If you enjoy using the Bevel Tool in modo and you have a predilection for edges you will LOVE "Edge Bevel". This sparky little production examines the heartfelt story of edges who strive to be more than a single edge. Follow their story as they expand their horizons thru the use of the Edge Bevel tool in modo 101 and learn how to add details to edges on models and meshes.

This modo 101 3D modeling software tutorial examines the much uner-touted power of the Flare tool. Have you got Flare? modo does. The Flare Tool combines the push tool with a linear falloff. See how to use the Flare tool when modeling in modo in this tutorial.

In this golf lesson golf instructor Steve Bishop discusses some popular takeaway methods, his whole club takeaway method, and examine some common faults among golfers. These tips will help you swing on plane from the very start.

In this video,examine the differences between wolves and the dog as it relates to human-to-canine communication.

In this series, Matt will examine the Stonewall Attack for White and display defenses which he thinks are challenging and/or interesting. Here's a prototypical Stonewall game where everything goes right for White.

You don't have to have a university degree to understand the basics of Iguana health and wellness. Let our expert show you in this first section on iguana health how to examine the animal's body, from teeth to tail tip, to determine its measure of health and how to deal with problems. Ron also advises on when it is best to consult a veterinarian.

How many stitches does your crochet art have? How can you tell? Why would you even want to know how many stitches are in your crocheted sweater or crocheted hat? Knowing how to count your stitches is a fundamental step in learning to crochet – assuming you want your finished product to be the right size and shape.

Is your girlfriend or boyfriend always right? No matter what you say, they will always be right? Well, in this tutorial learn how you can win in an argument fair and square with a few simple techniques.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

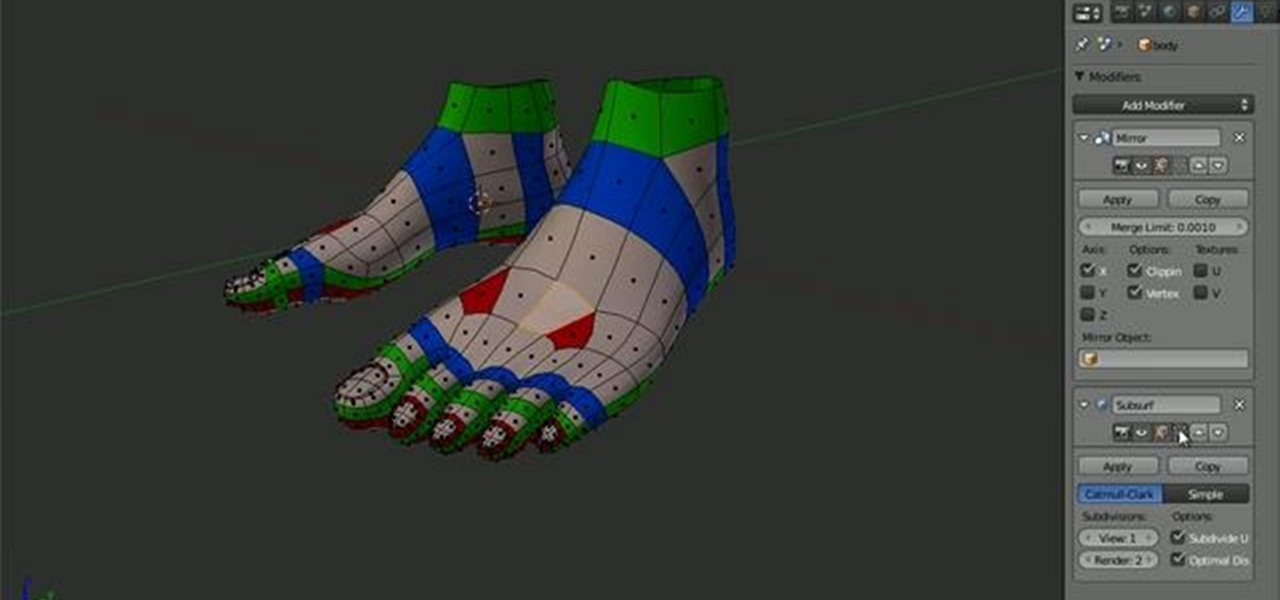
Arguably the single most important aspect to modeling is topology. This Blender 2.5 overview tutorial takes a look at the topology of the human foot, examining each of the main edgeloops, poles, etc. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the folks at CG Cookie. For more information,...

