As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!
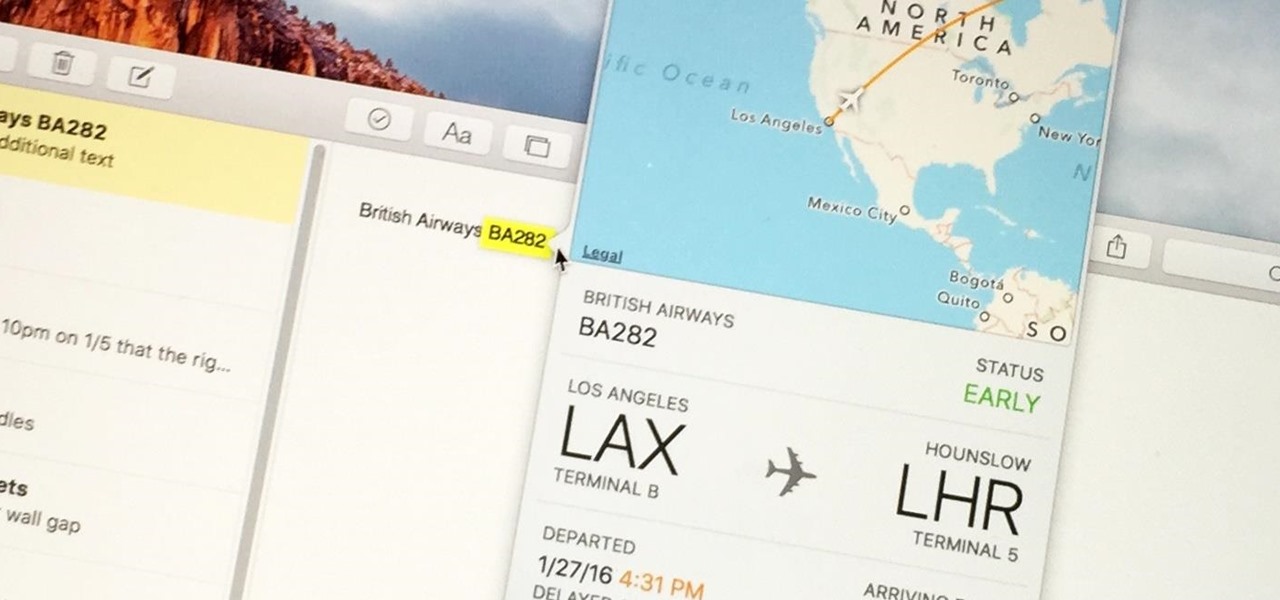
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.

I hate wasting money. To be fair: I doubt there are many people out there who relish the idea, but I especially hate it. And I also dislike spending in excess of what I need. This happens all too often, I feel, when it comes to recipes that involve using sausage.

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.

If you're a frequent baker like myself, you've probably realized that one box of cake mix makes quite a bit of cake. If your goal is to make a simple Bundt or an easy dozen cupcakes, all you really need is half the box mix—which leaves the other half for another baking occasion.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Here's a not-so-well-kept secret about the food industry: retailers love to take your money. And one of the ways they do that is by dividing food into smaller sizes and charging more. Have you ever noticed that a container of precut, washed broccoli costs more than a head of broccoli with the same amount of florets and stems?

I held the orange packet in my hands and presented it to my friend, Seth, as though it were a plastic-wrapped jewel—rather than three ounces of dehydrated noodles.

When it's frigid outside, all you can think about is getting inside and shutting out the cold. But sometimes even the largest house can get a bit, well, stuffy.

