
Apple AR: Alexa Plays Nice with ARKit in Demo
A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.


A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.

From all the demos we've seen, we know for sure that the marketing world is going to change drastically thanks to Apple's ARKit.
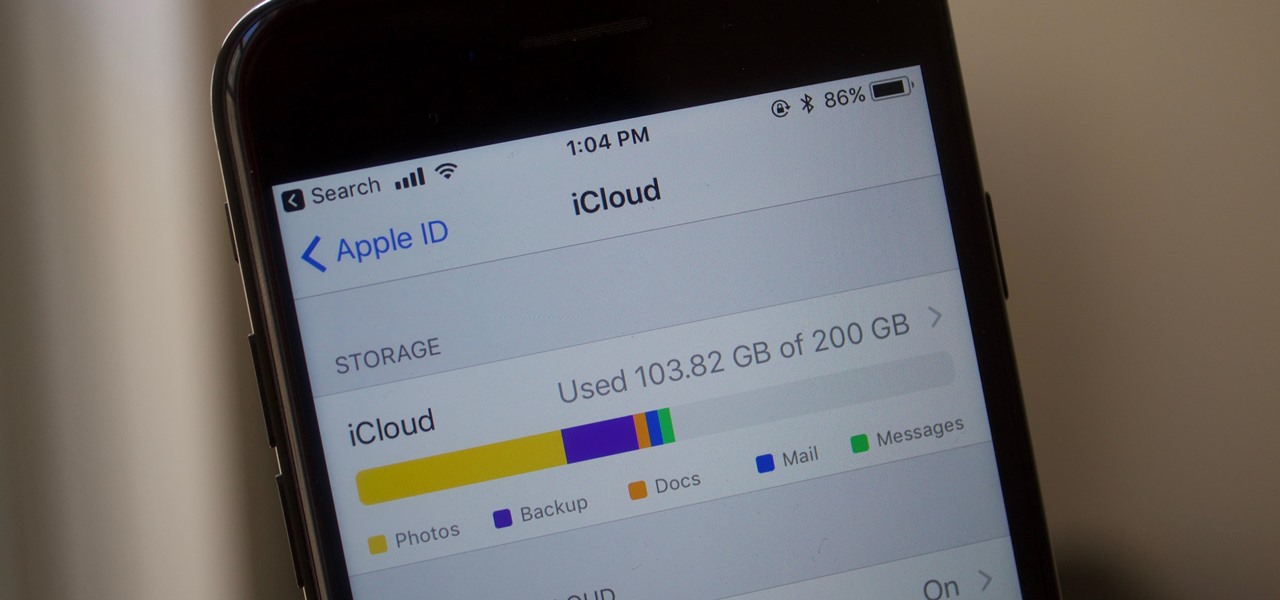
iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.
Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Want to go to Seattle and meet the Actiongram team?

Snapchat accidentally—and then intentionally—announced their digital eyeglasses, known as Spectacles, over the weekend. While we'd hoped their augmented reality-heavy platform would result in related hardware, Spectacles unfortunately seek to "reinvent" little more than a video camera.

LARPing, or live action role-playing, can look a little silly because it requires a lot of imagination to suspend reality. But mixed reality technology like the Microsoft HoloLens can change all of that with voice commands and special effects.
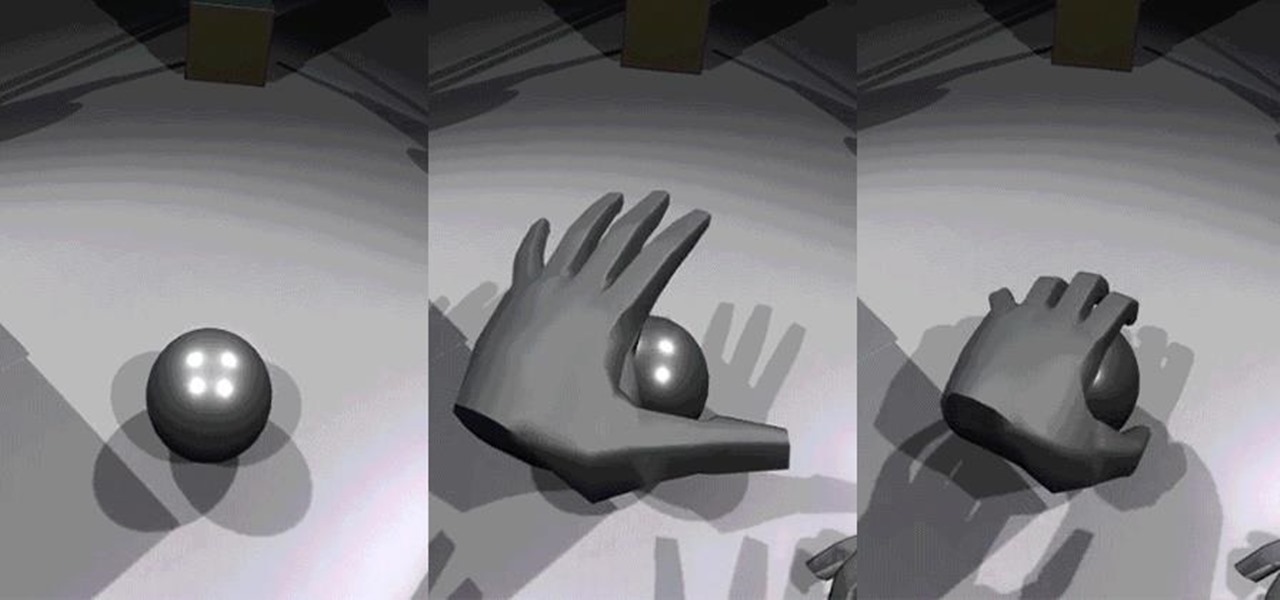
Leap Motion created gesture control for all sorts of things, including virtual reality, long ago, but developers must build in support for their tracking peripheral to use its full potential. As a result, they've created an "Interaction Engine" for Unity, the primary platform for developing virtual and mixed reality experiences, to try and take gesture interaction to the next level.