Curtis Smith (Extension Horticulturist) and Rick Daniell (Bernalillo Co. Horticulture Agent) examine the bark of a poplar tree. The young bark is smooth and will furrow as it grows older. There are straight horizontal lines on the bark that look like sap-sucker damage but in this case, the markings on the poplar is the normal bark development of the poplar. They also look at and discuss Fall Web Worm cocoons which look like bird nests on a tree. Web worms do not do as much damage to the tree ...

When using face unlock on the Pixel 4, your lock screen notifications are bypassed by default to help you unlock your phone instantaneously. This is different than Face ID on the iPhone, which shows the lock screen until you swipe up, but only shows notifications when you've been authenticated. If you want to do it Apple's way, there are settings you can adjust on your Pixel.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

In this video tutorial, viewers learn how to cite a cereal box in MLA 2009. citation is a reference to a published or unpublished source. In general, a citation requires the author's name, publication information and medium type. Start by examining the entire cereal box for the information. Look on the front, back, sides, top, bottom and even inside. Usually, users will only be able to find title, medium, corporate sponsor and place of publication. This video will benefit those viewers who ar...

In this video, Ed Kriston from AAA-Midatlantic explains how to winterize your car. He first talks about the fuel systems. The fuel pump and fuel filter are inside the tank, and lines and hoses run from the tank to the engine. He points out the fuel lines and injectors in the engine, and recommends that you make sure there are no leaks in the lines and hoses. He demonstrates how to remove and examine the air filter and shows one that is dirty that should be replaced. A dirty air filter will co...

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

The Western film, once the end all be all of great American filmmaking, is now rare to behold at all at the movie theaters. Whereas in the old days directors made the films about true American gung-ho spirit and handsome, stoic John Wayne cowboys championing the greater good, these days the genre gets ruined by CGI and other absurd additions.

You never know what you might stumble across on your next visit to a flea market or thrift store. Real gold is very soft, so biting down on the piece is a time-honored test for real gold. You can also examine your jewelry for a maker's carat stamp or discoloration that may indicate fake metal.

Veterinarian Mark Lopez of Wholesome Dairy Farms demonstrates how to milk a cow. Use a teat dip to wet the teats. Then, massage in the fluid so it loosens up the surface dirt and kills bacteria. Stimulate the teat end with your fingers. Next pre-strip the cow by gently pulling on the teat and mimicking the suckling action of a calf. Let the iodine teat dip to sit on the udder. When the cow squirts milk out of the teat, it means that she is stimulated and comfortable. Take a clean towel and wi...

An associate from Garden Years discusses the danger frost poses to small, outdoor plants. Since you don't have a lot of control over the weather, there are a few tips you can follow to try an avoid any unwanted damage to existing plants. The host examines a peach tree to identify when a plant is blooming and thus very delicate. If a plant is fully blooming, then any temperature below freezing (32 f) can damage the blossoms. Aside from putting cloth over the plant, mulch is also very helpful i...

This video demonstrates how to determine if your Ugg Boots are counterfeit. If you purchase Ugg boots on the Internet and you are wondering if they are fake, you should examine the box closely. Uggs are made in Australia. If there are any labels affixed to the side that indicate other countries (e.g. China), then they are fake Uggs.

