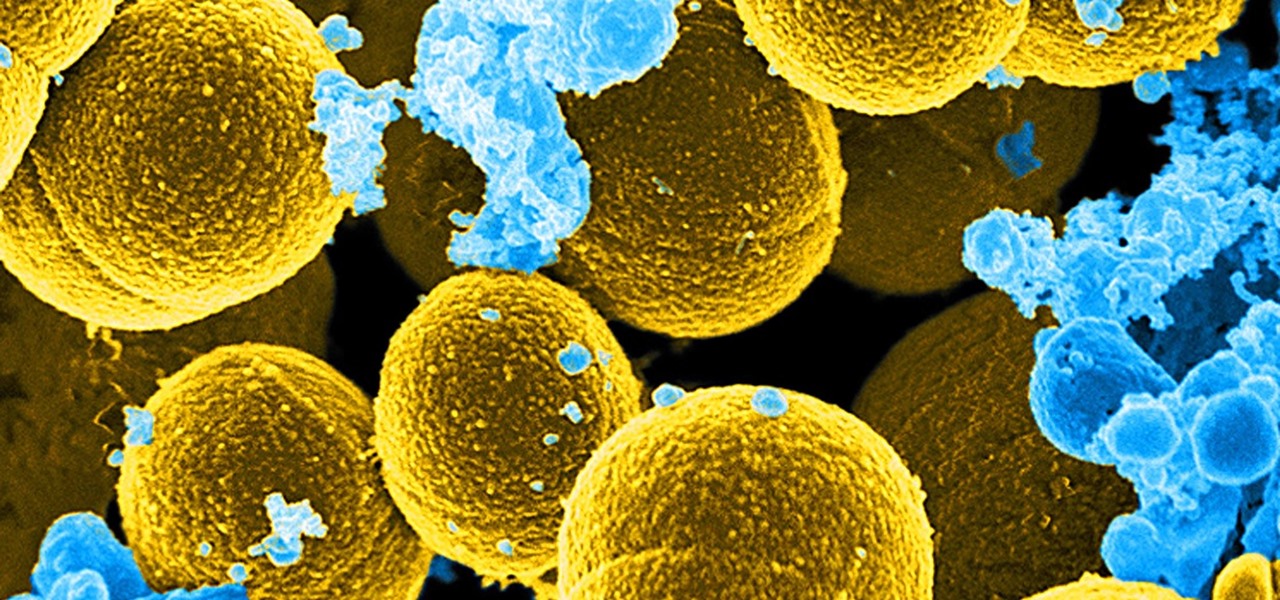
For once there is good news — surprising news, but good news — in the fight against antibiotic-resistant organisms. A recent study found that Staphylococcus aureus bacteria is becoming more sensitive to some key drugs used to treat it.

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

We've all been there: facing a lengthy, complex word that ignores the phonics we were taught in elementary school, unsure of not only its pronunciation, but also its meaning. These words, from autochthonous to esquamulose, are both terrifying and impressive. After all, if someone knows how to use them—and even say them—they must be quite smart. Yet before you begin stuffing every email and presentation with verbose prose, you might want to reconsider what others perceive to be intelligent.

We've all heard the cliches: always look at the glass as half full; a smile can change your entire day; and there's always a silver lining.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

The future: that time that lies ahead, unknown and overwhelming. Whether you're an obsessive planner or someone who can't think more than two days ahead, considering the future can be frightening with all of the "what ifs." Don't let the future keep you awake at night—in fact, the less you think about what life holds in store for you, the better off you'll be.

Decisions are rarely easy to make, and there are countless ways to mull your options over. You can sleep on it, pluck flower petals, make a list of pros and cons, or even follow the advice of a psychic. Yet to make the best decision possible, you might want to consider holding off until a certain time of the day—or even until you feel specific emotions. The state you find yourself in has significant impact on each decision you make.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.