Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

This year in Android has seen a myriad of visual improvements among various apps' user interfaces. From the card swipes of Google Now to the article fade-ins of Circa News, developers have shown that they can strike a beautiful balance between form and function. Check out the following video, complied by redditor hinesh, for some examples.

Most smartphone manufacturers focus on megapixels when it comes to cameras, but HTC took a different direction with the HTC One. Instead of trying to compete with the 13MP camera on the Samsung Galaxy S4, or the 20MP camera on the Sony Xperia Z1, or even the newer iPhone's 8MP, they decided on a simple 4MP camera. At first, you might think that 4MP is terrible, but not so fast. There are many advantages to your HTC One's camera that other phones just don't have.

This is a video by Tinkernut on How to Make a Chrome App in 5 Minutes. Making a Chrome App and an Extension is actually a fairly simple task. All you have to know is a few required fields and the JSON syntax.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

In this handbag fashion video series, learn how to choose the best handbag from fashion expert and handbag designer Lindsay Colbus. Lindsay will teach you how to choose the best handbag for you and will give you examples of good and bad handbags. She will teach you how to match a handbag to your outfits, how to choose an evening handbag, how to choose a day handbag, how to choose a trendy handbag, how to choose a casual chic handbag, how to choose a clutch handbag, and how to choose a handbag...

Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty time-consuming to create from scratch — but there's an easy way to forgo all these issues — make keyboard shortcuts.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

There are literally hundreds of granola recipes floating around the internet—but I can tell you right now that they're all completely unnecessary. You don't need a recipe to make granola; I've been making granola for years and have never once used one!

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

Before I really get into this article, it's important to note that you do not need a Steampunk persona (or "steamsona") in order to be a Steampunk, or wear Steampunk clothes. Some people like to pretend to be a different person when dressed up in Steampunk clothing, but that is entirely optional, and only to be done if it appeals to you. That said, even if you aren't actually acting as your character, it may still be helpful to have one in mind when putting together an outfit. Personally, I'v...

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

More and more tech-savvy leaders are flocking to the lucrative and exciting world of project management thanks to the high-pay, analytical environment, and nearly unparalleled flexibility. But this means that competition for the best positions in this dynamic field is fierce. If you want to stand out from the crowd, you're going to need to have more than a few base-level certifications on your résumé.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

There is not a single museum that houses all of the 36 paintings of Johannes Vermeer, so Google decided to come up with a solution to give art aficionados a venue to see the artist's work all in one place — your home.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.

While numerous examples exist of hospitals deploying the HoloLens to assist doctors, surgeons, medical professionals, and students while treating patients, California's Lucile Packard Children's Hospital Stanford is actually using the augmented reality headset to improve the patient's experience.

If you find yourself on the run from the Empire, you no longer need a droid to send a holographic distress message, you just need an iPhone X and the HoloBack app.

Over the past few weeks, a trio of developer lessons (one of which was revealed in Magic Leap's most recent Twitch livestream) have revealed samples of experiences that are possible while using the Magic Leap One.

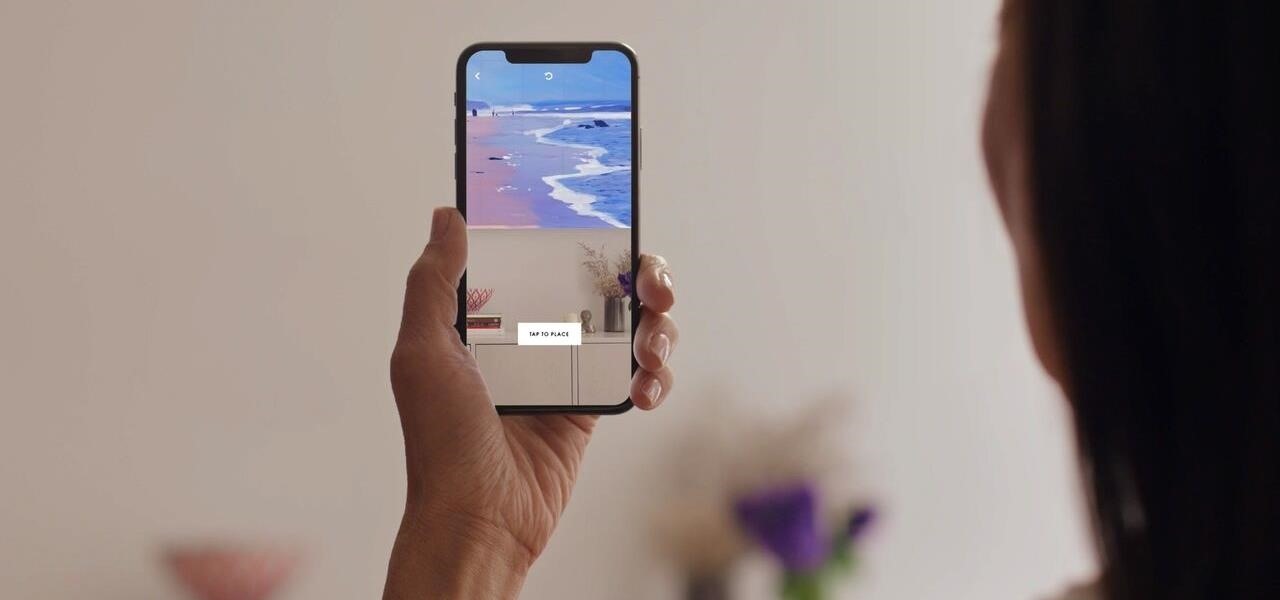
Less than a week after ARKit 1.5 became available to the public through the iOS 11.3 update, the App Store has its first app with AR features (Artsy) to leverage Apple's AR toolkit update.

Given Dwayne "The Rock" Johnson's blockbuster movie pedigree and the promotional power that usually accompanies his work, there's a certain predictable symmetry in the news that Rampage, a movie adaptation of the classic arcade game, has now become an augmented reality mobile app.

Soon, kids young and old aspiring to imitate Iron Man will only need to learn how to duplicate Tony Stark's snarky wit, because Hasbro will now supply the augmented reality helmet.

Augmented reality is making many of our childhood dreams from Star Wars come true. A week after Lenovo gave us the ability to actually play Holochess, Apple has now made it possible to take live video of ourselves and layer on a (non-3D) hologram-like effect, closely resembling the famous Star Wars hologram scene featuring Princess Leia decades ago.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.