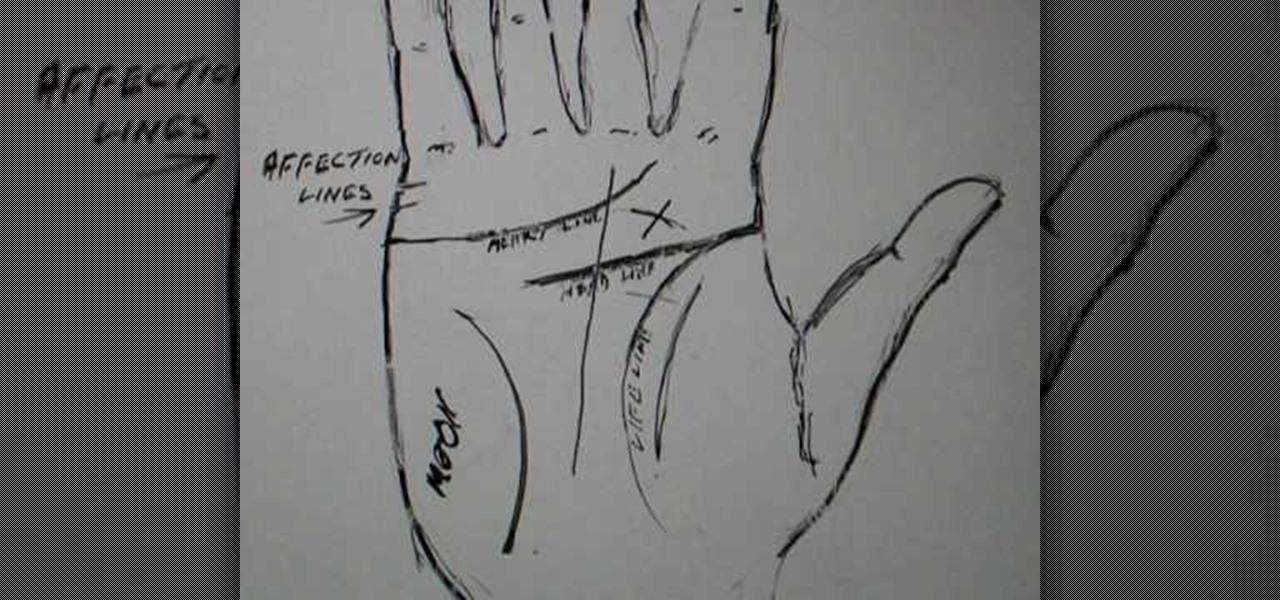
This video provides a diagram and explanation of the some of the more common mysteries in palm reading. Although the video does not provide much instruction for the actual act of palm reading, the diagrams are very helpful in determining which lines on the palm of the hand would be used to conduct a reading. The diagram shows the names and locations of each line that can be read on the palm. The life line, line of affection and line of intuition are explained in detail. The psychic cross is a...

Richpin shows the proper way to replace an engine coolant temperature sensor on a Saturn S series. Before he explains the steps of replacing the sensor, Richpin covers the tools to use. Also, Richpin illustrates the types of tools to avoid before beginning the replacement process. First, remove the cap from the expansion tank and then tighten it the way it was before. Next, Richpin shows the procedure for locating the temp sensor. Then, remove the connector from the sensor. Afterwards, Richpi...

This how-to video is about how to winterize your car exhaust and fuel system.

