Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.
Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.
The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.
We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

We all listen to podcasts differently — on the way to work, at the gym, when drifting off to sleep. If you're in the latter group and rely on Overcast to help you with your nightly routine, you're probably sick of its blinding light theme keeping you up. That's why the app features a dark mode, to keep things easy on the eyes while picking out or playing an episode.

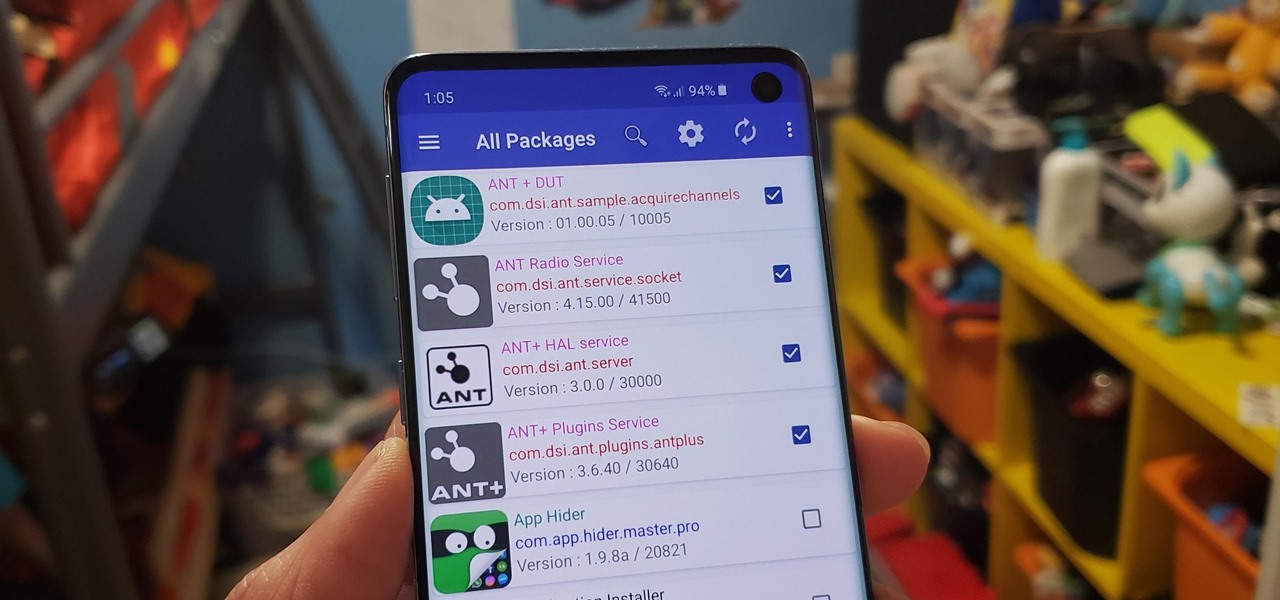
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

The navigation and status bars aren't very noticeable on the S10's home screen since they're transparent. The status bar will even change colors to match many apps. Unfortunately, the same can't be said for the navigation bar.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

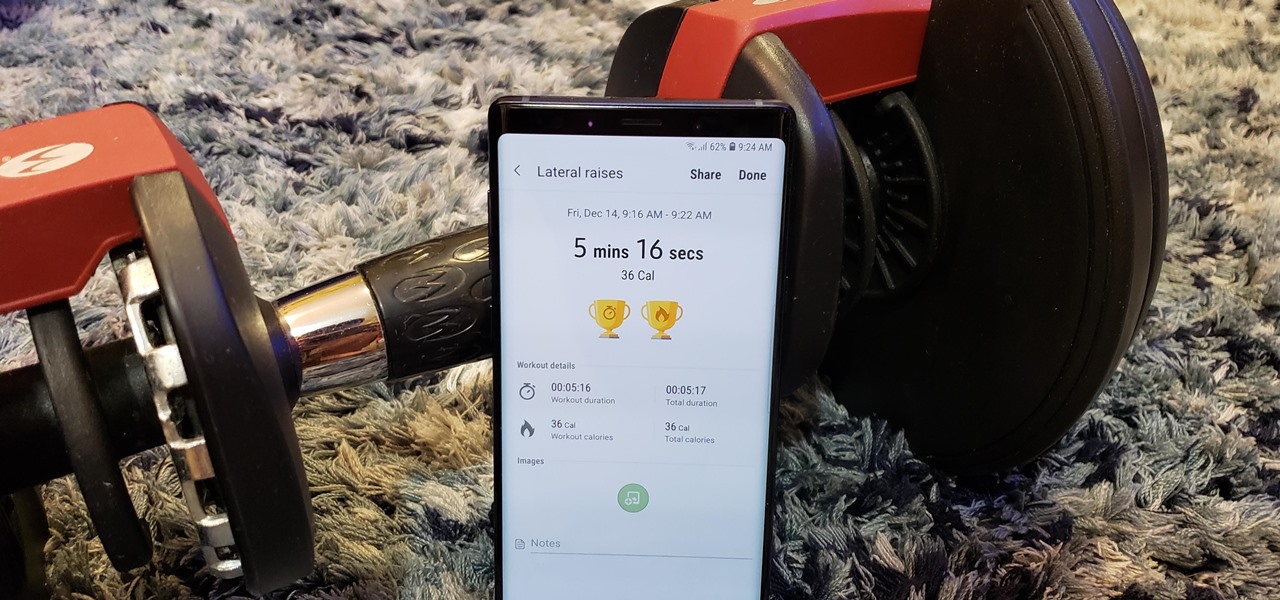
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