If you want to quickly understand EtherWars, imagine a game like StarCraft where you build out your base on your living room floor instead of on a computer screen. Before we had computer games to help us imagine what space wars might feel like, we played with toy ships and used our imaginations. EtherWars combines those two elements by replacing toys with holograms that actually react to your choices.
Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Mac OS X 10.11 and iOS 9 won't be officially released until later this year, but that doesn't mean you can't get a taste of it today. And the easiest way to do that is to download the new El Capitan and iOS 9 wallpapers.

To take group shots and better selfies on your iPhone, you can use your Apple Watch as a remote shutter for the Camera app—but what if you want to take a snapshot or video with a different app?
Left-handers only make up about ten percent of the world, which means they typically have to use things made for the majority, i.e., right-handed people. If that wasn't annoying enough, there are studies that show that lefties actually get paid less.

For over 37 years, Apple has been using the same "bitten" apple as their company logo. Sure, it's looked slightly different over the last couple of decades, from rainbow stripes to monochromatic colors, but its shape has change very little.

If you're into photography, you're probably no stranger to the myriad of ways you can take macros with your smartphone. Your phone's built-in camera may not take great pictures up close, but you can modify it to do so with anything from a magnifying glass to a drop of water. However, those types of DIY macro lenses can only get so close.

I loved my Lite-Brite as a kid. There was just something about using those little multicolored pegs to make my own designs, and it's not exactly a secret that kids love anything that lights up (LED sneakers, anyone?). So how do you combine the old-school fun of Lite-Brite with pumpkin carving?

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.

Thanks to its open-source platform and easy-to-use hardware and software, there's literally thousands of Arduino projects detailed online for anyone to make—a magic mirror, DIY polygraph machine, and hotel-hacking dry erase marker just being a few examples. Hell, you can even make the Daft Punk helmet.
Every so often, a big site will make a change to its terms of service that's not so great for its users—without even informing them—and they (understandably) get really pissed off. Recent examples are Facebook's and Instagram's changes, which resulted in user backlash.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.
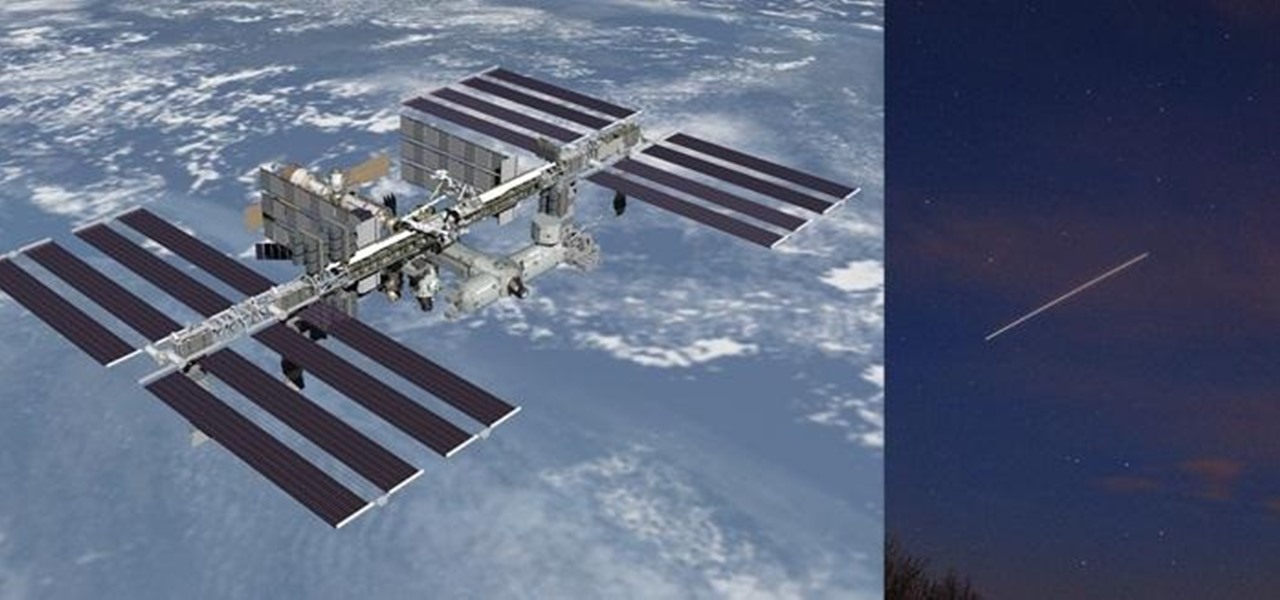
The International Space Station is one of the brightest objects in the night sky when it can be seen. If you know when and where to look, you can even see it from your house. It looks more or less like a really fast-moving plane—so fast, actually, that it's only visible from a specific place for a few minutes at a time. But now you don't have to do a ton of mathematical equations or rely solely on luck to spot the ISS at night. NASA just launched a program called Spot the Station that sends y...