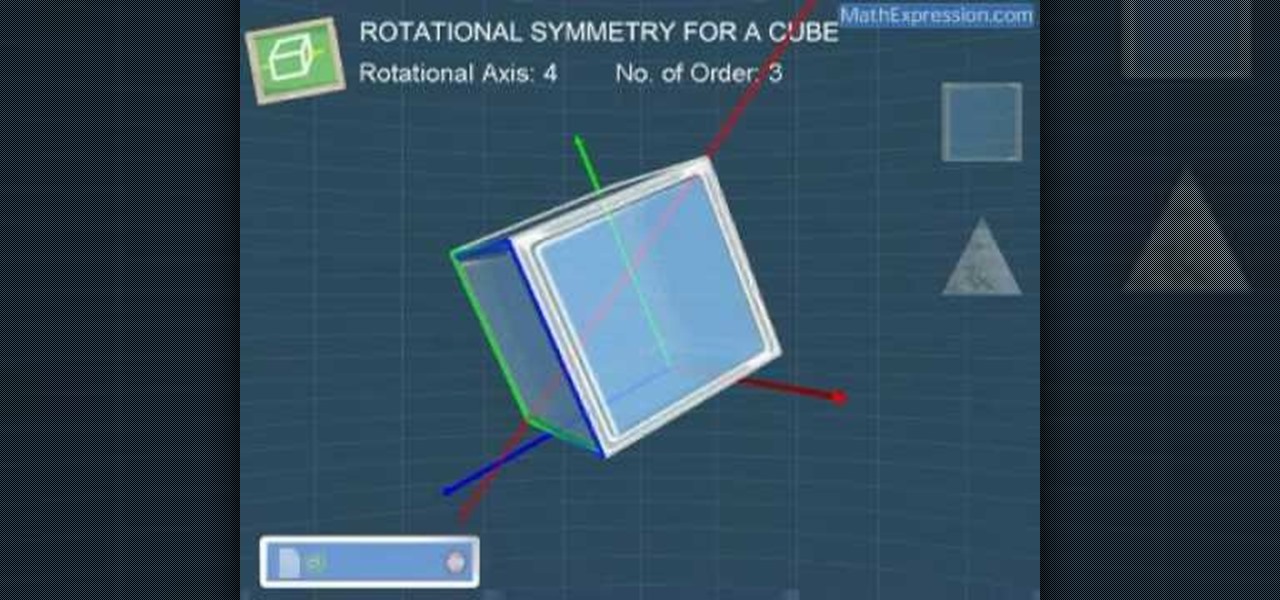
One of the most fascinating figures in the 3 dimensional world is the cube. This video goes into details about the rotational symmetry of a cube. The video examines this property of cubes by rotating the figure on different axis and inspecting how this property of cubes change or react. This video is for anyone interested in 3 dimensional figures. After watching this, viewers should have a basic overview and understanding of this unique rotational symmetry property of a cube.

This video shows how to use a special tool to redact or remove sensitive information from Adobe Acrobat 9. This includes hidden metadata, file attachments, comments, hidden text and layer elements within a PDF file. You can also set it up when you're emailing. The Examine Document function highlights information that you may want to remove. You can then select the different types of data and choose which things you want to remove.

The timing of a young power player - Team USA's Derek Eoff - is examined. Pick up some bowling tips and tricks to improve your game, whether you are a beginner or a competitive bowler in a bowling league. Learn how to use the six step approach with this bowling video.

Chris Barnes (8 PBA titles), Sean Rash and Kim Terrell examine how personal style affects equipment choices.

Check out this instructional English language video that demonstrates how to improve your English vocabulary skills, your listening skills, and your grammar skills. This is a lesson for the advanced English language learner. The theme is the 2008 Olympic Games that focus on VOCABULARY, LISTENING, and GRAMMAR skills. This is PART THREE, in which we examine and practice several (but not all) verb tenses. Be sure to watch the first two videos. Improve your English vocabulary with this instructio...