The New York Times has made a habit of publishing augmented reality stories throughout 2018, and now the media giant's magazine is getting into the act, too.

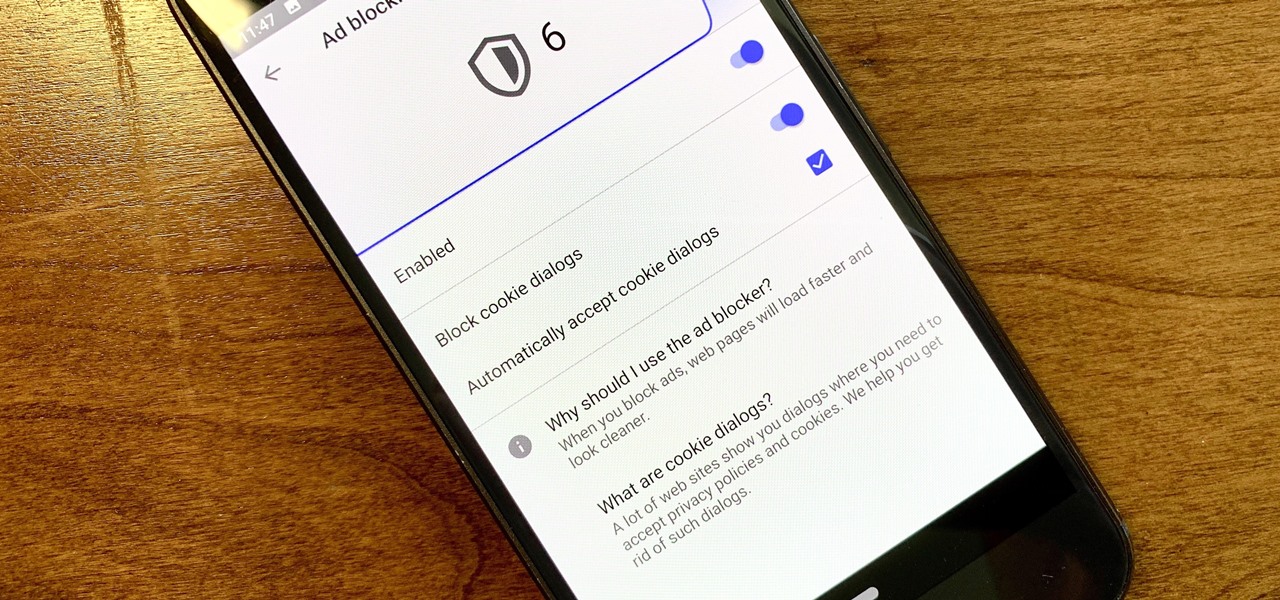
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

Following closely behind the developer beta, Apple released the first public beta for iOS 12.1 to testers Thursday, Sept. 20. The update comes only two days after developers received their first look at 12.1. Both the developer and public betas surprisingly mark the return of Group FaceTime, allowing beta testers to chat with up to 31 other friends.

Apple has finally released iOS 12 for everyone to enjoy, and there are plenty of cool features to go around. Perhaps the coolest feature, at least, for those of us with an iPhone X, is the return of an oft-used gesture we loved on other model iPhones.

In recent years, medical professionals have demonstrated how the HoloLens can assist in surgeries, ranging from collarbone repairs to spinal surgeries to cosmetic procedures. Now, the largest children's hospital in the United Kingdom is also ready to deploy the technology.