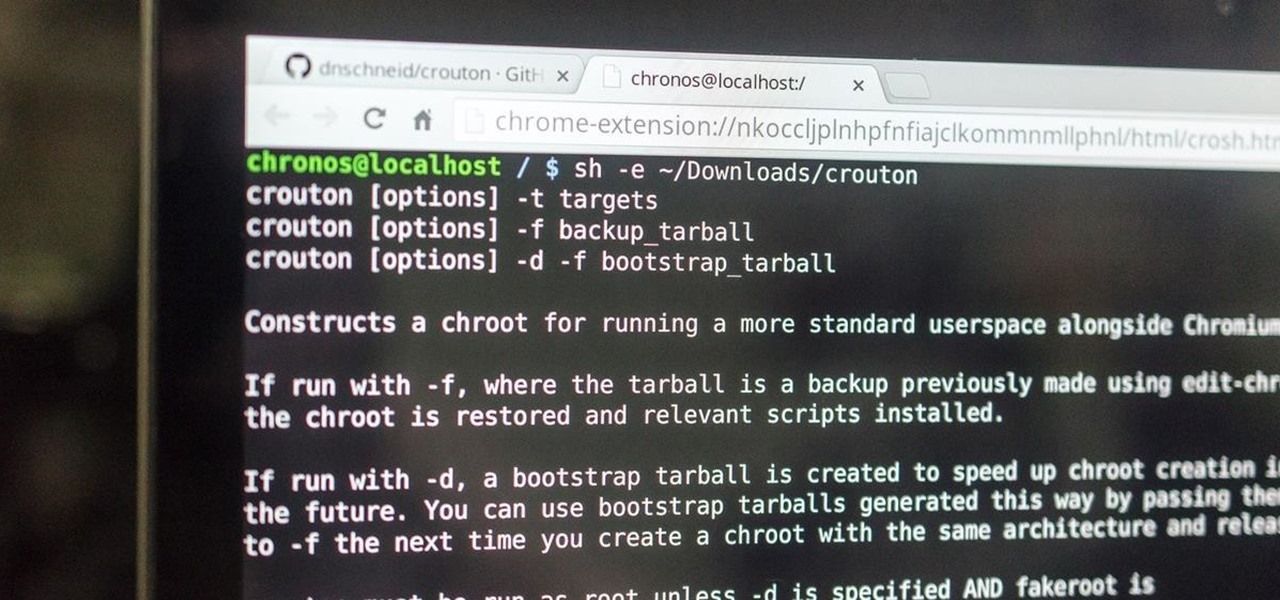
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

I scream, you scream, we all scream for ice cream. It's a universally loved treat that seems to make everyone who eats it giddy. However, there are two downsides to ice cream, in my opinion.

Alcohol isn't exactly considered a healthy lifestyle choice; more often than not, it's associated with empty calories and bad decisions. But that doesn't mean there aren't a few benefits to drinking in moderation. In fact, gin is a liquor with a wealth of potential benefits to offer. So read on, and discover ten ways in which gin might actually be a good drink for you.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Sushi rolls, known as makizushi in Japanese, are only limited by your imagination—and your ability to roll them neatly, of course. While it may seem like a lot of effort, rolling sushi is a snap if you have the right tools.

Preparing and serving seafood can be a daunting task. Fish is so delicate that one extra minute of heat can turn a juicy, flaky filet into a dried-out disaster. But that same fragility also allows us to use unconventional methods to chemically transform the fish into its cooked consistency.

In the world of breakfast, a great trench of injustice divides French toast and pancakes. Just look at the average brunch menu. While pancakes are treated to a wealth of variety (chocolate chip, silver dollar, blueberry, banana, and even some with pop culture references), French toast is often regarded with a one-size-fits-all attitude.

No offense to water, but if I could survive on coffee alone, I would. I swear I'm not addicted... I just really, really, really love the taste of a cuppa joe, whether it's hot, cold, frothed, milked, flavored, plain, whatever! And while my favorite thing to do with coffee will always be to drink it, recently I've become crazy about using coffee in cooking.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

Most of the time we only use the microwave to reheat or defrost, but you can actually save a lot of time by using it for cooking. These genius recipes make the most of this underused appliance, and also turn out some pretty tasty dishes.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

Super Bowl Sunday is just around the corner. With 111.5 million viewers tuning in last year (112.6 if you count streaming), which broke another record that it previously set for the most-watched television event in U.S. history, it's safe to say that most of us will be watching Super Bowl XLIX on February 1st, 2015, whether via TV, web, or mobile.

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Christmas trees, once decorated and brightly lit, are the penultimate holiday decoration, but authentic pines lose their brilliance fast without any nourishment. Plus, they are major fire hazards without regular hydration. But watering one requires a lot of sliding around on the floor, and it can be hard to tell how much water is in the bowl beneath the dark, prickly branches. These five hacks can help!

I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

I love pomegranates. I don't even mind the mind-numbing task of picking out the arils (which is what those ruby-colored seed-like things in the pomegranate are called). However, I'm always on the lookout for new, easy ways to peel it that don't make my kitchen look like a crime scene.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Gatorade: its popular red flavor can stain the whitest fabric, and its sweet taste is oddly refreshing after breaking a sweat. If you've ever participated in a sport, you probably spent halftime at games and practice breaks chugging the stuff. Though it made its name as a sports drink, Gatorade is also a well-known hangover helper—but its beneficial and interesting uses don't end there. The brightly colored drink can do so much more than just hydrate you.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

HTC has made it their mission to get updates out to its devices as quickly as possible, with new builds slated for release 90-days after Google finalizes a build—this is dubbed HTC Advantage.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.