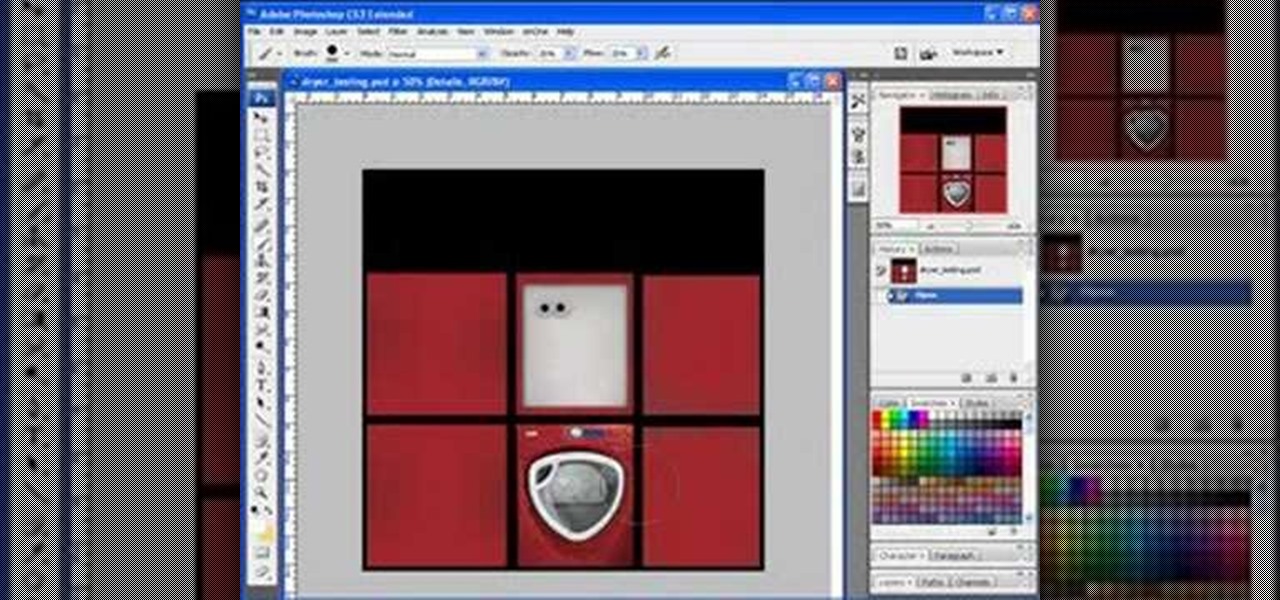
The third dimension has finally arrived to internet browsing! Be sure to catch the wave of innovation with this series of tutorials. Initially, we'll be examining the importance of texturing basic 3D objects. Watch as the almost magical effects of texturing in 3ds Max transform a simple cube into a trendy clothes dryer. Polygons are saved, browsing is made speedier, and clients are bound to be happy. Next stop, bring it into Papervision3D! If you wish to learn about using 3D elements on the i...

This video will guide you toward creating a pop-up bird. You will be shown how to fold the pop-up base with some suggestions for finishing the model. The final model will be of your own design. It will also examine some of the things you can change to alter the pop-up mechanism.

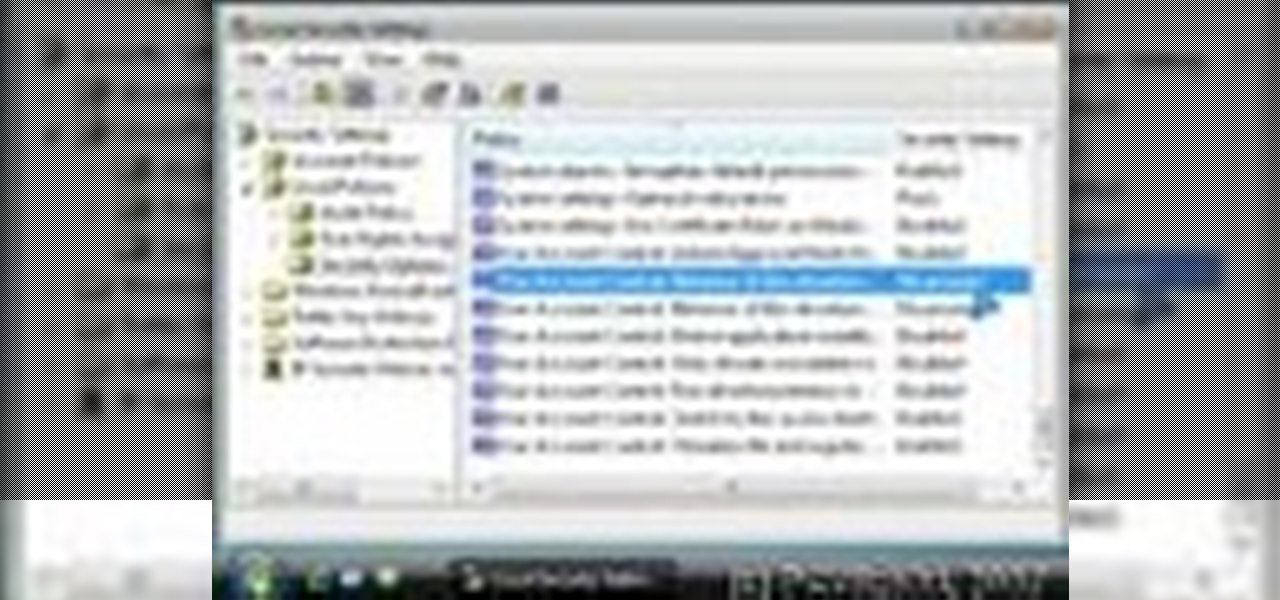
Why is Windows always asking you for permission before you do anything? Since when does Windows control your computer, and not you? Those user account control popups can be so frustrating, especially when it comes to simple tasks.

