When it comes to barbecues, vegetarians get the short end of the stick. While you're brushing fire-roasted ribs with your favorite mouthwatering barbecue sauce, we're crossing our fingers that there's some meat-free side dishes hiding away somewhere.

Samsung's Note series is directly responsible for some of the biggest innovations in smartphones. As the first "phablet," it sparked the current craze for bigger screens, and the S Pen stylus has been mimicked numerous times. Even the curved display made famous by the Galaxy S6 edge made its debut on the Note 4, so this is the one smartphone line you want to keep track of if you like to stay on the bleeding edge.

My husband's and my daily schedules are constantly changing. Frankly, it's complete chaos sometimes, so I can't plan to have elaborate dinners on the table at six o'clock every day. And by the time we actually get to eating in the evening, we've become so hungry that our moods have taken a nosedive.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

Fresh, homemade pasta definitely beats the dried stuff from the store. However, most of us aren't usually in the mood to knead dough for 10 minutes... or to clean up a sticky, doughy, floury mess afterward.

I recently wrote about fast food fakeouts you can make at home, but people cannot live off fast food alone. Sometimes you need to step up your game a little and enjoy the fare at a popular chain restaurant with a bit more variety to its menu.

When alcohol tastes bad, there's little you can do to save it—or so you think. While it might seem easier to toss your entire bottle of old, opened wine, or to give up and drink crappy vodka anyway, there are creative ways to turn a spoiled or just plain bad boozy beverage into one you actually want to drink.

One of the common complaints about dry pasta is that it lacks depth of flavor. This is why, once cooked, it often pairs best with bold and complexly flavored sauces.

For many of you, the carving fork only comes out at Thanksgiving as an essential turkey-slicing aid. Perhaps you pull it out of the knife block to slice up the occasional roast. But the carving fork (also known as kitchen fork) can be used for many more tasks around the kitchen, and some of the more unusual involve your favorite shellfish.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

There are literally hundreds of granola recipes floating around the internet—but I can tell you right now that they're all completely unnecessary. You don't need a recipe to make granola; I've been making granola for years and have never once used one!

Once again, you've found yourself inviting comrades, companions, and compatriots over for beverages on a Friday evening whim... but alas, your alcohol cabinet is looking rather meager, and your skills are lacking. No worries—just utilize these 10 tricks and spice up your at-home mixology game. Your friends will be none the wiser (and swear that you are a cocktail-concocting genius).

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Whether you're a seasoned wine drinker or just beginning to explore the wondrous world of fermented grapes, finding fantastic wine on a budget isn't as difficult as one may think. With these 8 tips, you'll see how and why you need not shell out $45 to get a great-tasting, high-quality bottle of wine without settling for vino.

Girl Scout cookies are arguably some of humankind's greatest creations. Not only are they tasty, but they also support an excellent, female-empowering cause. While many folks (cough—yours truly—cough) have been known to plow through an entire sleeve of cookies at a time, there are ways to use Girl Scout cookies beyond shoving as many as you can into your mouth at once.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Oven space is scarce on that fated fourth Thursday of November. Even if you can find a spare space for pumpkin pie on the bottom shelf, you risk turkey drippings overflowing from above and ruining your beautiful dessert — not to mention a burnt crust from different temperature requirements. The bottom line is: oven real estate is valuable, and it's tough to multitask cooking for Thanksgiving when every dish requires baking or roasting.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

I may be in the minority when I say this, but I love leftovers. Whenever I'm cooking for less people than the recipe calls for, I cook the full yield anyway. And when I go to a restaurant, I order whatever I want—regardless of how much I can actually eat in one sitting.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Barbecue season: it's the perfect time to play with fire, produce your best burger ever (until next year, that is), and find even more ways to make beer a part of your daily life. However, even a grilling badass occasionally gets stumped by minor BBQ problems. No worries: We've got solutions!

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

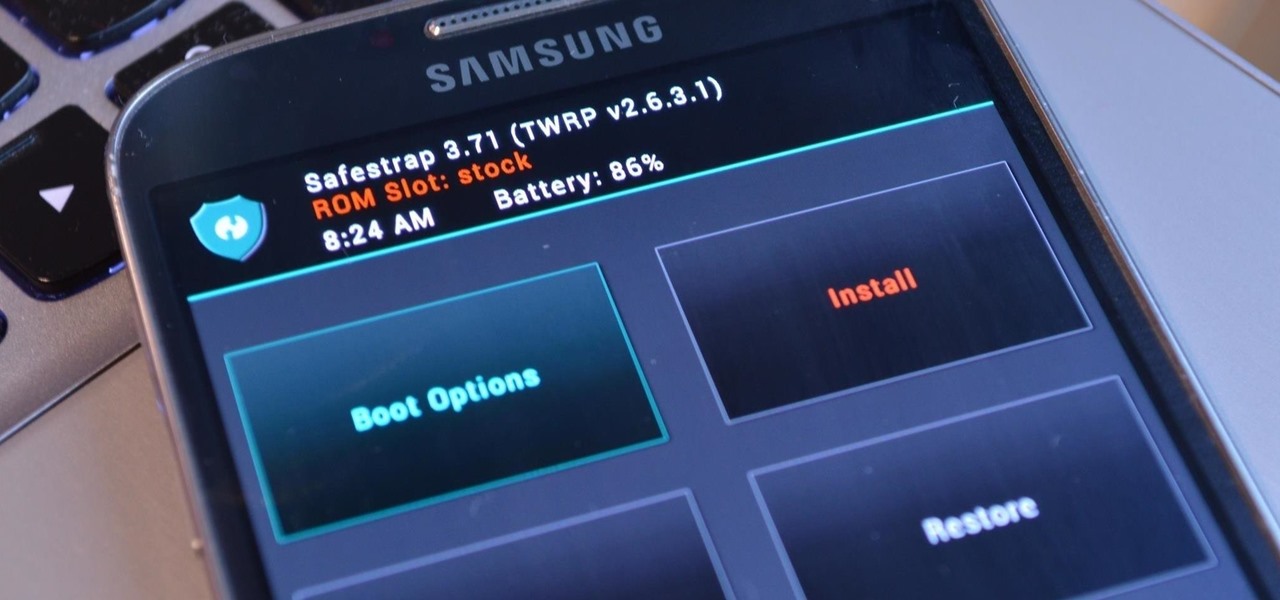
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.