
Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.
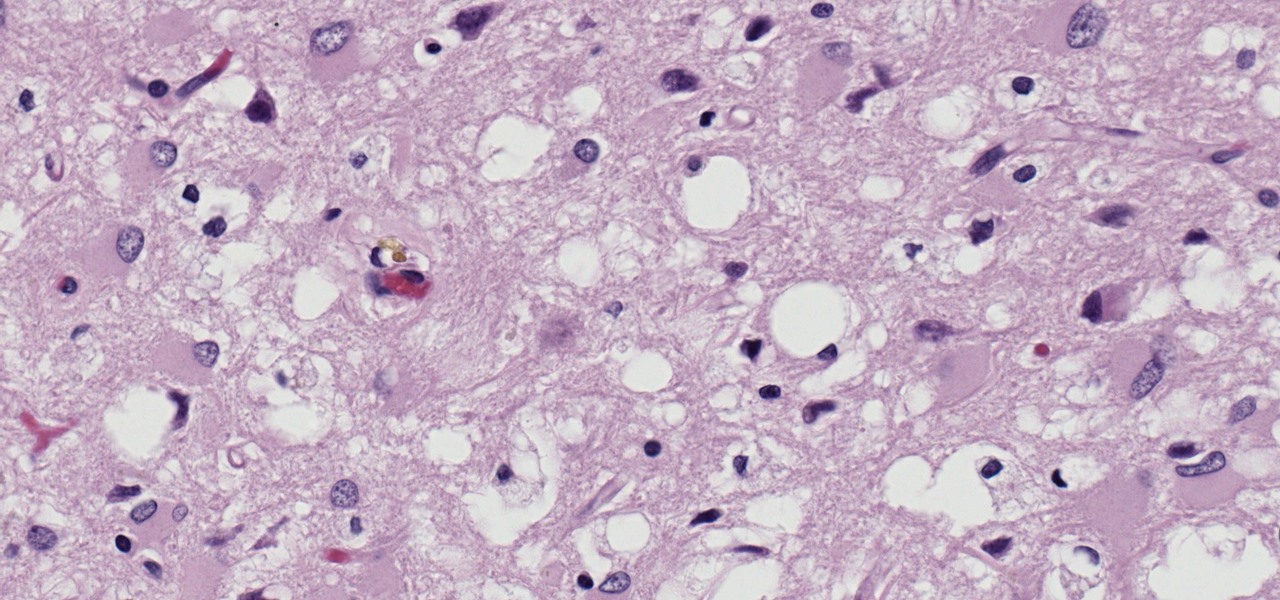
Prion diseases are a group of infectious brain diseases that causes extensive tissue damage, resulting in sponge-like spaces in brain tissue. Prions include Creutzfeldt-Jakob disease in humans, bovine spongiform encephalopathy (often called mad cow disease), and chronic wasting disease in hoofed ruminant mammals.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Even the most seasoned cook is always looking for ways to make cooking easier and cleaning up after meal prep a breeze. There are a million and one tricks and tips out there to simplify your kitchen routines, but some of them are more valuable than others.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

This was a busy week in the tech space. After everyone got over the major announcements of Apple's latest, we examined the metaverse through the lens of Hollywood, and then took a closer look at Facebook's first smartglasses.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a hamster.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a mouse.

Remember Dan White's "Twinkie defense" in 1979? Well it turns out that the the ability to convert food into glucose is correlated with the ability to control oneself.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Enjoy rolling around at night in the sleek luster of silk? Also afraid of a mobster finding out you're rolling around with his cousin's wife? Solution: bullet-proof silk sheets. All you need is the strongest biomaterial ever found--Darwin's bark spider silk. So, grab a loom and start weaving.

New serious results appeared regarding the early puberty "precocious puberty" and its impact on the health of young girls. New studies in Cambridge university regarding the shows that early puberty is associated with increased risk for diabetes, Cardiovascular disease, breast cancer and endometrial cancer.

Dopamine is a neurotransmitter that motivates us to engage in rewarding activities such as eating and sex. Animals without dopamine stop eating and starve to death.

Since the rise of private property and industrial production, modern capitalism has been on a undeniable crash course with Mother Nature. It's no so much that we'll end up murdering the entire planet, but just that the planet will quietly smother us with a pillow of famine, heat, cold and hurricanes. We over-farm land and replace the nutrients in the soil with oil. To package our oil-based produce, we wrap them in synthetic oil-based plastics, soon to be discarded in a trash heap or ocean.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...






























