If you're not much for office computers, and like using your own powerful PC at your workstation, then chances are, you're going to have to login to the network. Microsoft shows you how to quickly login and join a Domain or Workgroup in an office network.
Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...
Michael Weisner teaches us how to draw a cartoon bed. His credentials boast of him to be a computer animator. He starts the video off in a rather creative way with him as a cartoon. He slowly draws a cartoon bed by hand. He does this step-by-step, starting from the base up. Going rather quickly, he draws a bed and outlines it in marker. As Michael is drawing, he narrates the process and explains what he is doing and how it is done.

Oktay1979 takes a look into writing an annotated bibliography. Learn the steps such as citing a source, summarizing your reading, accessing your source, documenting your authors credentials, and reflecting on your source. Each bibliography is usually 150 words long and done in new times roman. You can also get a form to show you how to format the bibliography correctly. Make your writing process unique and accurate. Make sure you're doing your bibliography right by following the correct steps...

This is a basic video in order to draw a very pretty heart. The credentials that this creator boasts is that of a computer animator. He already drew a heart in pencil. He starts off by telling us the materials that he needs. The video shows him highlight and underline the pencil heart that he drew earlier and making it bolder. He talks us through making the heart, but does not slowly explain the specific strokes or techniques into making it.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

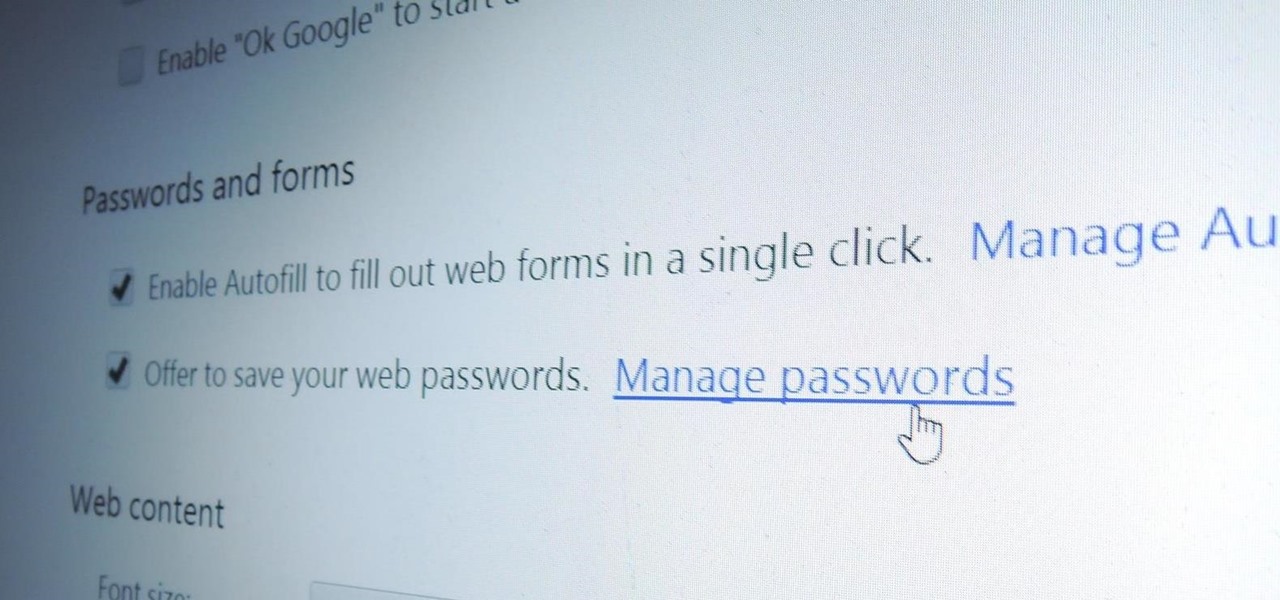
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

It's March once again, and while that might signify the beginning of spring for some, basketball fans have this month marked on their calendars for one good reason: NCAA March Madness. Though the tournament is already underway, the Sweet Sixteen leg begins Thursday, March 23, 2017. If you fear you may miss the upcoming games, worry not, as free apps for smartphones and tablets are available to help you watch all the action.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Welcome back, my greenhorn hackers!

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the power button mechanism, free of charge, for certain iPhone 5 models.

ER showed the world what goes on inside the emergency room, and in every episode, we experienced a common but very important procedure— intubation. But ER never made it seems easy; it showed just how hard it is for medical students to successfully intubate a patient due to fear and naivety. And for real-life doctors and medical practitioners, learning the art of airway management is just as difficult.

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...

Any patient with pain in the abdominal area will require you to perform an abdominal examination, and this video lesson outlines in great detail, how to perform a general abdomen exam. This is great for any medical student or up-and-coming doctor — even nursing students could benefit from this exam procedure. You'll learn about inspection of the abs, auscultation, percussion, palpation, the liver, the aorta, and the spleen. After watching the full procedure, you should be able to identify the...

Most won't know what the acronym HEENT stand for, but if you're a medical student, doctor or nurse, you know that it stand for head, ears, eyes, nose and throat. To perform a HEENT examination properly, you must know all the steps and techniques to diagnose your patient. This video lesson will outline the examination procedure, from start to finish, and shows you general palpation techniques and examining the temporomandibular joint, superficial lymph nodes, thyroid gland, eyes, ears, nose, m...

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

The folks behind StumbleUpon have created a video service that is just as awesome at introducing you to new content as their website service is.

Jordon Schranz brings you this tutorial on drawing. Search WonderHowTo for Sessions Online School of Fine Arts for more drawing tutorials. The technique & craft of drawing isn't necessarily about inherent talent, it is something that comes with lots of practice. It is all about being able to accurately record what you see.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

Whether you're at a bar or just with a group of friends, this is a great illusion that makes it look as though you are sending a large object right through a table!

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Media subscriptions are all the rage these days. Between Netflix, Apple Music, HBO Now, and countless more, your TV, movie, and music options have never been better. Unfortunately, all these choices weigh heavily on your wallet. So, when there's an opportunity to snag not just Spotify but Hulu and Showtime as well, all for just a tad bit over five dollars a month, how could you turn that down?