Bringing your back foot up after you hit the tennis ball puts you in position to recover back to the middle of the tennis court. The key, as we explain in this video, is to get your body facing the net after you hit (similar to the ready position). This will let you side shuffle back to the middle of the tennis court.

The fourth thing that every high-level tennis player does when hitting a backhand is follow through. Extend out in the direction you are hitting the ball, then smoothly bend the elbows and wrap the racket up over your shoulder.

This video explains how the amount of shoulder rotation you get during a windshield wiper forehand can differ from a classic forehand. After you hit the tennis ball, you typically have to rotate a little bit more than you otherwise would on the windshield wiper. There are a number of reasons for this, but in this video we keep our focus relatively narrow.

Every time you hit a tennis forehand you choose how you position your feet -- what stance you will use. You can hit a forehand with an open, neutral, or closed stance, but you should stay away from the closed stance if possible. This last stance makes it difficult to rotate your upper body through contact, making it difficult for you to use correct forehand mechanics.

This series of ping pong / table tennis videos demonstrate how to master the table tennis serve. Jim Clegg, a Level 4 Coach with the English Table Tennis Association and Head Coach of the Preston Table Tennis Association, explains and demonstrates how to do a table tennis serve correctly. Serving today is an extremely complicated topic. These are 9 in depth thought processes for a table tennis serve.

Watch this video tutorial from the Polish Guy to see how to polish silverware using Cape Cod polishing cloths. In this polishing tip we polish silverware using Cap Cod Metal Polishing Cloths. The cloths are individually packaged in an attractive tin that includes a pair of reusable gloves and a buffing cloth.

Squats are probably the most useful exercise you can do at the gym—no other single exercise encourages more muscle growth. With a range of motion that incorporates many different muscle groups in the legs, core and upper body, squats strengthen not only those muscles, but also the tendons and ligaments that connect them. In addition to their strength-building benefits, squats also teach you core stabilization, which is important for almost any athletic endeavor. Learn how to do barbell squats...

Learn how to do dumbbell reverse raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single-leg flat bench standups and sculpt your body without weights! Presented by Real Jock Gay Fitness Health & Life.

Tired of grandpa's baseball card collection rotting away in your attic? Well, unlike his pop bottle collection, baseball cards could yield a decent amount of income for you, if you know how to sell them. There are different outlets available for selling an individual baseball card or card collection. Know how to sell the fruits of your hobby and avoid getting ripped off.

FreshDV had the opportunity recently to speak with Jerome Courshon on the marketing and distribution of movies and films. Jerome offers a full course in the “Secrets of Distribution” . If you are a filmmaker of any kind you owe it to your crew, your cast and yourself to watch this segment. From contracts, residuals, and pitfalls to avoid Jerome covers the 101 basics of film distribution and helps prepare you for what you need to know once the ink dries on the DVDs. In Jerome’s words:

Learn how to do single leg cable curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do low cable bent bar squat and curl holding the bar high. Presented by Real Jock Gay Fitness Health & Life.

Ah coconuts, such a delicious...seed? Yeah, it's technically not a nut, but who cares. It tastes excellent once you get it open, which is no easy task. Ever wondered how to open a coconut without resorting to hammers, screwdrivers, chisels, or other unwieldly tools? Filmed in Hawaii at the Polynesian Heritage Centre this video explains how the Polynesian people do it - and it's so easy once you know how.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

This how to video tutorial demonstrates how to sew a straight stitch by hand, just in case you don't have a sewing machine. The straight stitch is excellent for simple hems, decorative stitching and gathering fabric.

In this language tutorial, you will learn how to nominative masculine plural and accusative masculine plural forms in biblical Greek (Koine). This lesson is excellent for scholars wanting to study this ancient language of Greece. Watch this how to video and you will be speaking biblical Greek in no time.

In this tutorial shows an exercise to learn all major chords, minor chords, dominate 7th chords, and diminished chords on the piano or keyboard. This is an excellent exercise to improve agility on the piano. Watch this how to video and you'll be playing all of the piano chords in no time.

When it comes to difficult-to-prepare BBQ cuts like the rump, you either get it completely wrong or completely right. Rump, also called "picanha" by Brazilians, is an excellent cut - if you know how to prepare it.