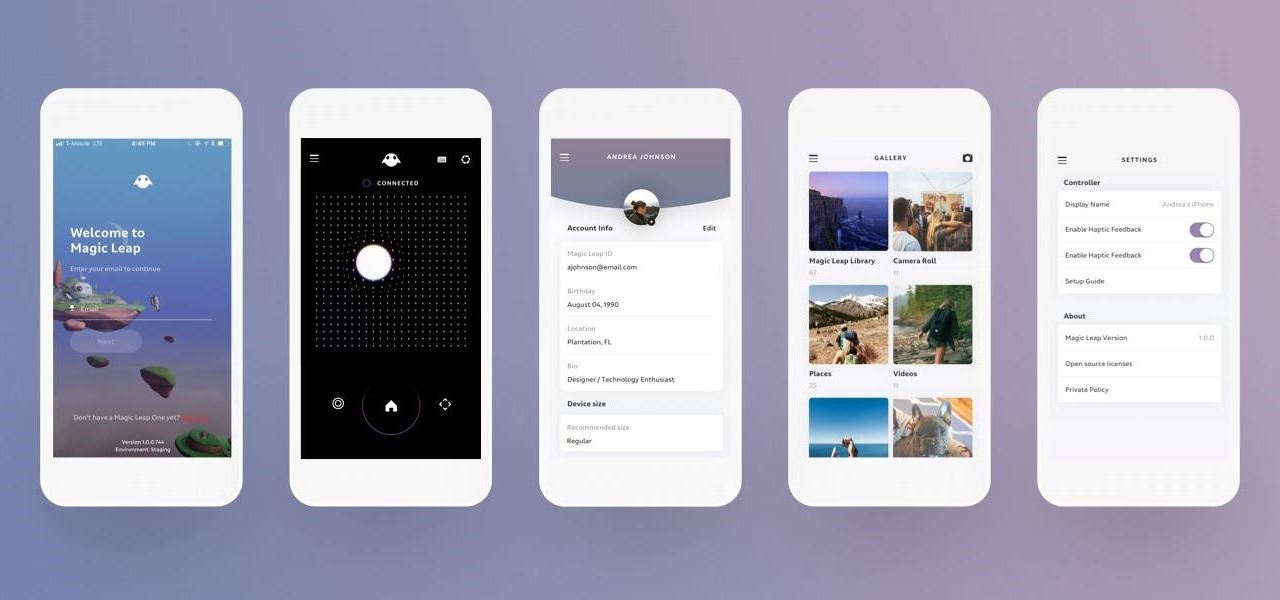
Among a treasure trove of new developer information on the Lumin OS that Magic Leap recently published on its Creator Portal appears to be the official confirmation of the Magic Leap Mobile Companion App.

Will smartphone batteries ever last as long as we need them to? Perhaps not. That's why we rely on external batteries to help us stay connected for hours, even days, longer than usual. But in 2018, you don't want to use just any external battery. Modern Android phones have fast charging — so should your portable charger.

Kings of Soccer recently soft launched in the Netherlands and a few other countries, garnering positive reviews from the mobile gamers who've experienced it. With the 2018 FIFA World Cup now in full swing, we wanted to let you in on a little secret: You can play Kings of Soccer right now ahead of everyone else, regardless of where you live.

When the iPhone X was first introduced, it came with an odd way to force-close apps. While all other iPhone continued to use a two-step gesture in iOS 11, iPhone X users were stuck with an annoying three-step gesture that was seen last in iOS versions from at least six years ago. Thankfully, iOS 12 has changed this and makes force-closing apps as simple as it should be.

Ads can detract from your mobile browsing experience, especially if they appear out of nowhere as popups or large annoying banners that take up almost all of your screen. If those weren't bad enough, some ads appear as extremely loud videos that can even disrupt others around you. In fact, ads have gotten so obnoxious that even Google itself was forced to act.

The augmented reality cloud and multi-user experiences are shaping up to be one of the hotter areas of augmented reality, and now Google is the latest entity to back these emerging branches of AR.

While certainly faster than writing by hand, manually typing passages from a book or document can be slow and frustrating. But thanks to Google Assistant, this is no longer the case. Whether you need to quote text for an essay or need to win an online argument, all you need to do is point your phone's camera at the paper and tap a few times.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Rooting has a long and storied history in the Android community. As OEMs push out more refined software, the need to root has diminished — still, the number of incredible things you can do with a rooted phone is enough to tempt many enthusiasts. Luckily, some manufacturers are still putting out root-friendly devices.

It took a few months, but several major phones are finally receiving updates to Android Oreo. At this point, we've spent significant time talking about Oreo on the Galaxy S8, Galaxy Note 8, and Essential Phone. While an update to the latest OS is always great, there is one big Android 8.0 feature that isn't coming to every phone.

Samsung's Galaxy S8 and S8+ are excellent smartphones that wowed critics and consumers alike. So, it's only natural that Samsung's followup, the Galaxy S9 and S9+, would garner significant anticipation. While we don't know everything about these devices quite yet, we do have guesses to some key points of interest, including when the device will be announced and even released.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

It's not rare to see an advertisement in tech directly call out the competition. Whether it's the famous Mac vs. PC ads from back in the day or the Pixel burning the iPhone 7's lack of a headphone jack, rivalries in these commercials are certainly commonplace. Samsung's new ad campaign takes a more subtle approach to this "throwdown" advertising, but the message is still clear — Samsung wants you to know its AMOLED displays are better than Google's and LG's POLED.

One of the most highly-cited drawbacks to the HoloLens is its limited field of view (FOV), but now it appears that Microsoft has solved that problem.

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.