Hey guys, I was building my floating island earlier today (and having a quick look at the competition) and I came up with a couple of hints and tips that will really improve your islands.

Steampunk scientists, there's a new spectrometer for your workshop, and it's called the iPhotometer 5.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Small containers are useful for many things. They're good for storing snacks if you have children, as well as holding coins or odds and ends. But those regular store-bought containers are lame—who wants to keep their stuff in a Tupperware dish or old butter container?

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.
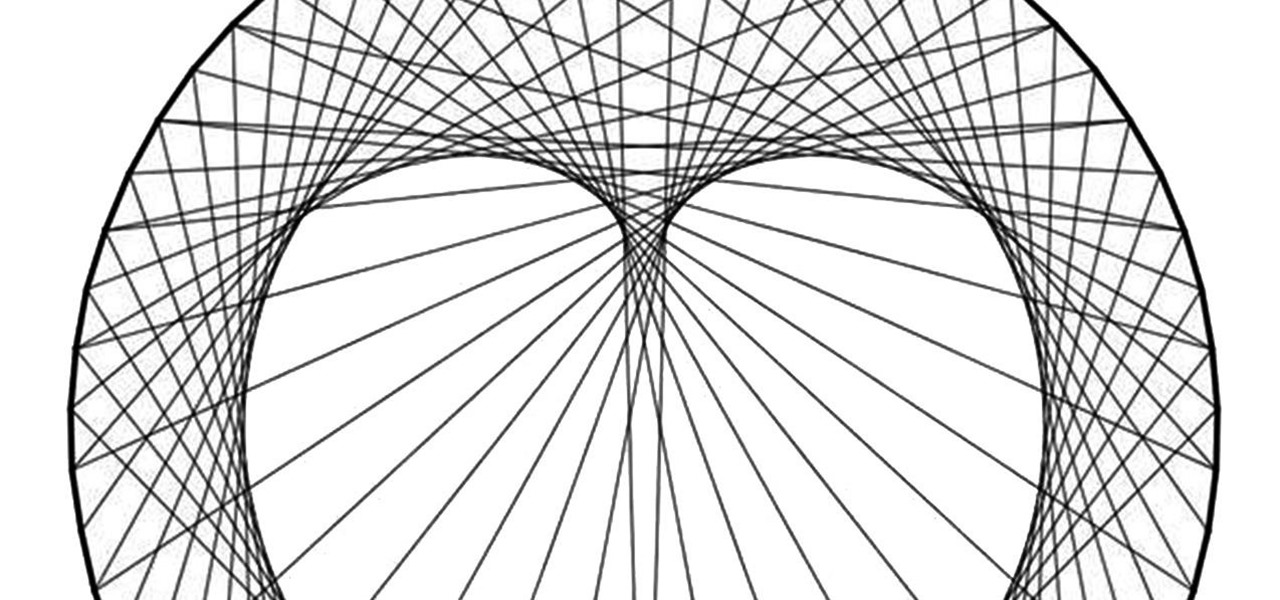
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.

Amber, emergency, and public safety alerts on an iPhone are loud — startle-you-to-death loud even. They can happen at any time, day or night, and sometimes back to back when you're in a big city. Those blaring sirens can wake you from sleep, interrupt an important meeting, or disrupt an entire movie theater mid-movie, but you can turn most of them off if you're tired of hearing them.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will likely keep rising as companies in every industry adapt their business models to a more remote world.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.