In this video he discusses a grip for the return of serve to maximize what you can do on it. This is a foundation of my teaching style that we will take over the point on the return of serve, assuming it's a second serve. On the first serve, our goal is simply to neutralize any advantage and place ourselves in a good position.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

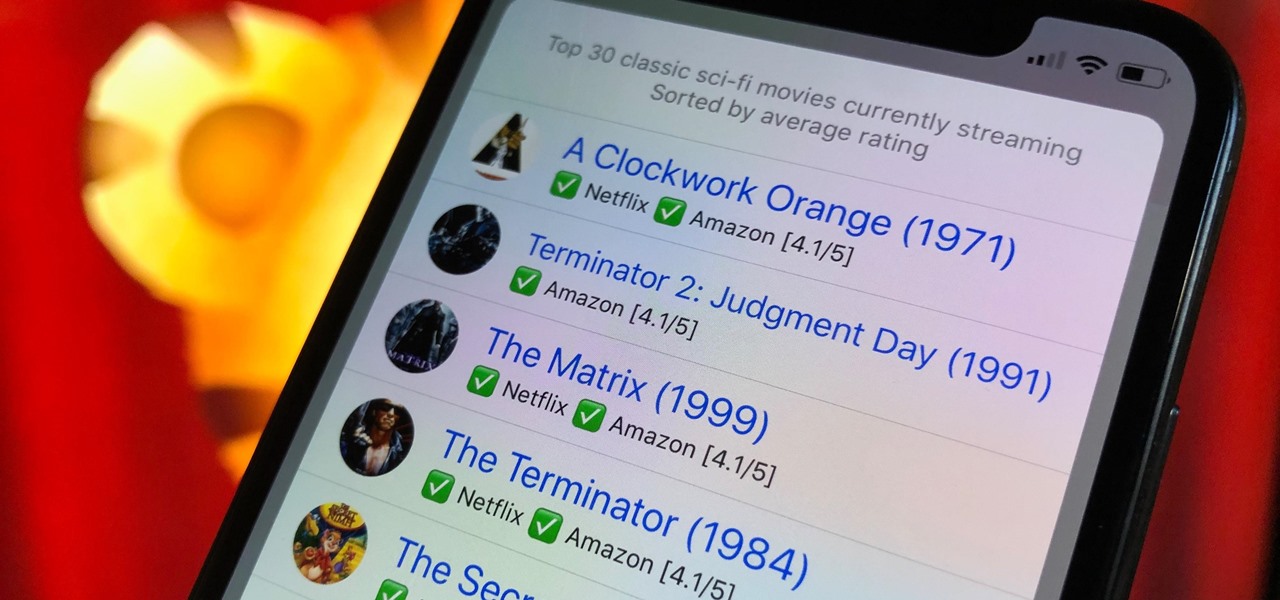
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Last year, Razer kicked off a new trend by building a smartphone from the ground up with mobile gamers in mind. At the time, many thought the Razer Phone solved a problem that no one really had — but a year later, we're starting to see that gaming phones are perfect for more than just Fortnite players.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.

Mobile World Congress 2018 is here, and with it, Samsung has officially announced the highly anticipated Galaxy S9 and S9+. While we already knew much about the new phones, Samsung's presentation officially filled us in on what to expect from the S9's cameras, including dual aperture, two cameras, and super slo-mo.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Enough with zoodles (zucchini noodles), spaghetti squash, and carrot 'pasta' spirals. A well-prepared dish of zoodles with sauce is beautiful and tasty, but let's get real, it doesn't fill you up. If you use it as a meal replacement, then you'll be hungry about 30 minutes later.

Even if you've put aside your percolator and have gone the way of the pod coffeemaker, there are still dozens of ways to use your leftover coffee filters. Incredibly cheap, absorbent, and shaped with a ruffle, coffee filters are useful in the kitchen, garden, and around the house.

Any pizza lover knows that a quality crust is crucial to the whole experience. Good pizza crust should be delicious on its own, for once you get to the edge, it will be without any toppings, sauce, or cheese to disguise a bad character. It should be redolent of fresh, good wheat and taste full-bodied, rather than flat, flabby, or metallic, the way so many big chain and frozen pizza crusts do. The exterior should be crisp, while the interior contains an airy crumb as well as having a tender, s...

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.