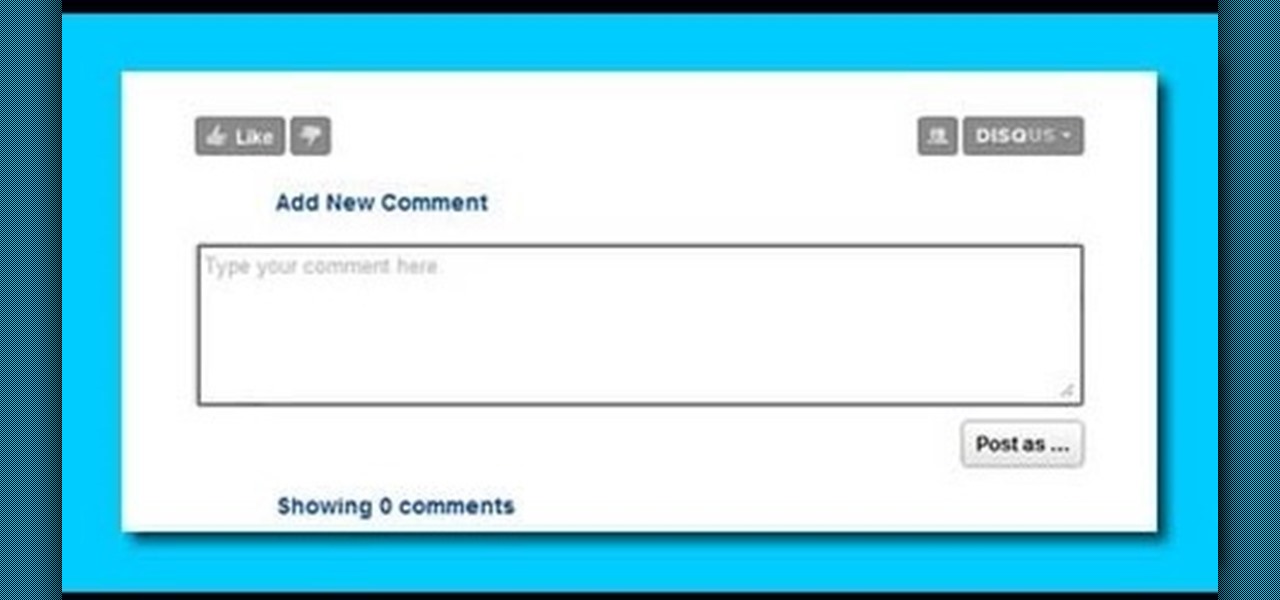
This Dreamweaver CS4 tutorial takes you on a step by step process for installing an automated comment box system for your website. The system is a great way for communicating and interacting with your website users. It has a great feature that automatically sends you an email everytime someone comments in your website. Also it will allow you to post a reply by email.

Got some information you want to circulate quickly and extensively? Learn what it takes to get people to pass it along.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.